Most security practitioners have heard of “The Pyramid of Pain,” David J Bianco first introduced that concept back in 2013. At the time, he was focused on incident response and threat hunting to improve the applicability of attack indicators.
The Pyramid measures the potential usefulness of your threat intel. It also measures the difficulty of obtaining that intel as well as evading detection at that level (from the perspective of the adversary). The higher up the pyramid we go as defenders, the longer-lasting our defenses.
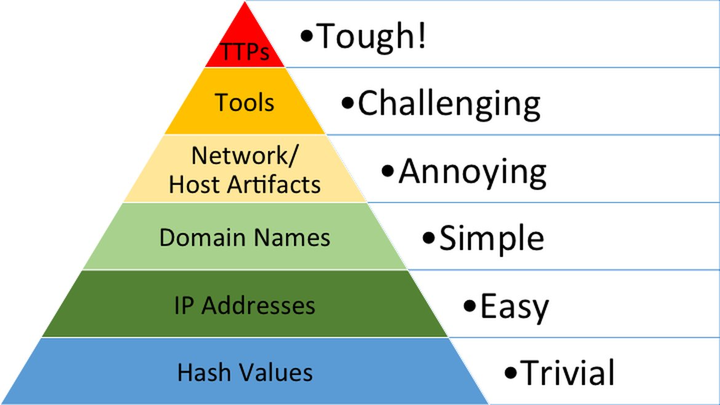
Referring to a related threat hunting paper from the Sqrll team, the types of indicators are described as:
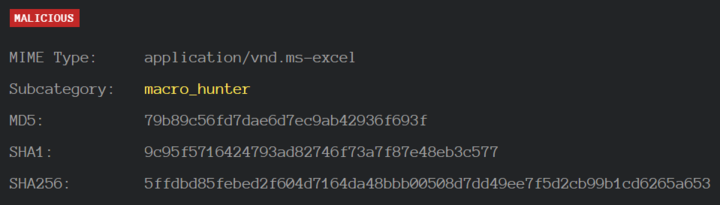
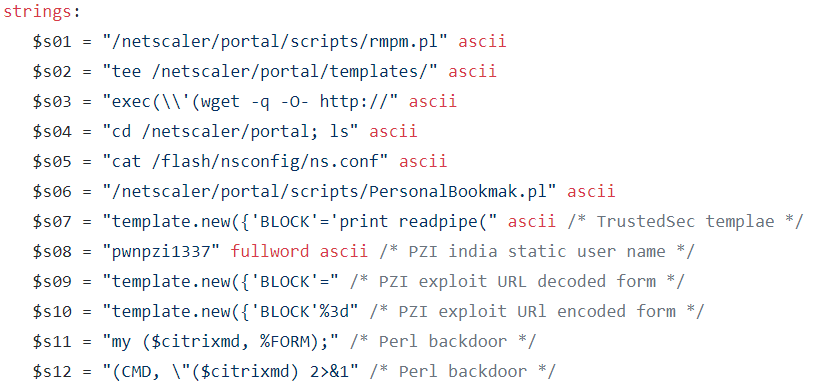
1. Hash Values: Cryptographic hashes (MD5, SHA, etc.) that correspond to specific suspicious or malicious files. Often used to provide unique references to particular samples of malware or to files involved in an intrusion. A single bit modification to a file results in a completely different hash value, and there are so many specific instances of malware, that’s in many cases, it’s not even worth tracking them. Fuzzy hashes such as SSDeep and TLSH can provide better mileage.
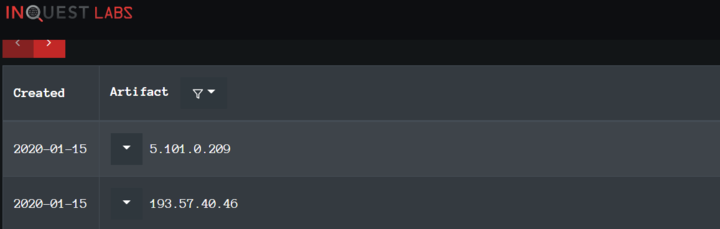
2. IP Addresses: IP addresses are quite literally the most fundamental indicator, but if they are using an anonymous proxy service like Tor or something similar, they may change IPs quite frequently and never even notice or care.
