Calculating Return-on-Investment (ROI)
When you’re considering making an IT or InfoSec procurement, how do you determine what your return on investment (ROI) or return on security investment (ROSI) will be? The problem is that the standard calculation to evaluate investments is based on expected cash flow, in the form of revenue earned or expenses avoided: ROI, Net Present Value (NPV), and Internal Rate of Return (IRR). The total cost of ownership is commonly used for IT investments but is exclusively based on fees by totaling the initial purchase price plus ongoing support. Investments in cybersecurity are challenging to value using these standard methodologies, leaving frustration on all sides of the discussion.
To help guide the conversation and thought process, InQuest has developed multiple ROI Calculators that illustrate benefits with regard to time saved, volume processed, and capacity for organizational directors, hiring managers, threat hunters, security operation center (SOC) analysts, and email administrators. We provide sliders across these calculators for tuning variables to match your environment and level of skepticism around vendor claims.
Let’s take a walk through each of the five calculators and their intent. Note that not all calculators apply to all environments.
First, we’ll take a look at the calculator for Threat Hunting Depth.
Going Deeper with Threat Hunting
While several great resources are available describing what threat hunting is and how it can benefit your organization, it can be challenging to provide the proper resources or a dedicated team for such an activity. Threat hunting is the human-driven, proactive and iterative approach to searching through datasets to detect malicious, suspicious, or other business risks that have evaded detection by existing security tools.
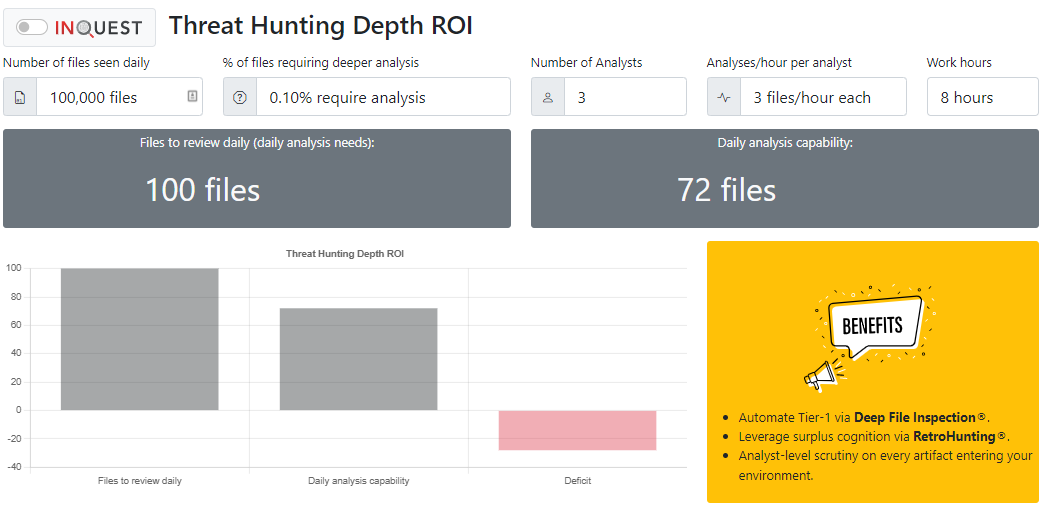
The threat hunting depth ROI calculator takes input from the volume of files seen daily, the percentage of files requiring additional analysis, the number of analysts on the team, and the rate at which each analyst can complete their review.
In this example, consider an environment that processes 100,000 files inbound daily. Of that volume, say .1% of these files require additional analysis and result in a daily review requirement of 100 files. Now consider your threat hunting team is staffed with three dedicated analysts, and their rate of review is approximately 3 hours per file. The staffing and analysis time creates a daily analysis capacity of 72 files and leaves a gap of 28 files that will not be analyzed based on the team’s ability.
