Intro
Most everyone in the security industry has heard the colloquial proverb “Prevention is ideal, but detection is a must.” Concerning this mindset, two common approaches are evident to help fulfill the requirement for ensuring the security of an organization. Defense in depth describes the layered, redundant approach to cover a variety of attack vectors. Detection in depth describes the multiple detection points within an attack chain. In an effort to throw everything and the kitchen sink at the problems associated with cyber defense, InQuest has incorporated Detection in-depth methodologies alongside our intelligent orchestration to help Prevent, Detect, and Hunt the cyber-threats impacting our modern world.
Defense in Depth
Defense in depth is a well recognized and commonly deployed architectural approach to assist in the defensible security of your organization. It is implemented by placing multiple layers of defenses throughout the environment to provide a type of “castle approach” to security. The layered approach with intentional redundancies closes the gap associated with different attack vectors and increases the safety of the system as a whole.
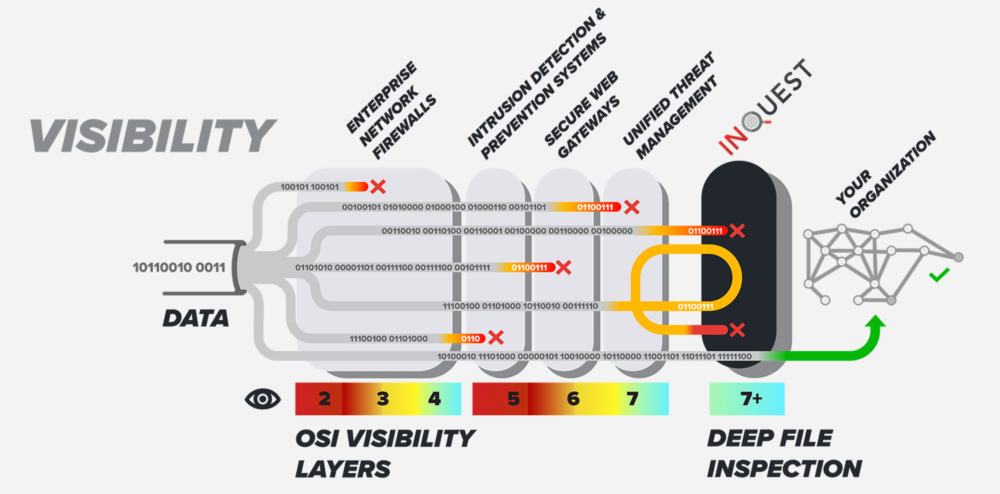
At InQuest, we have worked tirelessly to produce a turnkey SOC analyst in a box, throwing everything and the kitchen sink at the malicious content detection problem, then aggregating it all under a single pane of glass. It is still easy to acknowledge that there is no silver bullet to the ever-changing threat landscape. Considering that dilemma, InQuest provides intelligent orchestration to “play nice” and incorporate various technologies to supplement the detection of diverse threats. This includes bi-directional orchestration with multi-scanning and sandbox solutions, unique threat intelligence sources, and a seasoned signature development team augmented by machine learning all of which effectively drives the threat scoring algorithm to produce a single, digestible, well-balanced threat score.” Our ability to integrate a variety of Sandbox Detonation technologies, Multi-AV products, and event management solutions cements the best of breed technologies into your organization’s defensive posture.
