Phishing
Breaking The Chain
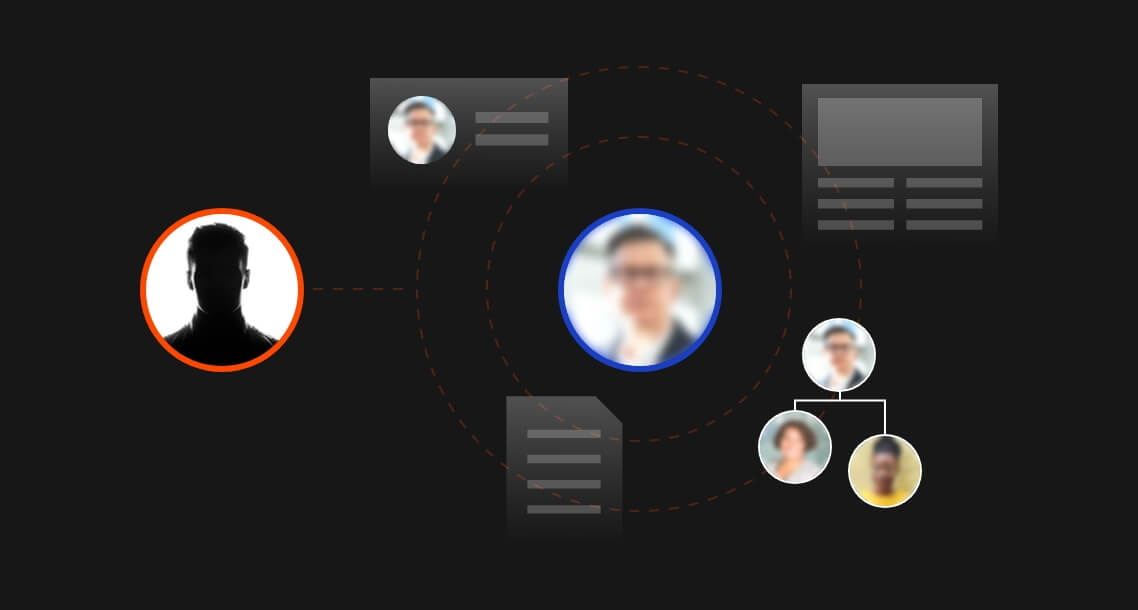
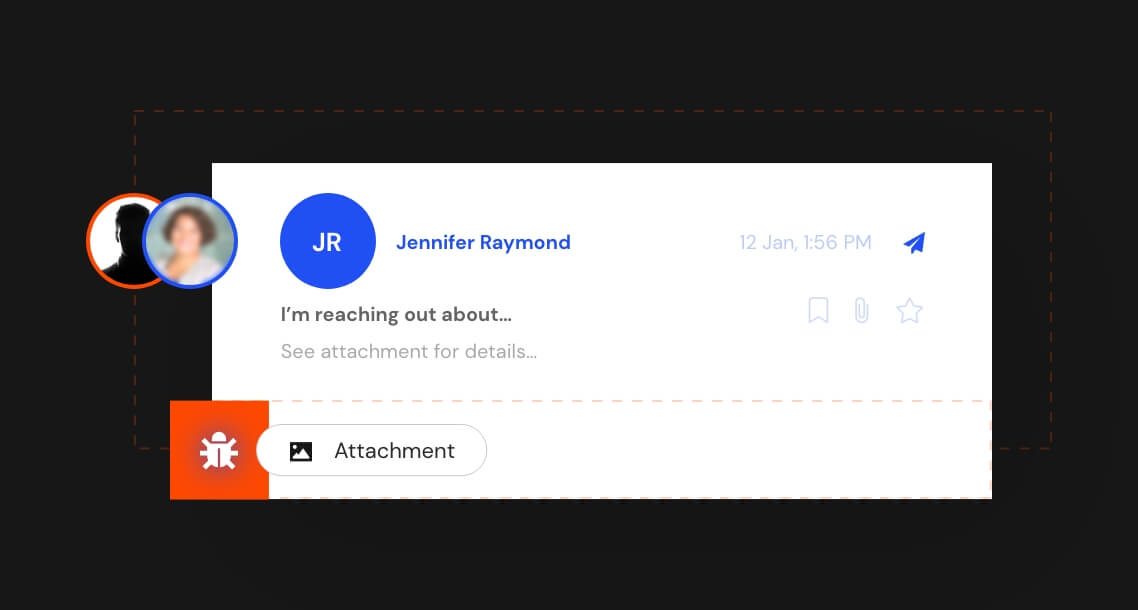
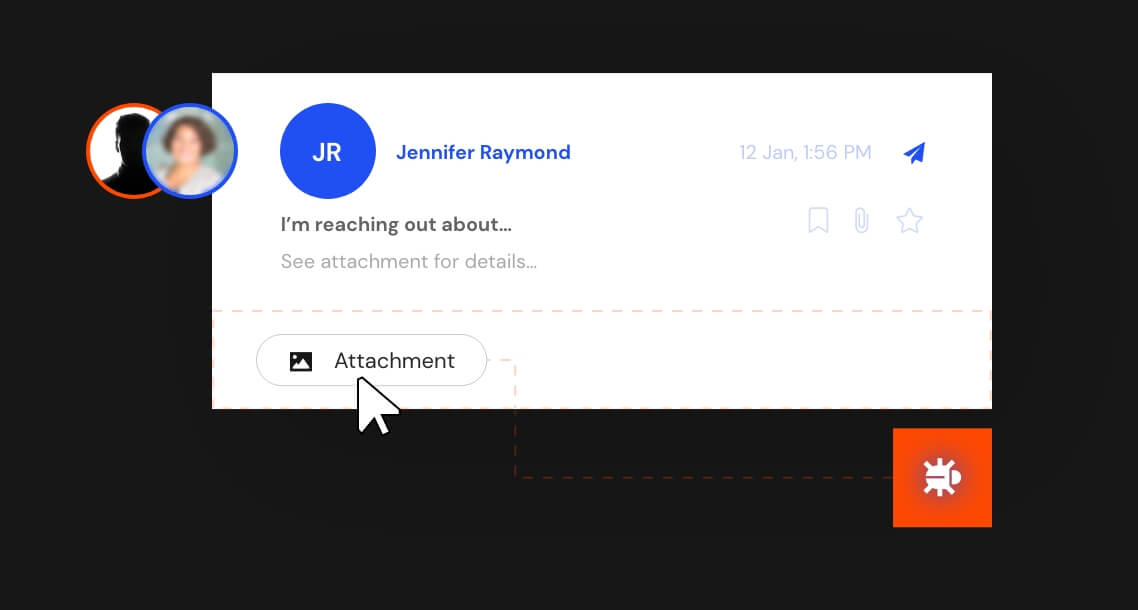
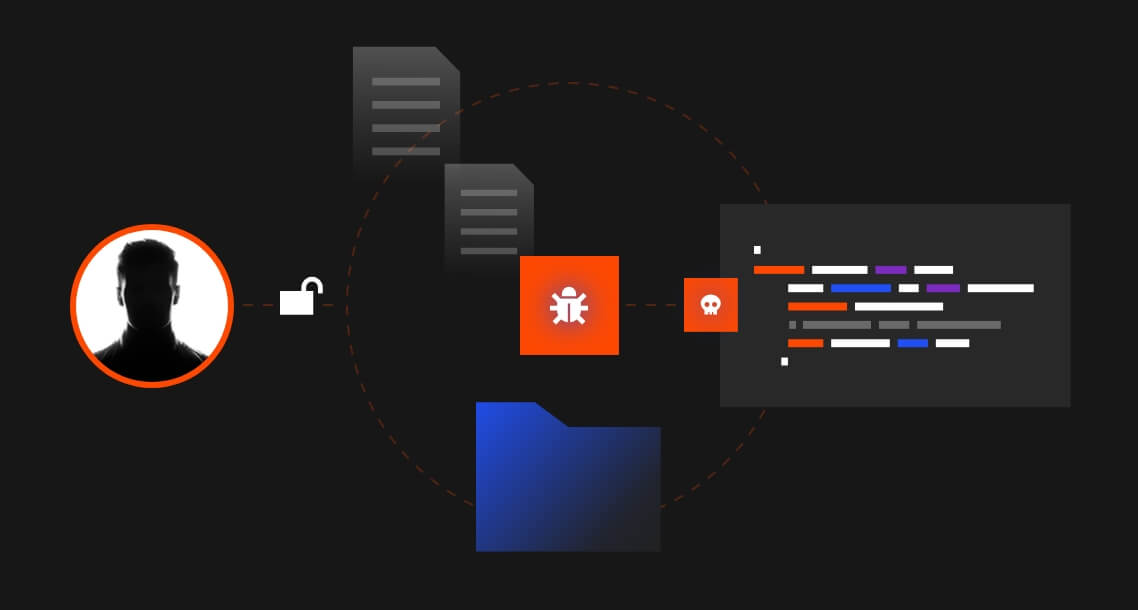