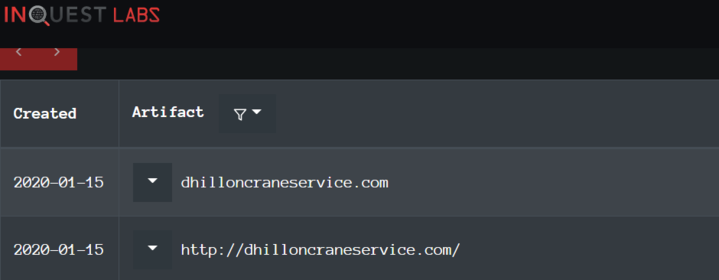
3. Domain Names: This could be either a domain name itself (e.g., “evil.net”) or maybe even a sub- or sub-sub-domain (e.g., “this.is.sooooo.evil.net”). They must be registered, paid for (even if with stolen funds), and hosted somewhere. That said, there are a large number of DNS providers out there with lax registration standards.
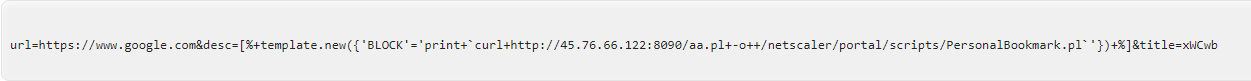
4. Network Artifacts: In practice, these are pieces of the activity that might tend to distinguish malicious activity from that of legitimate users. Typical examples might be URI patterns, C2 information embedded in network protocols, etc.
5. Host Artifacts: Observables caused by adversary activities on one or more of your hosts that would distinguish malicious activities from legitimate ones. These can be any distinctive identifiers, such as be registry keys or values known to be created by specific pieces of malware, files or directories dropped in certain places, etc.
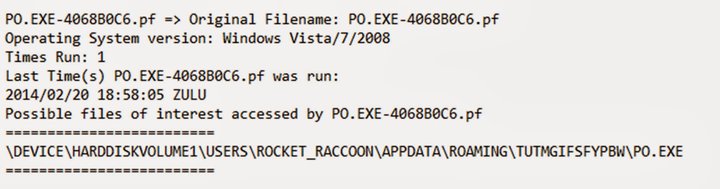
6. Tools: Software used by the adversary to accomplish their mission. Mostly this will be things they bring with them, rather than software or commands that may already be installed on the computer. This would include utilities designed to create malicious documents for spearphishing, backdoors used to establish C2 or password crackers, or other host-based utilities they may want to use post-compromise. For a unique example of anchoring on tooling, consider the following search on InQuest Labs that anchors on a deep indicator, an XMP ID within InQuest Labs. A myriad of malicious and benign samples are found here. We can filter on the benign ones to focus our efforts on why detection was low.
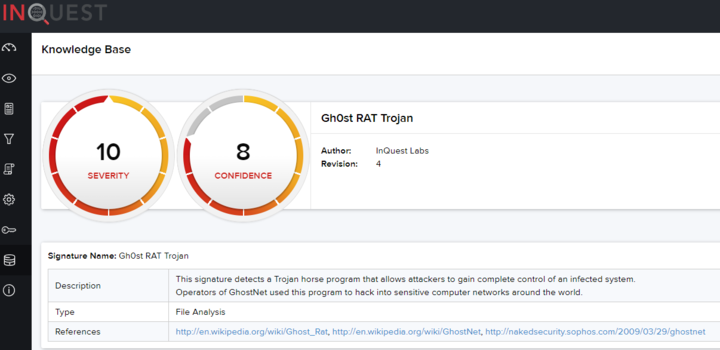
7. Tactics, Techniques, and Procedures (TTPs): At the apex of the pyramid is how the adversary goes about accomplishing their mission, from reconnaissance all the way through data exfiltration and at every step in between. When you detect and respond at this level, you are operating directly on adversary behaviors, not against their tools. “Spearphishing” is a common TTP for establishing a presence in the network.
