Anticipating File-Borne Threats: How Deep File Inspection Technology Will Shape the Future of Cyber Defense

The InQuest Insights threat intelligence team recently fielded a question: what complex, layered file format attacks do modern adversaries use in their attack sequences to gain a foothold in target networks? This is a space that InQuest knows well, having leveraged our technology and expertise in this area for more than a decade defending mission-critical networks in various sectors against file-borne attacks. In this post, we’ll share some insights on this topic, and we’ll reinforce what cyber intelligence trends tell us about attacker adaptation in what we call a “post-macros” threat landscape as we discuss why this knowledge is so important for defenders. With a growing number of adversaries leveraging complex file formats, InQuest’s focus on File Detection and Response solutions powered by Deep File Inspection® (DFI) technology is more crucial than ever when facing today’s threat landscape.
Complex and Layered File Format Attacks in Adversary Playbooks
At InQuest, we specialize in finding the hard to detect file-borne attacks. Adversaries attempting to make use of complex, layered file format sequences during initial access and execution or to gain a foothold in a victim environment are of particular interest to us. This approach is something that has grown in frequency and sophistication over time, with more threat groups adopting these techniques than before and the level of sophistication increasing. This is why it is critical to have predictive detection that can detect these sophisticated attacks. In many ways, we feel like this is one of the most important points requiring attention from defenders today. How prepared are you to defend your environment against an attacker that has mastered evasive file tradecraft for smuggling payloads past gateway defenses and other signature based systems, hiding malware in layers of various file formats that may be decoded or decrypted at runtime, and bypassing defenses when deploying their toolset?
The saga of file-borne attacks is not new. During the 2000s and 2010s, a number of advanced persistent threat groups were successful leveraging file types such as Compound Documents (OLE), Portable Document Files (PDF), Java archive (JAR) and Shockwave Flash Movie (SWF) files in packaging exploits used to execute code in client-side attacks. Countless organizations were breached as security teams discovered that they could no longer depend on antivirus software or traditional sandboxing solutions to protect them from complex file formats that could bypass network IDS, gateway controls and endpoint defenses. This tradecraft was also adopted by crimeware groups that collected these exploits into browser exploit kits, commoditizing the drive-by download for malware distribution. Over the years, we’ve seen successful use of these and other file types such as RTFs, Microsoft Word, Excel and PowerPoint documents, and others used by state sponsored as well as financially motivated criminal groups during malware distribution campaigns. Three primary evolutions have occurred in recent years:
- File format abuse has exploded, expanding from primarily document and multimedia formats to numerous file types to include Compiled HTML Help (CHM), OneNote and disk images (ISO, IMG, VHD/VHDX) to name a few. In this way, we see a reemergence and continuation of tried and true formats like CHM files alongside more recent developments like OneNote carrier files.
- File format abuse has shifted from techniques that primarily packaged code execution exploits targeting vulnerable client-side software to execution techniques that do not rely on unpatched vulnerabilities, and instead leverage social engineering to trick users into allowing execution of attacker code.
- The underground economy has exploded, and the barrier to entry has dropped. Specialists in this area have developed solutions and services that place advanced tradecraft in the hands of less skilled attackers. This has occurred in the form of malware builders and malware as a service (MaaS) offerings available to buyers, as well as a rise in initial access brokers – attackers that specialize in breaching networks and handing off access to paying customers.
A great deal of information is documented publicly today about adversary usage of complex file formats. We review a few of those in the following sections.
Chinese Threat Actor Group
An example of a group attributed to the PRC is Tonto Team.
- Targeting: Impact in numerous regions and industries including Asia, Europe, North America, Defense, Government.
