Those who keep tabs on ransomware are no doubt aware of the Black Basta ransomware group. They’ve gained their share of notoriety since some of the group’s malicious code was first detected back in April of 2022. What is interesting here today is that in just the past two weeks, Black Basta deployments are on the rise. As many as 75 organizations have now been compromised – based on information posted on their leak site. This appears to be the result of a new deployment method used in the final stage of a QBot malware infection.
In this post, we cover four key points:
- A high-level overview of Black Basta ransomware and its attack sequence
- A few discoveries about the organization behind this particular ransomware
- A detailed run-down of Black Basta infection steps
- How organizations can guard against Black Basta
What is Black Basta and How Does It Work (At a High Level)?
BlackBasta is a cross-platform ransomware written in C++ and utilizes the ChaCha20 encryption algorithm. Black Basta IOCs include QBot, Cobalt Strike, and .basta extensions.
Essentially, QBot infections (also known as QakBot, QuakBot, QuackBot and Pinkslipbot – a common trojan malware which steals passwords) are delivered via a phishing email containing a malicious HTML file that invokes a fairly complex infection chain.
First, a QBot payload is deployed on the host. Next, a Cobalt Strike is launched. Cobalt Strike is a paid penetration testing product that enables an attacker to deploy an agent – known as ‘Beacon’ – on the victim machine. Beacon gives an attacker an arsenal of capabilities including command execution, key logging, file transfer, SOCKS proxying, privilege escalation, mimikatz, port scanning and lateral movement. With Cobalt Strike successfully deployed, the third and final step is executed. Black Basta is dropped and it’s game over for the victim machine.
Black Basta then drops a ransom note instructing the victim to visit their TOR website – which is nothing more than a chat server running on NGINX 1.18. Upon entering an ID and a captcha, the victim is connected to a person claiming to be part of Black Basta.
To see what would happen, InQuest researchers engaged the threat actors. Their demand was $35,000,000 for a four-computer infection- and they were unwilling to negotiate.
What Have We Learned About the Black Basta Ransomware Group?
From a little G2 with friends in Ukraine – as well as the exchange itself – InQuest Labs researchers gleaned a few interesting points about the Black Basta group and its persona:
- Black Basta possibly adopted their name from the Russian rapper known as Basta (notably banned from entering Ukraine after performing in Crimea after the 2014 invasion)
- Black Basta appears to use translation software – given odd grammar choices and language inflections that get lost in translation
- Black Basta does not have a good understanding of common corporate titles or hierarchy in the US
The Black Basta Attack Chain in Detail
In the initial infection stage, a victim receives a phishing email as the result of a hijacked thread. The attacker then employs a technique known as HTML smuggling – which consists of a benign-looking HTML file with an embedded password-protected zip archive. The victim is prompted to enter a password which unzips the archive and drops a VHD image. Once the user mounts the VHD, they are presented with an LNK file along with several decoy files. If the LNK is clicked, a malicious javascript or VBScript is launched which executes a batch file. This batch script launches the QBot DLL payload.
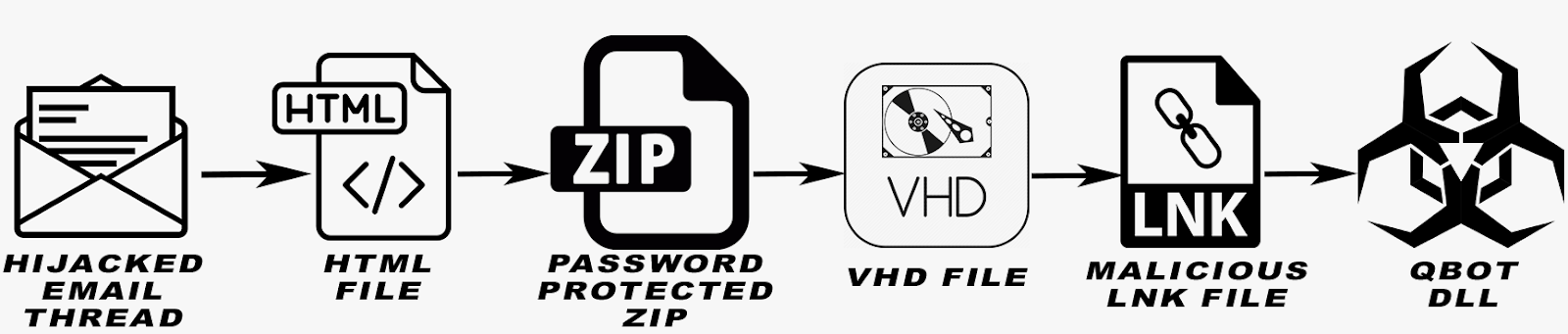
This leads to the secondary infection stage – the QBot infection. With a QBot DLL payload now launched, it injects itself into explorer.exe or wermgr.exe and begins to communicate with QBot C2s in its configuration file. From here, QBot downloads and deploys CobaltStrike to further compromise the victim, and to laterally compromise additional network hosts. With additional hosts now compromised, Black Basta is firmly rooted.

