How does fishing work in real life? The fisherman chooses a suitable place for fishing, he chooses the right tools; a fishing rod or nets, and he also needs to choose the right bait. When everything is ready, he can expect a good degree of success.
In fact, fishing in cyberspace is not that different from fishing in real life. A threat actor needs to choose the right tools. Depending on the purpose, they can use different tools; such as bankers to steal money or espionage tools to steal data. A threat actor may also use third-party tools such as Cobalt Strike or Metasploit, at their discretion to suit their needs.
It is just as important for a threat actor to choose the right lure. Why? The fact of the matter is that the first step in many cybercrime incidents still require a minimum amount of user interaction. If the document provided by the macros is provided, then the attacker must coerce the victim to enable the macros to proceed. This assumes the attacker leverages malicious documents rather than other means of achieving remote code execution.
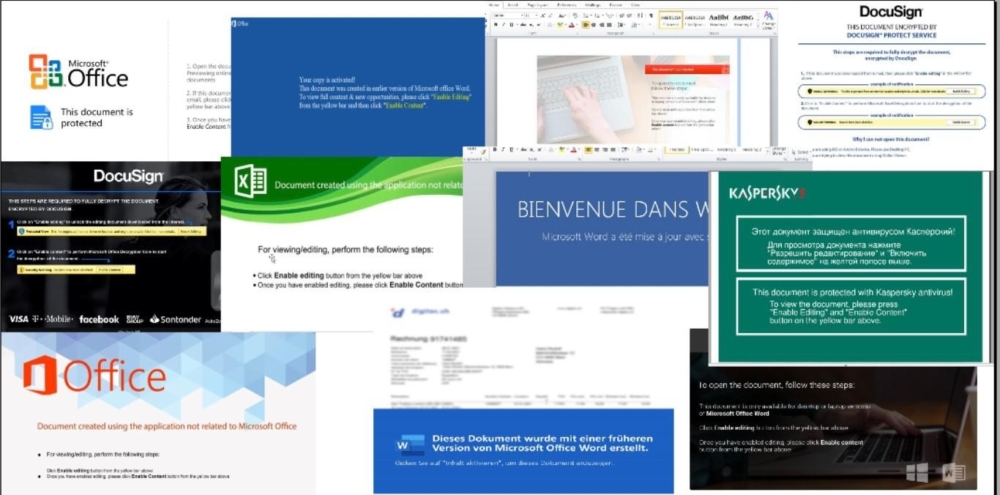
In this blog, we will look at some of the visual honeypots that cybercriminals use, as well as observe different varieties of decoys used for mass phishing or targeted attacks.
Hancitor
The Hancitor downloader has been known since 2013. Using a macro, it loads and runs various payloads. These are usually banking trojans and bots. Periodically, attackers will change the visual bait to bypass and delay detection efforts. A real world example of this occurred in the last month and happens at fairly regular intervals.
It is evident that considerable effort goes into making the new bait look modern and sleek. Increasing perceived credibility and the chances that targets will follow instructions.
Qbot aka QakBot
This bot exists and has been successfully distributed for quite some time, dating back to 2007. Like other campaigns, visual lures change regularly and we will look at a few that have been and/or are currently in use.
IcedID
Banking trojan used by the threat actor TA551. They have been observed active in the wild since 2017, likely prior. In some cases, it is distributed along with a password to decrypt the document. Visual lures also change quite often. Interestingly, it bears similarity to Qbot lures, possibly indicating a connection between the campaigns.
Agent Tesla
The group of cybercriminals behind the spread of this remote access trojan uses an interesting method in choosing a visual lure. In some versions, they deliberately blur the fake document so the user is more likely to click on the content enable button to “view” the document.
Dridex
Dridex is created and used by the TA 550 group. This is a data stealing program that spreads through phishing emails. Threat Actors are constantly using various lures to carry out malicious campaigns.
Very often the documents of dridex pretend to be documents from transport companies.
Emotet
Some time ago, Emotet was the most popular banking trojan for stealing data. Recently however, attackers were able to leverage it to install other malware families as well as ransomware. Most of the malware downloaded by Emotet, normally distributed via phishing emails, leverage Emotet’s infrastructure for higher infection rates. In January 2021, international law enforcement authorities shut down a large amount of servers controlled by the actors, causing the campaign to go dormant until its November resurgence.
