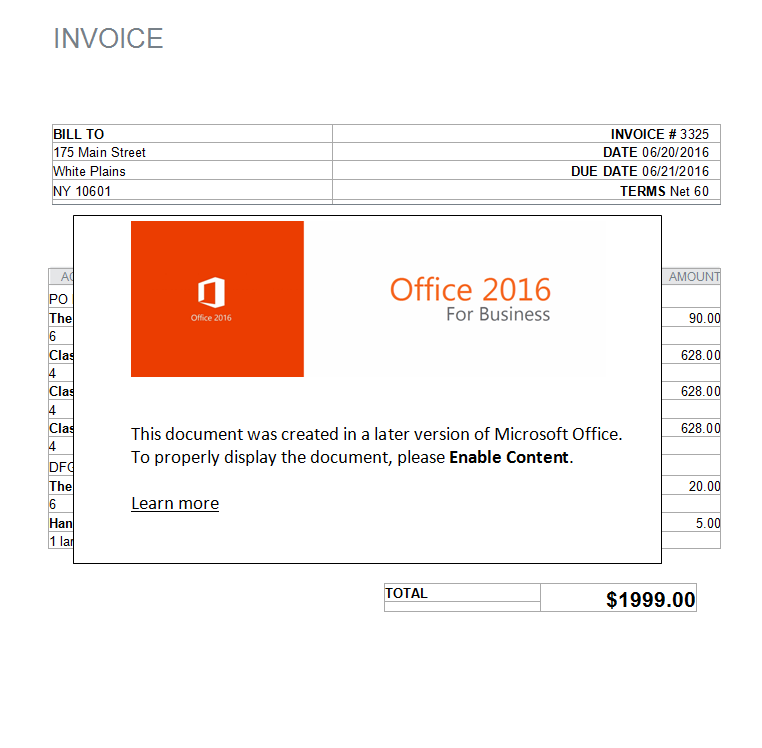
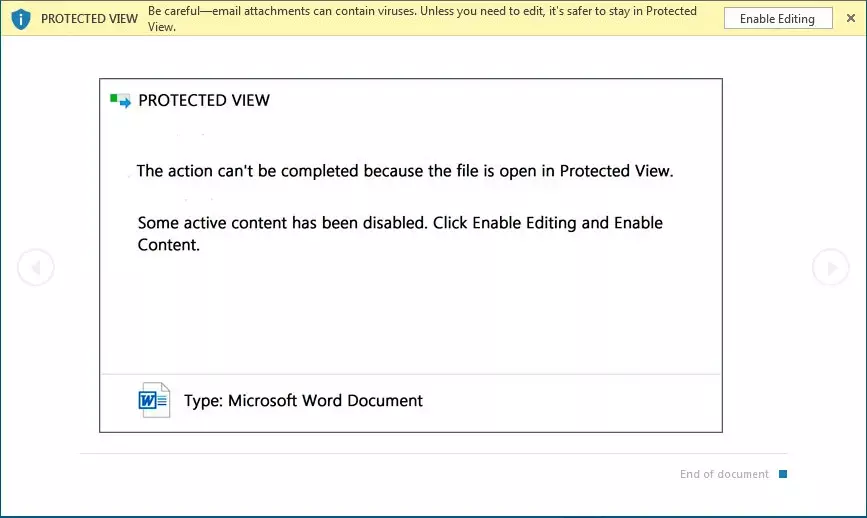
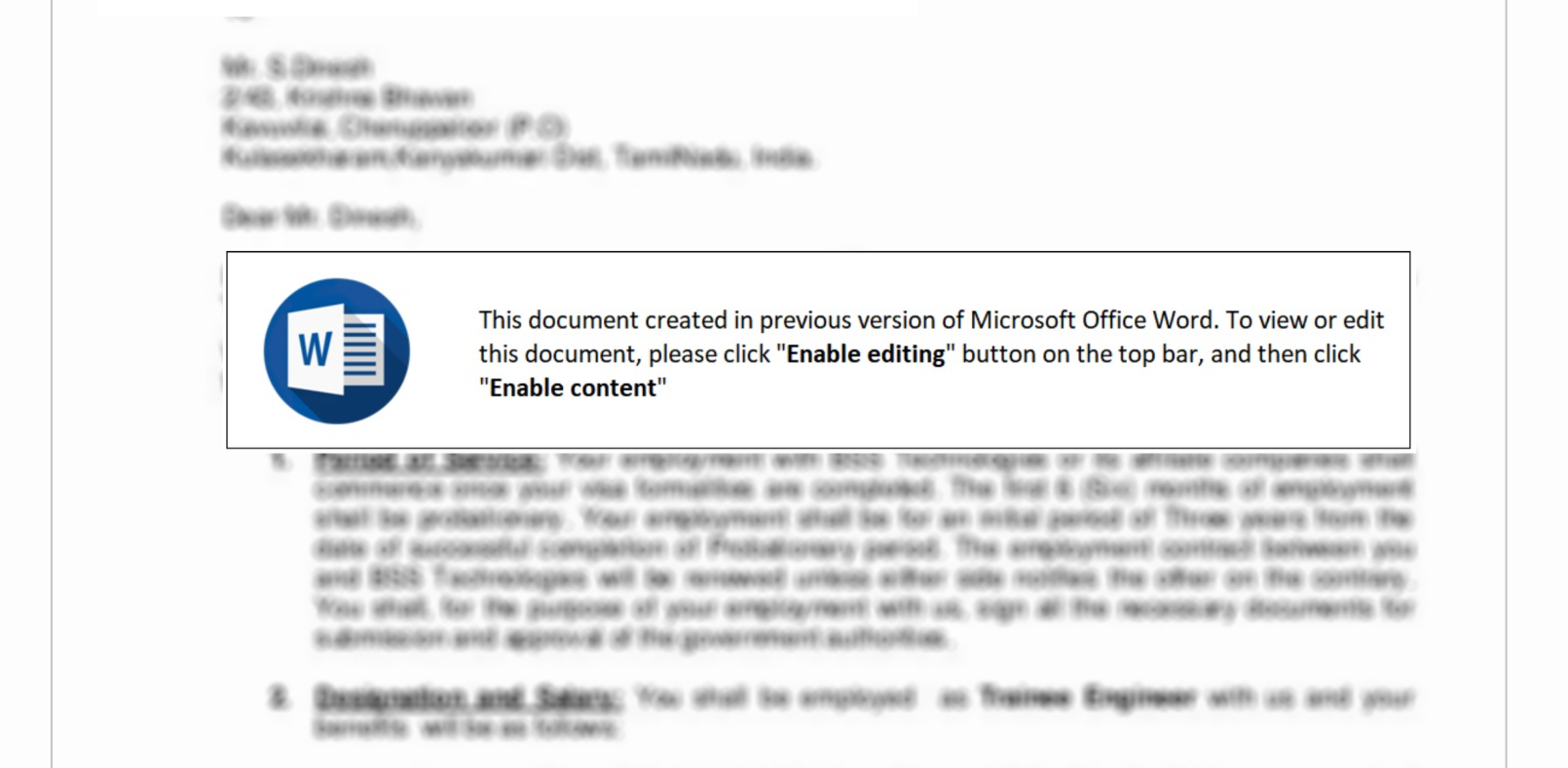
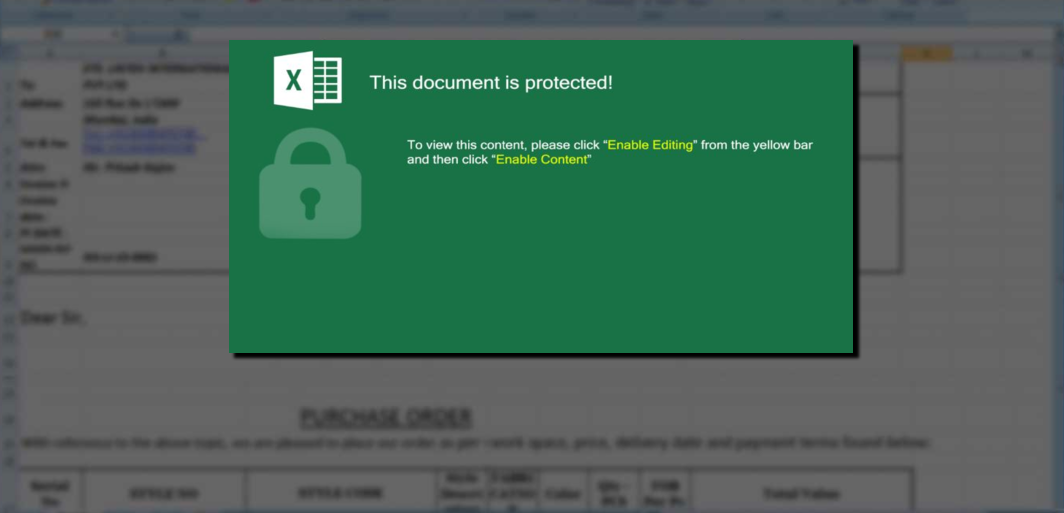
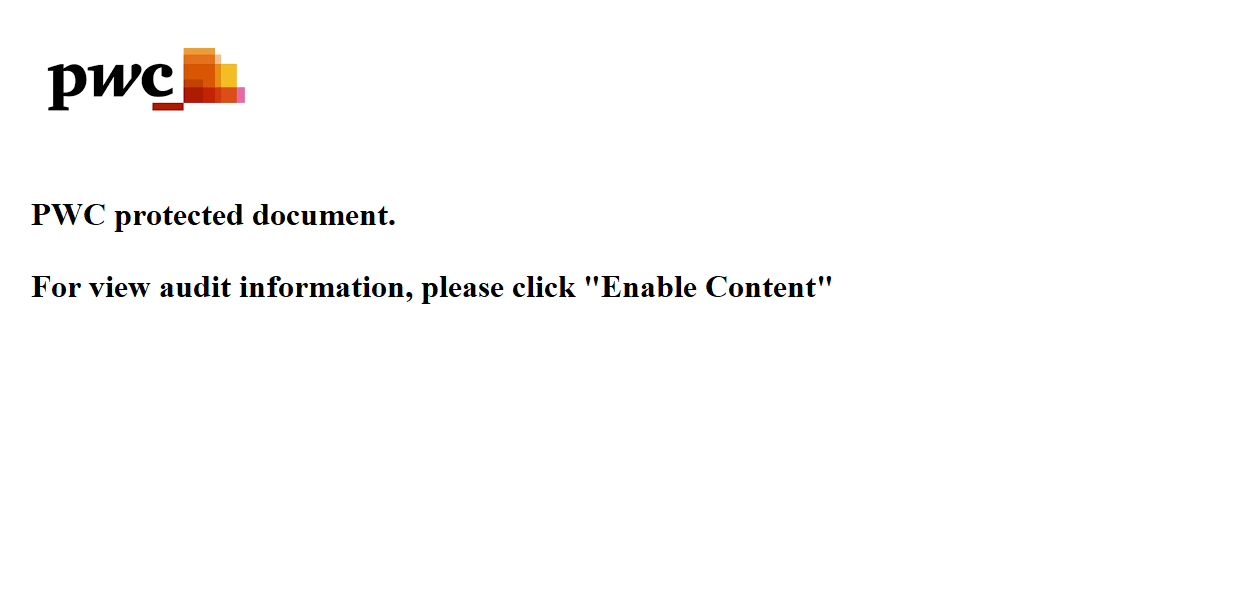
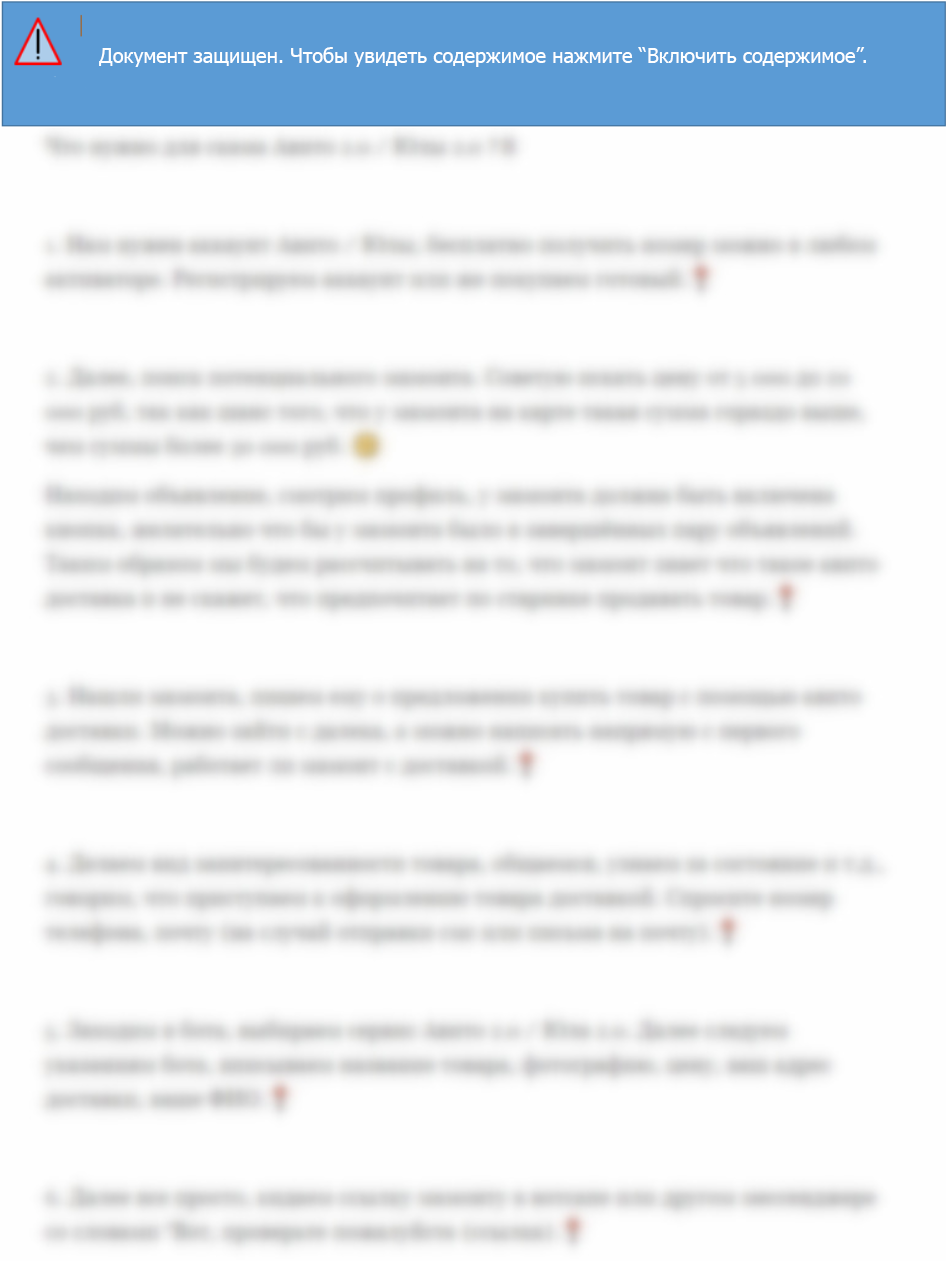
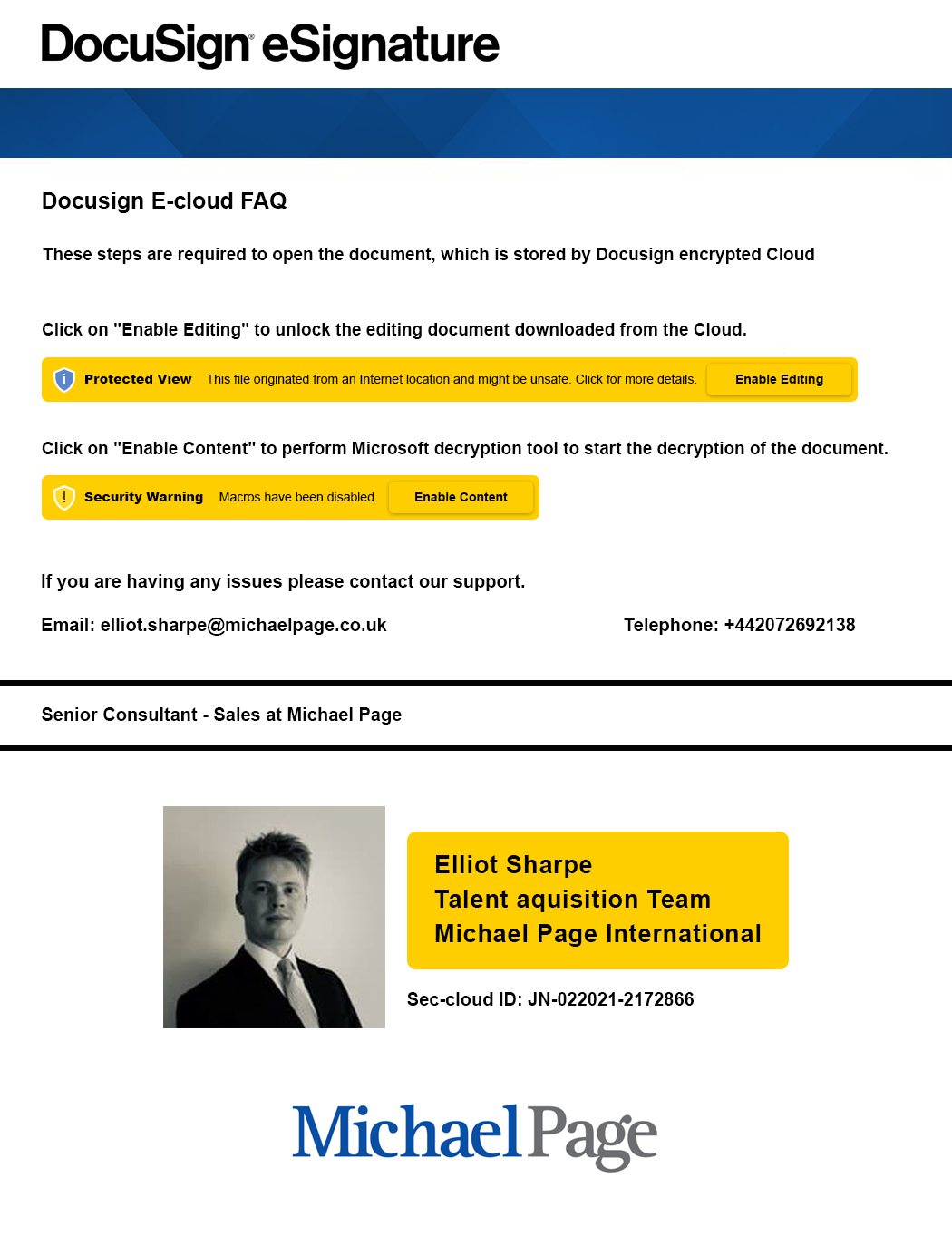
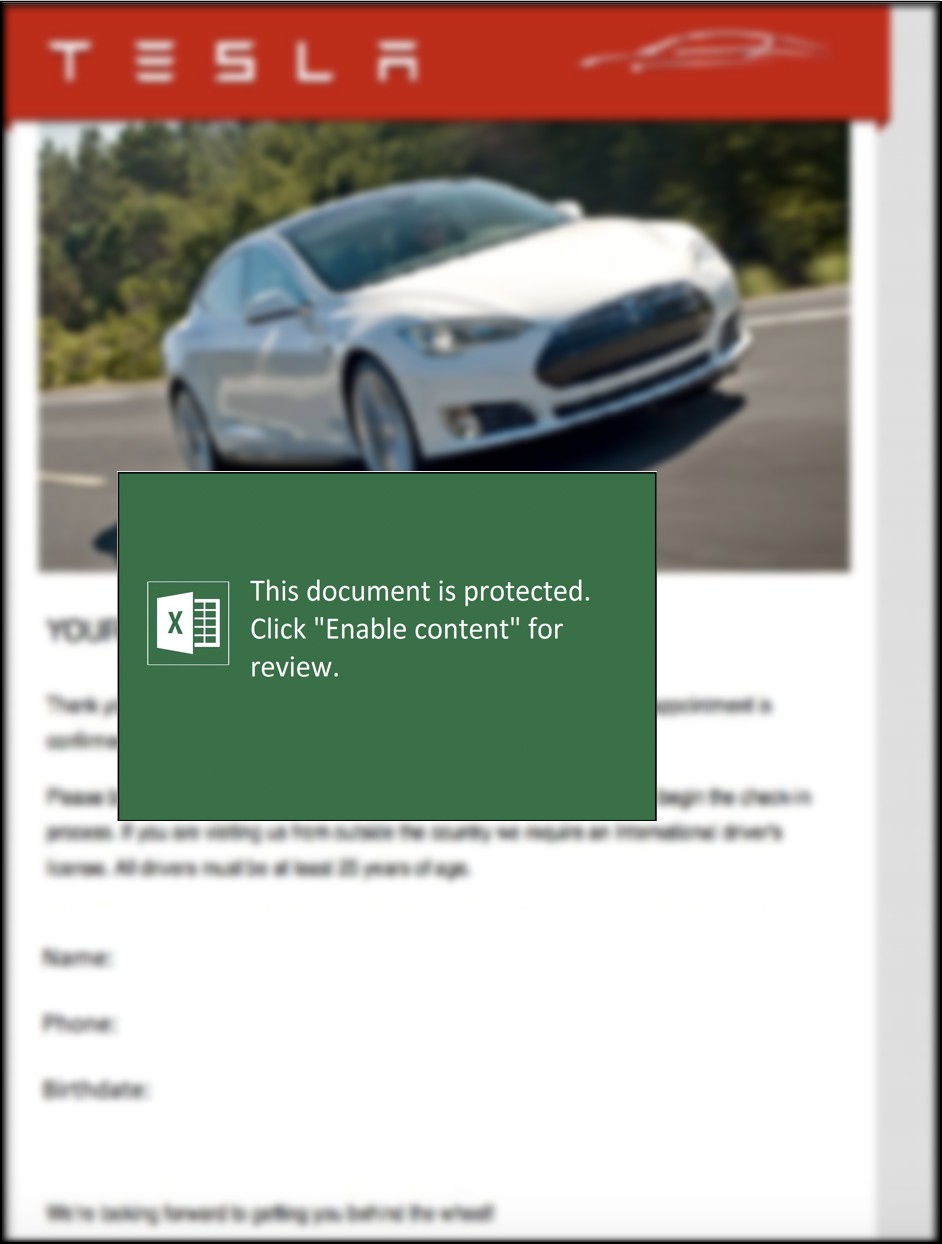
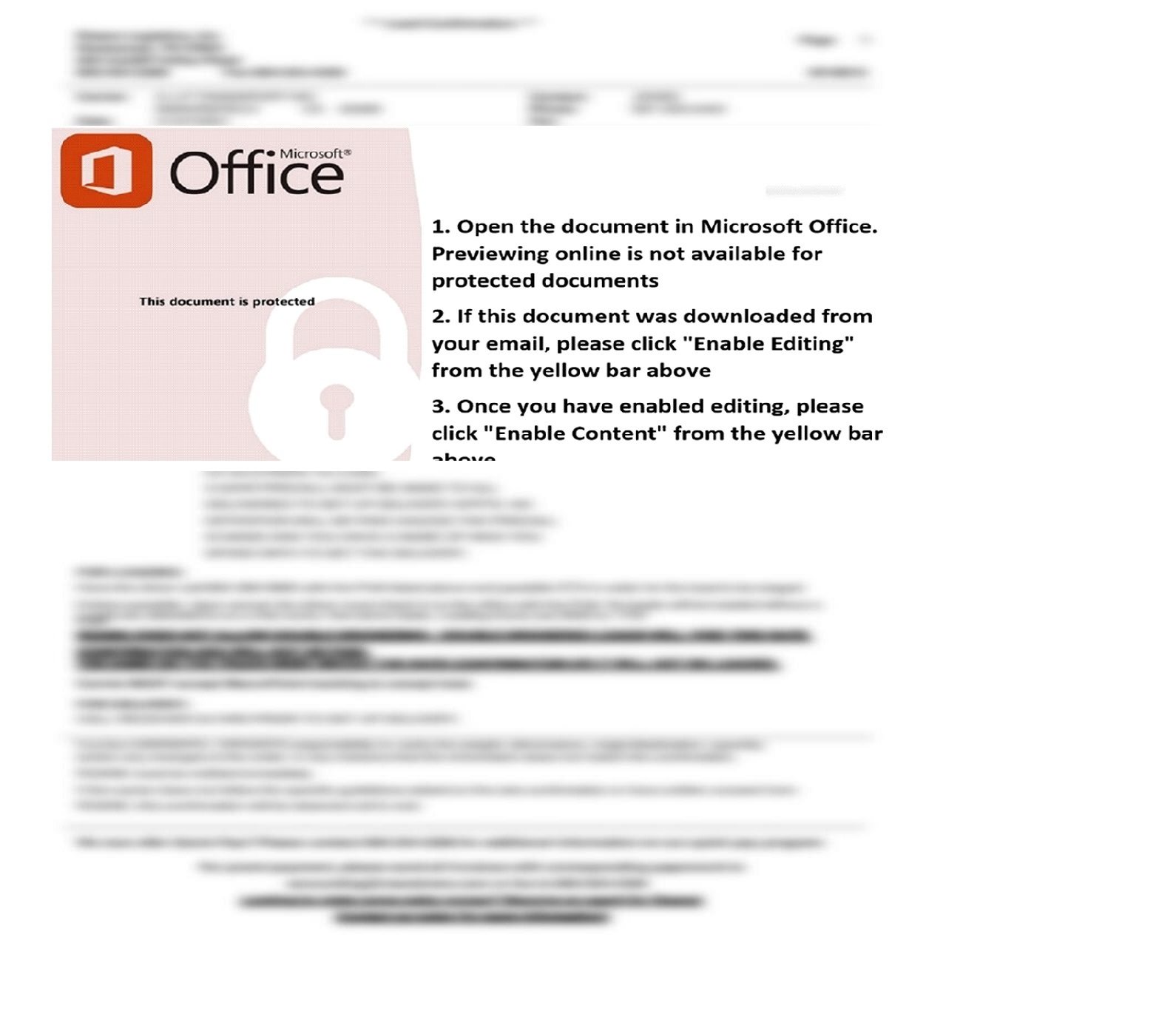
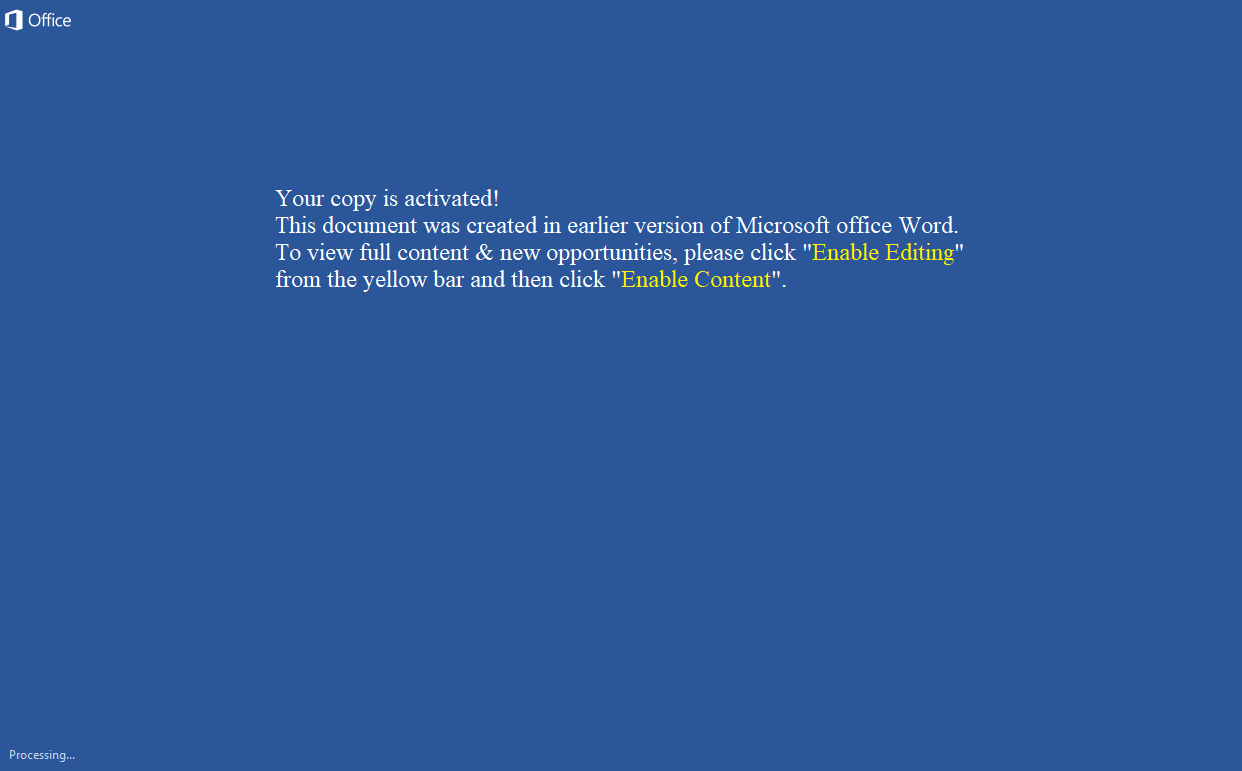
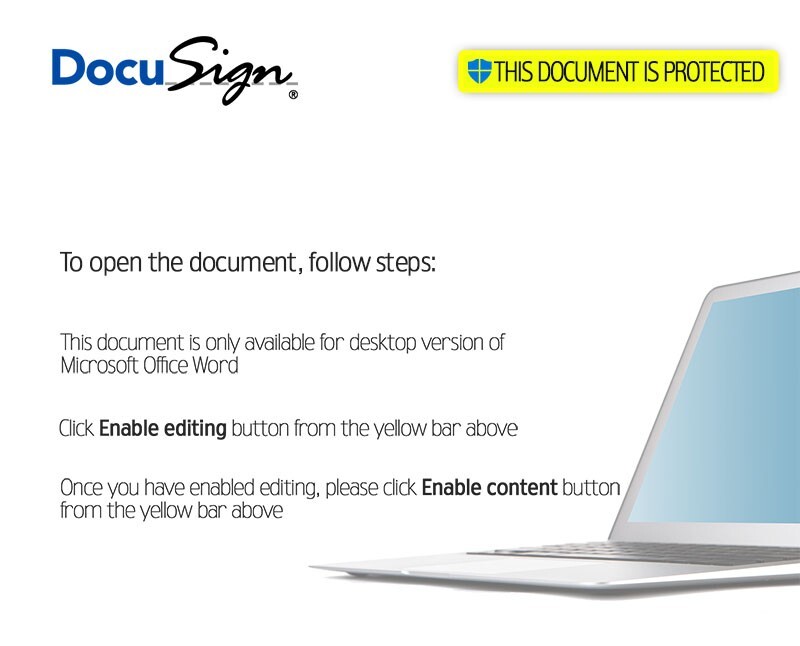
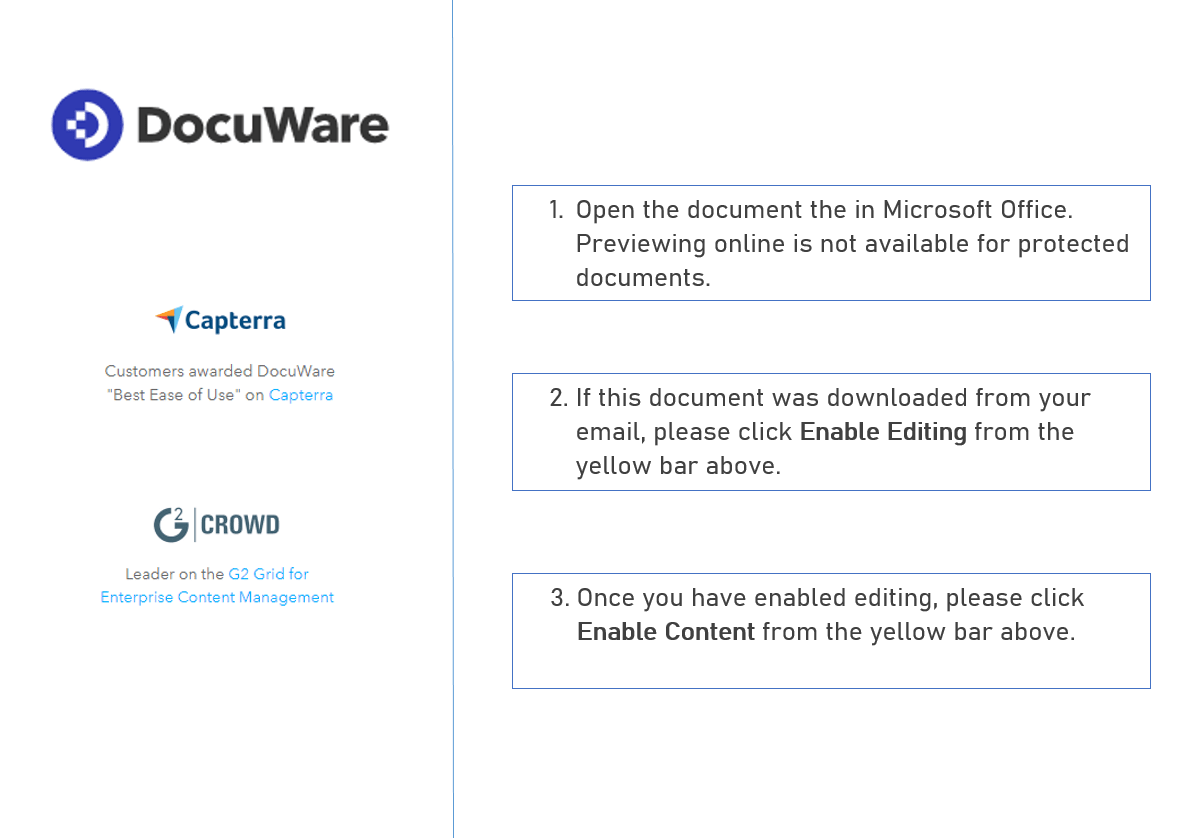
Malware Lures Gallery
It’s no secret that client-side attacks are a common source of compromise for many organizations. Web browser and e-mail borne malware campaigns target users by way of phishing, social engineering, and exploitation. Office suites from vendors such as Adobe and Microsoft are ubiquitous and provide a rich and ever-changing attack surface. Poor user awareness and clever social engineering tactics frequently result in users consenting to the execution of malicious embedded logic such as macros, JavaScript, ActionScript, and Java applets.