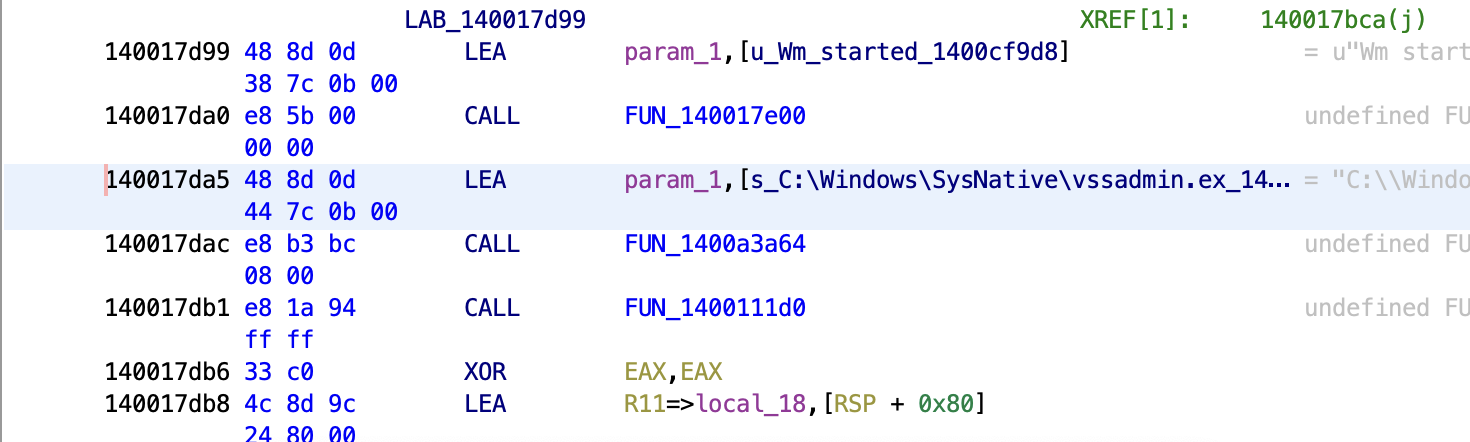
At this point, the third infection – Black Basta itself is deployed. File encryptions begin and a ransom note is dropped onto the desktop. Additionally, vssadmin is used to delete volume shadow copies – ensuring data cannot be recovered from backup.