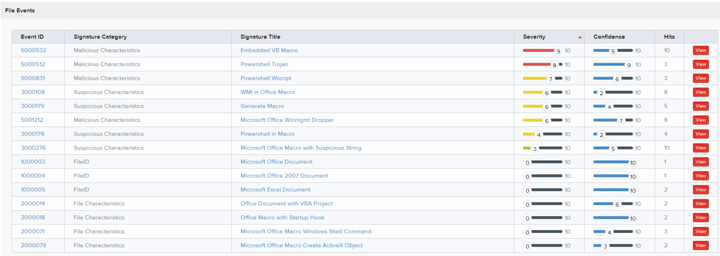
The IceBerg of Inspection flips the pyramid upside down into the sea of threat intelligence and highlights the difficulty of identifying these indicators for use in security monitoring or threat hunting. Considering that 90% of the iceberg is below water, the iceberg of inspection is a perfect analogy for inspection at the application layer and for file types most often weaponized by the adversary.
Deep File Inspection(DFI)
Deep File Inspection (DFI) exposes TTPs through an in-depth static analysis engine. DFI is the reassembly of packets captured off of the wire into application-level content that is then reconstructed, unraveled, and dissected (decompressed, decoded, decrypted, deobfuscated) in an automated fashion. This allows heuristic analysis to better determine the intent by analysis of the file contents (containers, objects, etc.) as an artifact. Deep File Inspection presents a methodology to unwrap these nested files and objects, and classify documents based on their intent, flagging malicious files based on the subsets of functionality they’re using.
Threat Hunting
While most threat hunting is accomplished post-compromise or through the threat intelligence development cycle with the utilization of endpoint data, InQuest adds the pre-compromise dimension by analyzing files inbound to your organization. When threats are detected, the indicators are utilized to pivot to other similar occurrences or write additional detection logic to prevent and detect to subsidiary attacks.
ATT&CK
When looking at the Mitre ATT&CK Matrix, it is evident that there are fewer tactics than occurrences of malicious campaigns or vulnerabilities available to exploit. While identifying TTPs of the adversary may be on the more difficult end of the spectrum, their utilization in security operations will be more fruitful for your defensive posture.
MITRE ATT&CK™
| ID | Name | Description |
|---|---|---|
| TA0001 | Initial Access | The adversary is trying to get into your network. |
| TA0002 | Execution | The adversary is trying to run malicious code. |
| TA0003 | Persistence | The adversary is trying to maintain their foothold.. |
| TA0004 | Privilege Escalation | The adversary is trying to gain higher-level permissions. |
| TA0005 | Defense Evasion | The adversary is trying to avoid being detected. |
| TA0006 | Credential Access | The adversary is trying to steal account names and passwords. |
| TA0007 | Discovery | The adversary is trying to figure out your environment. |
| TA0008 | Lateral Movement | The adversary is trying to move through your environment. |
| TA0009 | Collection | The adversary is trying to gather data of interest to their goal. |
| TA0010 | Exfiltration | The adversary is trying to steal data. |
| TA0011 | Command and Control | The adversary is trying to communicate with compromised systems to control them. |
| TA0040 | Impact | The adversary is trying to manipulate, interrupt, or destroy your systems and data. |
EXODUS
There is sometimes a misconception between vulnerabilities and exploitation techniques; it is detrimental to differentiate the two. A vulnerability is a flaw in a system that could provide an attacker with a way to bypass the security infrastructure of the host operating system or of the software itself. Exploiting is the act of trying to turn a vulnerability into an actual way to breach a system. A vulnerability can be ‘exploited’ to turn it into a viable method to attack a system.
Exodus Intelligence is a recognized leader in vulnerability discovery, exploitation techniques, and vulnerability intelligence. Our team works closely with Exodus to leverage their knowledge and capabilities to 0-day attacks targeting our customers. Customers responsible for maintaining awareness regarding unknown threats to their enterprise networks can subscribe to the Exodus Intelligence enterprise zero-day feed (Enterprise Zero-Day Feed). This offering gives the customer access to a minimum of 50 unique zero-day reports and corresponding exploit code for vulnerabilities discovered by the Exodus team throughout one year. Typically, flaws included in such a subscription affect high-profile vendors such as Microsoft, Adobe, EMC, Novell, IBM, and others.
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge, for 30 days.