- Observed threat sequence: CHM >> EXE (DLL side-loading) >> VBE (encoded VBS) >> VBS (ReVBShell backdoor) >> EXE (DLL side-loading) >> Bisonal backdoor
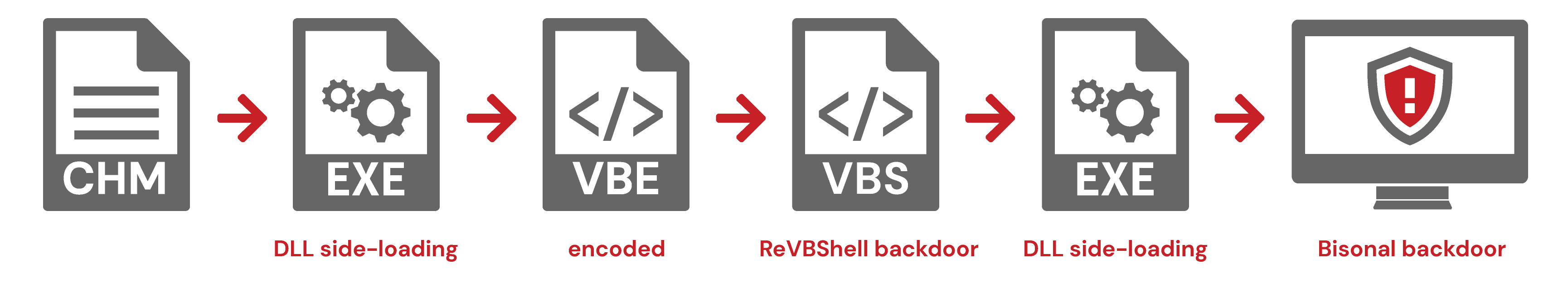
As documented by researchers, Tonto Team has abused Compiled HTML File (CHM) files as the tip of the spear in setting off an execution chain of multiple malware stages, including characteristic VBS backdoors and layers of DLL side-loading. CHM files have an evasive quality of being compiled code, requiring decompilation to reveal inner content, making them ideal for smuggling payloads past defensive controls. Notably, CHM files are found in the playbooks of numerous threat groups, leading to them being a relevant element in today’s threat space. Another Chinese state sponsored group utilizing CHM files is APT41.
North Korean Threat Actor Groups
A group whose activity is believed to be directed by DPRK is APT38. They pursue high yield financial theft operations that are suspected to fund the regime.
- Targeting: Global, Financial, Media, Technology.
- Observed threat sequence: LinkedIn message (attachment) >> RAR >> CHM (downloader) >> MSI >> PowerShell (downloader) >> MSI >> JavaScript/JScript (backdoor)