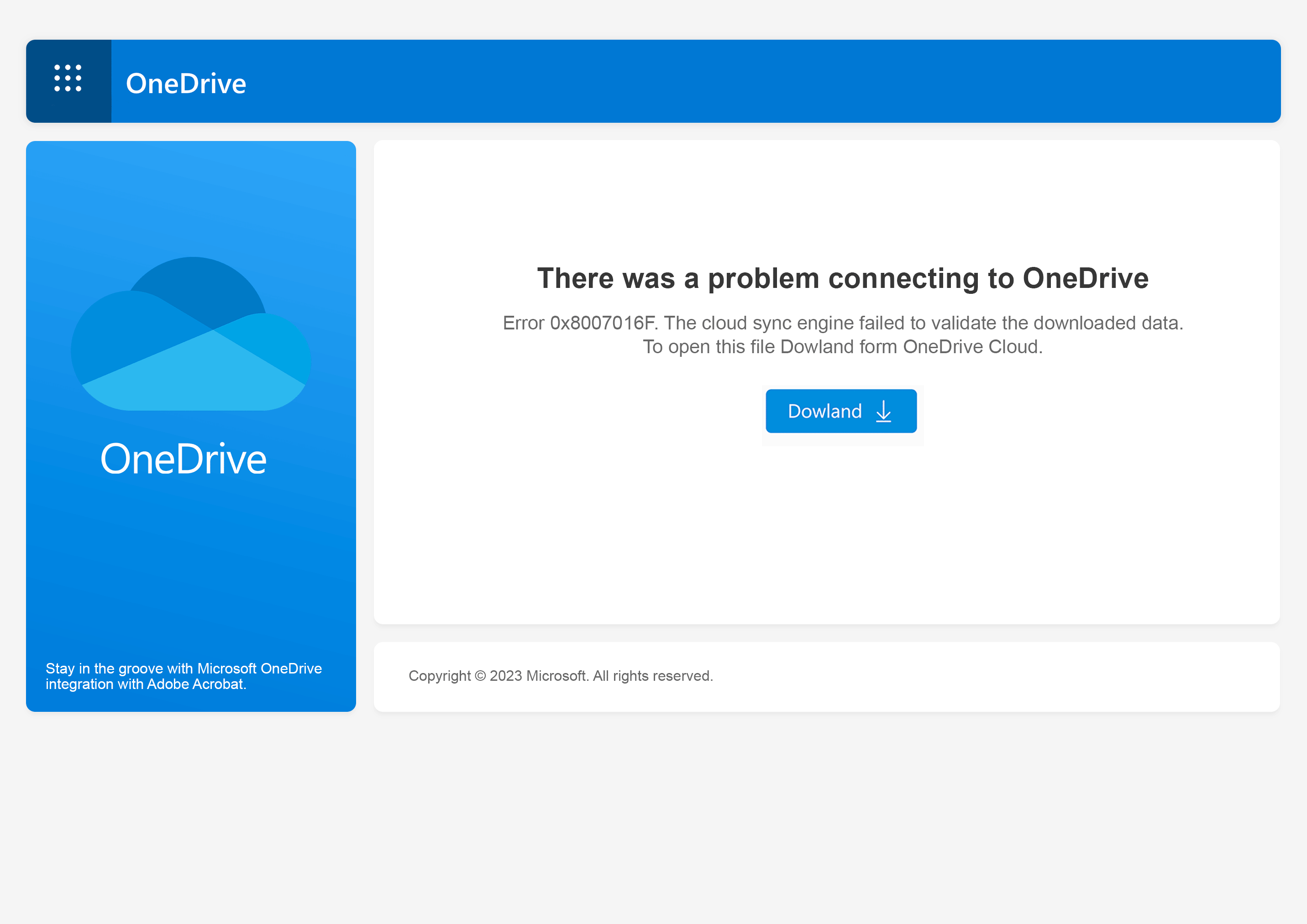
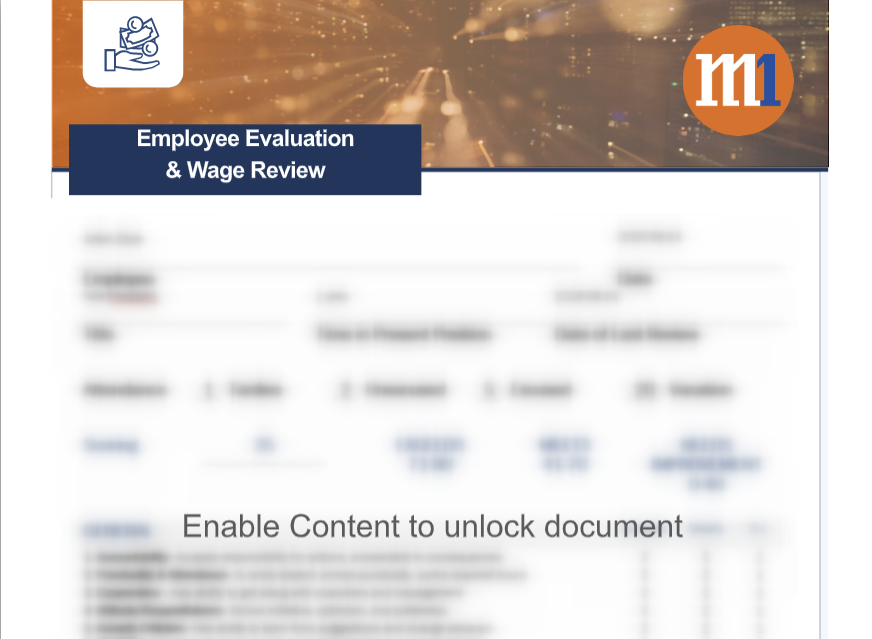
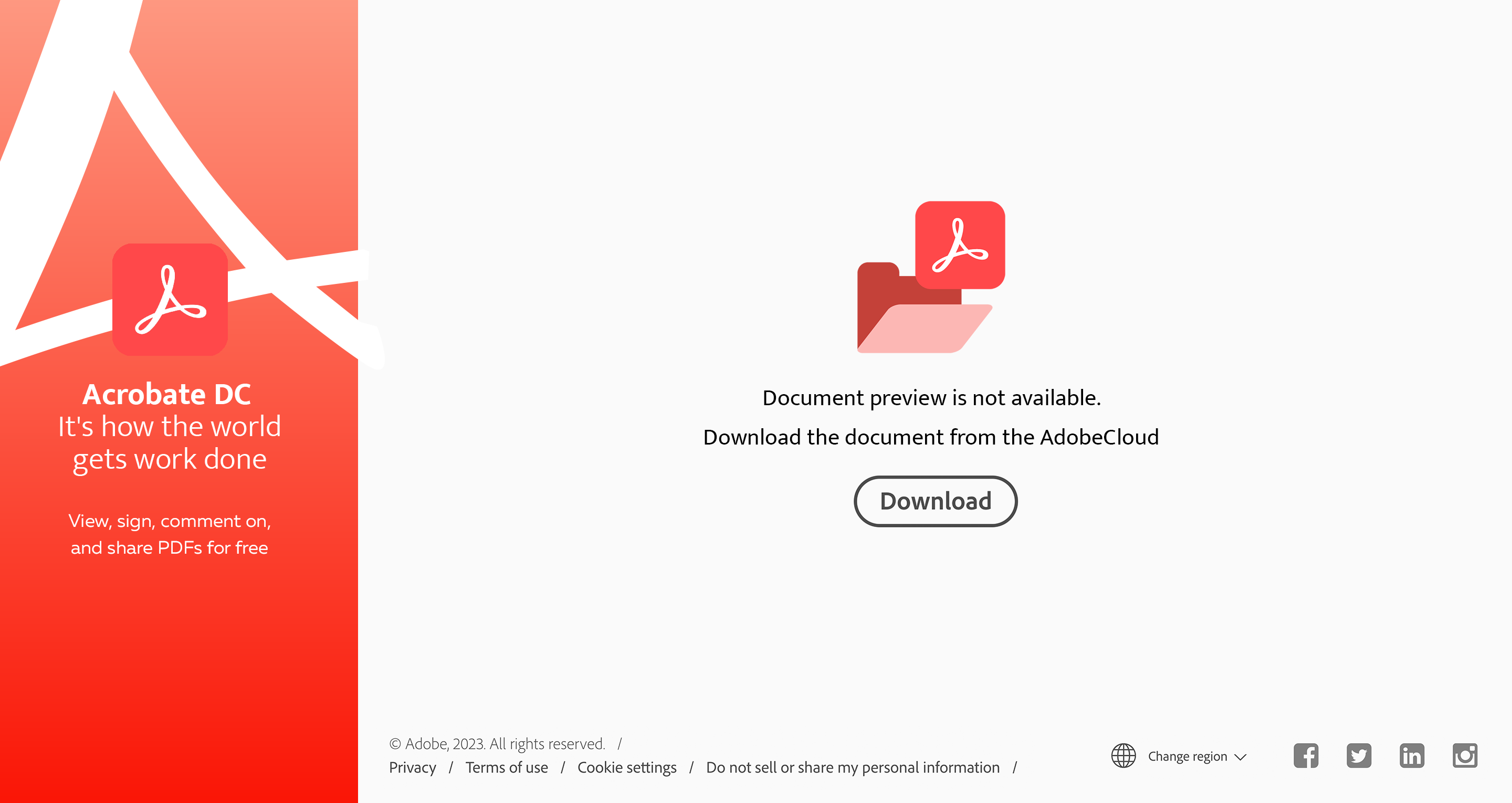
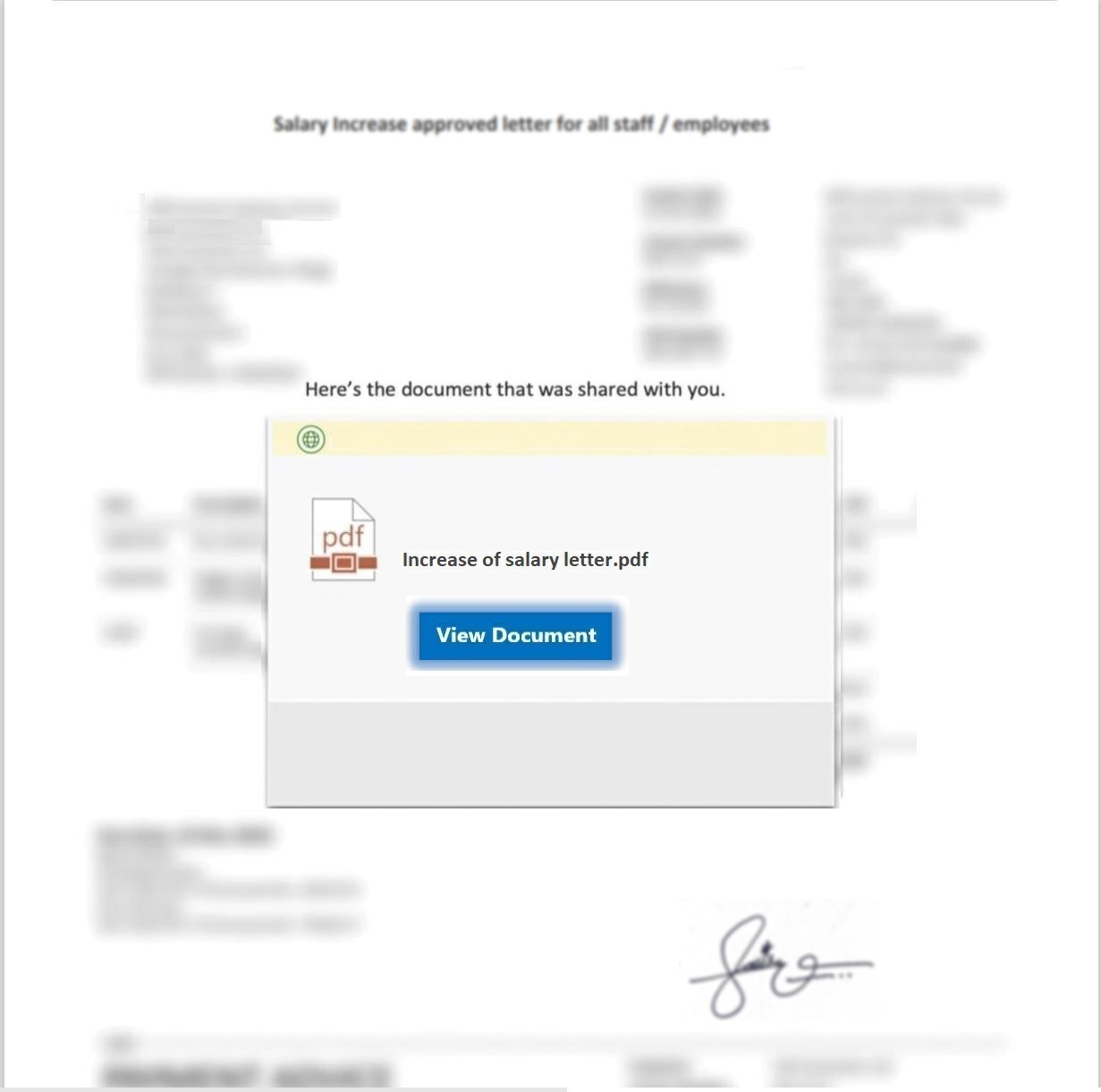
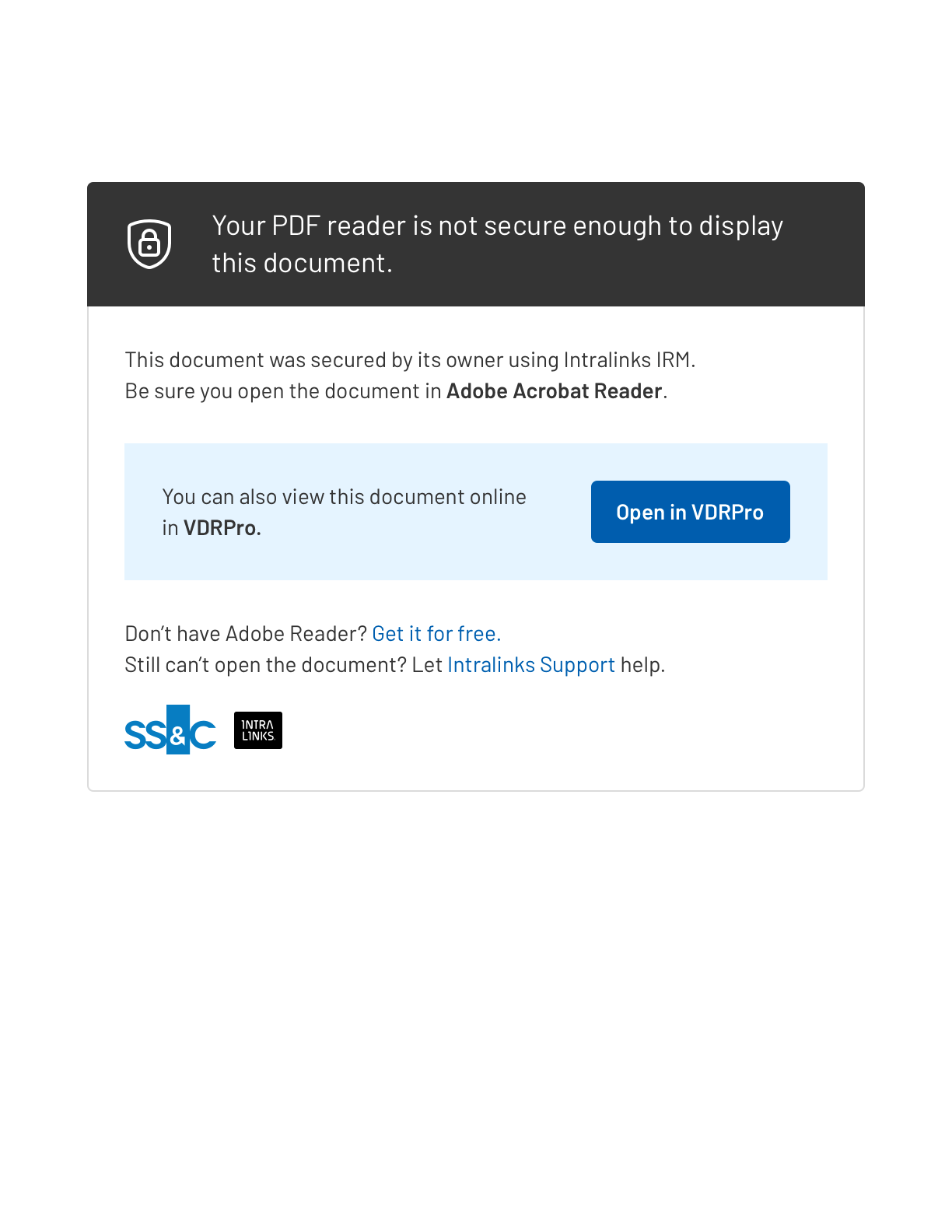
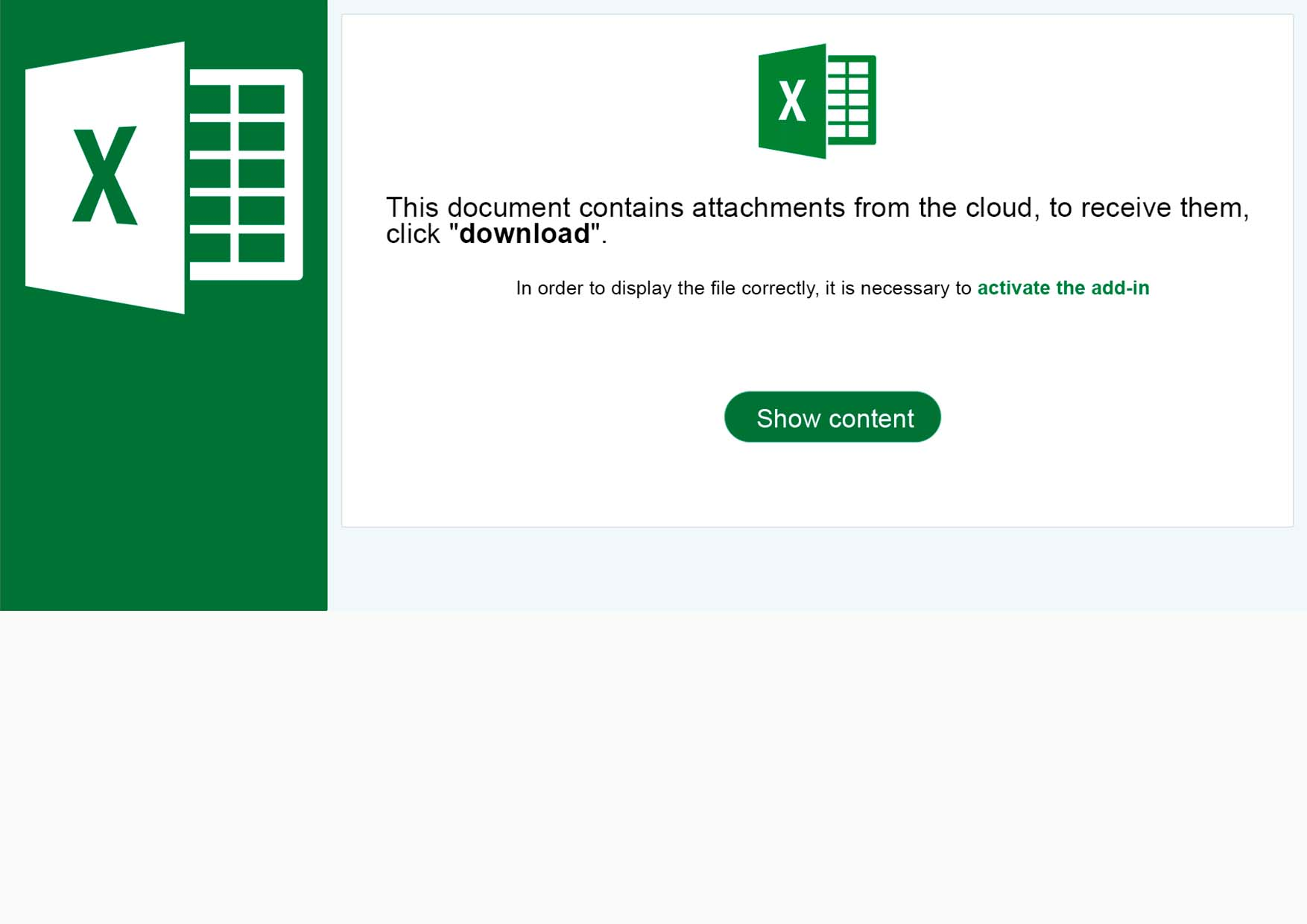
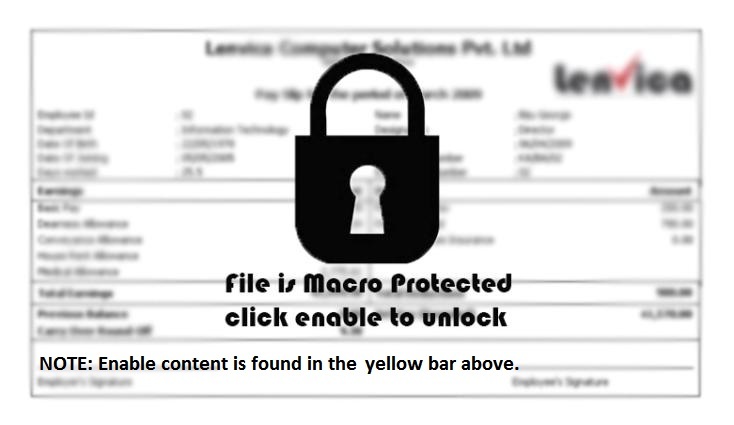
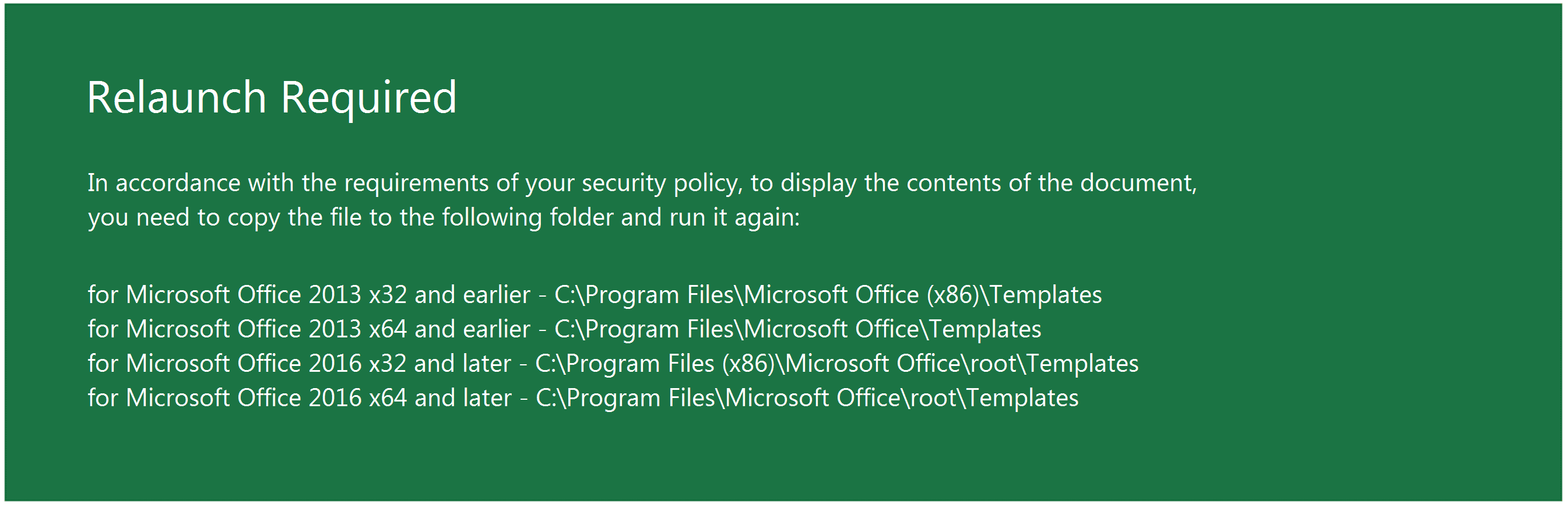
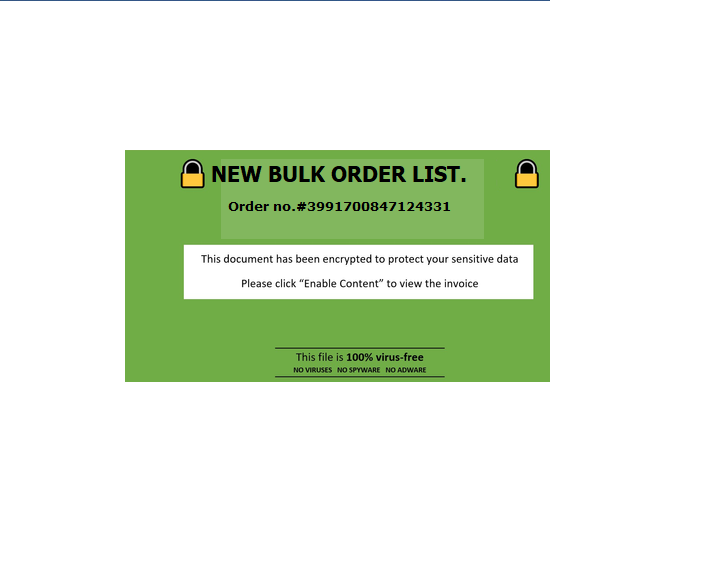
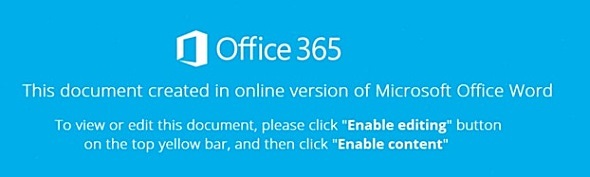
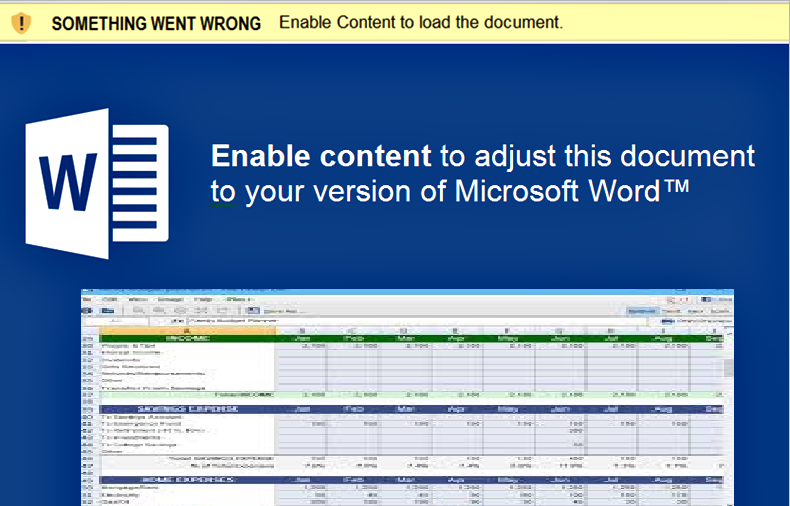
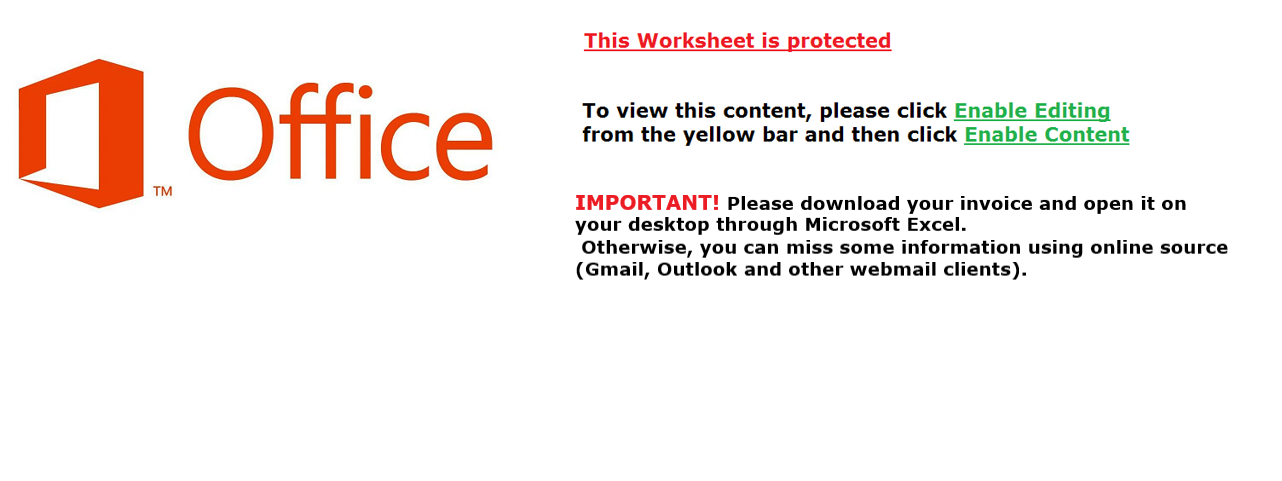
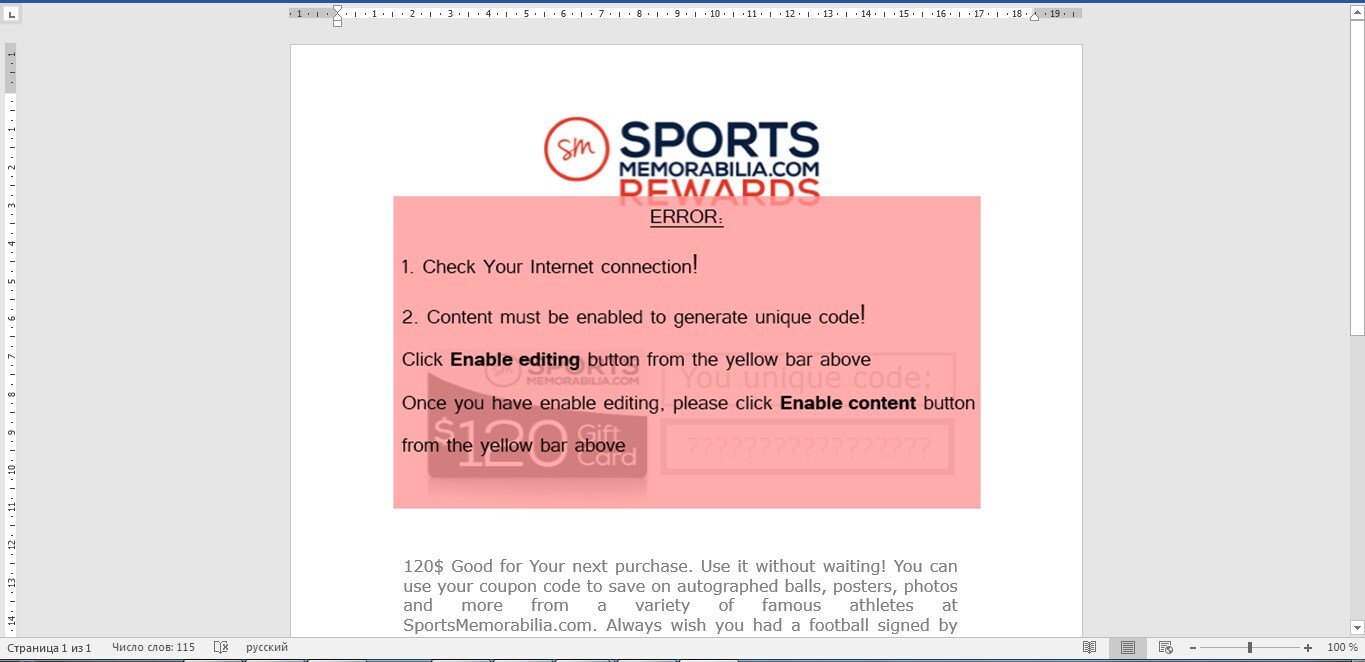
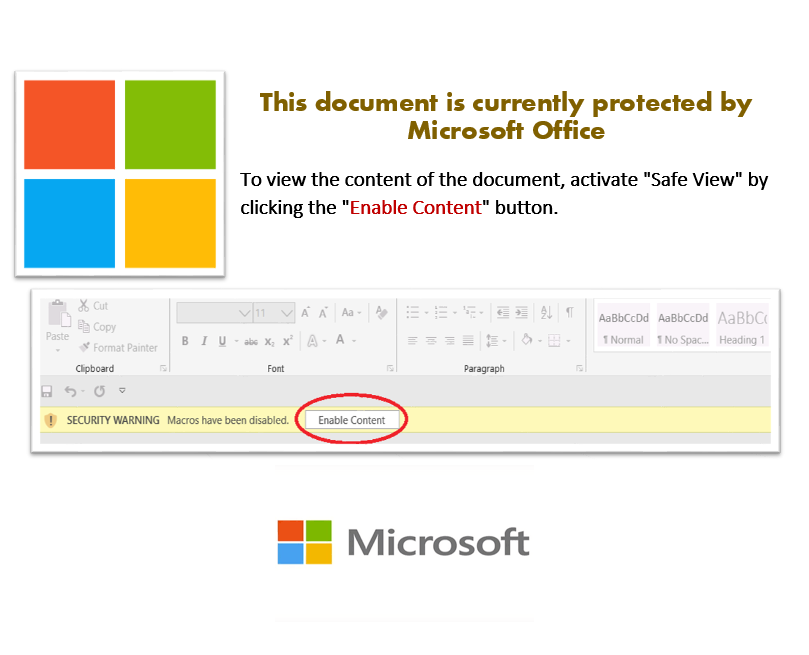
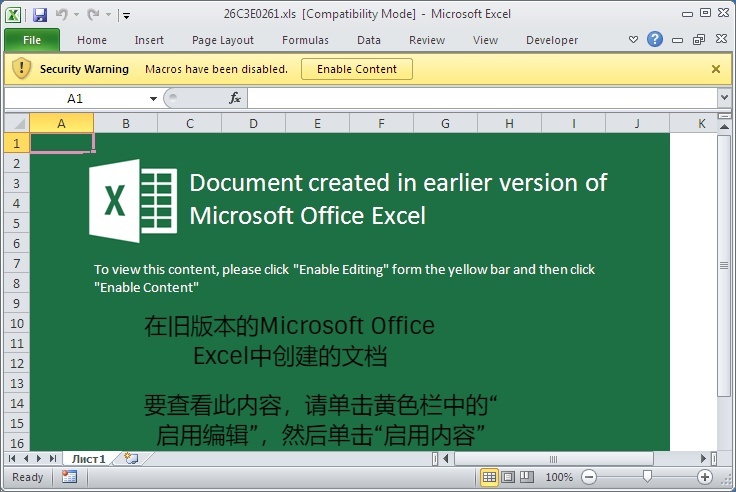
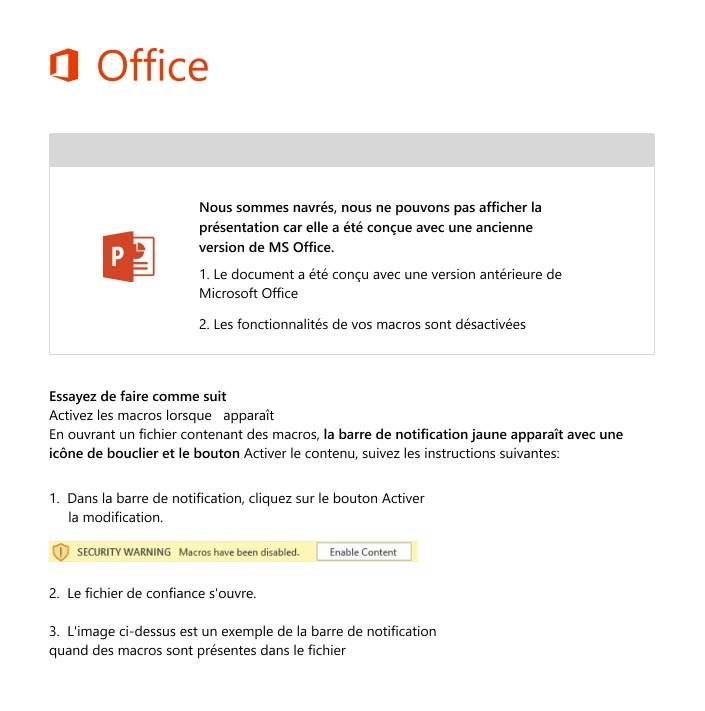
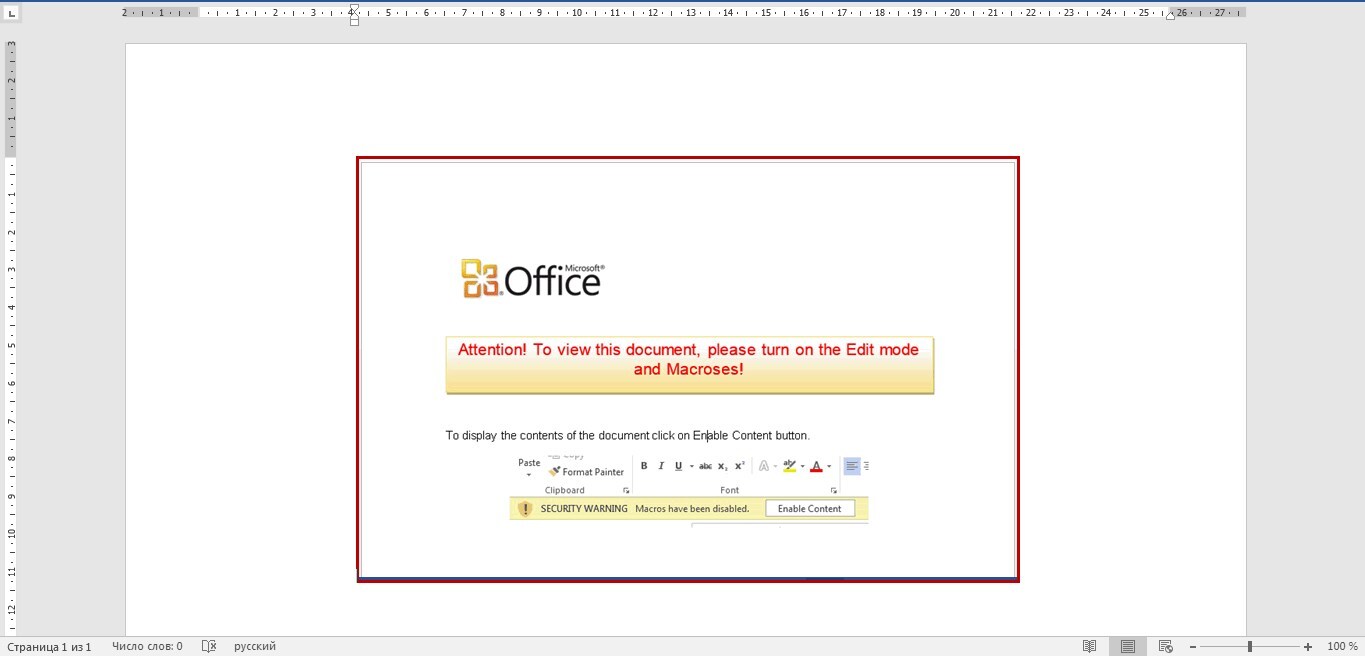
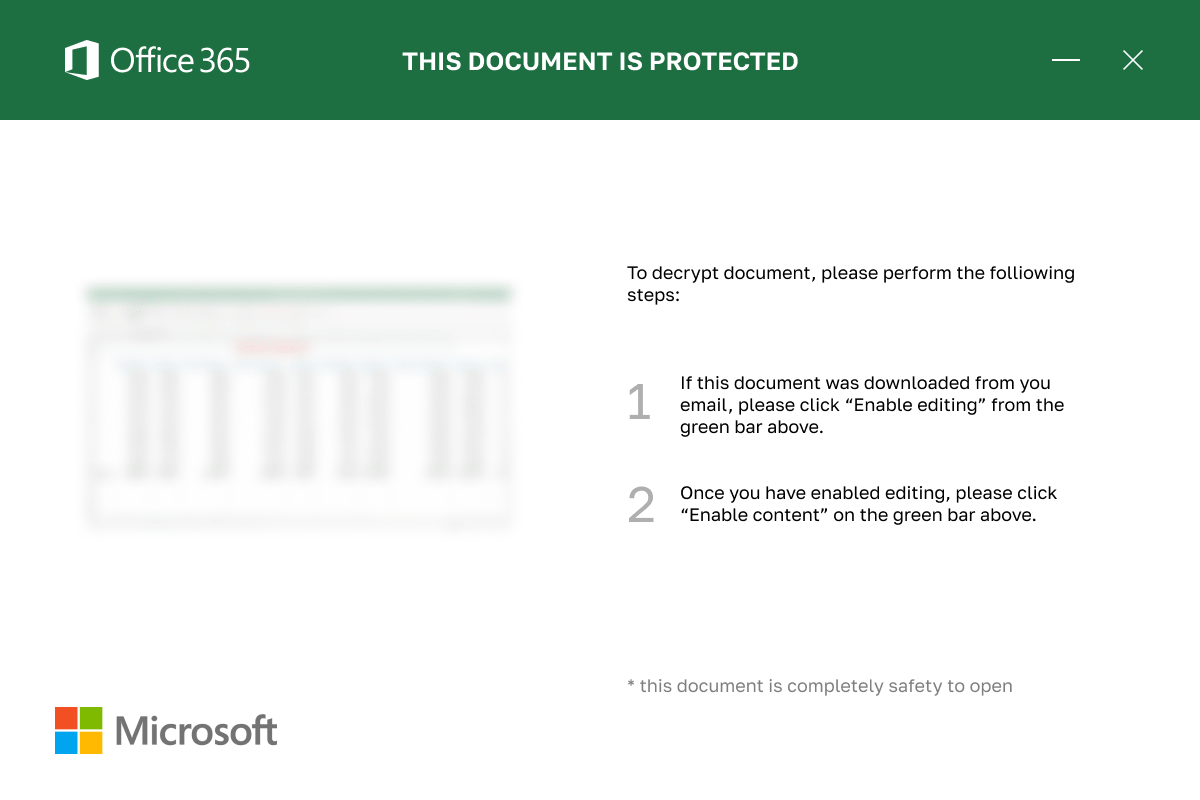
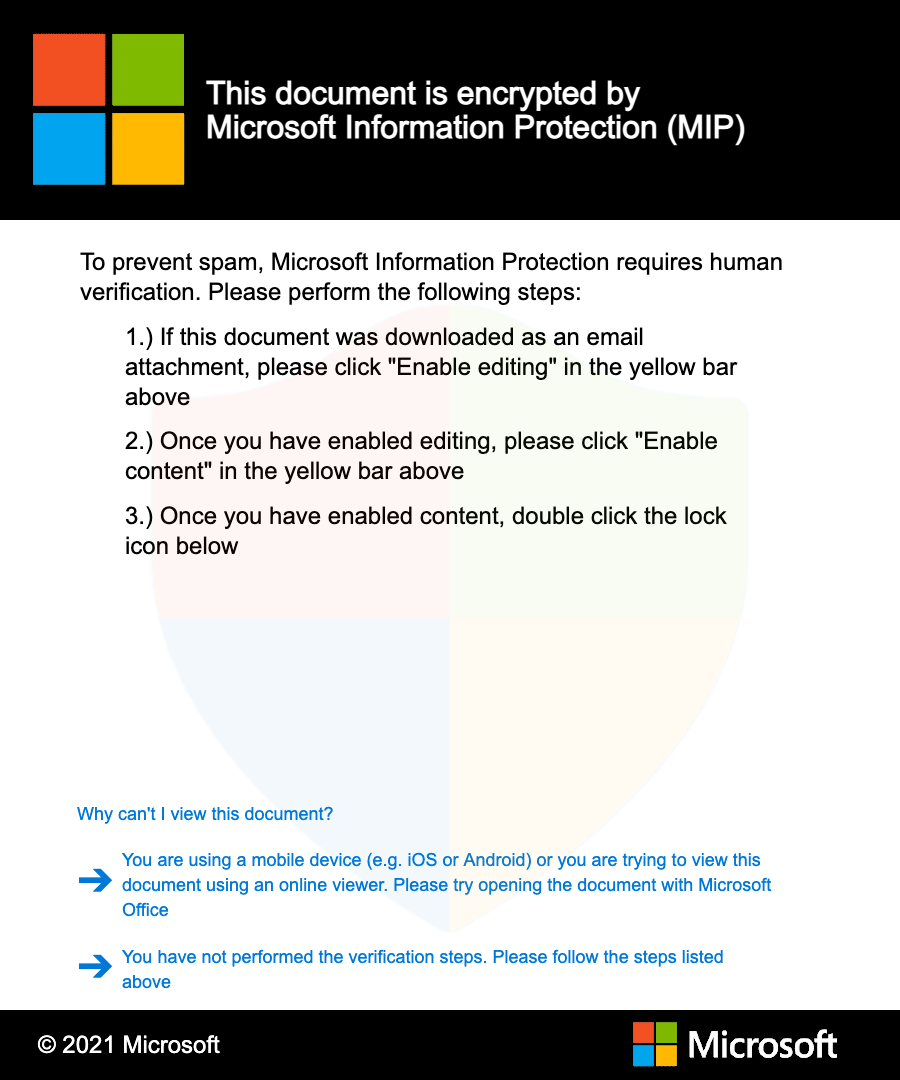
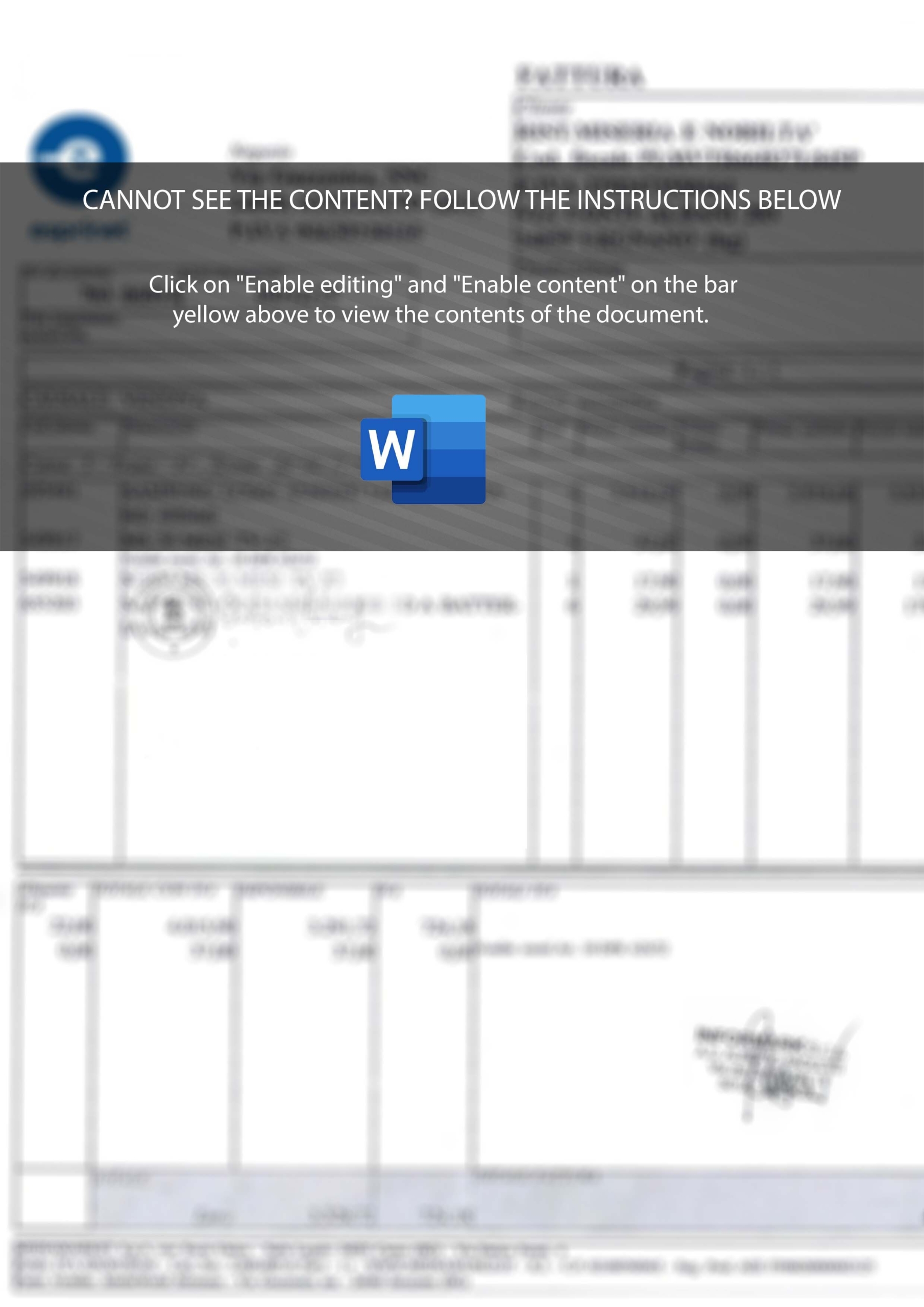
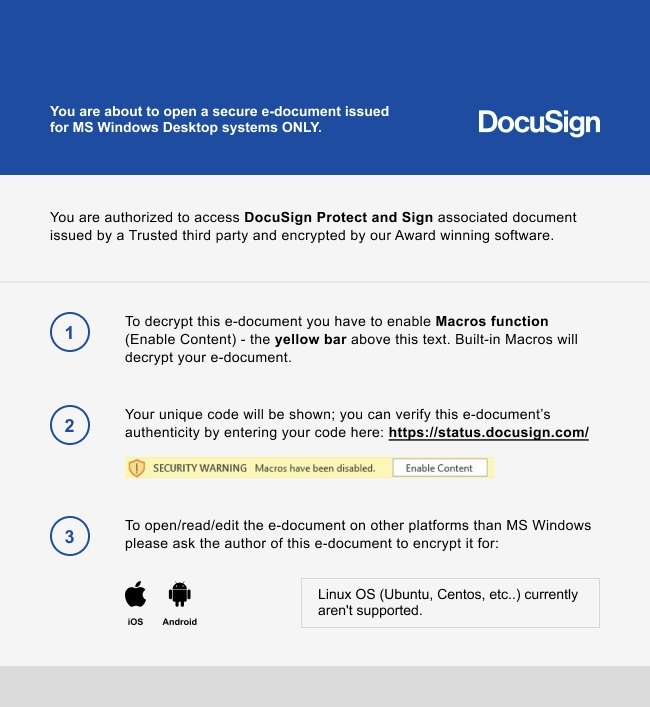
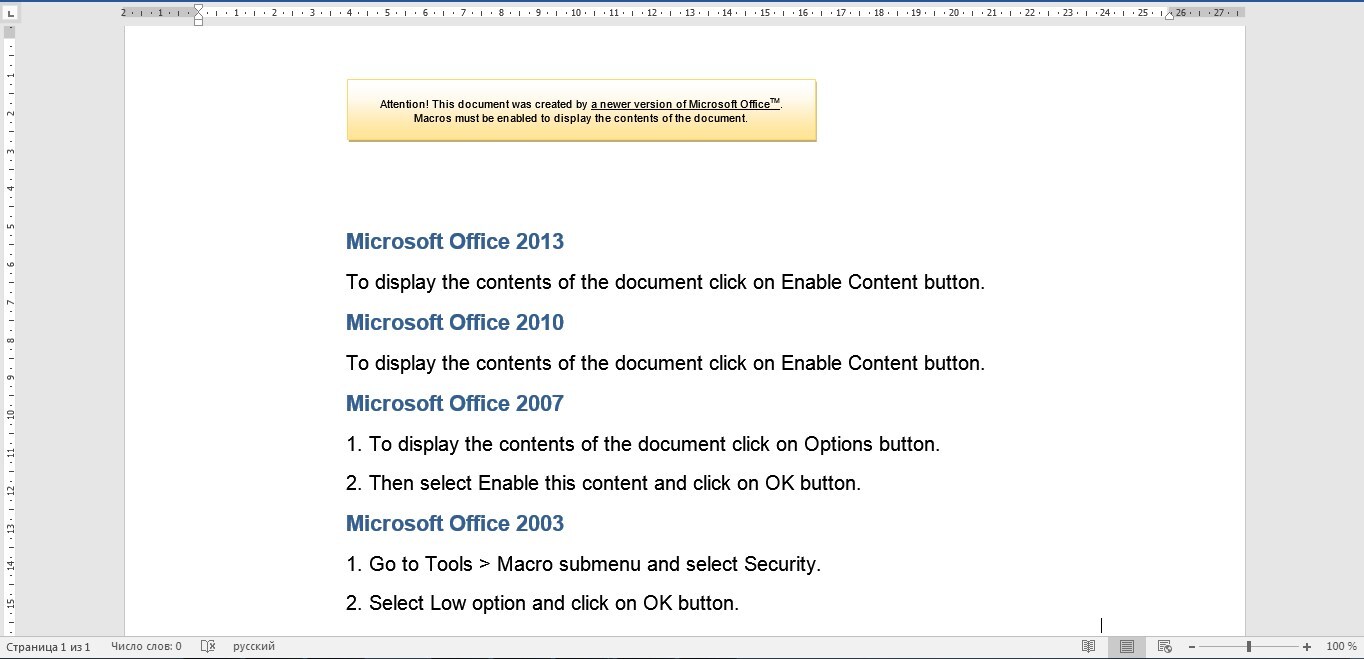
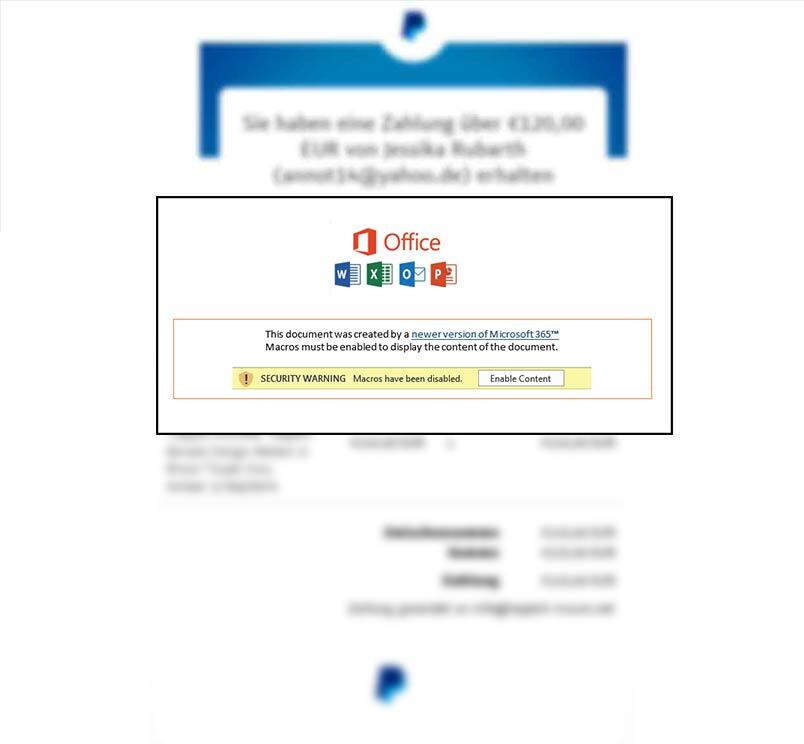
