To streamline detection, response, and remediation, SOCs must find ways to integrate personnel, systems, and tools without drawing team members into mundane, time consuming tasks.
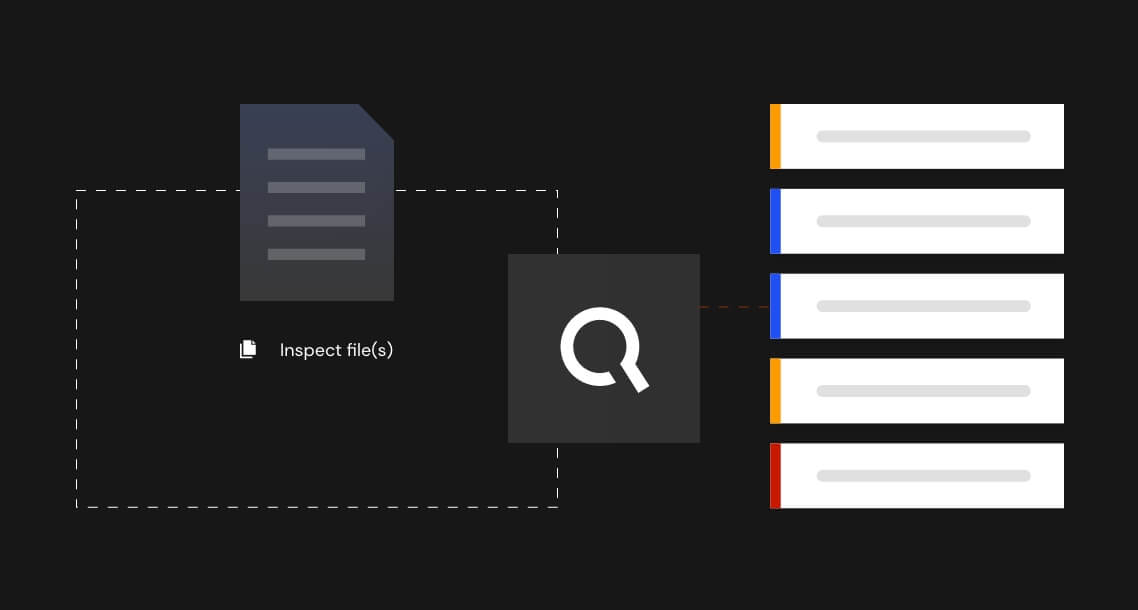
We strategically integrate with a number of complementary security solutions that can be found on our Partners page. When paired together, these joint solution offerings provide a greater return on investment because we consume different analytical perspectives and provide them all in a single composite IQ score.
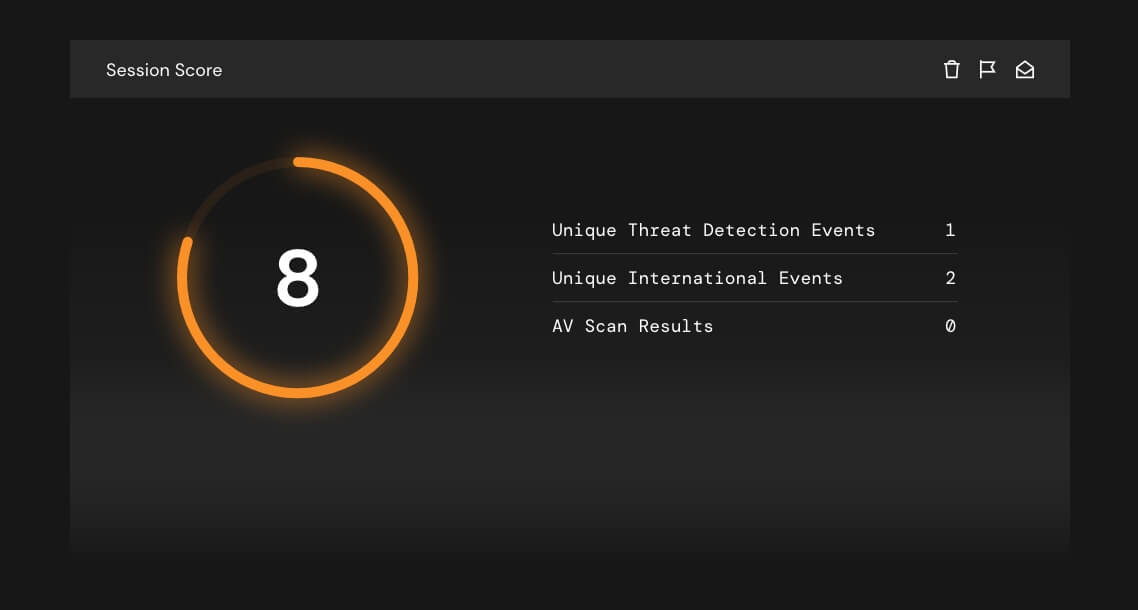
Our Intelligent Orchestration approach involves aggregating, curating, and analyzing terabytes of internal, public, and private threat intelligence data to give your SOC team the pinpoint guidance it needs to enhance SIEMS, enable industry sharing, and strengthen your security posture.