Social Engineering
Social engineering is a common, low-tech approach where a threat actor impersonates someone else to obtain sensitive information or persuade the deceived to comply with some other request type. It has been described as “hacker-speak” for tricking a person into disclosing authentication information, executing malicious code, or opening a door. Some classic example of social engineering is the promise of funds from the prince of Nigeria, and the process has matured into malicious documents with coercive DocuSign lures or spoofed invoice scams changing the routing information for payments.
Social engineering can be combined with many other attack types to compromise security for just about any purpose. While social engineering attacks are simple in concept, they have proven unexpectedly effective when executed well. In the past, the telephone was a favorite vector for gaining information. The process included a threat soliciting a company for sensitive information after masquerading as an employee, system administrator, or business partner.
Today, the majority of social engineering attacks are carried out through e-mail due to the low risk and low cost of mass e-mailing. E-mail works across different computing platforms and various devices and can be effective against targets while at home or work. E-mail threats typically offer a lucrative subject to convince the recipient to open an e-mail attachment, which results in compromise. More effective campaigns use a sense of urgency, monetary compensation, or personal information to coerce the recipient. Further developed e-mails might pretend to be official looking messages from DocuSign or other business invoices or spoofed family members or acquaintances.
Another prevalent social engineering technique is phishing. Phishing attacks aim to harvest authentication information and begin with an e-mail seemingly from a reputable financial provider or other legitimate business and suggest a problem with an account or a transaction. Some phishing attacks are poorly developed and contain obvious misspellings or easily identifiable characteristics. However, some of these e-mails are carefully designed to appear official, include corporate graphics, and are uncomfortably convincing. These e-mails typically include a link directing the victim to a genuine-looking website to capture and personal information submitted by the victim.
Spoofing
Spoofing is when someone or something pretends to be something else in an attempt to gain our confidence, get access to our systems, steal data, steal money, or spread malware.
Generally, e-mail spoofing is the concept of sending e-mails with false sender addresses, usually as part of an invoice scam, business e-mail compromise, or phishing attack designed to get you to send them money, install some malware, or provide access to sensitive information.
But a spoofed e-mail address isn’t always enough to fool the average person. There are a few different components and approaches to identify social engineering e-mails:
• The false sender address is designed to look like it’s from someone you know and trust or a company you do business with.
• Familiar Branding when sent from a company or organization.
• Personalized language for spear-phishing attacks targeting an individual.
• Typos and poorly translated content.
Payment Scams
Another problematic social engineering technique for many organizations is payment or invoice scams. Invoice fraud occurs when a company is tricked into switching the bank account information for legitimate expanse and sizable payment through phishing e-mail or manipulated documents. Invoice fraud is considered a low-risk crime by attackers due to legality, extradition concerns, and the difficulty of tracking and is increasing at alarming rates. Despite the increase in crime, many companies are still being infected and losing high-value amounts to the criminal.
Coercive Documents
Consistently, threat actors are trying to convince the unbeknownst user to “enable macros” or “enabling content” to progress down the attack chain. A curated gallery of these graphical lures is on display in the Malware Gallery
Acknowledging that phishing is still the predominant access vector for threat actors to carry out their attacks, it is irresponsible to think that it is possible to “Squish the Phish” or get that “click rate” down to zero. Regarding the colloquial security proverb, “Prevention is ideal, but detection is a must”, InQuest has been following various techniques used in malicious documents.
Typically, these documents contain a macro called “Auto_Open” or “Document_Open”, but it could be any one of a dozen or so canonical names that cause Microsoft Office to execute the macro once the document is opened automatically.
The Problem
Even the most sophisticated e-mail security controls are easily evaded and not enough to identify and mitigate the tactics and techniques of today’s advanced threats. InQuest’s cloud-based integrated e-mail security solution leverages Deep File Inspection (DFI)to analyze, identify, and ultimately prevent malware, phishing, ransomware, spam, and other social engineering attacks before they are delivered to the users.
The Solution – E-mail Banner Decoration
There are four million lines of code that enable InQuest’s unique banner to work, but our users will never have to encounter any of them. However, what they will experience is a seamless system that catches even the most elusive threats while protecting, training, and empowering users across the enterprise. InQuest instantly analyzes an e-mail and displays a banner at the top of the e-mail. These banners detail precisely what, if anything, is fraudulent or suspicious about the e-mail message. Warning banners are color-coded to empower the employee.