The victim will notice that file icons have changed to a custom logo with a .basta extension:

The ransom note directs the user to visit a .onion site to contact Black Basta ‘for assistance decrypting their files’:
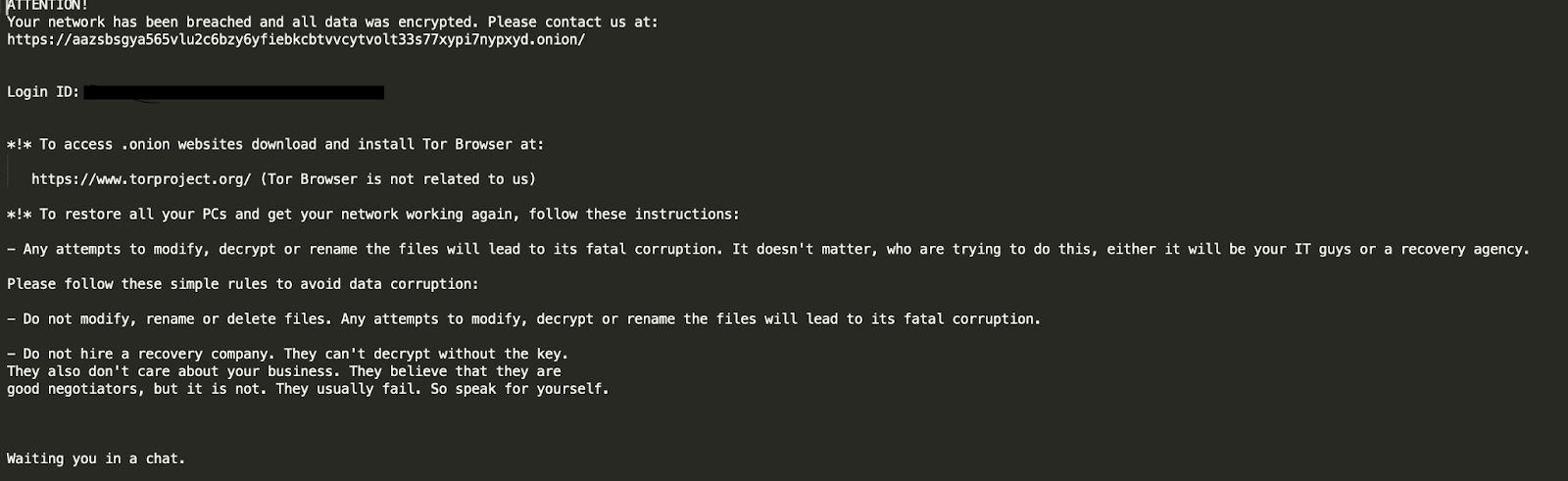
The TOR site
hxxps://aazsbsgya565vlu2c6bzy6yfiebkcbtvvcytvolt33s77xypi7nypxyd[.]onion/ has been in use since at least April 22, 2022. With that lifespan, the site is likely hosted on hardened infrastructure. Upon visiting the site, the victim is presented with a prompt for their unique login ID (provided in the ransom note) and a captcha.
