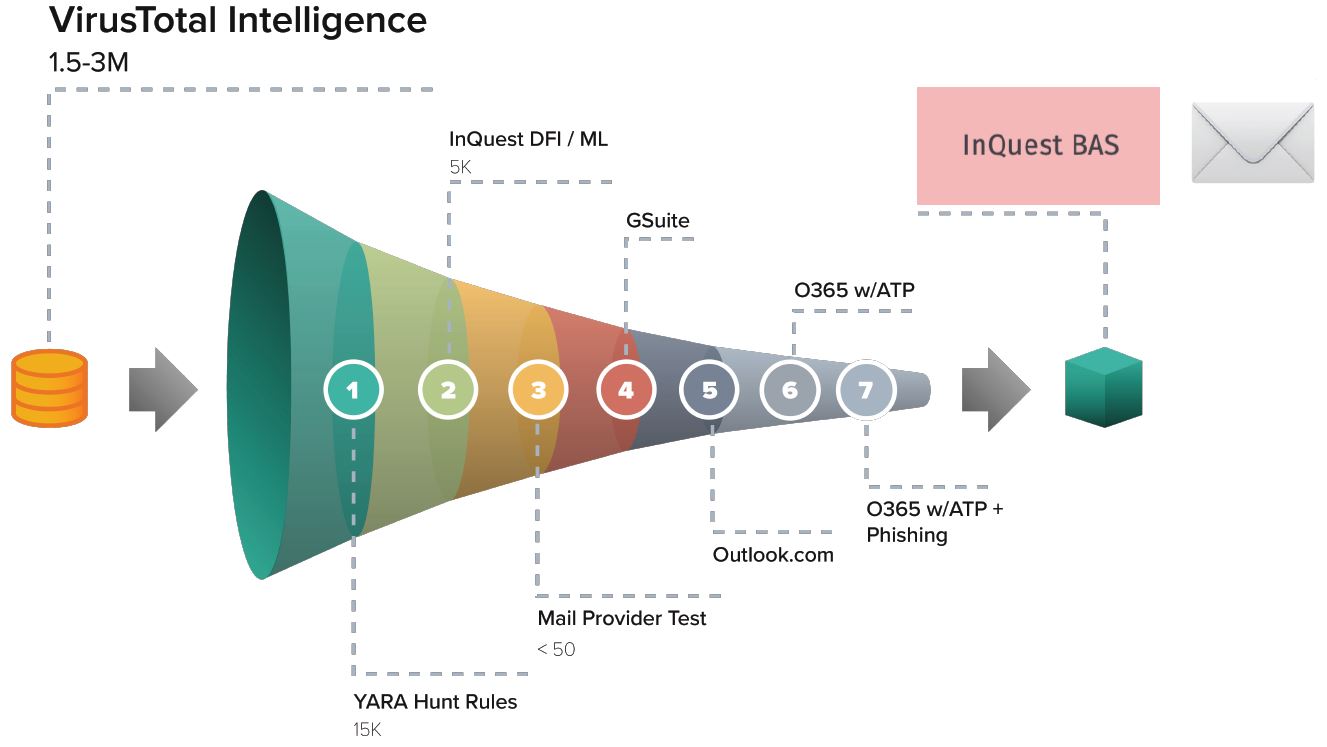
To validate an e-mail security stack’s capability in blocking current real-world threats harvested from the wild, InQuest gathers unique malware daily and validates the common cloud e-mail providers (GSuite, O365). Collectively (stacked on top of one another), the providers’ default security stacks are capable of detecting between 85% and 95% of these novel attacks. The samples capable of bypassing these stacks are candidates for the InQuest Email Security Assessment.
High-level illustration showing how threats are distilled into the assessment.
Read more about the Trystero Project in a recent interview our CTO did with George Rettas on Task Force 7 Radio
Task Force 7 Radio Interview with Pedram Amini
Why Are We Still Talking About Email Security?
The Chief Technology Officer for InQuest, Pedram Amini breaks down why e-mail security is still a massive issue for most businesses, what types of e-mail attacks are prevalent in the market today, and how corporations can defend themselves against these resilient attacks. Amini also unpacks the email technologies provided by Microsoft and Google, which one of them have more effective email security, and the projects and technologies he has developed to fight the good fight against one of the most significant attack vectors used by Cyber Organized Criminals today.