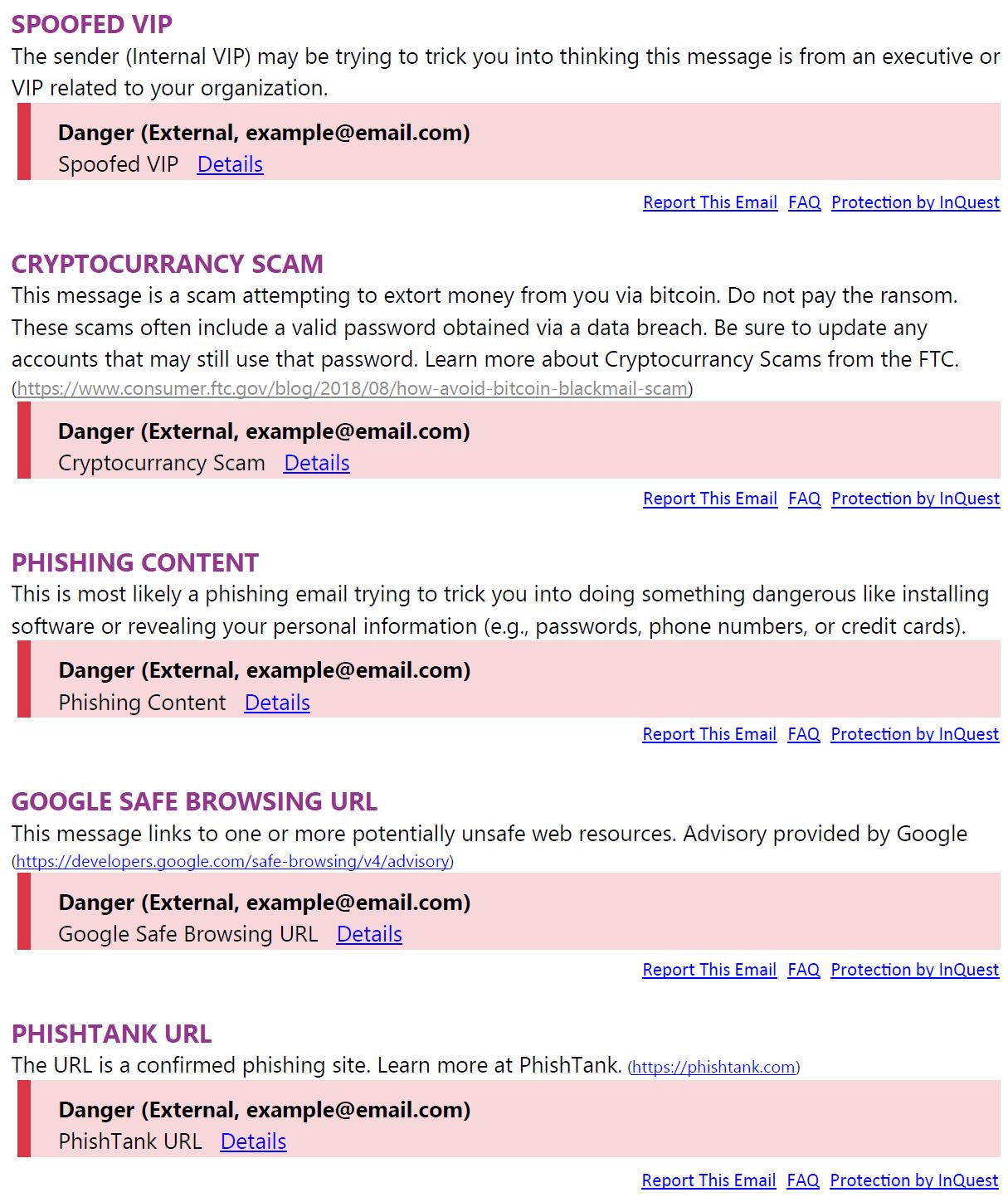
InQuest banners come in different forms. Each banner could have one or more of the threat types with the color corresponding to the most severe among them. They also can include custom policy statements showing end users helpful security reminders.
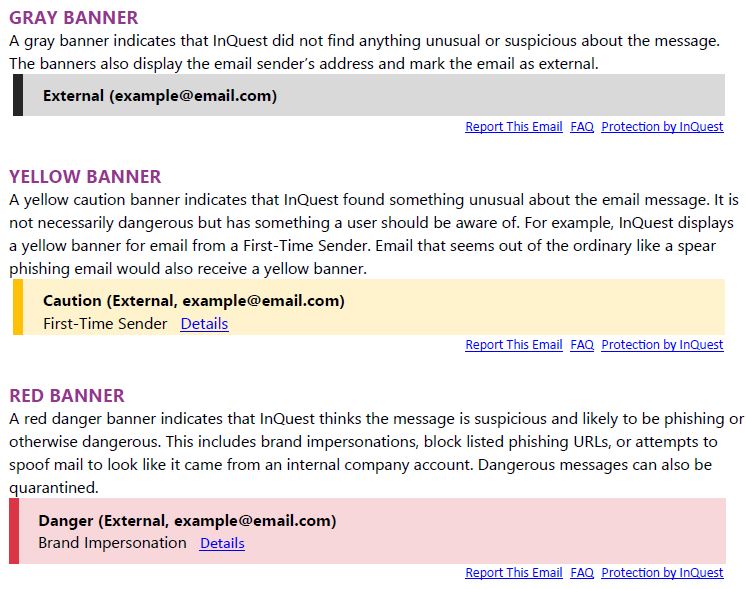
InQuest banners include various threat types such as Brand Impersonations, Spoofed VIPs, and Spam. These are a sample of the most common types, and new ones are added occasionally as new threats appear in the wild.
Conclusion
Malicious actors utilize social engineering attacks that prey on curiosity, desire, and human psychology to compromise their targets’ information. With this human-centric focus in mind, it is up to organizations to help their employees counter these types of threats. The InQuest solution decorates your e-mails with various banners representing the perceived level of threat that an e-mail and an associated attachment contains while providing the ability to tailor your e-mail banners to align with your organizational policies and risk tolerance. Utilize the InQuest E-mail security solution to combat business e-mail compromise by mitigating e-mail spoofing, preventing account takeovers, and protecting against various impersonation and social engineering trickery.