This reported attack sequence shows an adversary that relies on an evasive delivery approach, staging delivery of an attachment from a trusted social media platform, and benefitting from multiple layers of indirection and embedded content in the form of compressed archives, compiled HTML, and multiple Windows Installer (MSI) files deploying backdoors implemented in different scripting languages.
Other North Korean groups exhibit similar variations of evasive file-based tradecraft, revealing a playbook among numerous subgroups that have developed capabilities in a post-macros world and can adeptly navigate around common defensive controls:
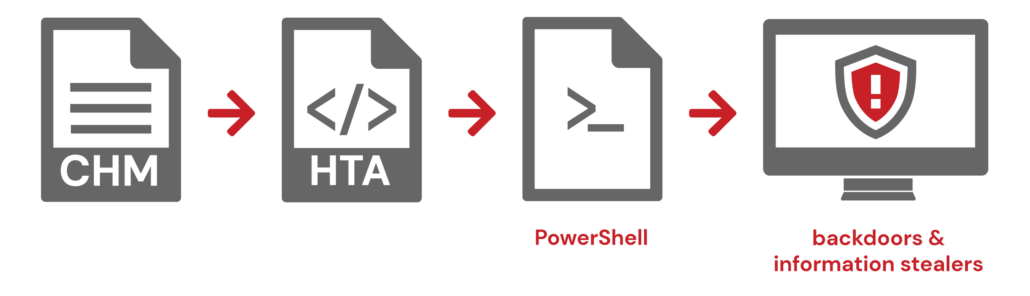
APT37 A/K/A Reaper, RICOCHET CHOLLIMA, ScarCruft
- Targeting: Asia, Middle East, Civil Society, Defense, Government
- CHM >> HTA >> PowerShell >> backdoors & information stealers
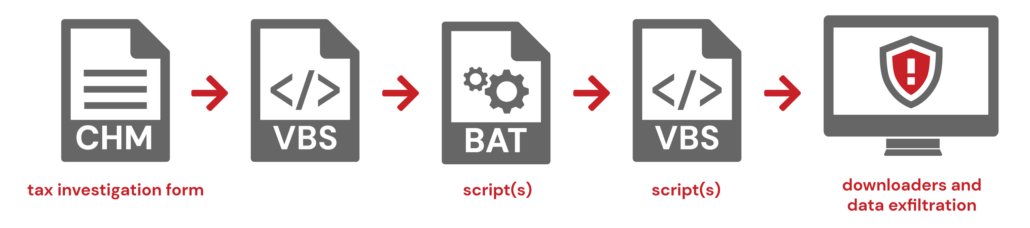
Kimsuky A/K/A APT43, THALLIUM/Emerald Sleet, VELVET CHOLLIMA
- Targeting: Europe, Japan, South Korea, USA, Defense, Energy/Nuclear, Government/Diplomacy
- CHM (tax investigation form) >> VBS >> Batch script(s) >> VBS script(s) >> downloaders and data exfiltration
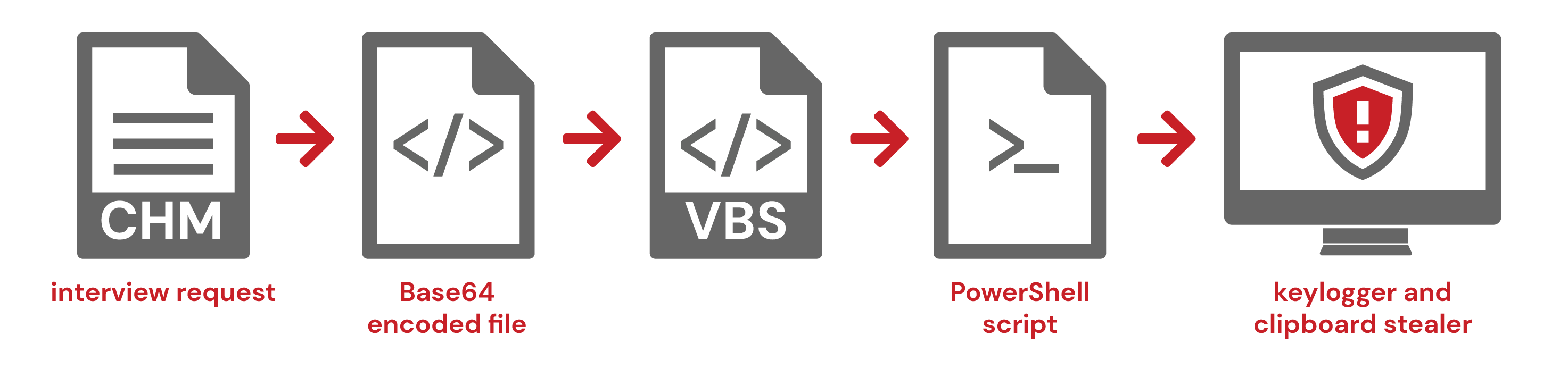
- CHM (interview request) >> Base64 encoded file >> VBS >> PowerShell script >> keylogger and clipboard stealer
Russian Threat Groups
APT29, a threat group believed to operate under the Russian Federation’s SVR foreign intelligence agency, is notable for complex and evasive file formats in their execution chains leading up to footholds on target networks.
