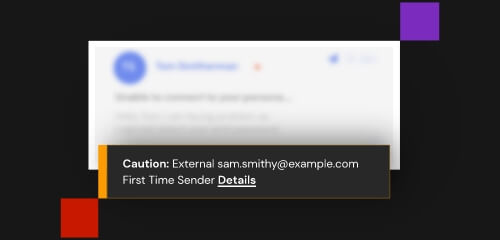
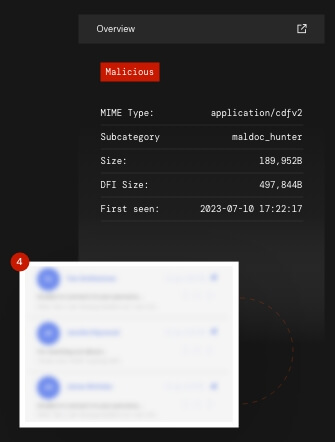
If a member of your organization does fall for a phishing attempt, their credentials may be compromised. The attacker may now have access to, or control over, that member’s email account and other connected systems.
The attackers will now begin to impersonate the affected user by sending fraudulent emails to colleagues, clients, partners, and vendors asking for financial information or other sensitive data.
Sophisticated attackers may even use social engineering to conveniently mimic the target’s behavior, or to create high stress or urgent situations in the hopes of tricking someone into leaping without looking.