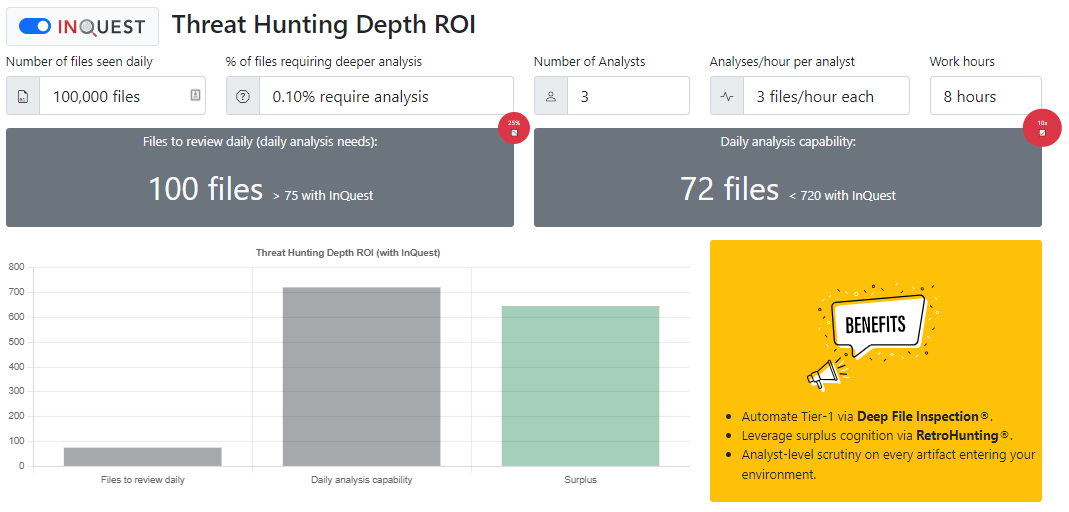
Based on user feedback/surveys collected over years, we conservatively estimate that the InQuest solution can reduce the number of files that require further analysis by 25%. Additionally, Deep File Inspection’s (DFIs) ability to decode, decompress, decompile, and decipher file content provides unsurpassed security visibility and increases the daily analysis capacity. The combined effect results in a higher capacity of 720 files daily with the same threat hunting team.
Shifting Focus Away from False Positives
False positives (FPs) cost your staff time. Lost time is easily calculated into wasted dollars, but this is only part of the story. Reviewing false positives is typically seen as a mundane task that can lead to fatigue and systemic turnover. If we can reduce the number of FPs being analyzed, we can redirect that captured time towards discovering missed threats (false negatives, FNs).
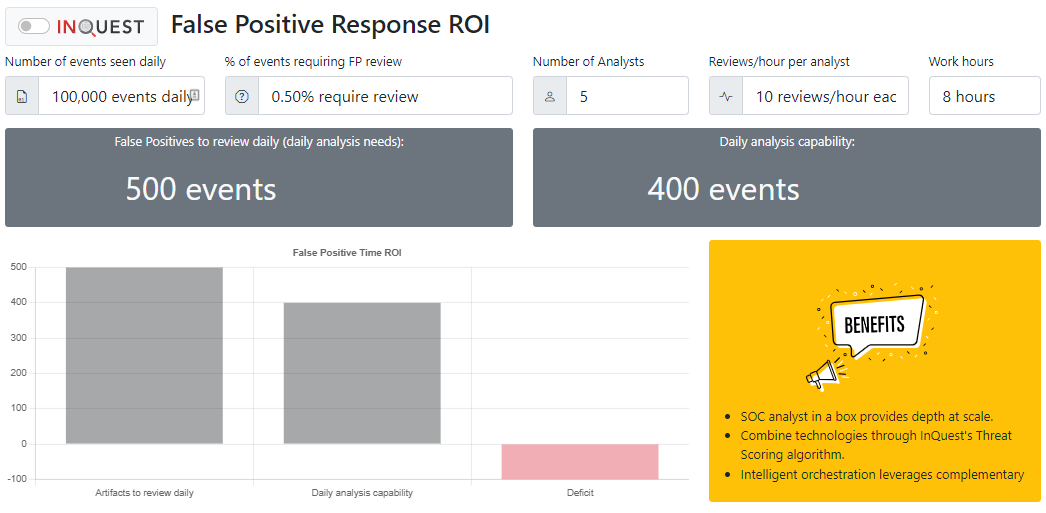
Our ROI calculator here aims to illustrate how much analyst time is burned on The false-positive response ROI calculator aims to identify the daily analysis capacity of members of the security operations team or dedicated signature/content experts. Whether the team is encountering blatant false positives or perhaps benign true positives, response time is needed to improve the efficacy of detection capability for the organization’s continuous security monitoring. While an iterative approach exists, the release of new and emerging threat signatures, coupled with in-house or user-defined rulesets, can justify a dedicated team. The following calculation uses the duplicate 100,000 inbound files daily. With five analysts and a rate of 10 reviews per hour for each analyst, the daily analysis capacity is 400 files. Unfortunately, if the % of events requiring FP review is set to .5%, there will be a deficit of 100 events daily.