This interview with George Rettas (EA) was featured in Ep: 159: Why Are We Still Talking About Email Security?01:00
Questions are displayed with the main points to the response.
GR:Last we spoke was August of 2019 in episode 97. You had just launched InQuest Labs at Blackhat and announced InQuest was getting into the enterprise space with e-mail security. Catch us up on your background and what’s been going since we last spoke.02:12
PA:
• InQuest Labs is basically an interface into our R&D “apparatus”.
• We made the investment internally in order to stay ahead of malware and to discover 0-day attack samples. That was the subject of the Blackhat presentation.
• Fast forward to today, and InQuest Labs has over 100k monthly visits, 100 active (free) API keys, a Slack and Reddit community with over a dozen experiments running on against real-word traffic. Some of the outputs of which you can see through the automatic posting to Twitter and Reddit.
GR:Why e-mail security? It’s a crowded space, no?03:24
PA:
• E-mail security products are plentiful for a reason. The majority of attacks start with an e-mail. Look around at the headlines; it’s far from a “solved” problem and for a good reason.
• According to the Verizon Data Breach and Investigation Report, ~95% of attacks start with an e-mail, and more than 30% are phishing related.
GR:What do email-based attacks look like? Is there a common theme?05:31
PA:
• Lower tech: Phishing, vanity spoofing, invoice scams, social engineering.
• Higher tech: Well-developed, targeted attacks. Nations-state APTs, Red-Teams, cybercriminal organizations Walkthrough of a common malware carrier or Tale of a Polished Carrier.
GR:What about on the defender side? What’s the common theme there?09:46
PA:
• Secure E-mail Gateways
• Application Programming Interfaces
• Endpoint Detection and Response
• Threat Intelligence Platforms
• Security Awareness Education and Training
GR:It’s common knowledge that Microsoft/Google are the big providers. What’s the actual breakdown between the two?12:00
PA:
• While we are not sure on overall users, we have examined some anecdotal observations from commercial utilization
• From the perception of popularity, it appears that the distribution is around 90% Microsoft and 10% Google, but the growth for Google is gaining by a point every year.
• Amazon is one to look at as well. They offer both SES and Workmail. SES has a security option as well. We’re looking at that option next and expect to start posting monthly updates in 2021.
GR:While we’re talking numbers, what’s the malware volume like? What’s that landscape look like? What’s the volume of malware daily? What is it, 100k? 1M? 10M? a day.13:51
PA:
• The volume is well over one million files a day. These observations quantify a tremendous increase over the years.
• There is consistently a higher volume of PDF (phishing) than DOC (malware)
• Dozens of operators innovating regularly. It’s a business like any other.
• Through various pivots and anchors on “malware as a service” type organized criminal elements. There are around 3 dozen common campaigns that we track, such as Emotet, Dridex, Lokibot, QBot, Trickbot, and SmokeLoader.
GR:The volume alone is an indicator of how this isn’t a solved problem; any other contributors come to mind? We left talking about the volume of malware and actors behind it, again though why e-mail, why target users?16:38
PA:
• Software is complex and ever-changing. The client-side will be the last place for vulnerabilities to die.
• Attackers are motivated, clever, and have plenty of time to develop, test, and tune their attacks. For consideration, use of a macrosheet instead of a macro for AMSI bypass.
• Users are “creative” and will often surprise you. For example, take a look at RTF docs being used as containers.
GR:So I’m curious to hear more about the “Trystero Project”. You’re basically running an experiment where you’re feeding real-world malware through the providers daily, and measuring efficacy?25:44
PA:
• The Tyrstero Project has been measuring the baked-in security efficacy of GSuite, Outlook, O365+, and O365++.
• The experiment can be described at a high-level as the connection of InQuest Labs through a mail loop we created on each provider.
• If a sent e-mail with malicous attachment loops back, then we know the provider missed it, and the file would have ultimately been sent to the user.
GR:Ok, so who’s got the best security?27:48
PA:
• Well, that depends! It’s back and forth between the vendors.
• Outlook is not adequate alone for detection.
• Generally, free account users go for GSuite.
• There are nuances between O365+ vs O365++.
• There is a Java gap for Microsoft’s detection.