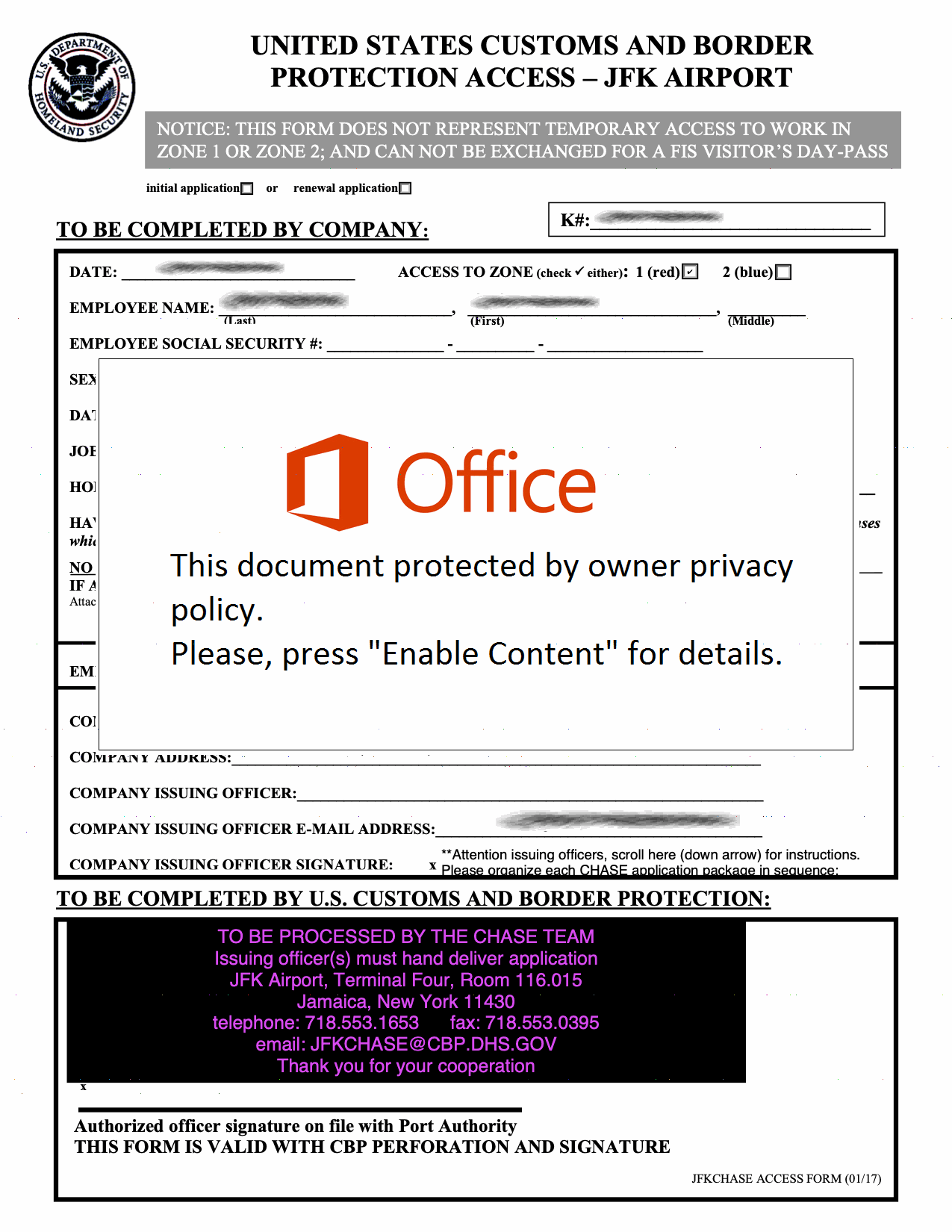
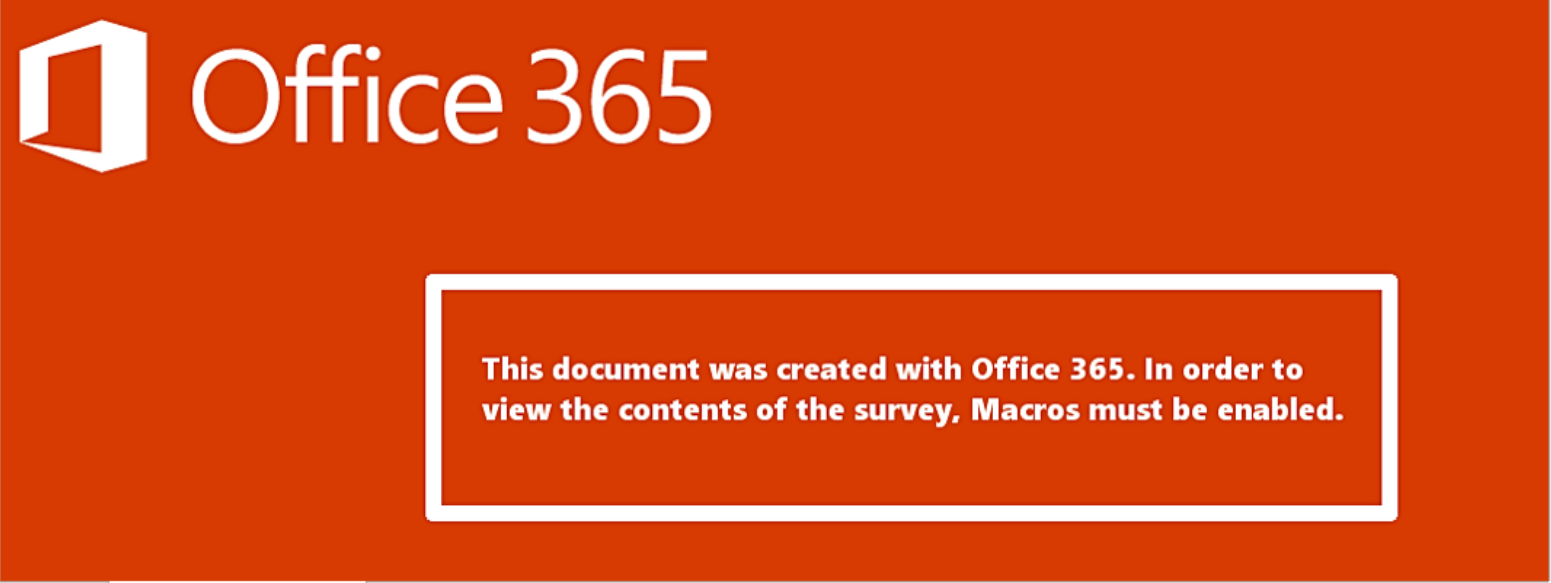
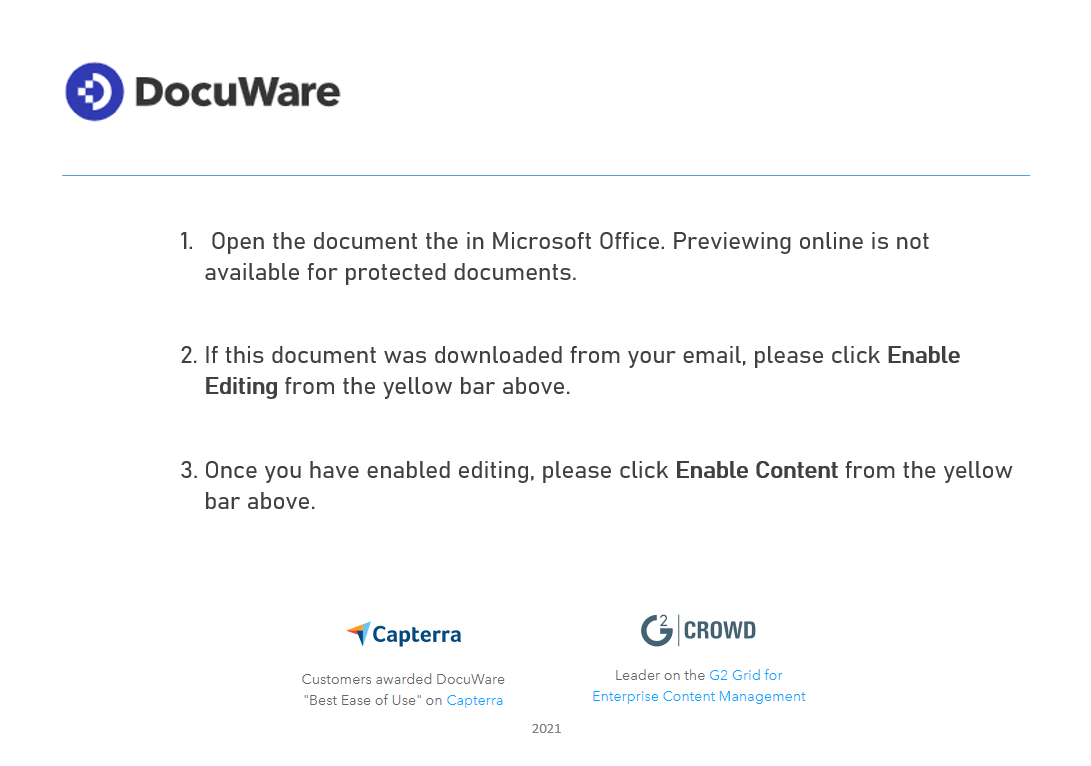
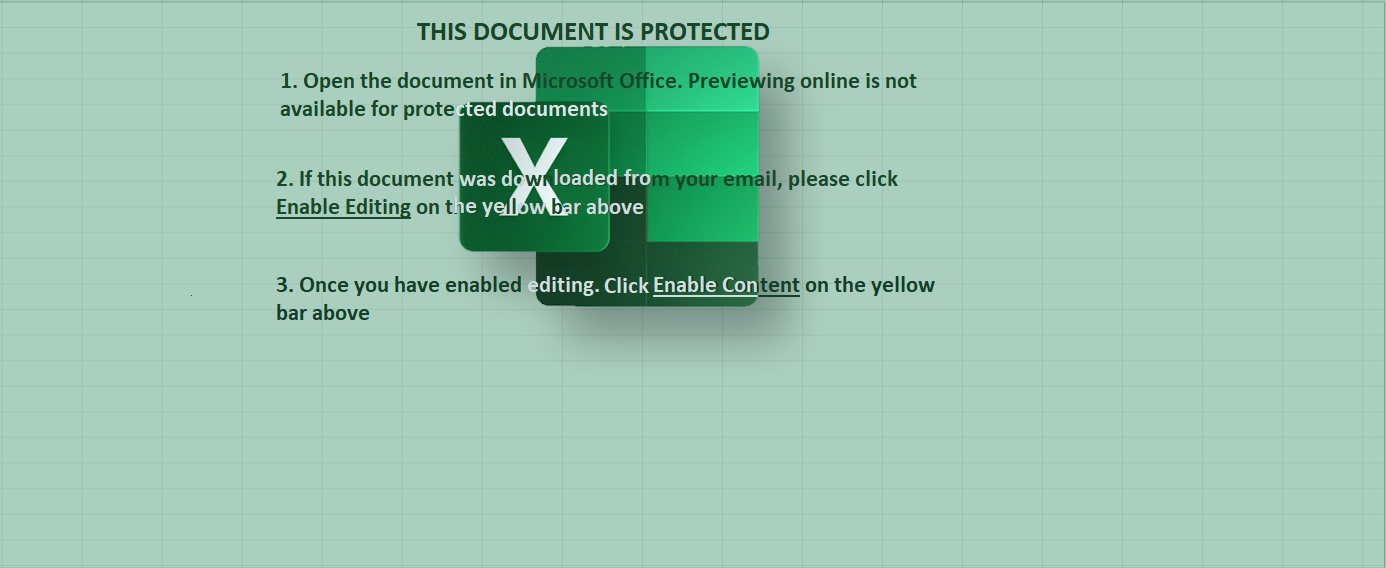
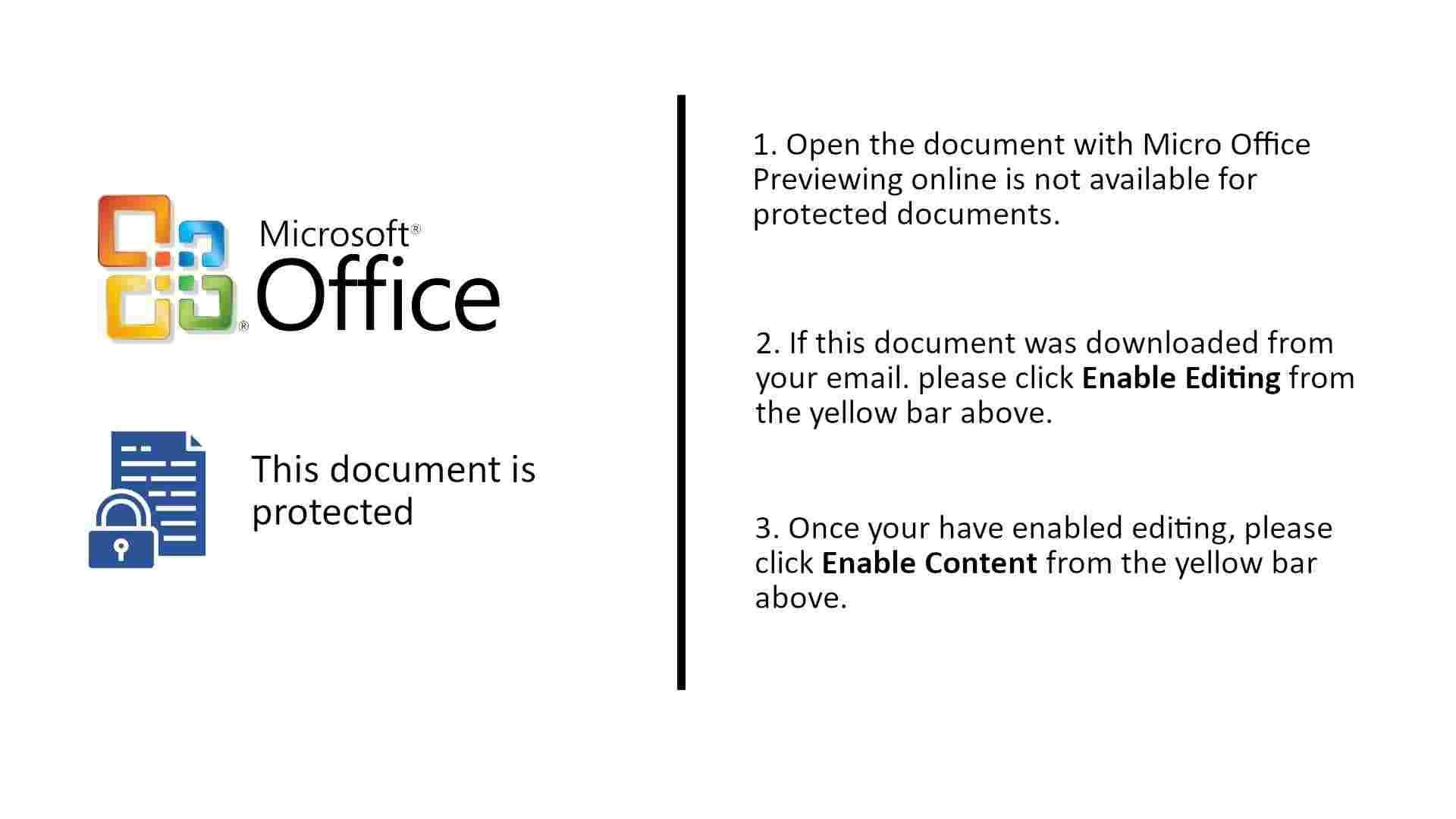
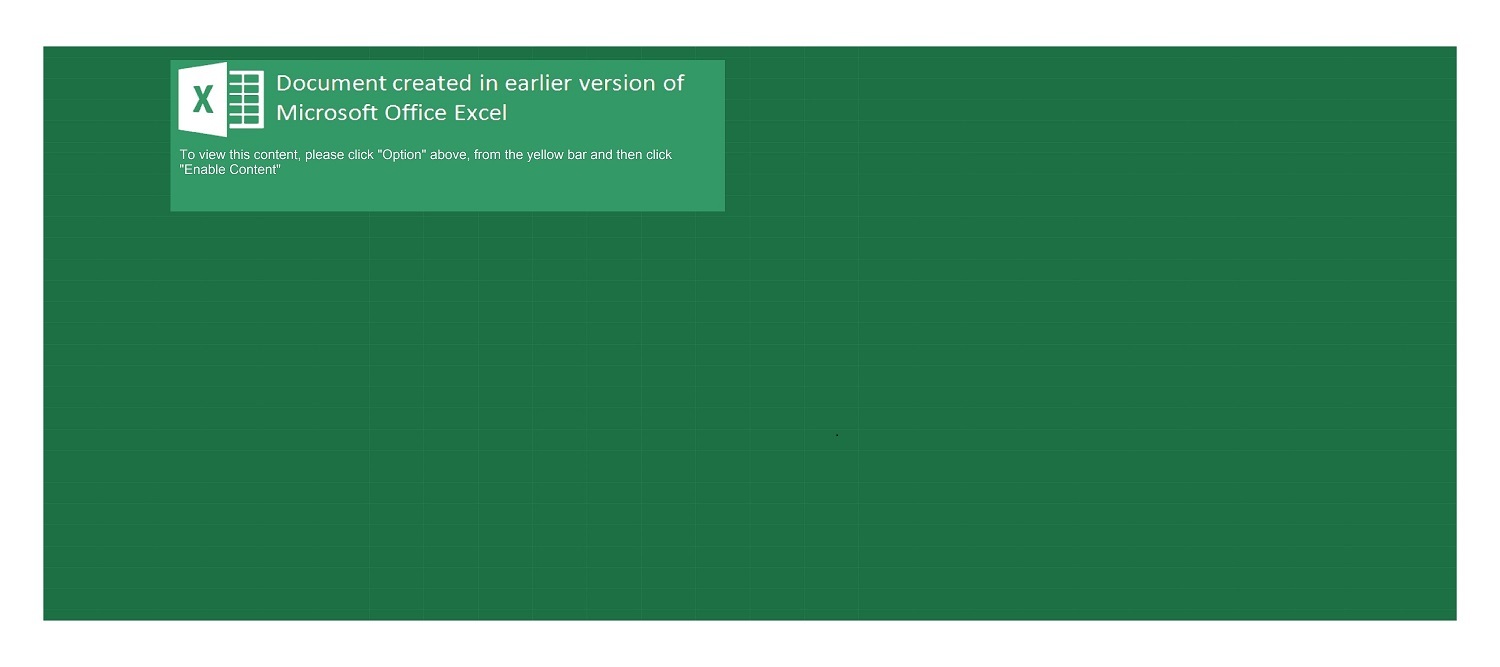
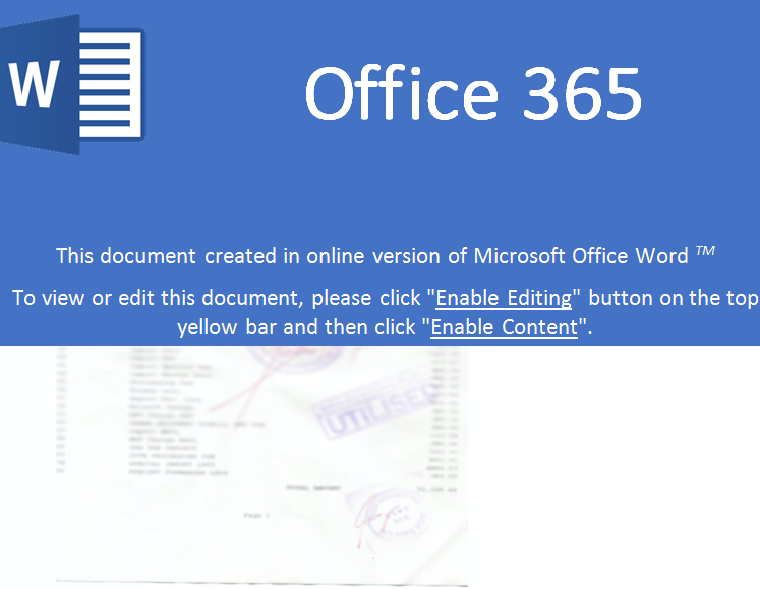
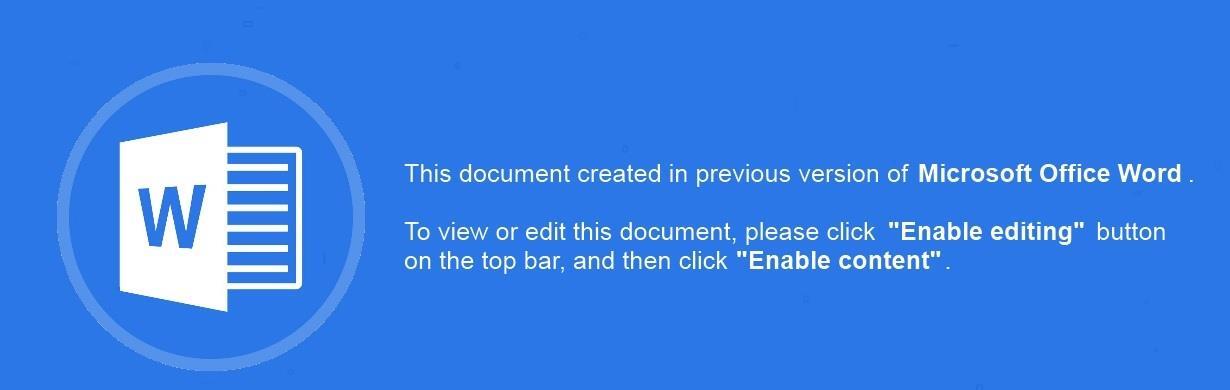
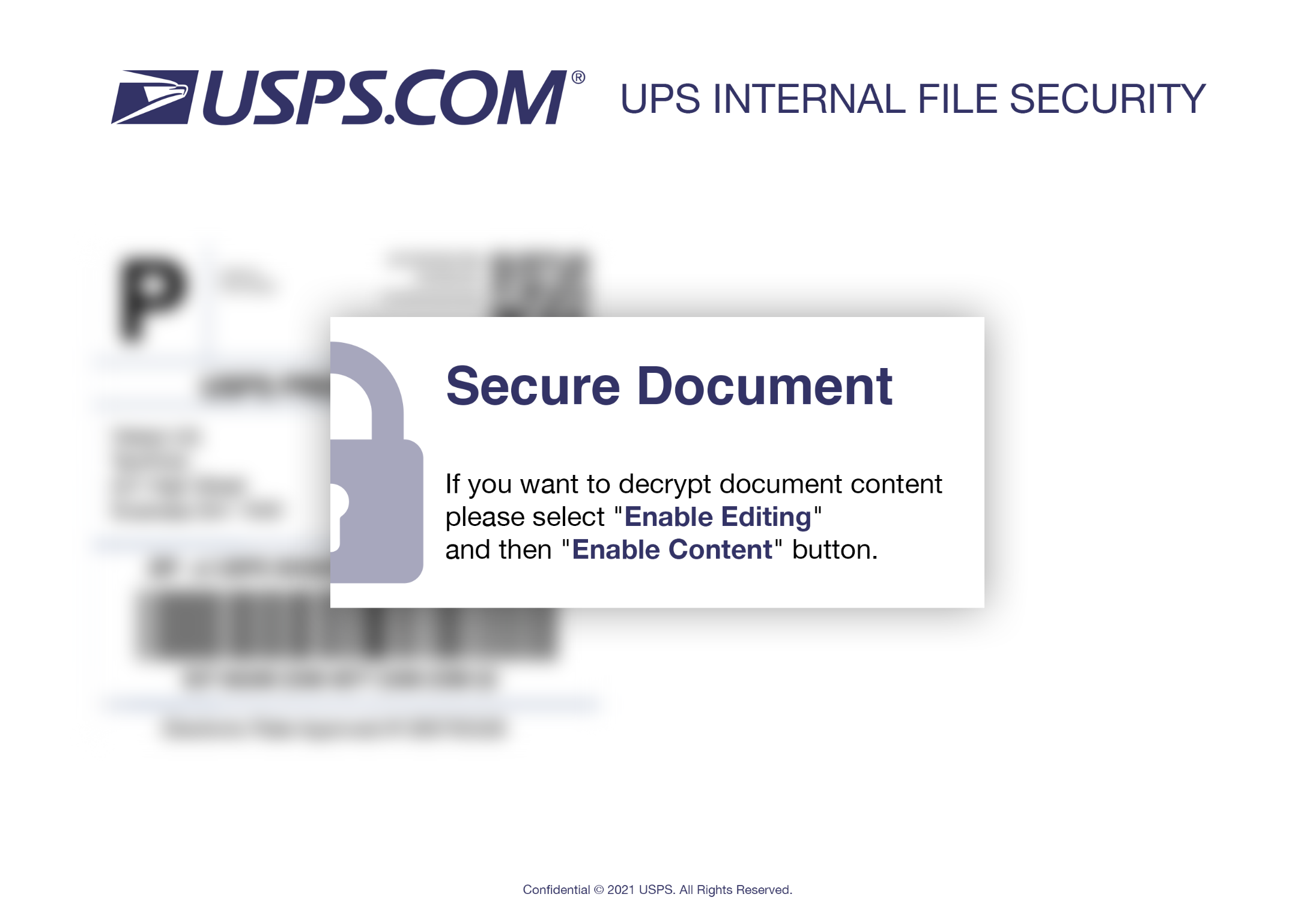
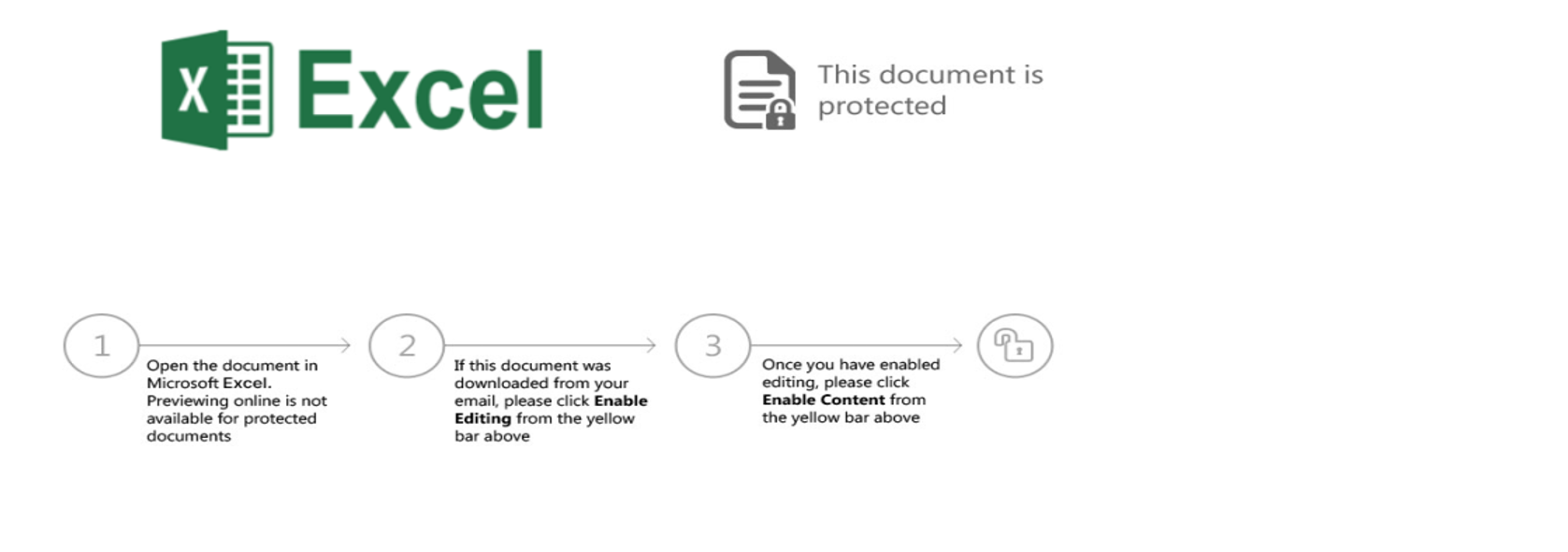
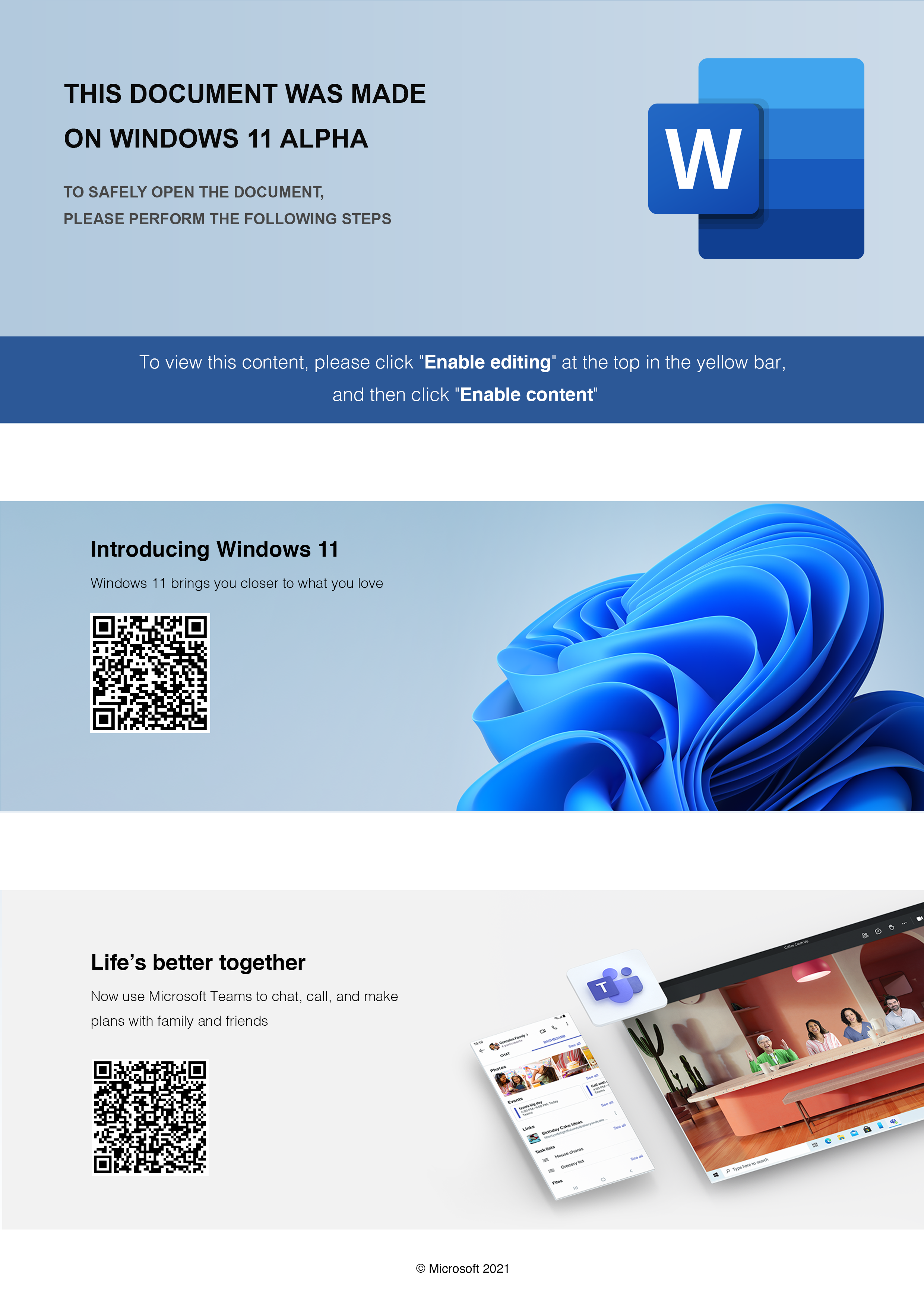
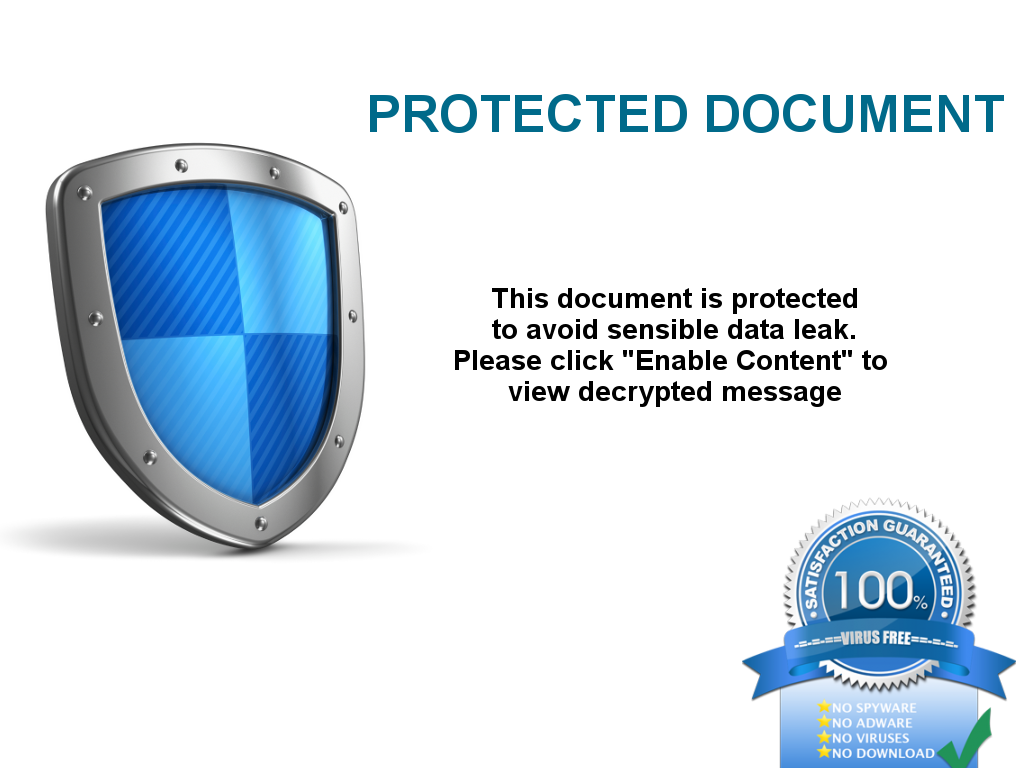
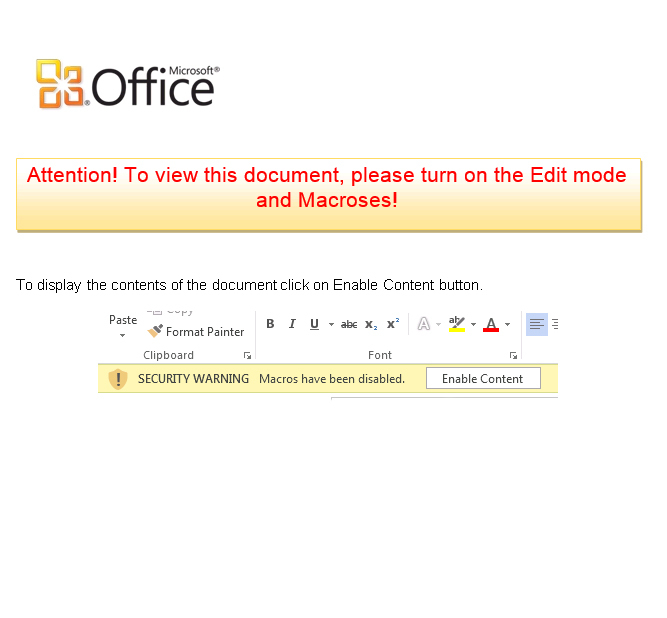
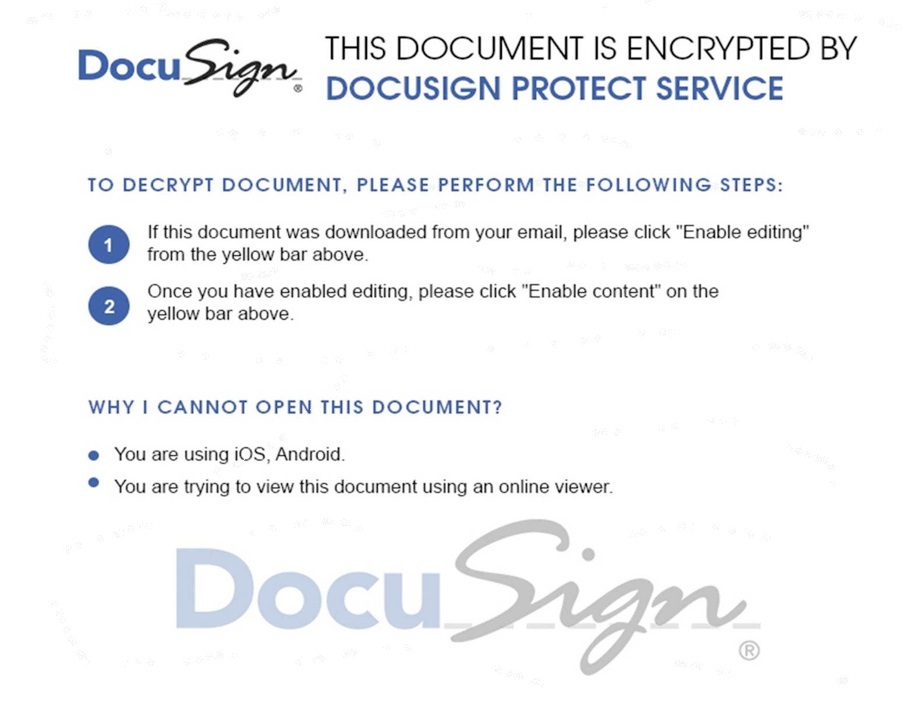
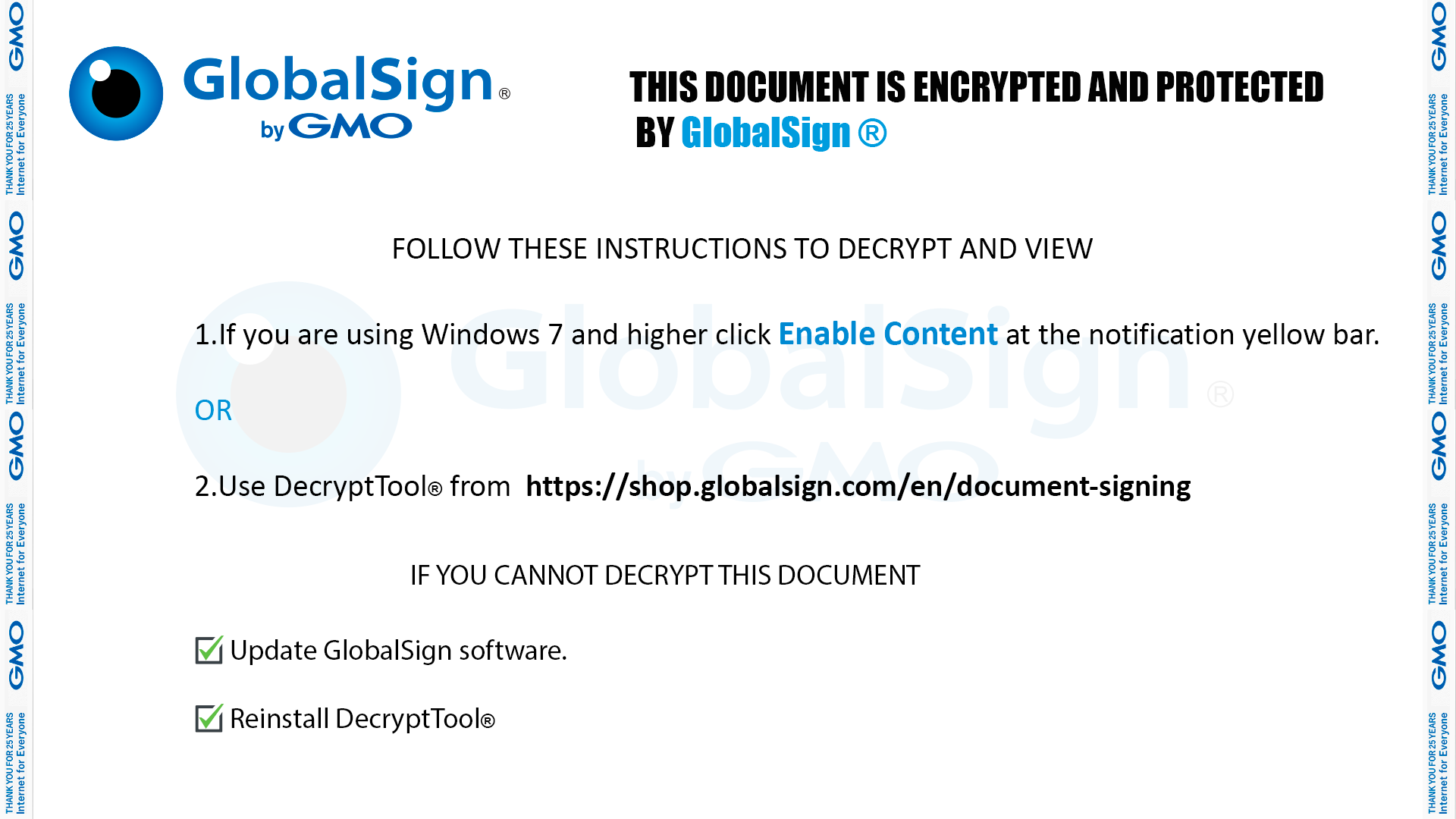
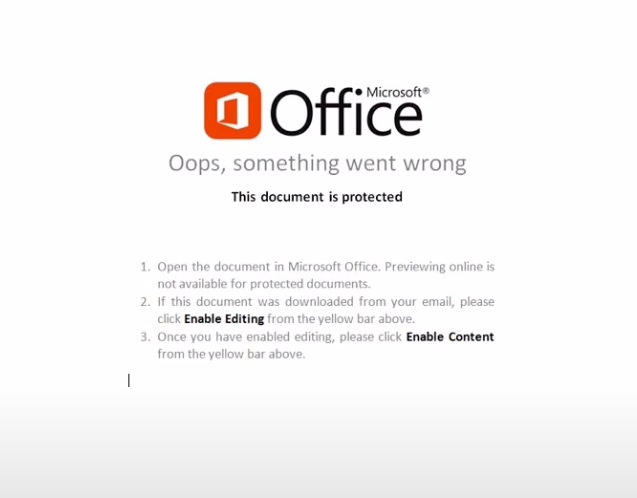
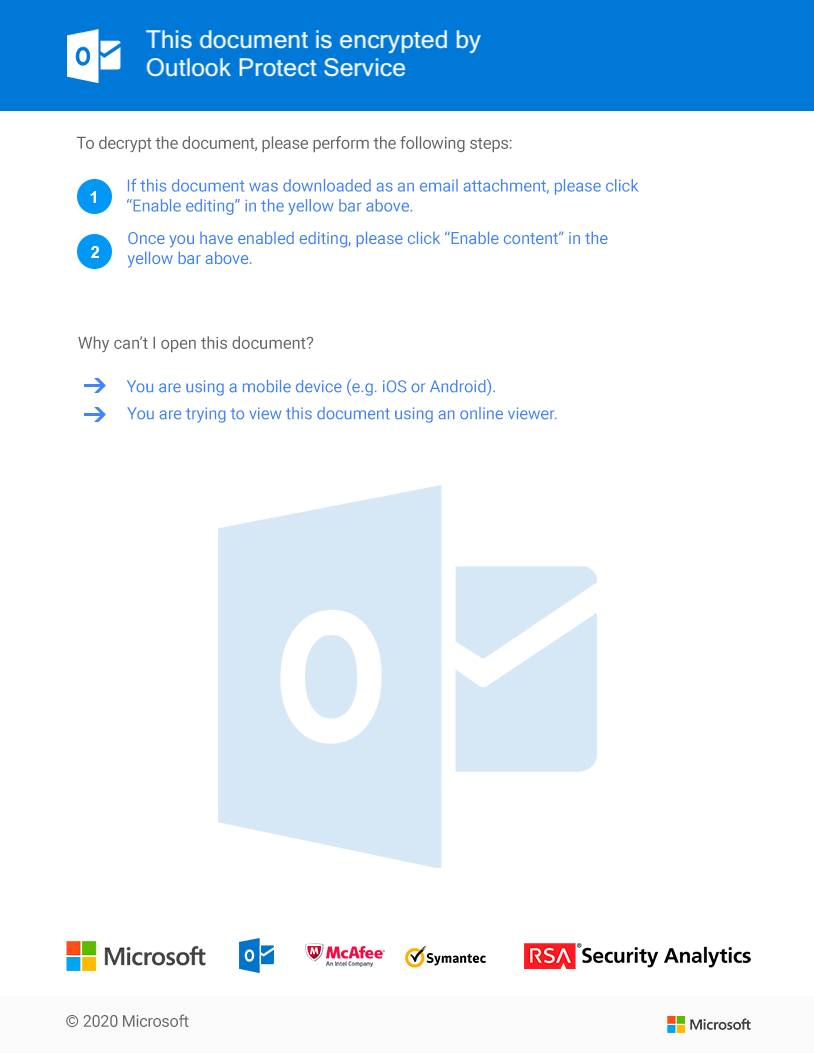
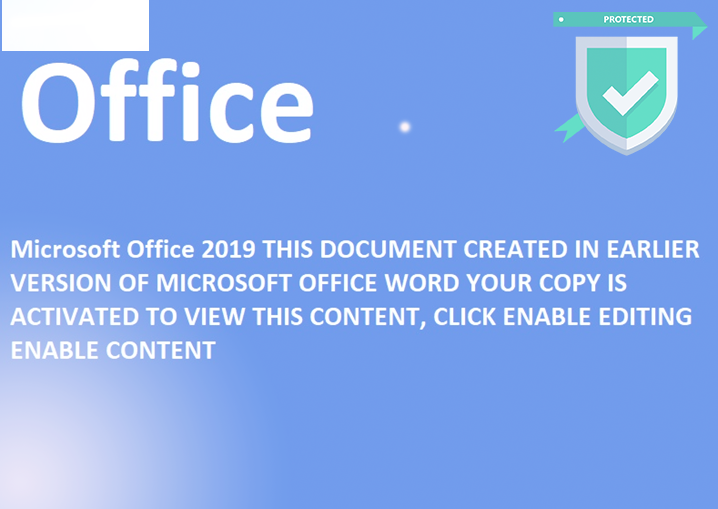
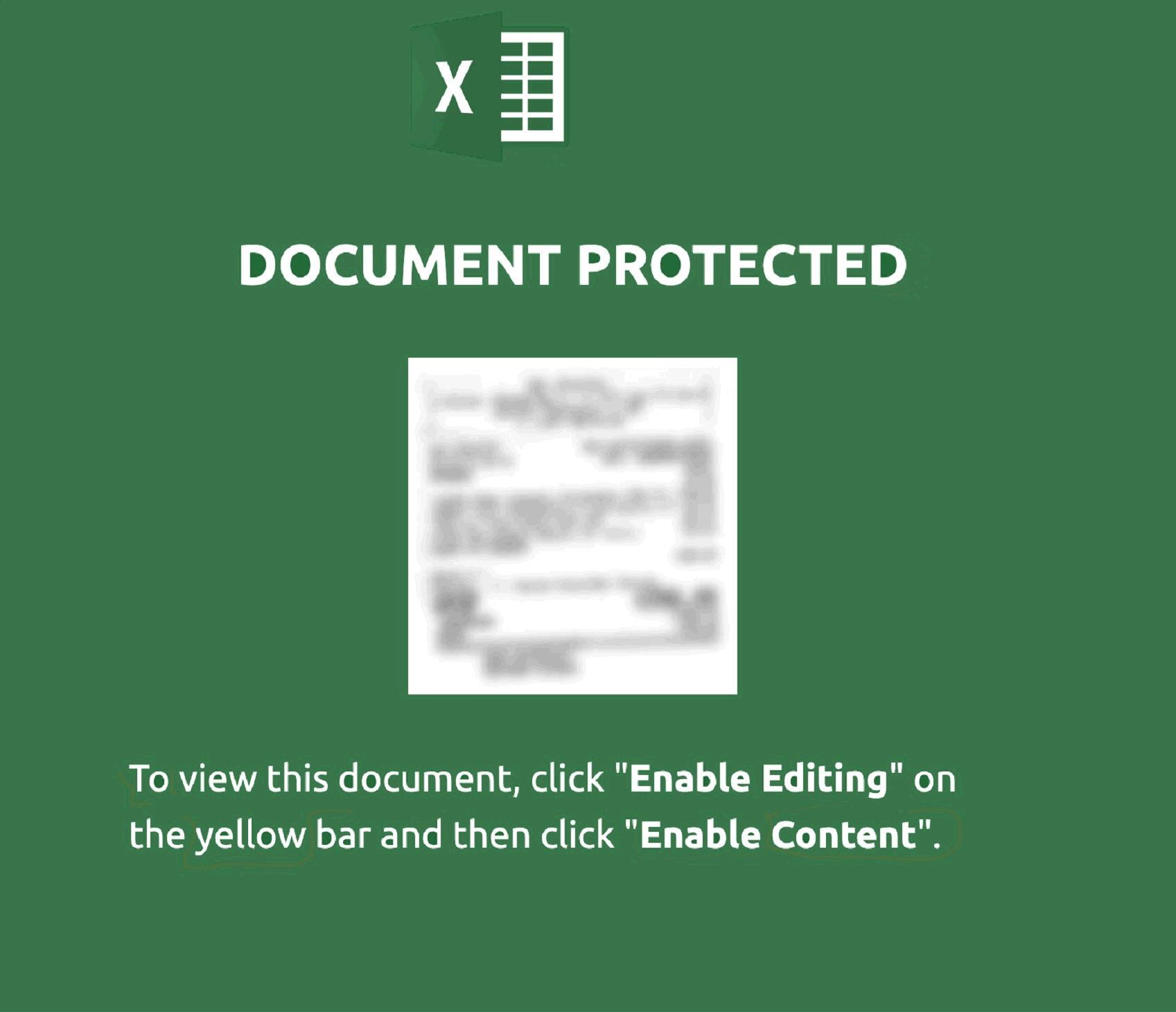
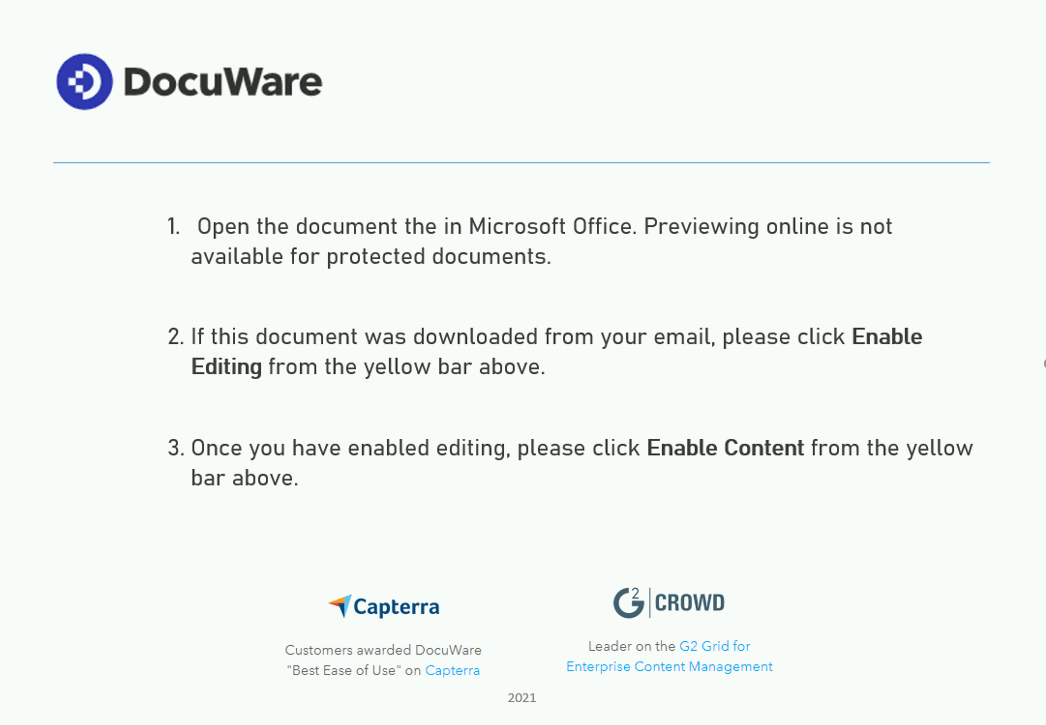
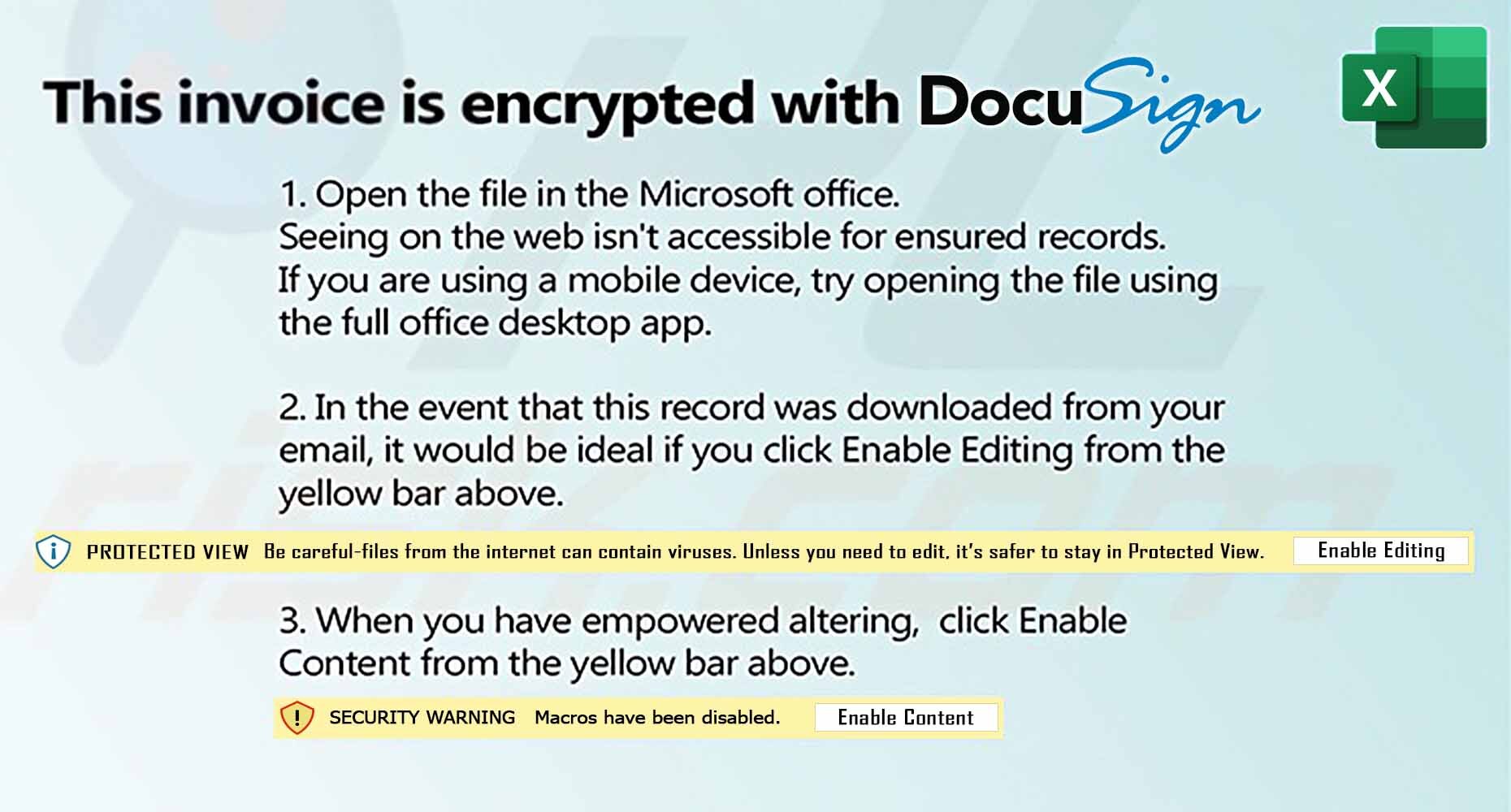
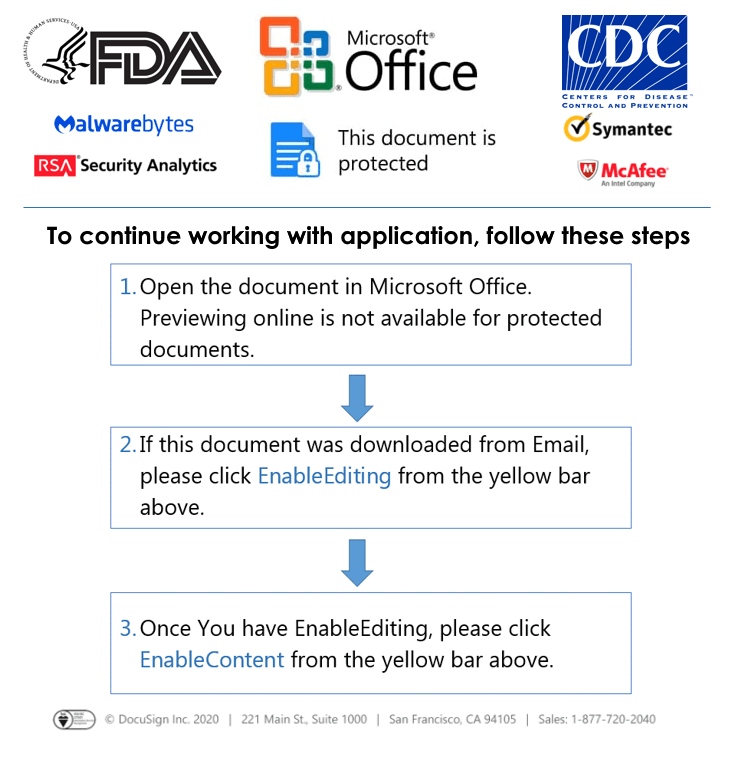
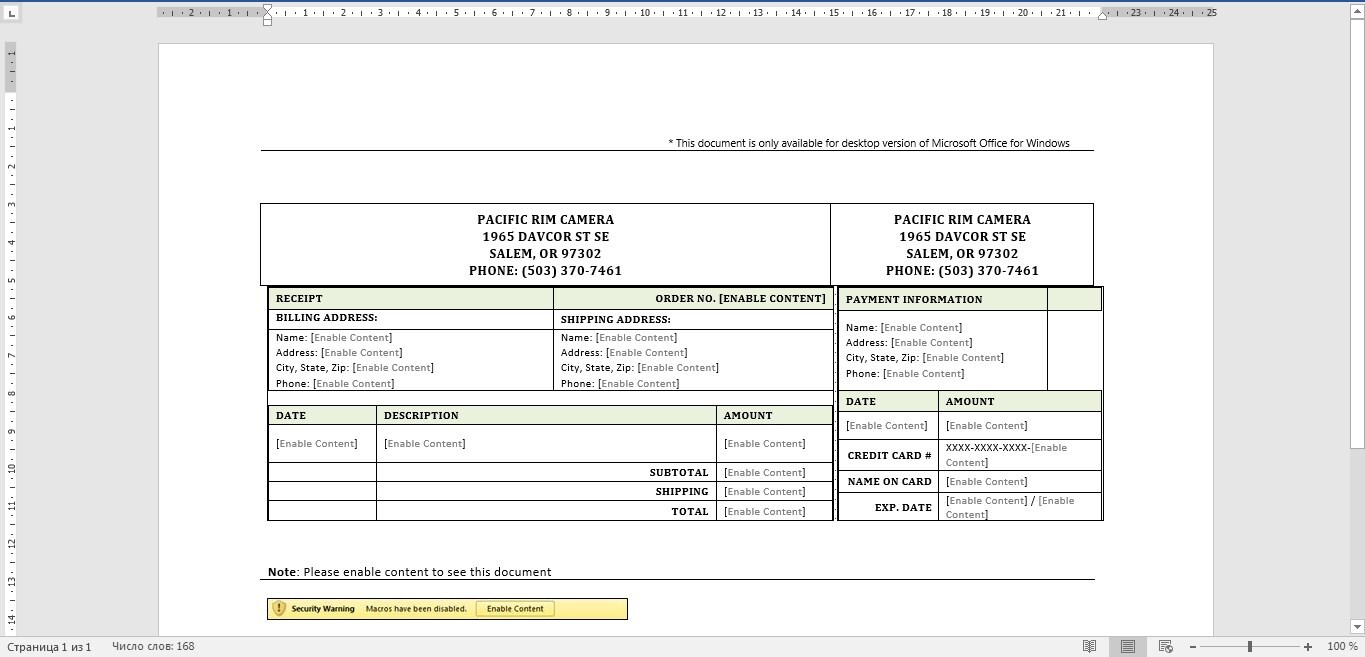
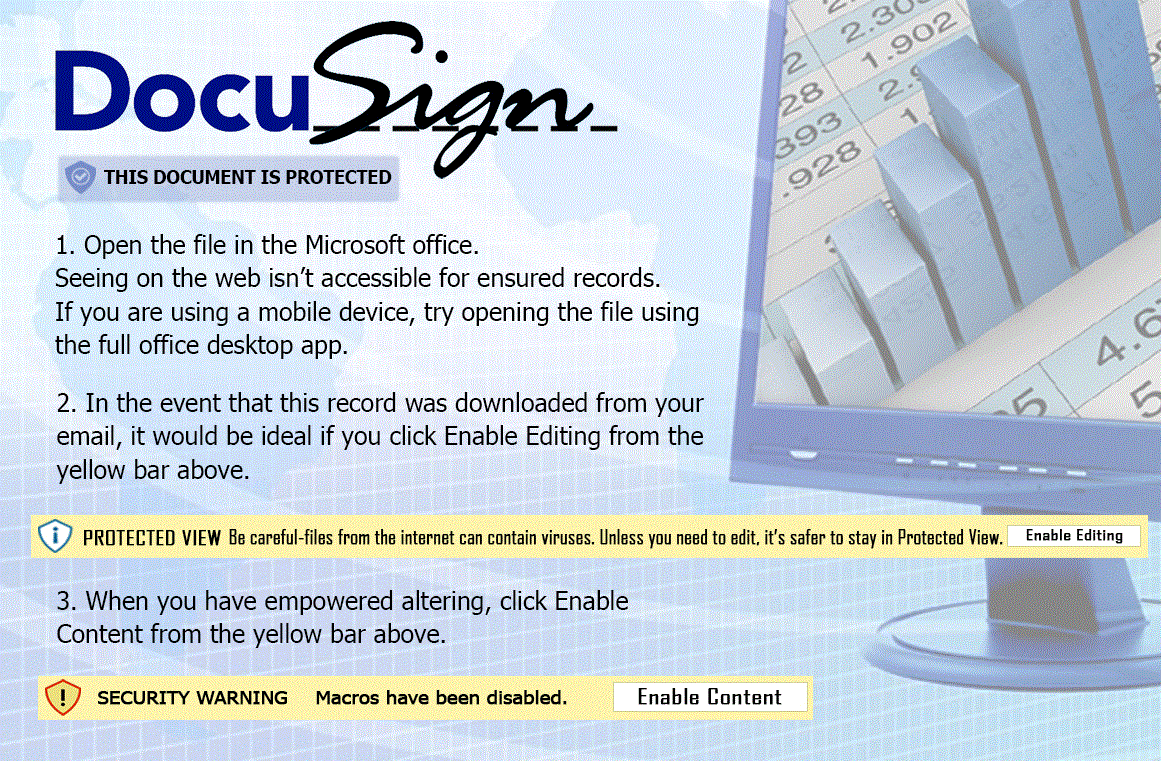