Detection in Depth
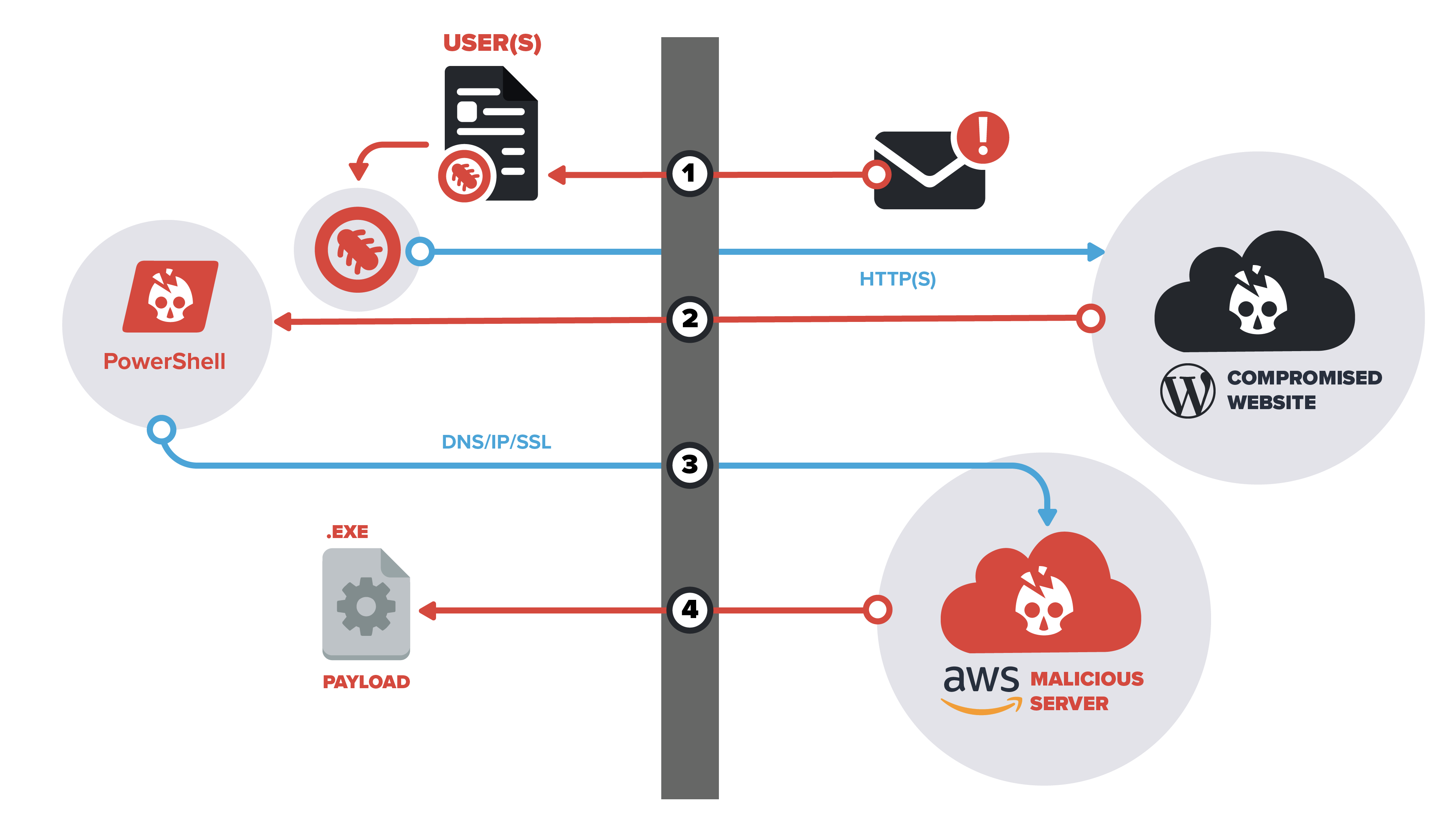
The concept of Detection in Depth is the design and implementation of multiple detection points for a single attack technique to effectively increase the probability of detection. This specific methodology is invoked by writing detection logic at different layers to uncover various Achilles heels. For example, the first layer will look for the coercive text or graphical asset included within the malware lure in a phishing email. The identification point can move to various fileless malware pivots to include techniques hidden with scripting or development technologies like ps1, hta, mshtml, vba., etc. Within, there are commonalities in campaigns in the communication patterns for items like cookies or URI patterns. Additional indicators to include SSL certificates, known-bad IPs and domains, can effectively attribute to previously identified attacker infrastructure. At InQuest, we consider complete coverage when we check off all of the above boxes for a given threat actor or campaign.