- Targeting: Government and other sectors across multiple continents
- PDF (link) >> JavaScript >> HTML smuggling >> ISO, ZIP or IMG >> Cobalt Strike loader

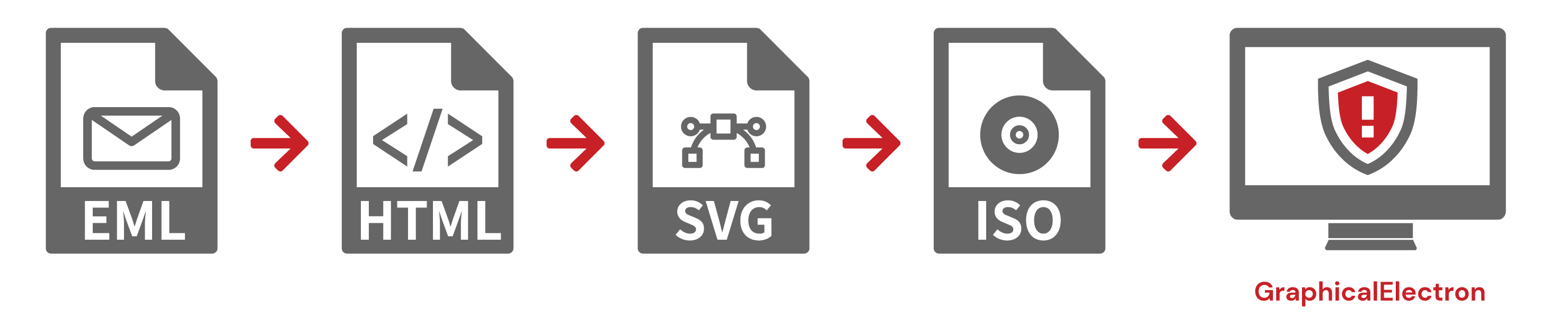
- Email >> HTML >> SVG >> ISO files >> GraphicalElectron
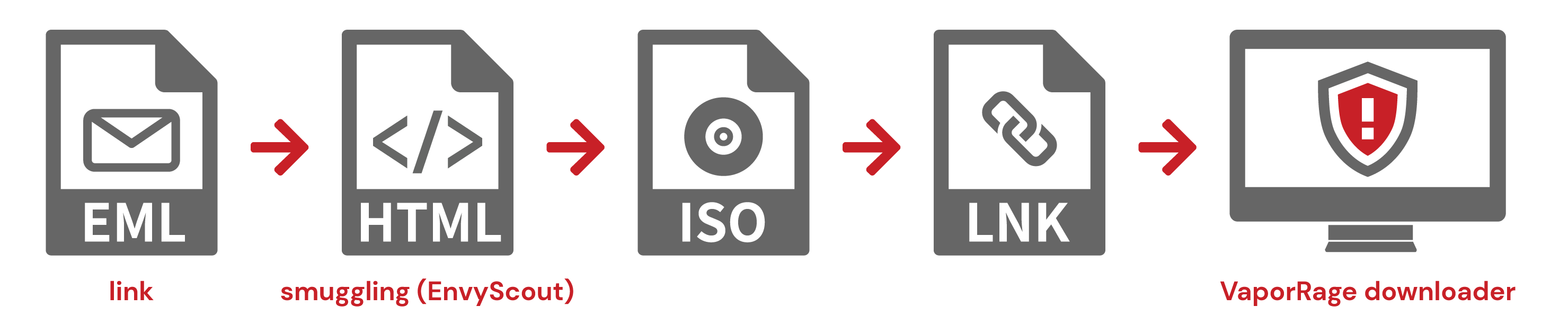
- Email (link) >> HTML smuggling (EnvyScout) >> ISO >> LNK >> VaporRage downloader
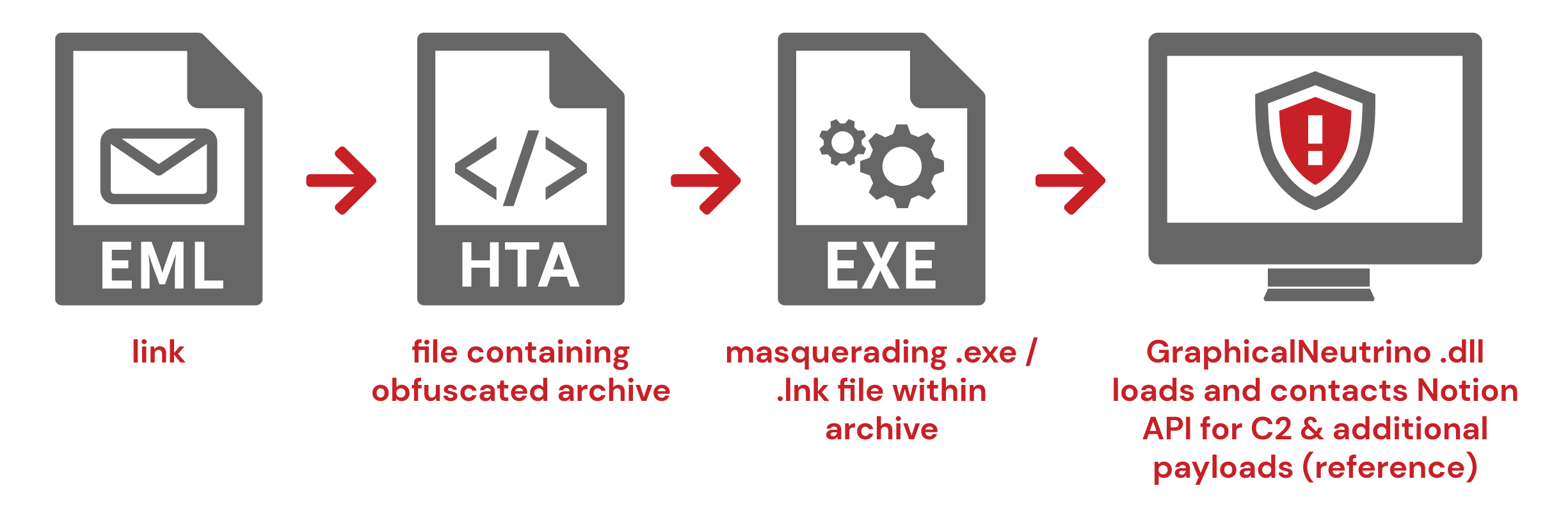
- Email (link) >> HTA file containing obfuscated archive >> Masquerading .exe / .lnk file within archive >> GraphicalNeutrino .dll loads and contacts Notion API for C2 & additional payloads (reference)
With APT29 activity, we can observe an evolving playbook that has been used over the years with a mix of staples such as HTML smuggling and abuse of legitimate cloud services for C2 and data exfiltration, but also integrating and experimenting with other methods of payload smuggling and embracing post-macros tradecraft. In addition to ISO files for container abuse and defense evasion, the group has utilized IMG and VHDX disk image formats, extracted from HTML content observed during spearphishing attacks. Further development in this area shows utilization of SVG image file content to encode smuggled payloads, effectively an extension of HTML smuggling.
Other Russian origin groups exhibit a similar appreciation for multistage file format attacks:
EMBER BEAR A/K/A Cadet Blizzard, Lorec53, UNC2589 (state sponsored – suspected GRU military intelligence agency)