GR:What makes your e-mail security different from what the big vendors (Google and Microsoft) are offering? What are you guys doing on top of this?30:06
PA:
• Similar to how we started in the on-premise space, we focus on the gaps. Hence the Trystero project/Mail Provider Comparisons. More importantly, we can focus on customer-specific gaps to help them mitigate the risks to their business.
• Deep File Inspection (DFI) provides unparalleled visibility into the files and super granular detection logic and controls. No documents with embedded files. No one-page PDFs with a suspicious URL being delivered from a new sender. What VBA functions can be called even.
• Your existing provider may re-write URLs in the e-mail body, but who’s looking at URLs embedded within documents? How about layered files that have the payload resting at the bottom? What about password protected files where the key has been provided to the target?
• Best practices that we have seen are PDF without JS, remove Java, and disable Macros. While potentially not applicable to a large enterprise that is macro dependent. There is also signing, but that’s insufficient and can even provide a false sense of security as a recent technique was shown this year to be spoofable (CurveBall).
• Optical Character Recognition for data-loss discovery. Looking at scans of documents, pictures of e-mails, and even slanted photos.
GR:I know your on-premise solution provides a retrospective analysis capability called “Retrohunting”. Is that offered through the SaaS platform as well?36:20
PA:
• Absolutely! Retrohunting has been a significant differentiator for us across the board.
• We all know that hindsight is 2020. With Retrohunting, you can leverage tomorrow’s threat intel against today’s data.
• Proactive hunting with emerging or user-defined signatures against previously seen organizational traffic.
• Retrohunting can help to determine if our customers were targeted by an in-the-wild 0-day or N-day campaign.
GR:In several of your previous roles, you were entrenched with identifying and/or validating 0day vulnerabilities. The buzz around 0-day, who has them or who prevents them from being exploited, doesn’t seem to be what it was years ago. Is that still an area of interest for you at InQuest? If so, what are you doing to protect InQuest customers from attacks targeting 0-day?41:21
PA:
• Absolutely. We have some eye-opening intelligence sharing partnerships through Microsofts Active Protections Program (MAPP) and Exodus Intelligence.
• Through research and concepts like the Iceberg of Inspection, we have shown that the quantity of: Malware > vulnerabilities > exploitation techniques
GR:What if you want to go further? Nothing is bulletproof after all.46:02
PA:
• E-mail Decoration provides a phishing prevention tool that uses banners at the top of e-mails to inform users of the security status for inbound files and malicous links. Decorative banners range from informational to indicative of danger and have the ability to identify first-time senders, brand impersonation, vanity spoofing, malware content, and other threats.
• Tailored intelligence enrichment. From malware at scale to malware in your spool. We discover outliers via machine learning, extrude, and share related indicators to the customer. These derived indicators are great for rapid deployment.
• Deception based. While I can’t disclose the methodologies, this incorporates a proactive approach in extruding information from your adversaries.
GR:What about folks with hybrid environments? Exchange plus 0365.50:57
PA:
• Not only do we support these hybrid architectures, but you can mix native capture with IMAP, ICAP, data-at-rest, and API. All through a single, multi-tenant capable platform.
GR:This sounds neat. How does one go about testing their e-mail security stack?53:22
PA:
• We recently announced that we’re opening up this loop as a Breach and Attack Simulation service. There are no GDPR concerns, just validation of the regular security controls.
• The simulation is relatively straight-forward, create a new account with a forwarding rule back to InQuest, and our BAS service will loop real-world samples through your stack and provide a report on what kinds of threats made it through and which detection engines could have helped stop them.
Free Assessment Inquiry
At InQuest, we’re fanatical about malware analysis and ingest real-world samples at-scale, dissecting millions of files daily. We leverage a combination of our Deep File Inspection (DFI) analysis engine and a proprietary machine learning apparatus to distill the volume into a daily harvest consisting of dozens of “interesting” samples. These samples are verified as capable of bypassing all of Google’s and Microsoft’s available security features combined. We then innocuously “loop” this daily harvest of malware through your email stack and provide you with a daily report assessing your detection gap for bleeding-edge real-world malware. Select the keep the assessment ongoing to serve as continuous validation of your email security. If you’re interested in hearing more or are curious to try the assessment for free (as in ?). Let us know your name and corporate e-mail address and we’ll get in touch shortly.