Email-borne pathogens frequently commence with the inclusion of a malicious document. This long-running trend continues to pose a serious threat to the security of organizations and users. Criminals are constantly improving their methods and looking for new ways to compromise victims. Payload trends change over time, with Ransomware being one that is capturing many headlines.
However, the initial intrusion point remains mostly unchanged… Phishing attacks targeting users. In this article, we’ll take a look at the timeline behind an IcedID mailing campaign.
IcedID is a malicious program that steals the bank details of victims in order to steal money. It was first described in 2017 by a team from IBM. Criminals are constantly improving their arsenal and techniques for infecting companies. The program has the ability to deploy its own server with its own certificate using also a browser patch in order to collect all connections, including banking carrying out an attack man-in-the-browser (MITB). This is very well described in this article from IBGroup. IcedID: When ice burns through bank accounts
This short article will describe the new method of infecting users as well as some indicators provided.
| File Type | Microsoft Windows Document |
| SHA256 at InQuest Labs | b17fa8ad0f315c1c6e28bafc5a97969728402510e2d7dc31a7960bd48de3fcb6 |

Interestingly, attackers often choose rather primitive and simple image lures. We have a whole collection of such lures, you can see them here in InQuest’s Malware Lures Gallery
But we see that the sample in question looks elegant and is abused by many companies, including pharmaceutical companies.
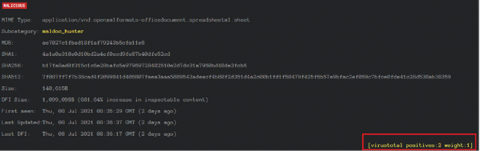
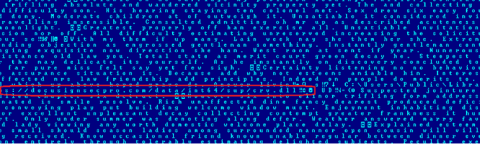
The program contains many superfluous strings. The URL to which the library will be loaded can be found in clear text in the document.
The document pivots to the next stage binary payload through the loading of a DLL from the following recently registered domain name (2021-07-05, 15 days ago as of this writing).
hxxps://docusignsecpro[.]com/data/int64/sup/ crv[.]dll
https://whois.domaintools.com/docusignsecpro.com
This domain name choice is a clever move by the threat actors, a very believable variant of docusign.com that resolves to an Amazon IP address (75.2.115[.]196), one that is home to thousands of other domains.
| File Type | PE x64 DLL |
| SHA256 | 33cc3816f98fa22354559711326a5ce1352d819c180be4328a72618d20a78632 |
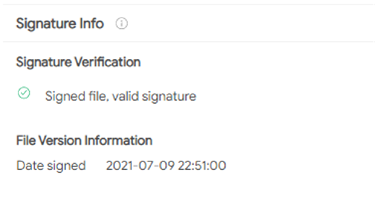
The Virustotal service marks this library as one with a valid signature. Most likely the signing certificate is involved with a malicious signer, as the quantity of related, signed malware is quite high. https://www.virustotal.com/gui/search/signature%253A%2522Amcert%2520LLC%2522/files
If we start analyzing the library that is being loaded, we will see that it has a large block of packed data, this is immediately noticeable based on the entropy of the data. An experienced analyst will recognize this directly from viewing the hex bytes, it’s visually apparent in the following hex dump.

The payload of this library was encrypted with its own algorithm.
Here is a custom decryptor to unpack the payload.