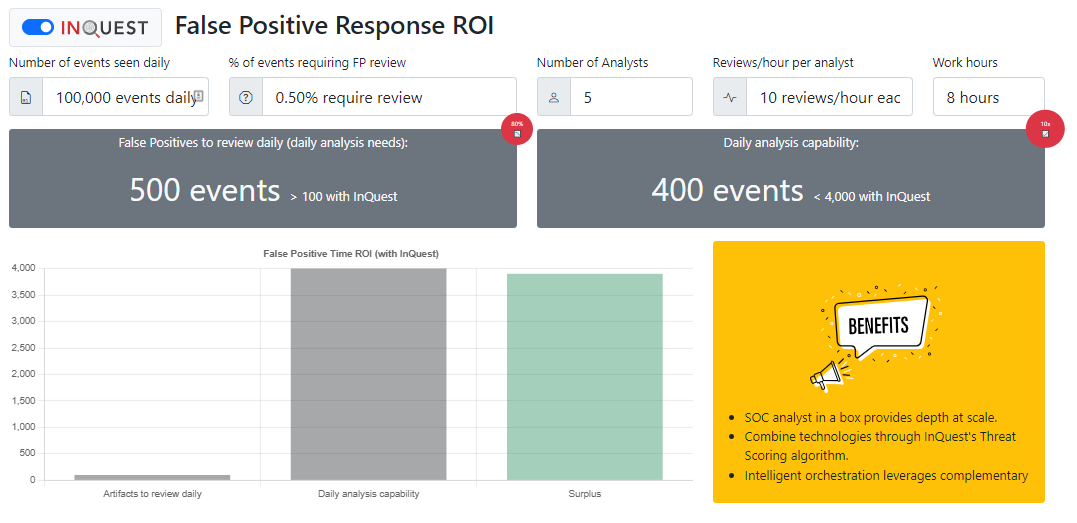
With InQuest SaaS Email security or the flagship on-premise product, false positives decreased by more than 80% due to the dedication of the InQuest Labs signature development team. InQuest utilizes Terabytes of real-world traffic daily to ensure the appropriate detection of dangerous files. Existing signatures are also reviewed for relevance and the opportunity to tighten the rules logic on a defined schedule.
The following calculations show the volume of events decreased to 100 files when utilizing an InQuest platform. The analysis capacity is also increased 10X with the same staffing level providing an opportunity for a surplus of event analysis bandwidth.