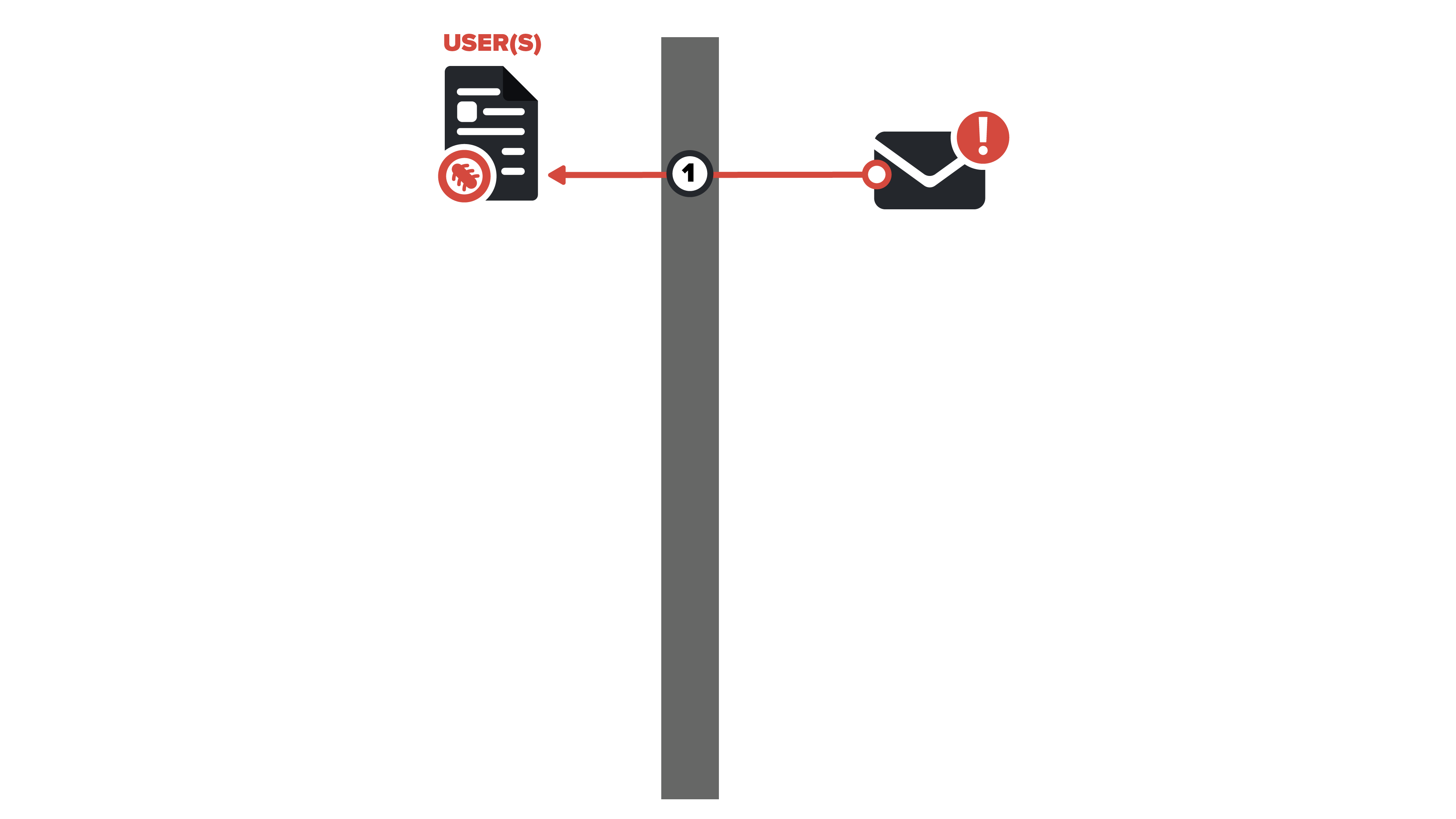
1. Initial delivery of the email lure
The first detection point within the Detection-in-Depth sequence is the identification of the initial email. There is a variance of different mechanisms that can be weaponized within the stage. Common implementations run from invoice-type malspam, generic phishing attacks, to well-written targeted attacks on users and organizations
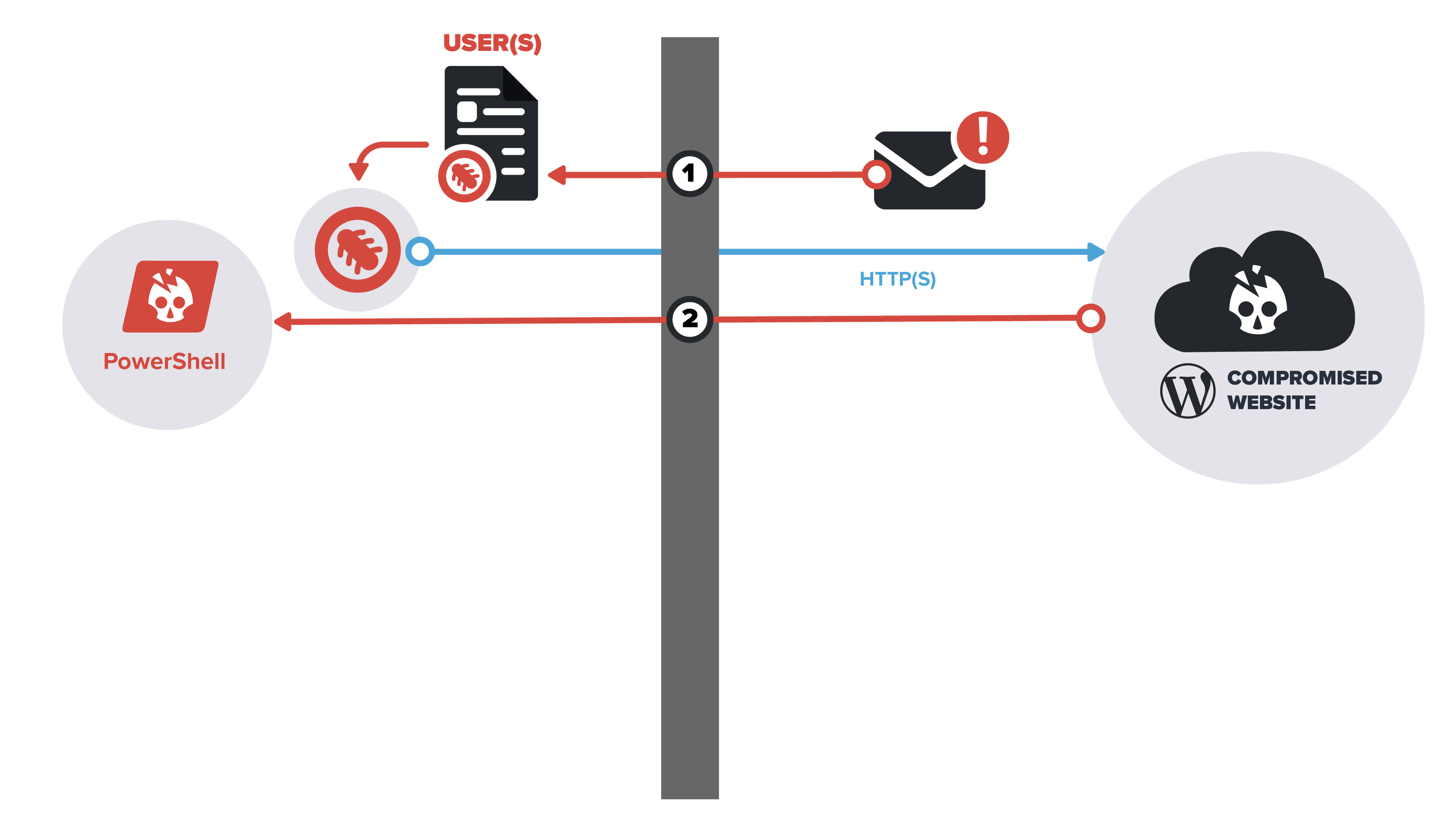
2. Pivot Detection and header analysis
The second detection point looks to identify the subsequent pivots from the carrier document. The scrutinization of web-based protocol headers and session destinations derived from the initial carrier document provides insight into the subsequent steps of the attack chain. Whether this point implements the acquisition of the second stage payload or intermediary file-less malware, additional detection capability is presented.