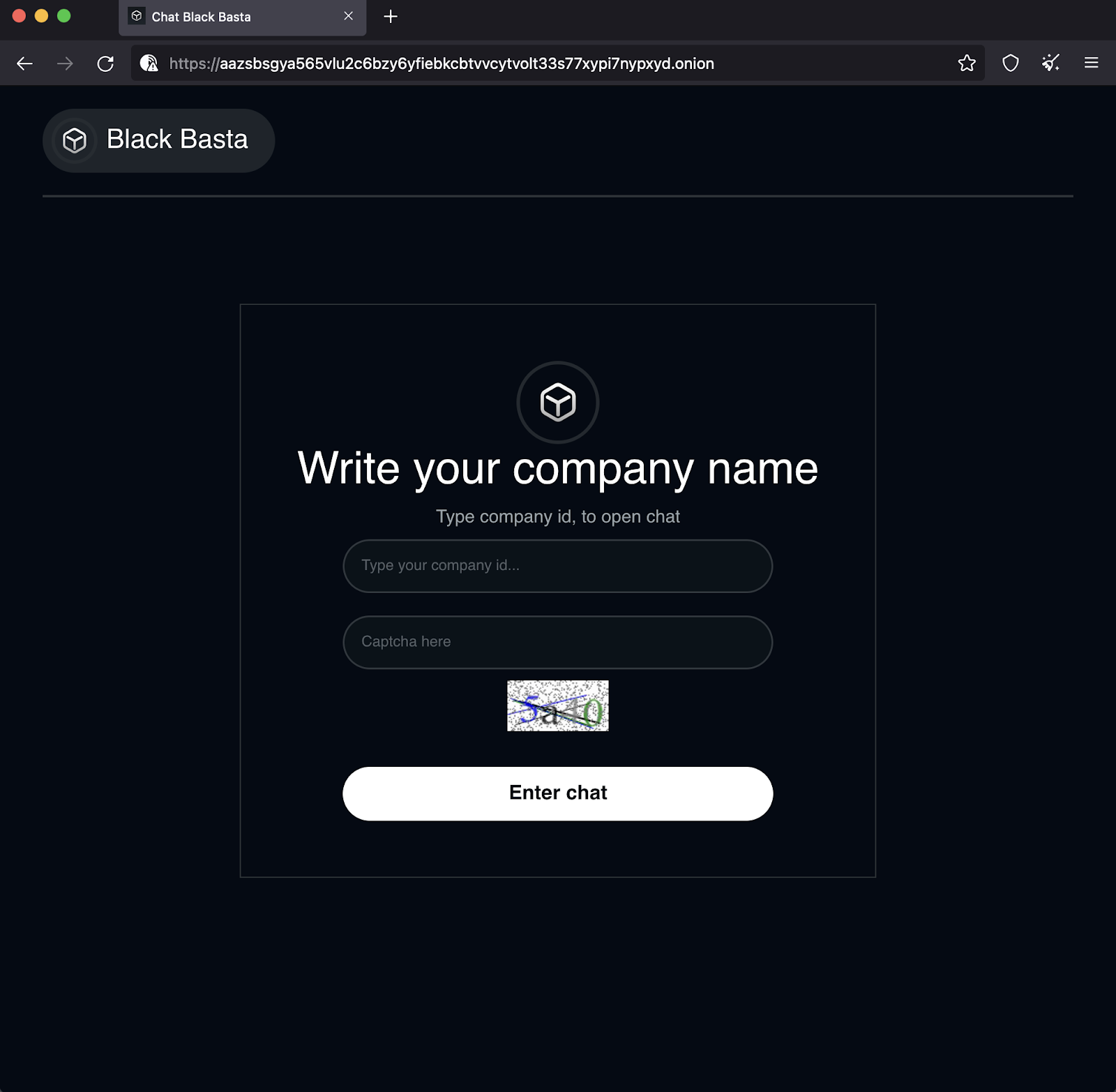
Upon entering login information, the victim is entered into an online chat application. Analysis of the web server reveals it is running NGINX 1.18 and utilizes JavaScript for a good portion of its functionality.
Here is our chat dialog:
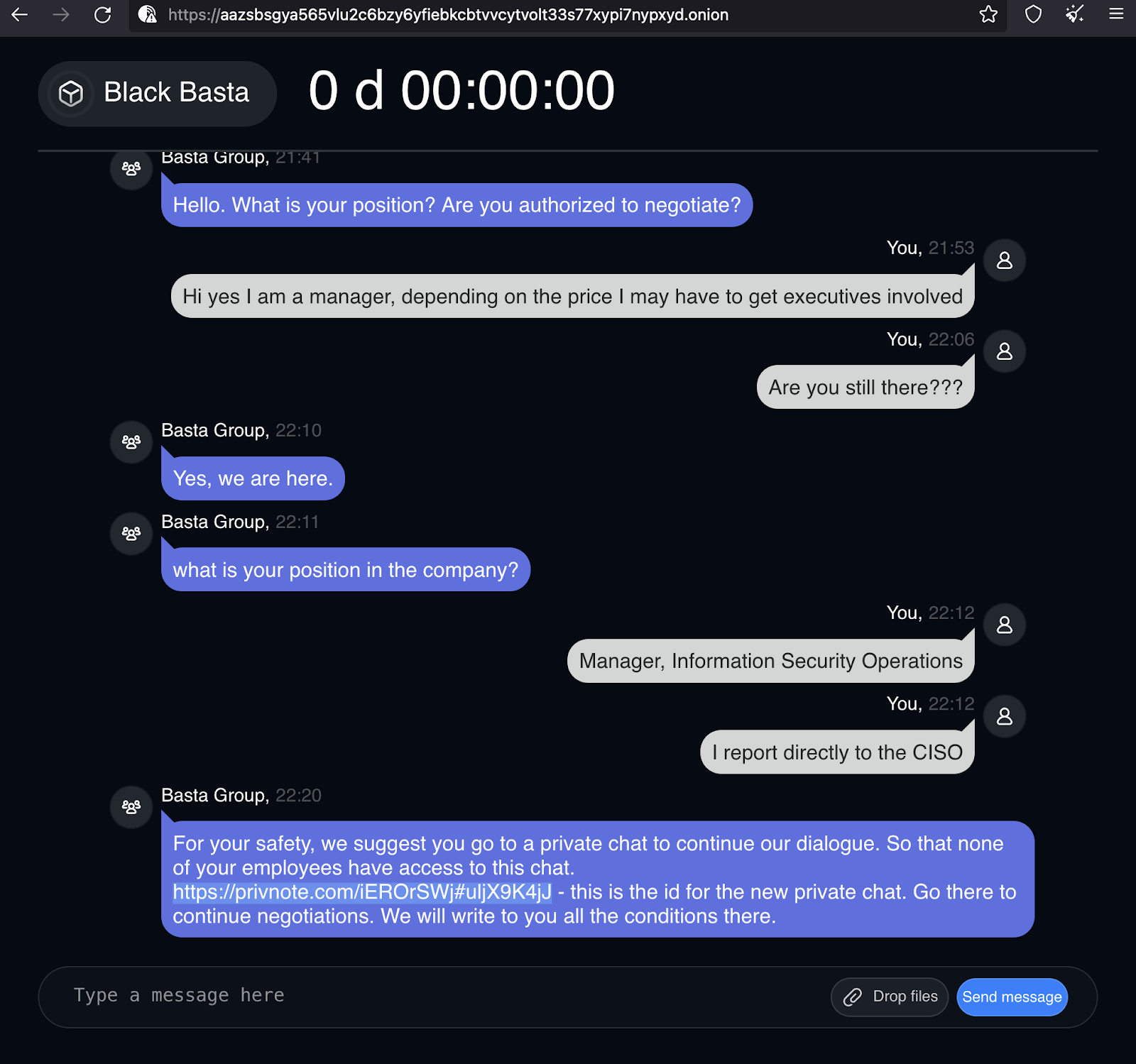
When the victim begins communicating with Black Basta, they are immediately questioned about their job title/role and if they are authorized to negotiate. The victim is then directed to follow a PrivNote URL to obtain a new login ID:
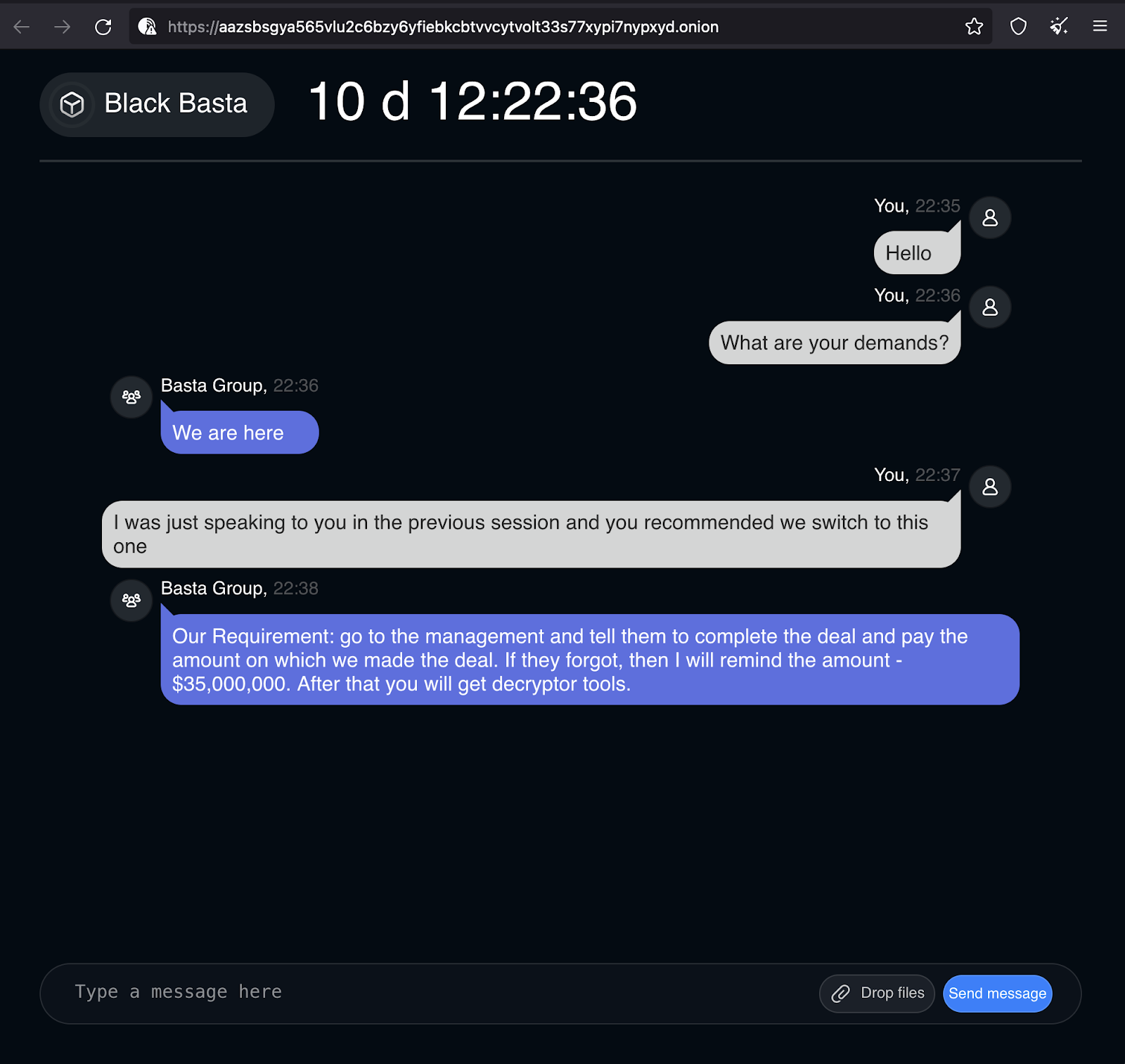
With the new ID, the attackers convey their demands in a passive-aggressive manner, demanding $35,000,000 for the decryption tools.
As noted earlier, language patterns reveal that Black Basta is likely using translation software. This can be deduced from the passive-aggressive inflection and choice of words – easily identified by anyone fluent in Russian and Ukrainian natives – but potentially lost on native English-speaking victims. As an example, the phrase “go to the management” is indicative of Russian culture ties, due to their persistent efforts to have victims quickly escalate the situation to management. As well, “If they forgot, then I will remind” carries passive-aggressive undertones from a Russian language perspective.
How to Protect Your Organization from Black Basta
Be aware, Black Basta is a very serious threat – and while some attackers may be willing to negotiate terms, these guys are not. That said, there are definitive steps you can take right now to sharply reduce your odds of being victimized:
First and foremost, educate your users on common phishing techniques and facilitate easy reporting of suspicious emails
Second, ensure your security defenses are up to date with Cobalt Strike signatures.