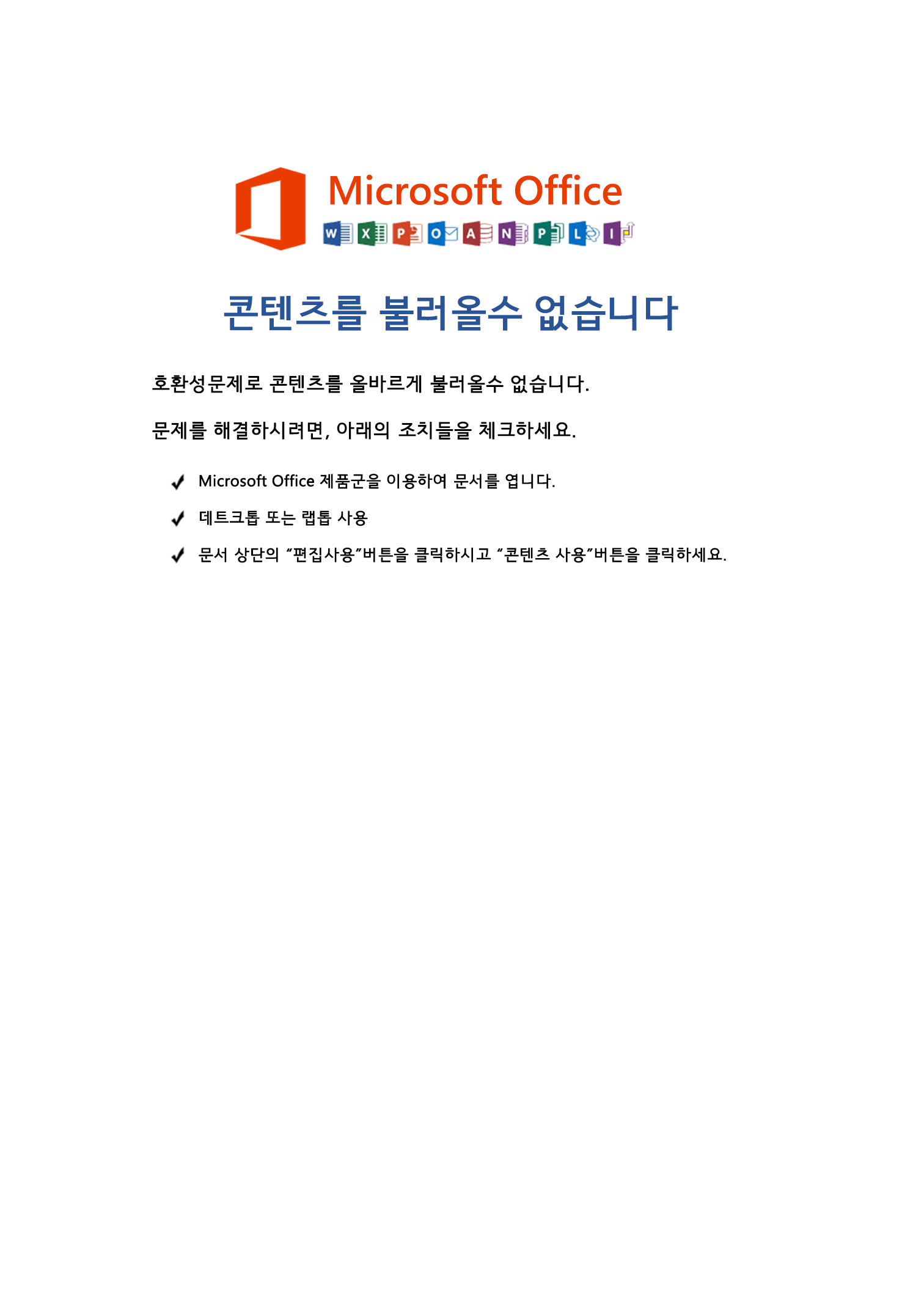
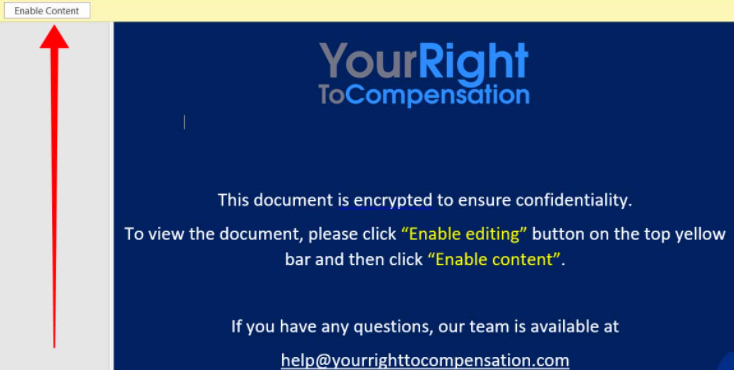
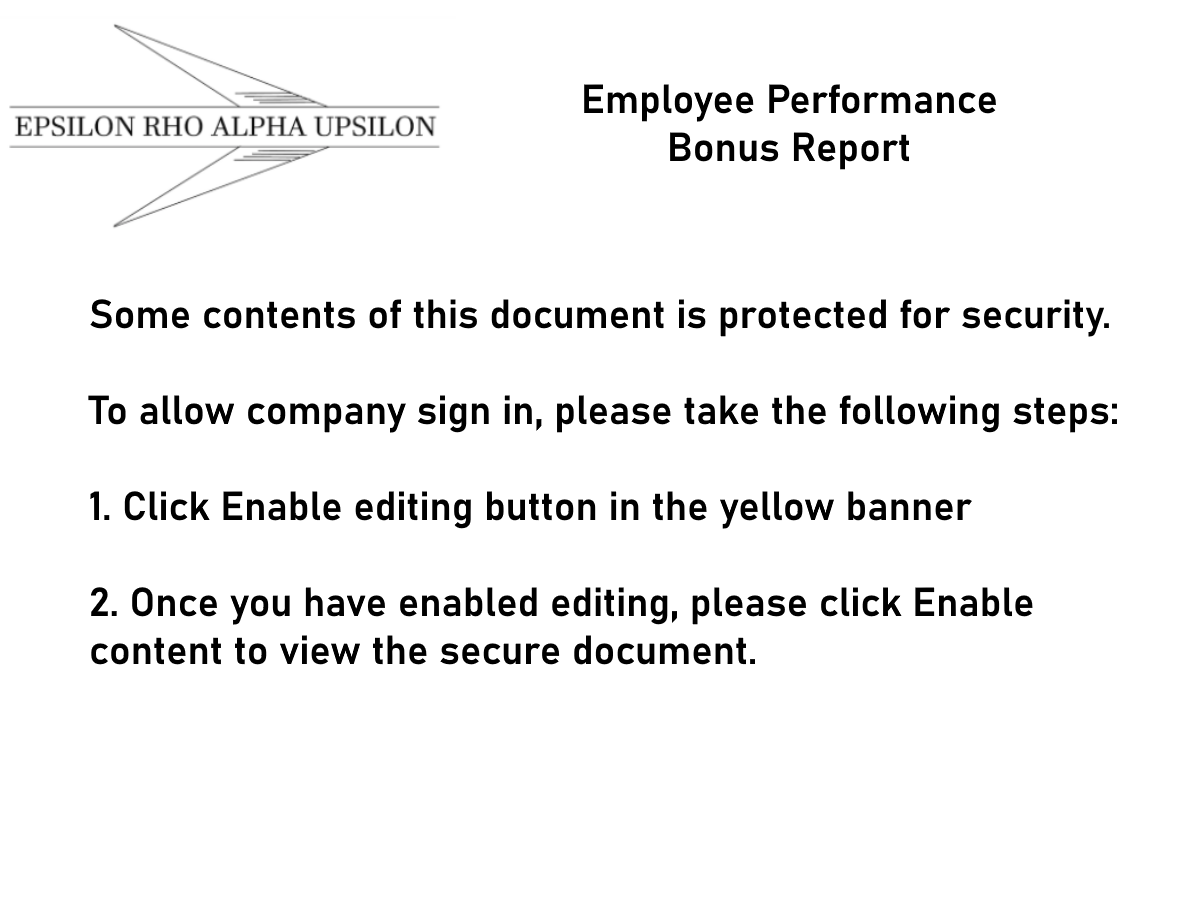
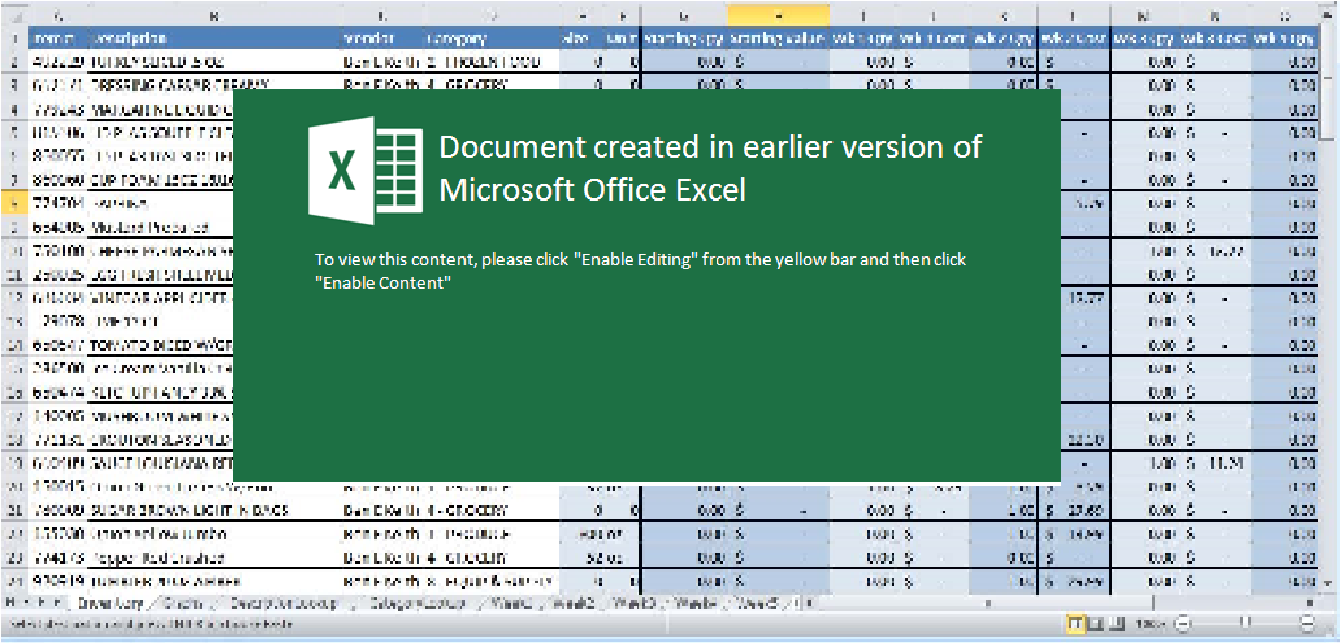
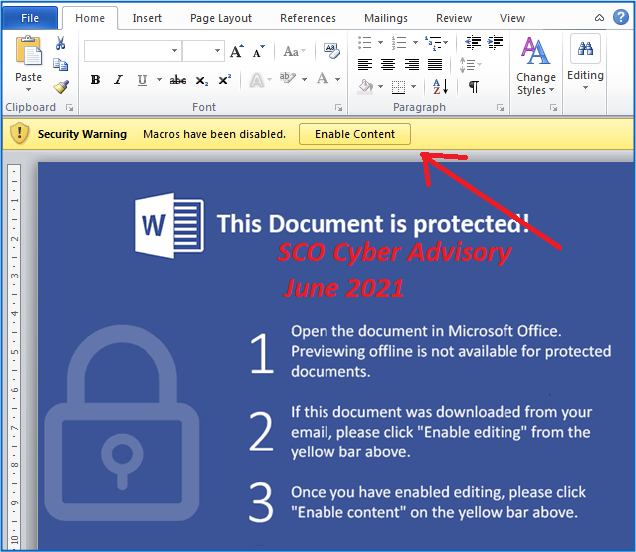
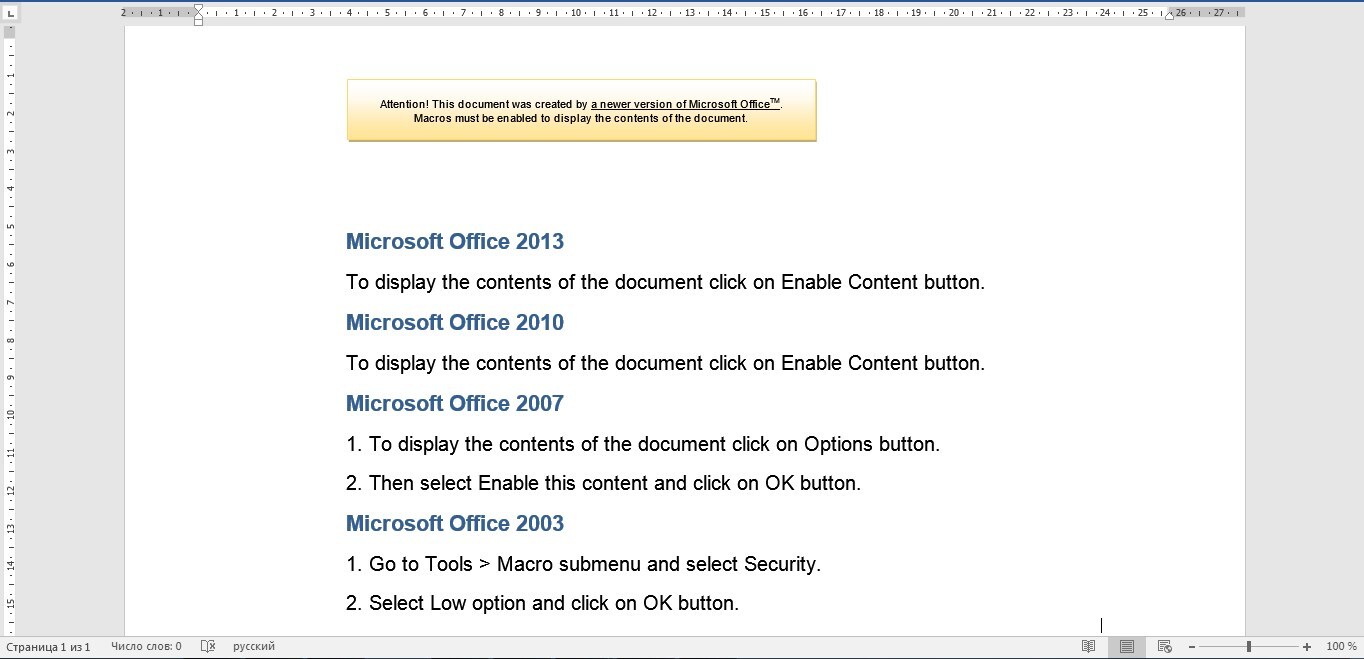
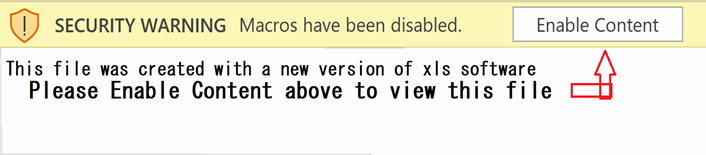
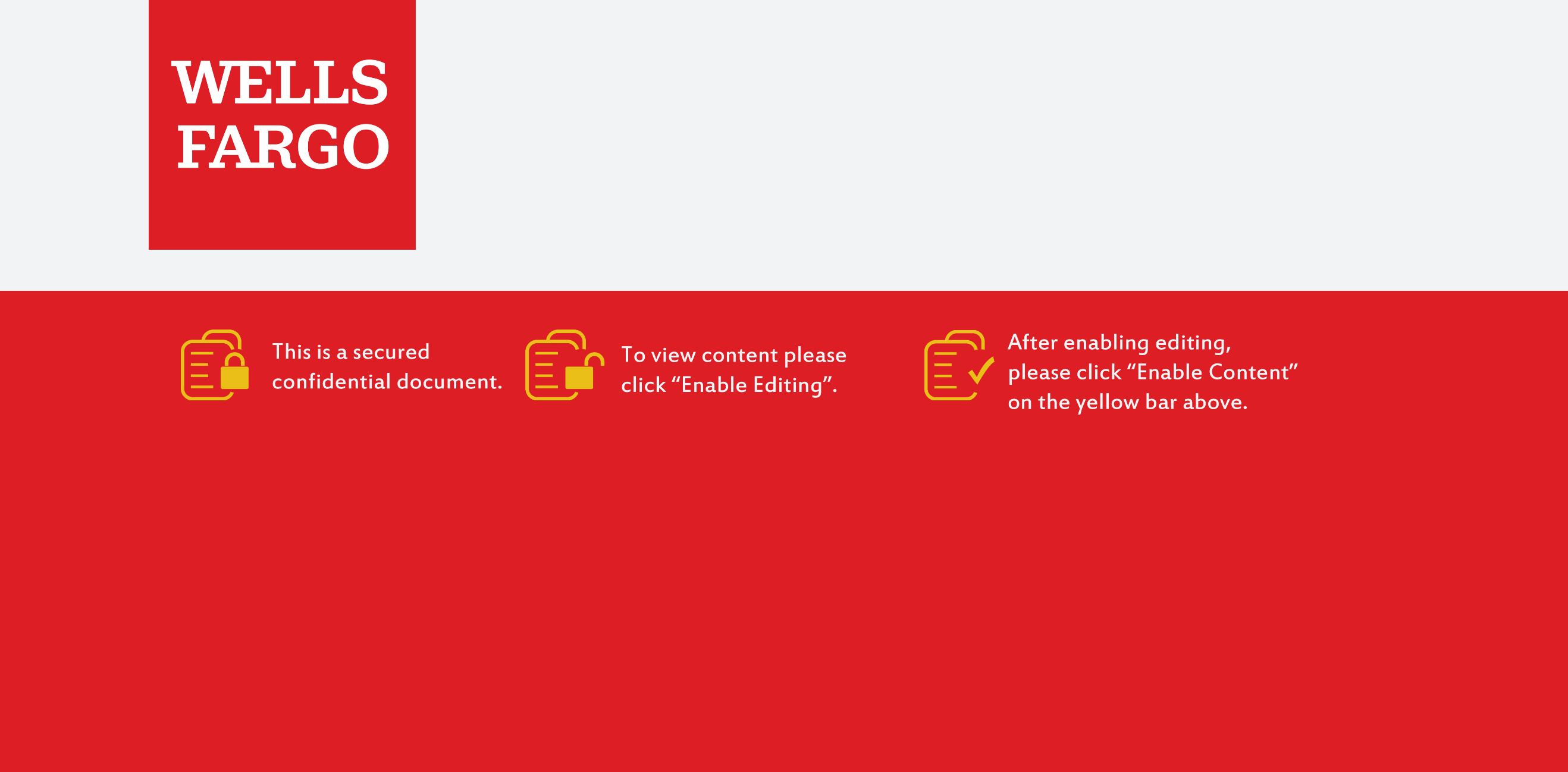
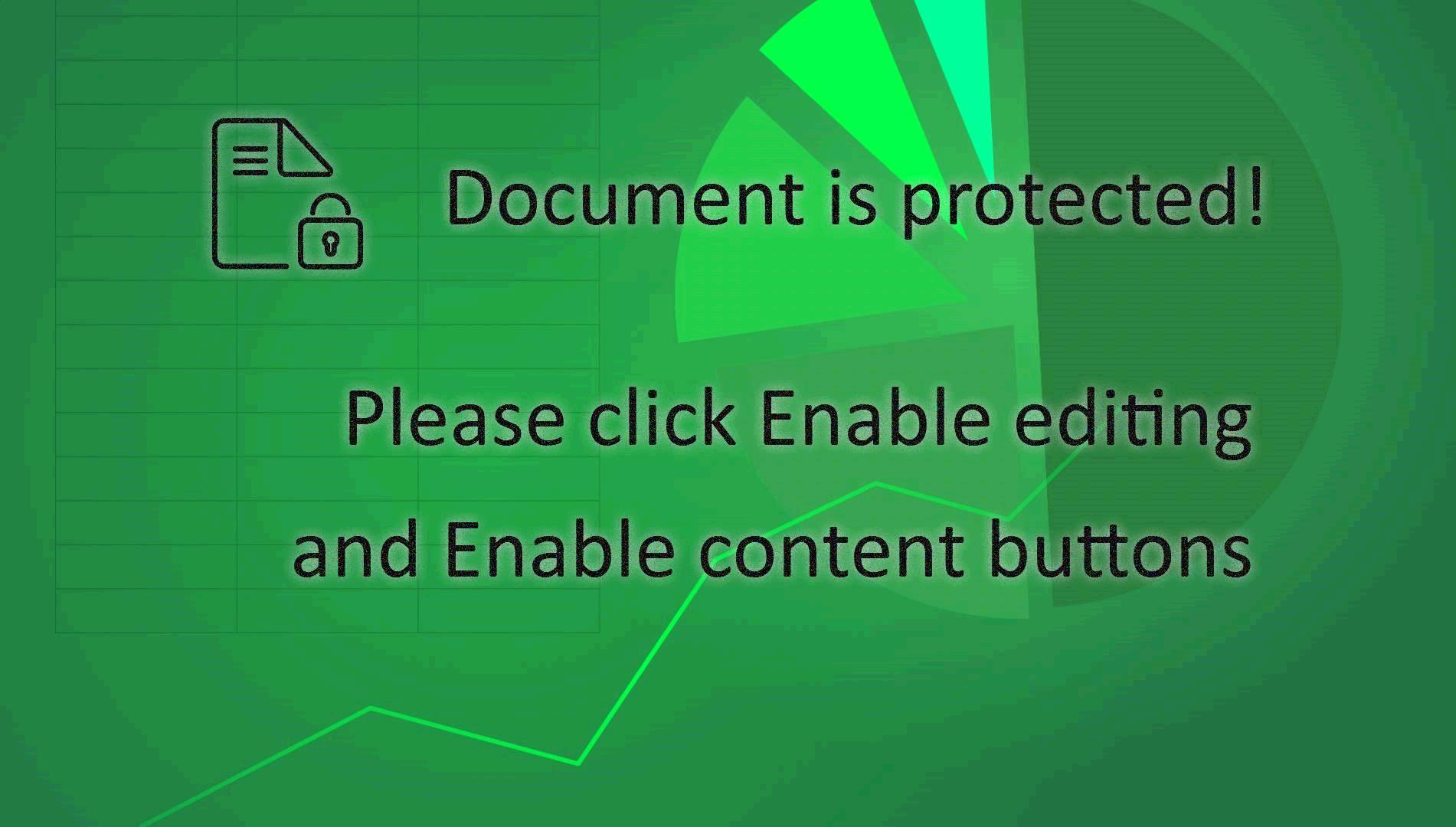
Welcome to our curated gallery of malware lures. An ever-growing collection of images we extract from the millions of real-world malicious files we analyze daily. Malware operators prefer image-based lures over text-based ones as it creates a blind spot for any security solution not equipped with modern computer vision and text recognition models.
If you’re interested in more technical research from the InQuest team, find us on Twitter, follow our Blog, or explore our open / free (as in 🍺) InQuest Labs research portal.
Unveiling the Threat: Malware Lures in Business Email Compromise and Phishing