Reducing Email Administrator Frustrations
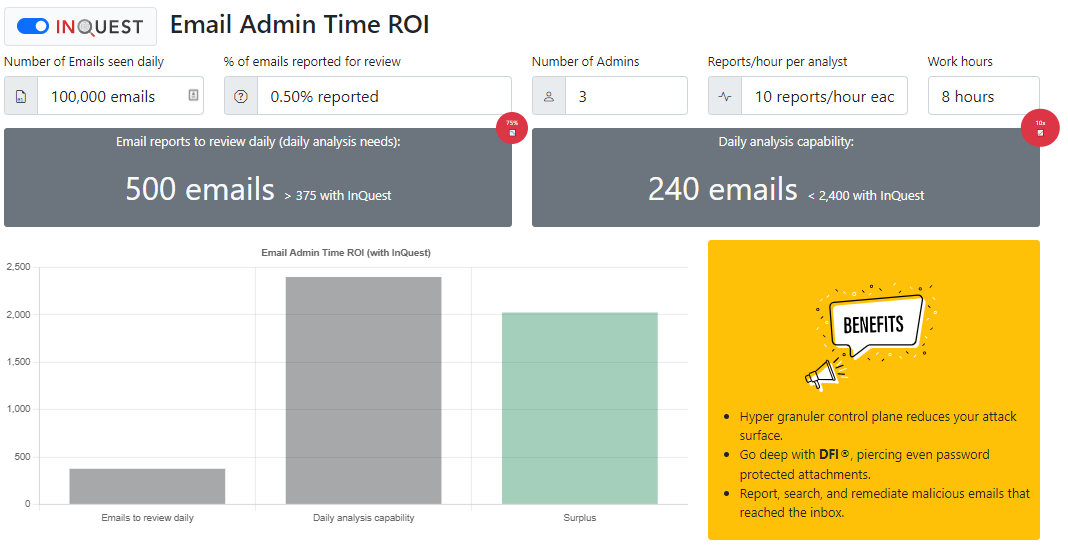
The email admin time calculator was designed to help email administrators and their management understand their capacity to review emails that have been placed in quarantine or reported for review by an end-user. According to Microsoft, only admins can manage messages that were quarantined as malware, high confidence phishing, or as a result of other mail flow rules. Admins can also view, release, and delete all types of quarantined messages for all users. For an organization that sees an average of our de-facto 100,000 daily file exemplar, and .5% of these emails require review, there is a daily need to review 500 emails. With three email admins and a rate of 10 reports per hour for each admin, there is a gap deficit of 260 emails that are not reviewed due to admin time constraints.
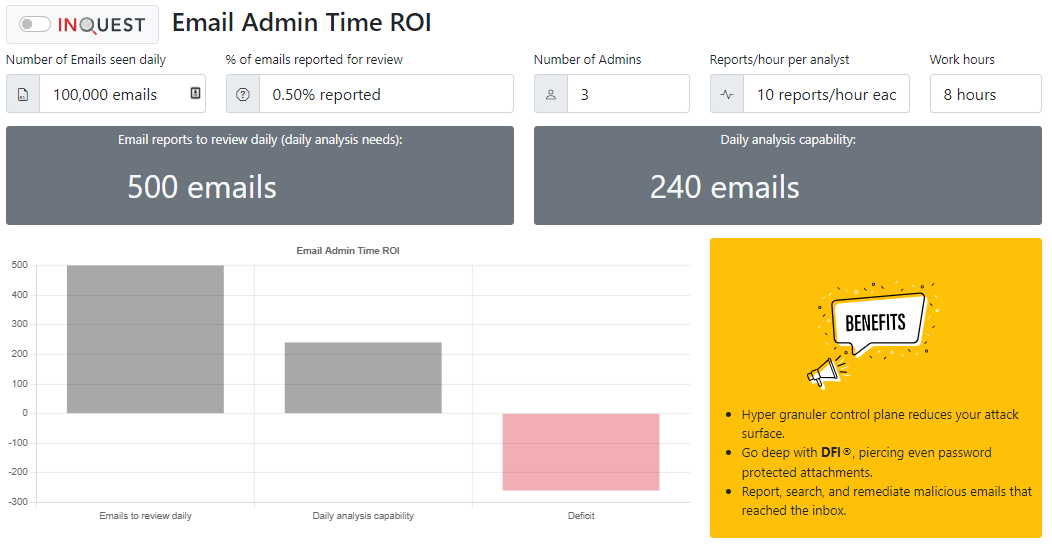
The InQuest SaaS Email security platform can reduce the daily analysis needs by 75% due to the sustained superior detection performance for phishing, malware content, VIP spoofing, and other email-borne threats. Analysis capacity is increased by 10X resulting in an appreciated surplus in time for the previously exhausted email administrators.