- Targeting: Europe, NATO countries, North America, Defense, Government, Law Enforcement
- Email (attachment) >> LNK >> backdoors >> WhisperGate wiper

- Email (attachment) >> PDF, Word, JS, CPL files >> VBA macros, exploits >> PowerShell

UAC-0006 [1, 2] – financially motivated attacker targeting Ukraine with distribution of SmokeLoader trojan
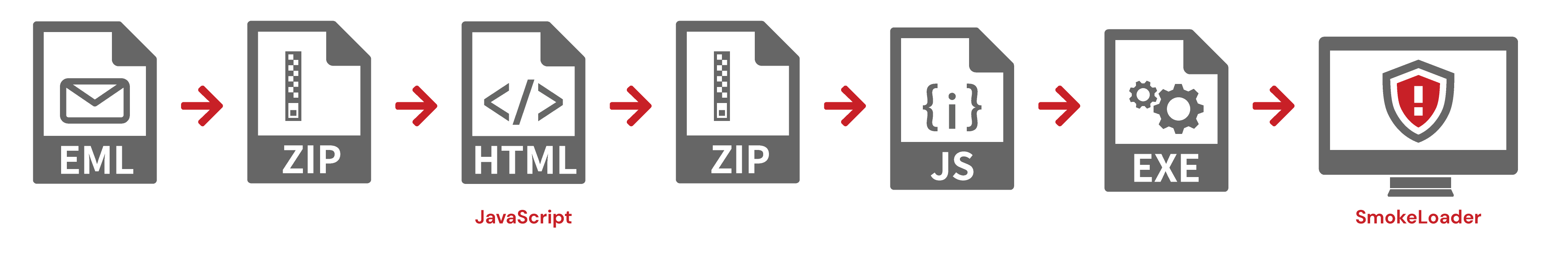
- Email >> ZIP >> HTML (JavaScript) >> ZIP >> JavaScript >> EXE >> SmokeLoader
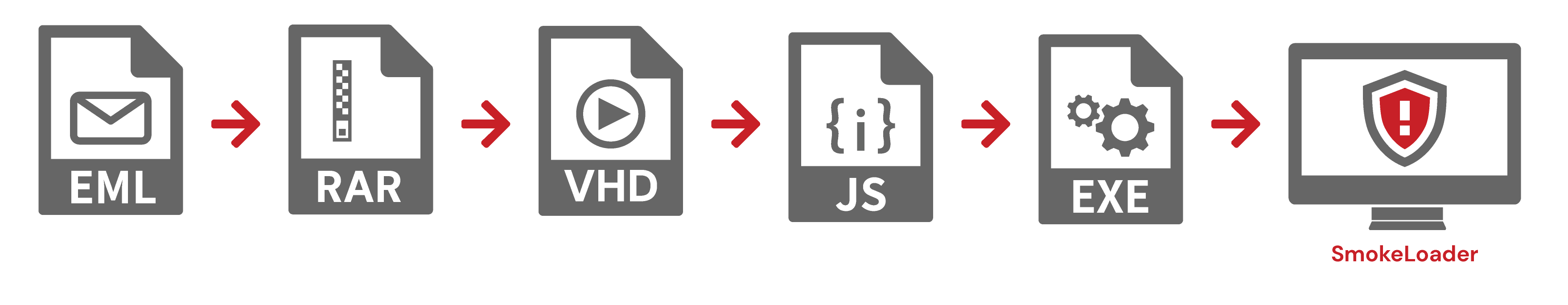
- Email >> RAR >> VHD/VHDX >> JavaScript >> EXE >> SmokeLoader
The Chink in the Armor Against Today’s Threat Landscape
One thing we note in the above analysis is that attacker tradecraft has evolved in recent years. Attackers are structuring their file based attacks to evade traditional security products. This includes the use of execution chains based on evasive, complex file formats that provide them with certain advantages against commonplace defensive controls. A robust capability here enables attackers to engage targets with a higher chance of success in establishing a foothold after gaining initial access. We believe that this fact is strategically significant in the adversary playbook, and therefore key for defenders to understand as we seek to defend against modern day threat actors. The following highlight important aspects of this situation:
- Gateway controls such as Secure Email Gateways (SEGs), antimalware, and phishing detection solutions inspect outer file layers, but modern techniques leverage complex, multilayered files formats. Gateway controls are bypassed and defeated because attackers smuggle payloads and nest data inside of carrier files. To be effective, controls at these layers must be able to see into files, decomposing them to the basic levels and scanning all layers.
- Many security architectures, particularly those that are zero trust focused, have placed significant levels of pressure on EDR tooling, relying on technology with a well understood evasion and bypass issues to defend against threats. Many of these architectures remove a critical control from the equation; the web proxy or secure web gateway. Many threats are delivered to end users over the web using techniques such as malvertising, blackhat SEO, drive-by downloads, and social engineering. Many organizations that have adopted security architectures like zero trust have removed the critical web gateway component entirely, and even those that are used often inspect only the outermost file layers, enabling threats to reach the endpoint unhindered.
- A strategy that places the weight of defense on endpoint controls only is tenuous at best, as these same threats have reached the endpoint and are in the process of executing — the literal last mile of mitigation space. This fact places significant pressure on end users to tell the difference between safe and malicious files, and asks them to be the last line of defense. At InQuest, we refer to this concept as the end user security gap.