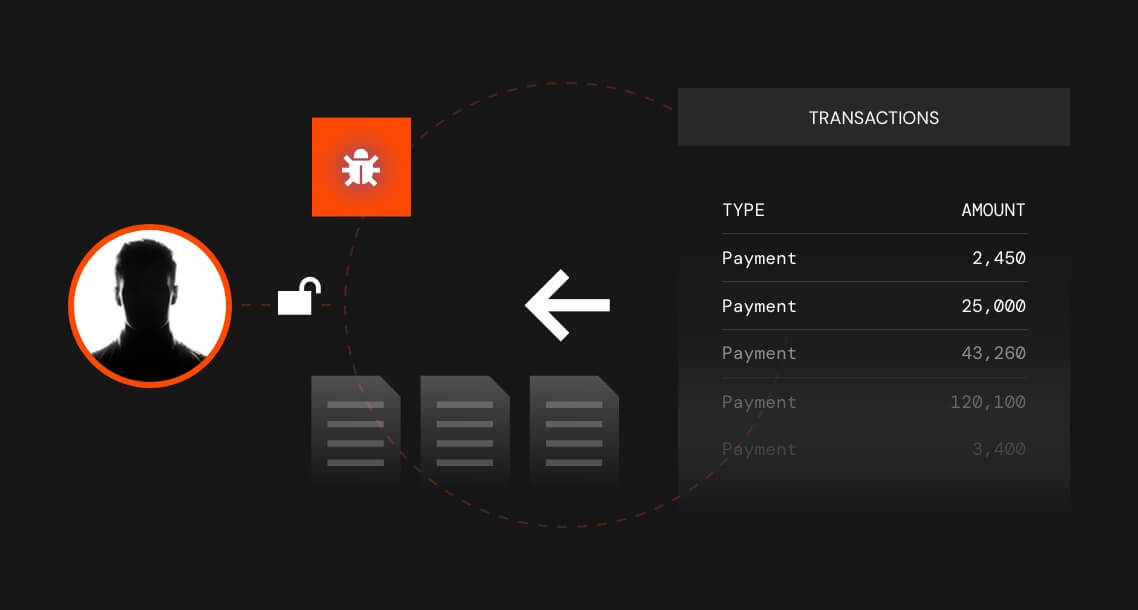
When cybercriminals initiate a phishing campaign against your organization, they generally follow a specific pattern of behavior known as the attack chain.
InQuest built the MailTAC product offering with this in mind. With our tools in hand, your SOC team will have everything it needs to break the attack at any point in the chain.