Third, leverage a detection and response solution that is capable of detecting each and every attack stage identified above. You should not have to rely upon a ‘patch quilt’ approach to detect and disrupt these attack chain steps. There are solutions on the market that can perform this seamlessly on your behalf. We’re biased to our own unique and effective approach in File Detection and Response (FDR), but the point is to have a fully capable detection and response solution. FDR is specifically equipped with countermeasures, e.g., threat detection engine (YARA), machine learning, malware detection engine, reputation, and spam score that can detect, alert, and/or invoke policy action on activity along the entire attack chain – from initial vector (email), through each stage of delivery, all the way to the payload drop. Below is a high-level overview of Black Basta-specific countermeasures:
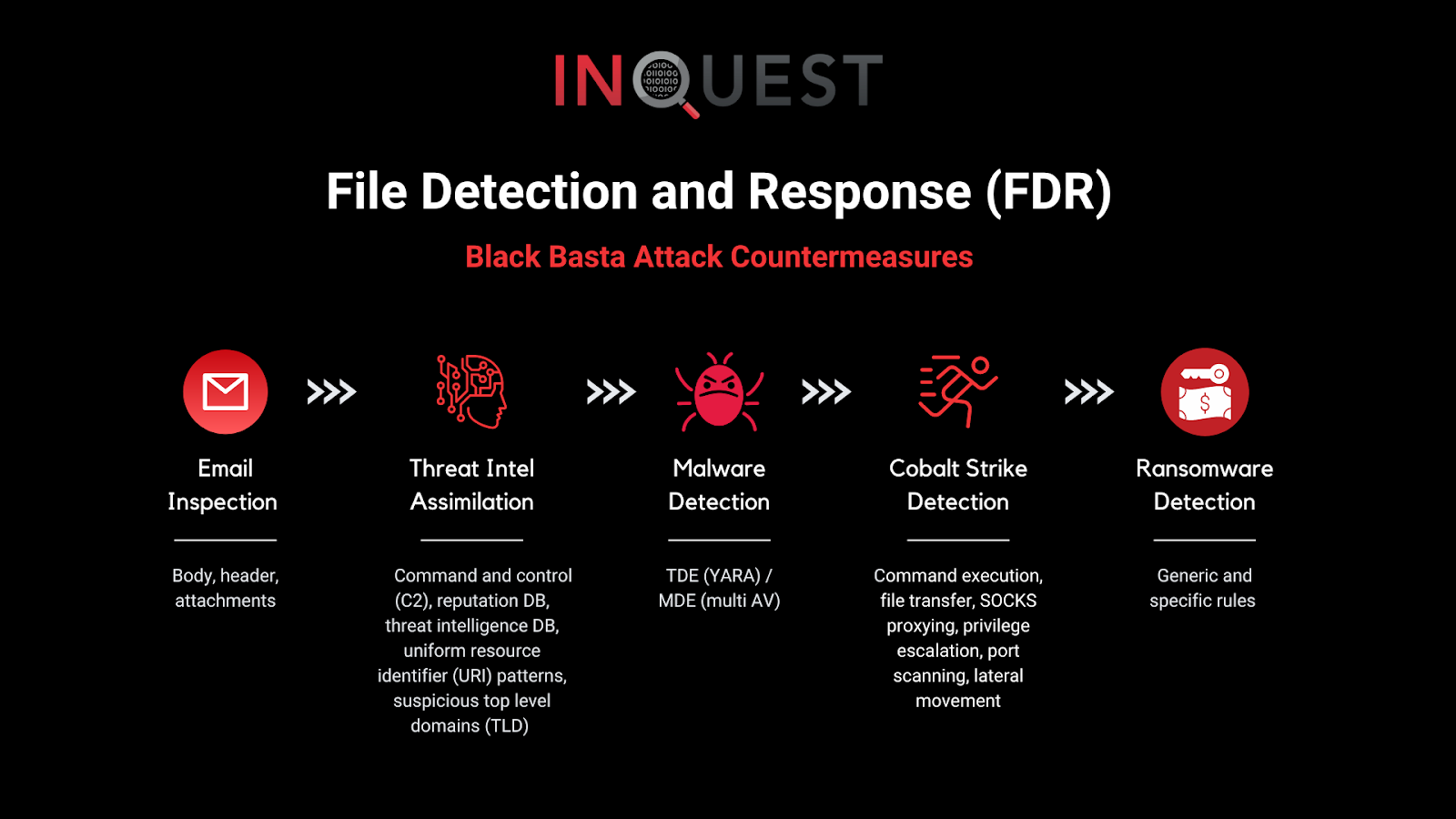
Of course, if we can answer specific questions about Black Basta, ransomware at large, or other forms of end-user security attacks involving files and end-user interactions, feel free to reach out. In the meantime, don’t let your guard down this holiday season!
Free Email Hygiene Analysis
Solid email security begins with proper email hygiene. There are a variety of email hygiene technologies and wrapping one’s head around them all is challenging. Try our complimentary Email Hygiene Analysis and receive an instant report about your company’s security posture including a simple rating with iterative guidance, as well as a comparison against the Fortune 500. Try it today!