Reducing Email User Frustrations
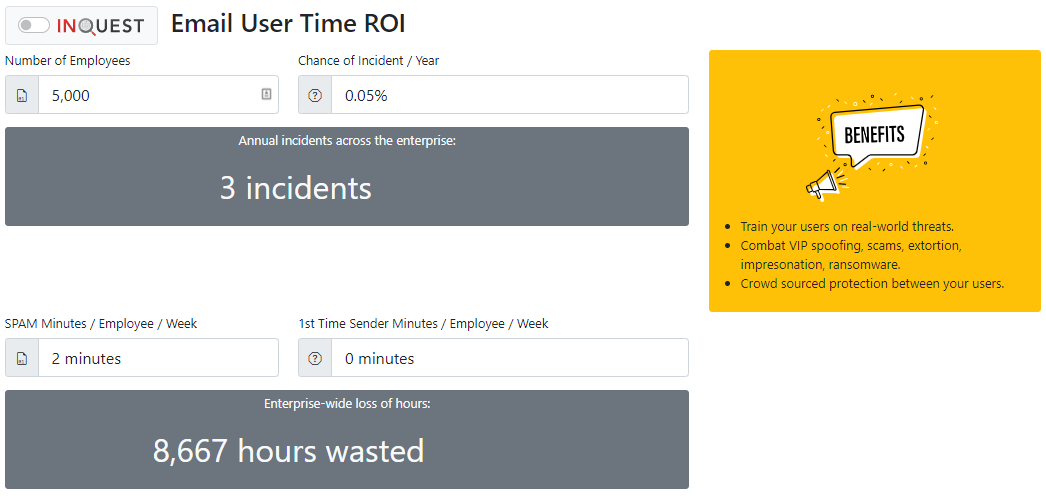
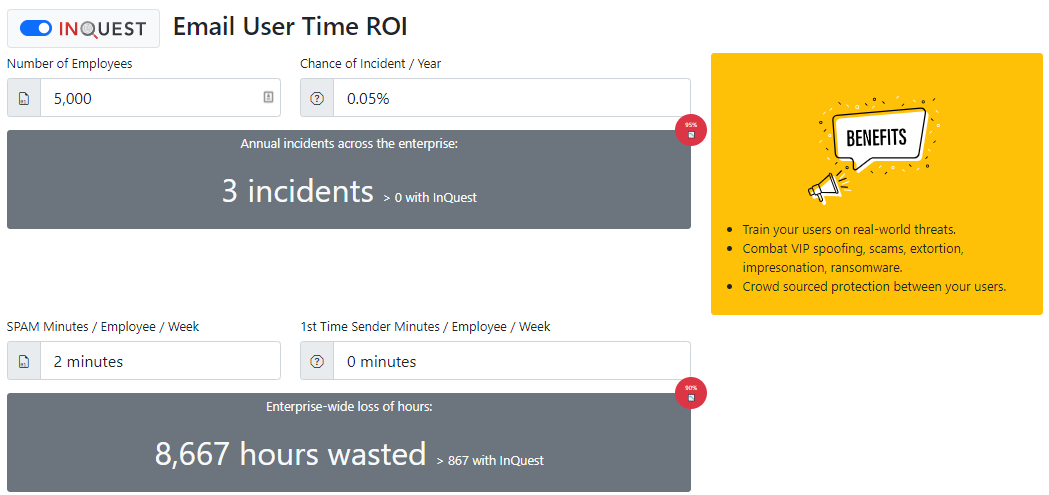
Another exciting calculation is computed for the time of the email user. The email user time calculator considers the number of employees and the chance of an annual incident. With an organization’s user base of 5,000 employees, .05% of compromise, there is an estimation of 3 incidents occurring every year. Additionally, for every SPAM email that an employee encounters, 2 minutes can be lost, resulting in over 8,600 lost hours of productivity per year.
InQuest SaaS email security takes the ball out of the (sometimes loose) users’ hands and lowers the chance of an incident by 95%. Due to the intuitive detection, bannering, and quarantine system, training time and costs are also reduced. Mitigating 90% of delivered spam lowers the hours wasted by nearly 8,000 hours over the year for the organization.