def Searchciphertext (dump):
for i in range (len(dump)):
comsize = len(dump)
symb = dump[i]
if symb == 0x37:
symb = dump[i+1]
if symb == 0x63:
symb = dump[i+2]
if symb == 0x36:
symb = dump[i+3]
if symb == 0x69:
offset = i
print("Success ciphertext ICEDID 07.2021 was found")
i = offset
while i< 100000:
if dump[i] == 0:
symb = dump[i+1]
if symb == 0:
symb = dump[i+2]
if symb == 0:
symb = dump[i+3]
if symb == 0:
size = i
break
i += 1
return offset, size
def decrypt(offset, size, dump, result):
cont = 0x5C
r = 0
i = 0
loop = size - offset - 1
while i < loop:
n1 = dump[i] - 0x36
n2 = dump[i+1] - 0x62
n1 = n1 << 4
n3 = n1 | n2
n3 = cont ^ n3
cont = cont + 1
if cont == 0x100:
cont = 0
result[r] += n3
r += 1
i += 2
print("Decryption was successful")
return(result)
if __name__ == '__main__':
file = open("malware.dll_","rb")
dump = bytearray(file.read())
offset,size = Searchciphertext(dump)
dump = file.seek(offset,0)
dump = bytearray(file.read(size-offset))
result = bytearray(15000)
opendata = decrypt(offset, size, dump, result)
new = open("unpack.dll_","wb")
new.write(opendata)
new.close()
file.close()The executable library decrypts another library from its data.
| File Type | PE x64 DLL |
| Sha 256 | c4a1485fdd8b3c79a2a76d79a07f8f288b21f640073e9909ff0d1787e44d18a7 |
First, the library will check the system’s internet connection. Calling the address “aws.amazon.com“.
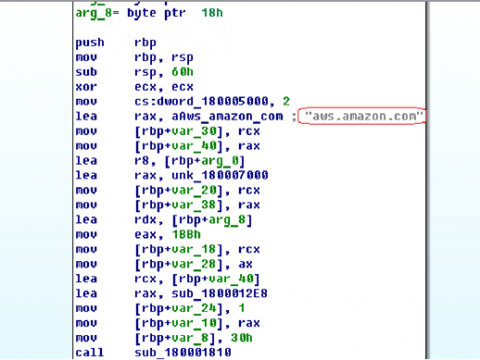
Depending on the received response from the server, the program falls asleep and tries to connect again. This is done for the purpose of anti-analysis. Since the sample needs the system to be connected to the network. If there is no connection to the network, then it does not perform its malicious functions.
If there is a connection, the program decrypts the URL address and connects to it.
The program collects information about the system and generates a unique identification number for each bot and each system.
The program uses the SID as a unique attribute. A SID is a number used to identify user, group, and computer accounts in Windows, created when accounts are first made in Windows; no two SIDs on a computer are ever the same
The program also receives information about the network adapter of the system. The bot sends all this information to a remote server.