Today’s defenses and security architectures face clear challenges, and are not optimized to the techniques used by modern attackers, as described above.
How InQuest Helps
In a world where the volume and complexity of cyber threats are escalating, the need for robust solutions to shield networks from file-borne attacks is critical. As a leader in the market of File Detection and Response (FDR) solutions, InQuest provides customers with a vantage point for detecting and responding to file-based attacks.
One solution at the forefront of protecting organizations from these threats is FileTAC, our comprehensive tool designed to forestall file-borne attacks efficiently and effectively. The core of our platform, FileTAC technology is also found in our Integrated Cloud Email Security solution, MailTAC.
Deep File Inspection Merged with Intelligent Analytics
A hallmark of FileTAC is the Deep File Inspection (DFI) technology, an intricate analysis engine that reveals threats concealed in encrypted channels and nested files. Incorporating InQuest Insights elevates this feature by adding an analytical depth, deriving actionable intelligence from massive data troves to facilitate proactive defenses against emerging threats.
Proactive Threat Detection and Response
A defining feature of FileTAC is its proactive posture towards threat detection. Through the integration of machine learning and behavioral analysis, it allows for a real-time response to emerging threats, ensuring that security teams are never caught off guard. This translates to a robust security control where threats are identified and neutralized swiftly, mitigating potential damage. Alongside InQuest Insights, your organization can leverage historical data and current intelligence to foresee potential threats, enabling organizations to not just react to threats but to anticipate and neutralize them before they can cause harm.
Automated Processes to Facilitate Threat Hunting
FileTAC eases the burden on security teams by automating complex threat-hunting procedures, thereby reducing the workload and allowing teams to focus on critical high-value tasks. Through automation, it eliminates the pitfalls of manual labor, preventing exhaustion and ‘alert fatigue’ which often result in missed indicators and unnoticed patterns.
Real-Time Malware Detection
In a cyber landscape where time is of the essence, FileTAC stands tall with its real-time malware detection capabilities. When leveraged alongside NetTAC, It grants teams a clear insight into the network activities, empowering them with the most recent tools to comprehend and act upon the data, thus fostering a dynamic and responsive defense mechanism.
Collaborative and Community-Driven Defense
InQuest Insights promotes a collaborative approach to security, fostering a community of defenders united in a common goal. Gain access to the most complete dataset anywhere, aggregated and curated from an array of public, private, and internal sources. InQuest Insights augments FileTAC’s capabilities by bringing collective intelligence to bear on cybersecurity, enhancing the system’s ability to identify and mitigate threats through shared intelligence and collaborative efforts. Additionally, Threat Actor Tracking lets you identify and track threat actor groups, their tactics, and techniques so you can proactively identify new threats specific to your organization or industry. Customers can even opt-in to share anonymized data around detected threats to alert fellow organizations.
Conclusion
As cyber threats evolve, solutions that marry efficacy with intelligence stand as the beacon of hope for organizations globally. The integration of our FileTAC solution alongside InQuest Insights creates a cybersecurity system that is not just robust but highly intelligent, offering a multi-faceted defense mechanism against file-borne attacks.
Leveraging the power of Deep File Inspection, predictive analytics, intelligent automation, and a collaborative approach fostered by Insights, FileTAC ensures a defense that is not just reactive but anticipatory, ready to tackle the cyber threats of today and tomorrow.
As organizations steer towards a digital future rife with unseen challenges, embracing a solution that is fortified with the brilliance of InQuest Insights isn’t just a choice, it’s a necessity. It is a step towards a future where security is no longer about responding to attacks but about foreseeing and forestalling them, promising a secure, resilient, and prosperous digital landscape.
Webinar On-Demand: Death by 1,000 File Types
Join our on-demand webinar to navigate the intricate threat landscape of today’s digital world. As security experts grapple with a myriad of file types used in attacks to circumvent stringent security protocols, we take an in-depth look at file-based threats. Our session focuses on the root causes of these challenges and how our tailored solutions address them, offering insight and strategies for effective security management.