In the realm of cyber threats, malware lures have emerged as powerful tools used by malicious actors to compromise business email accounts and conduct hacking activities. These lures leverage various techniques to deceive users and trick them into executing malicious actions. Understanding the different types of malware lures employed in business email compromise and hacking is crucial for organizations to strengthen their defenses and protect their sensitive information.
1. Malware Lures in Business Email Compromise (BEC): Business Email Compromise attacks have become increasingly prevalent, posing significant risks to enterprises worldwide. In these attacks, threat actors manipulate employees into taking actions that lead to unauthorized access to corporate email accounts. Malware lures play a pivotal role in initiating and facilitating these compromises. Let’s explore some common types of malware lures employed in BEC attacks:
a. Phishing Emails: Phishing emails are a staple in BEC attacks. They employ social engineering tactics, masquerading as legitimate emails from trusted sources such as colleagues, clients, or business partners. These emails entice recipients to click on malicious links or download infected attachments, which subsequently compromise their devices and grant access to the attacker.
b. Invoice and Payment Requests: Attackers often send fraudulent invoices or payment requests, mimicking legitimate vendors or service providers. These lures exploit the urgency and trust associated with financial transactions, compelling victims to interact with the malicious content. Once engaged, the recipient inadvertently installs malware that enables the attacker to intercept sensitive information or gain unauthorized access.
c. Executive Impersonation: In this type of lure, attackers impersonate high-level executives within an organization. They craft emails that appear to originate from CEOs, CFOs, or other influential individuals, demanding urgent actions such as wire transfers or sharing sensitive data. By