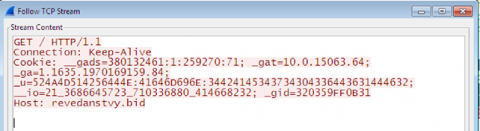
revedanstvy[.]bid
https://whois.domaintools.com/revedanstvy.bid
registered 6/24 (27 days ago as of the time of writing), updated on 7/8. Not resolving to an IP address at the moment.

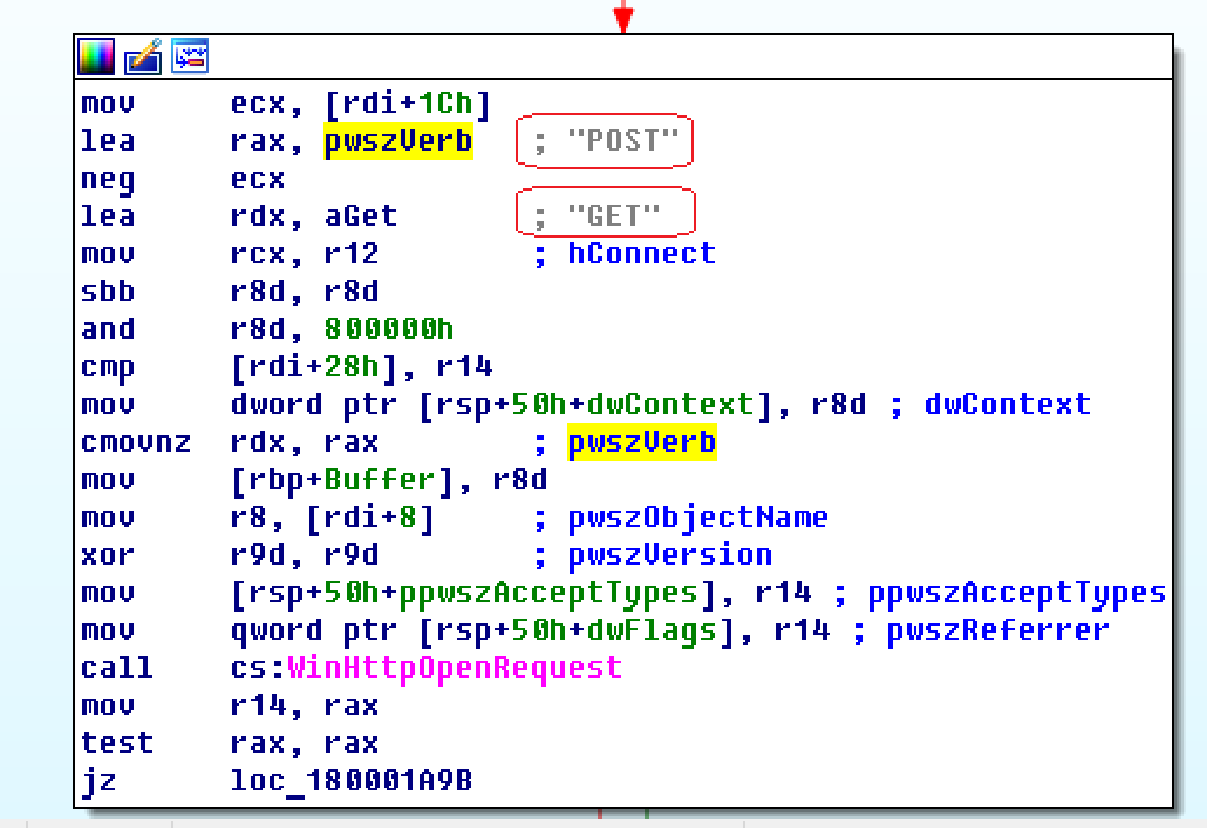
Having transferred all data to the remote server, the bot continues to wait for a connection. The bot has the ability to both transfer and receive data. This can be seen in the picture above.
In response to a remote connection, the server sends an encrypted shellcode, which is decrypted and launched.
After the supposed death of Emotet, there is no doubt that the IcedID will quickly lineup as its successor. The attackers behind this campaign have gone to great lengths to develop and deploy tools to steal bank data.
IOC:
| IOC Type | IOC | Description |
|---|---|---|
| SHA256 | b17fa8ad0f315c1c6e28bafc5a97969728402510e2d7dc31a7960bd48de3fcb6 | Maldoc |
| SHA256 | 3651c72474f95b0aa0346bb65cca763418a37e244d5e8210402393c691ebf394 | Maldoc |
| SHA256 | 2c4de0613a4381fd1c7e59fdac5e71a30326252babebe7d366edb12df8f6433b | Maldoc |
| SHA256 | e7856fd676cb6995e077c14920cffb677e9e032a7af7c1e04ae90a3454ea1607 | Maldoc |
| SHA256 | a7f190dab13ae5f8196f75b66c001c2a33ce7334c0223994e4842cde57d72dca | Maldoc |
| SHA256 | c8ecc53d90c50be4a6202f2aaca024158e584c29c03920b439d6ed86099f2613 | Maldoc |
| SHA256 | f3a9d96d885e6bc574ff9686b7087f3dc16d9f671cbc45632a21a139a628c126 | Maldoc |
| SHA256 | dc2312d239aba03c43c757f981c363db43af1b62d9d4503f4c9c6d5016a057cc | Maldoc |
| SHA256 | 33cc3816f98fa22354559711326a5ce1352d819c180be4328a72618d20a78632 | crv.dll |
| SHA256 | c4a1485fdd8b3c79a2a76d79a07f8f288b21f640073e9909ff0d1787e44d18a7 | Unpacked DLL |
| Payload | hxxps://docusignsecpro[.]com/data/int64/sup/crv[.]dll | 2nd Stage Payload |
| URL | revedanstvy[.]bid | C2 Domain |
Free On-Demand Webinar: Think Before You Click
Whether sent as an email attachment, sitting in your cloud or traversing the Web, file-borne threats have become a proven favorite for delivering malware and phishing campaigns. View our webinar on-demand and get firsthand tips about how to safeguard your cybersecurity stack with File Detection and Response (FDR) and stop file-borne threats in their tracks.