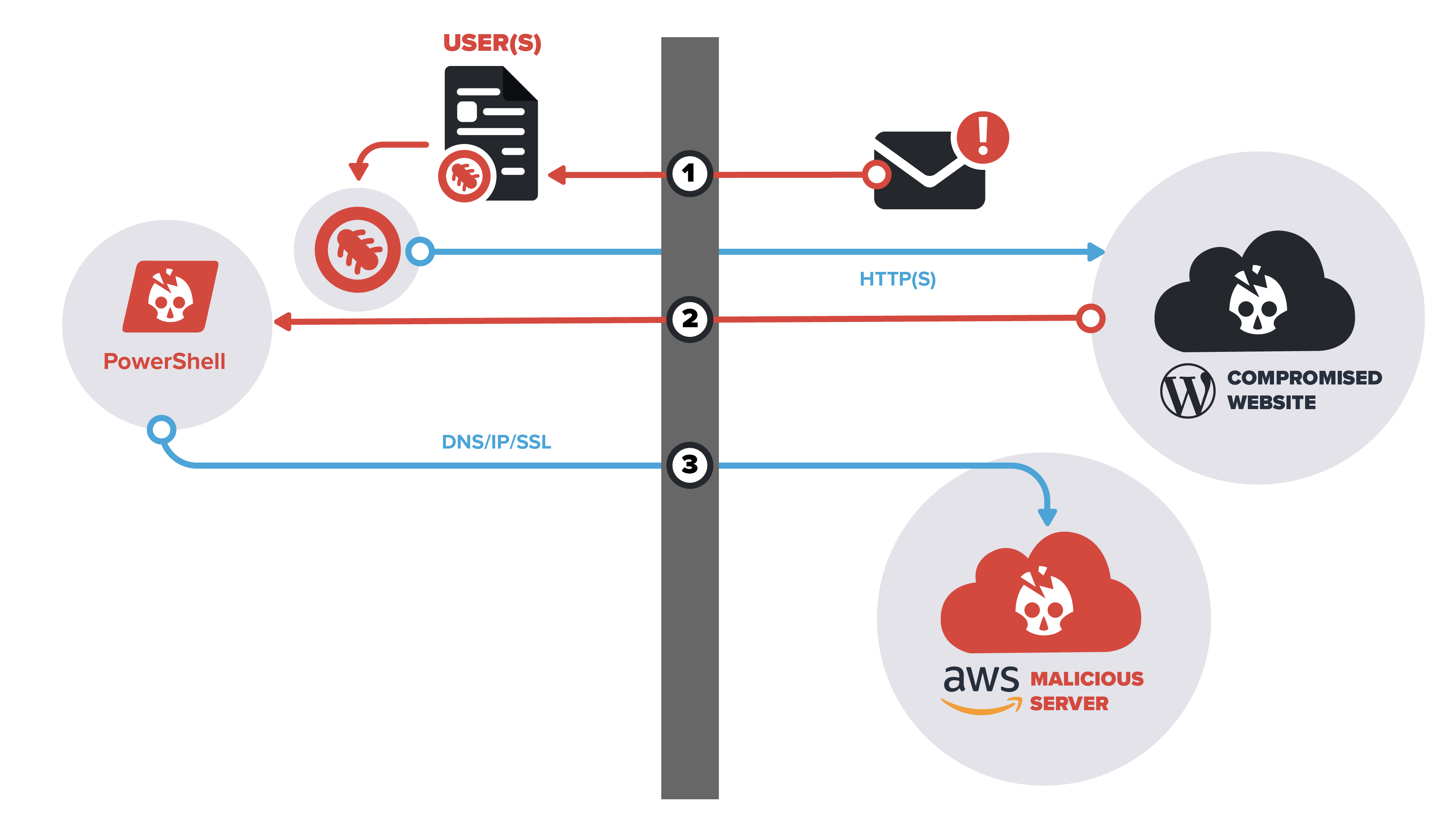
3. Command and Control breach detection
InQuest’s platform constantly monitors command and control (C2) communications for signs of anomalous activity. Cognizance of the latest C2 nodes through threat intelligence is key for detecting this activity. Our C2 detection engine alerts you if any of those nodes are seen touching your network, so we not only focus on what is being said but also who is saying it. The InQuest Labs Team publishes daily updates of known C2 artifacts globally, which are then flagged in our UI for further investigation. Research and empirical observations have provided a glorious lead time on many indicators; up to 357 days and an average of 192 days before disclosed to the general public.
4. Delivery of final payload
Delivery of final payload The final stage of the attack chain occurs when the malicious payload is downloaded and installed on the victim’s machine. Considering the variety of today’s perpetual malware, the intent of the compromise can vary from stealing credentials, personal records, ransomware payments, or even staging to attack other systems.
Conclusion
While continuing to emphasize “Prevention is ideal, but detection is a must.”, we have covered two common approaches to help check the boxes for protecting the security of an organization. Defense in depth describes the layered, redundant approach to cover a variety of attack vectors. Detection in depth describes the multiple detection points within an attack chain, culminating the effort to throw everything and the kitchen sink at the problems associated with cyber defense. InQuest provides Detection in Depth anchor points alongside our intelligent orchestration to help Prevent, Detect, and Hunt the cyber-threats impacting our modern world.