leveraging authority and exploiting the recipient’s trust, these lures successfully manipulate employees into unwittingly aiding the attacker’s objectives.
2. Malware Lures in Hacking: Hacking activities often involve the deployment of malware lures to gain unauthorized access to systems, exfiltrate data, or disrupt operations. Understanding the types of lures employed in hacking incidents is essential for organizations to bolster their cybersecurity defenses:
a. Malicious Attachments: Hackers frequently employ email attachments containing malicious payloads to exploit vulnerabilities in software or deceive users into executing harmful scripts. These attachments may be disguised as legitimate documents, spreadsheets, or executable files, enticing victims to open them. Once opened, the malware is executed, granting the attacker control over the compromised system.
b. Drive-by Downloads: Drive-by downloads occur when users visit compromised websites that automatically initiate the download of malicious software without their knowledge or consent. These websites are often compromised through various means, such as exploiting unpatched software or injecting malicious code. Users unknowingly trigger the download by simply visiting the infected site, enabling the attacker to infiltrate their systems.
c. Social Engineering Tactics: Hacking attempts frequently leverage social engineering techniques to deceive users into revealing sensitive information or performing unintended actions. Phishing emails, deceptive pop-up messages, or fake login pages are commonly employed to trick individuals into sharing credentials or granting access to their systems. These lures rely on exploiting human psychology, manipulating emotions, and creating a false sense of urgency to persuade victims to comply.
As the threat landscape continues to evolve, malware lures remain a prevalent tool in the arsenal of cybercriminals targeting business email accounts and conducting hacking activities.