Calculating Return on Security Investment (ROSI)
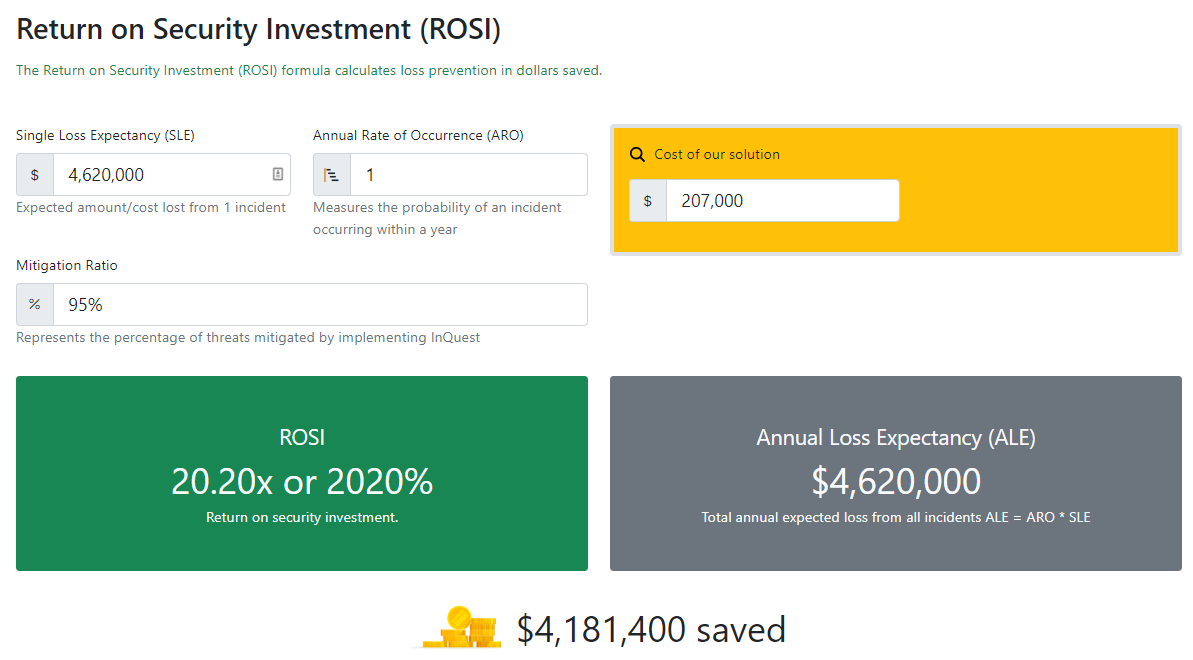
One way of calculating the Return on Security Investment (ROSI) involves taking the average cost of an incident and multiplying that number by how many incidents a business may experience in a given time frame. With an approximation of potential expenses, companies can then assess whether the price of the solution and the reduction in incidents it will bring is worth the investment. While costs are sometimes difficult to quantify, some models identify activities and assign costs according to actual use. Four process-related activities drive a range of expenditures associated with an organization’s data breach: detection and escalation, notification, post-breach responses, and the impact of lost business. According to the 2021 IBM Security Cost of a Data Breach Report, the average total cost of a ransomware breach is $4.62M. Taking this average as a Single Loss Expectancy and multiplying it by the Annual Rate of Occurrence, the Annual Loss Expectancy (ALE) is revealed. The ROSI is then calculated based on the procurement cost of the security capability. The ROSI is 20X the detection/prevention capability investment in this case.
InQuest can be deployed as either a SaaS or on-premise solution. The platform is compatible with existing cloud-based email providers such as Microsoft O365 and Google Workspace (GSuite). Our on-premise network sensors are capable of ingesting at rates from 1Gb to 40Gb in a 1RU rack mount solution. Get in touch to learn more, receive a free email security assessment, or receive threat intelligence feeds.