Targeted attacks.
What we have discussed above is the distribution of phishing emails sent out on a huge scale every day. Such campaigns can be carried out regularly or in limited intervals. Targeted attacks are carried out with a careful choice of target and bait. In such cases, it is not easy to attribute a group to a particular campaign, the following are examples of such cases.
Some time ago we found an interesting document that loaded Сobalt Strike. They had a very interesting visual lure, which has not yet been encountered in large quantities as with large campaigns.
https://labs.inquest.net/dfi/hash/0a4315aced819ab564058480ffeeeb059756030d8c056605f2e0c6fc88b8b2f5
Some visual decoys are written in the language of the victim so that the likelihood of opening the file and activating macros is heightened. The following sample, tailored for a French target, is a prime example.
https://labs.inquest.net/dfi/hash/f970630a41a2e8fe61fa3f2cf69dff87ac3fb272d006d6af866ca17264b14ff3
https://labs.inquest.net/dfi/hash/5724843c6427901c55203478455e817c7cac07dd56f19649824554dd35b20b3f
The following is another document used in the targeted attack whose payload was also Cobalt Strike.
SHA256 – 5d3220db34868fc98137b7dfb3a6ee47db386f145b534fb4a13ef5e0b5df9268
SHA256 – d063c3938bb3ce3a0fe0c5492b7a8fe072524db87606b071152958e795501f7f
SHA256 – 0dde111712db81b5a70d9cf35f5e1fcd5d585c62f678a5db66d2a166ef3a3399
SHA56 – 20fe5a152878e31a0bab6102a8c265f8e4e0309a4cbd1d03cba00ddb22bc1633
APT Actors
The tools used by APT actors are very often fundamentally different from those used for phishing. The fact is that APT campaigns are focused on striking covertly with specific goals in mind. Very often, documents used in APT campaigns mimic or leverage internal government documents, reports and bulletins.
Often, malicious payloads are embedded within documents primed for target emails rather than retrieved as seen in other campaigns. We’ll look at a few examples.
https://labs.inquest.net/dfi/hash/3b548a851fb889d3cc84243eb8ce9cbf8a857c7d725a24408934c0d8342d5811
https://labs.inquest.net/dfi/hash/1dd03c4ea4d630a59f73e053d705185e27e2e2545dd9caedb26a824ac5d11466
https://labs.inquest.net/dfi/hash/2bf088955007b4f47fe9187affe65fffea234ff16596313a74958a7c85129172
https://labs.inquest.net/dfi/hash/713a10d7b50b534c7249d02c74ef3342338948e4d98d7e11371d03b6cfbdc43a
SHA256 – cad6611f90ce66e74418e47e45203e5771e61c57f49e27e8278a03165de741fe
It would be quite daunting to comprehensively cover the lures in the wild within this blog. However, we have a great collection of such lures within the Malware Lures Gallery.
Conclusion.
Visual lures used in malicious documents are aimed at making users open the document and enable the execution of macros. Another goal is to hide malicious activity and create the impression of a legitimate document that the user is likely to interact with.
These simple rules will help mitigate the risk of falling prey to threat actors.
- Always update your operating system and Office.
- Never click “Enable Content”.
- Never open suspicious documents.
- Never use pirated software.
- Take care of the cybersecurity of your enterprise.
You can familiarize yourself with the InQuest DFI Platform and SaaS Email Security Solution
References:
Hancitor
https://inquest.net/blog/2021/04/16/unearthing-hancitor-infrastructure
https://malpedia.caad.fkie.fraunhofer.de/details/win.hancitor
Qbot
https://inquest.net/blog/2021/10/19/advanced-qbot-downloader
https://malpedia.caad.fkie.fraunhofer.de/details/win.qakbots
IceID
https://inquest.net/blog/2021/07/19/icedid-070721
https://malpedia.caad.fkie.fraunhofer.de/details/win.icedid
Agent Tesla
https://inquest.net/blog/2021/11/02/adults-only-malware-lures
https://inquest.net/blog/2021/06/28/magnificence-agent-tesla
Targeted Attacks.
https://inquest.net/blog/2021/05/26/pschain
https://inquest.net/blog/2021/05/11/dive-cobalt-strike
APT Attacks.
https://www.sentinelone.com/labs/a-deep-dive-into-zebrocys-dropper-docs/
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge for 30 days.