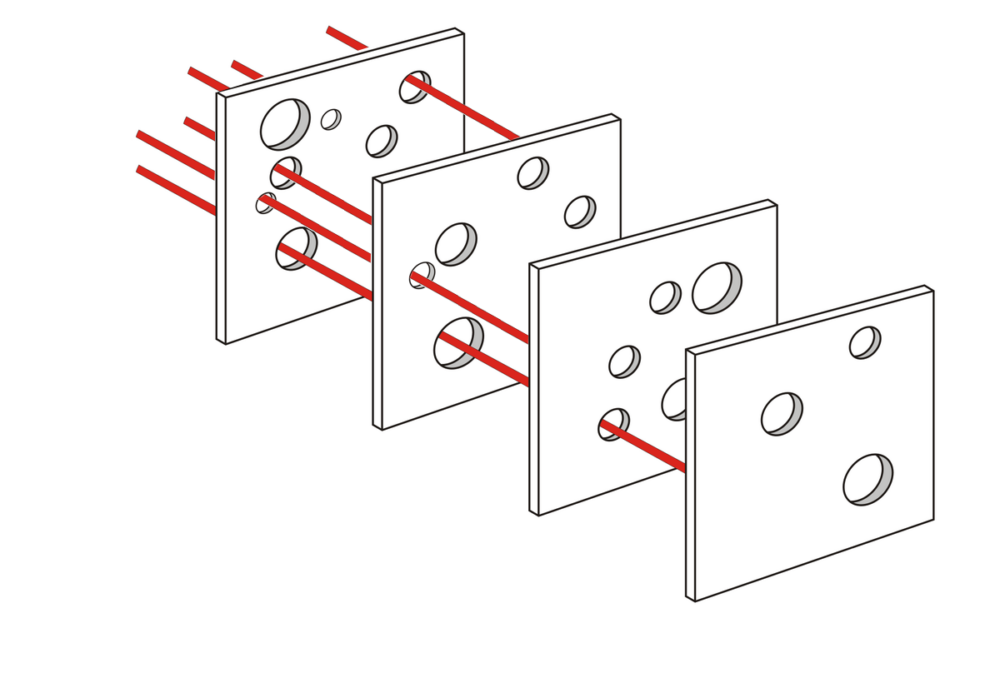
We believe that any security stack, in essence, follows the Swiss cheese model. With each slice of cheese representing a security product, and each hole representing some bypass or evasion. Following best practices and employing a Defense-in-Depth model results in a stacking of these slices, each additional stack reducing the exposure window and minimizing the overall risk to a computing environment.

Network defenders benefit from overlapping layers of security inspection. Examples of which may include:
- Pairing static / heuristic analysis with dynamic analysis.
- Combining host-based and network-based inspection.
- Leveraging a variety of threat intelligence feeds.
Traditionally the Security Information and Event Management (SIEM) system has been the central point of alert aggregation, correlation, reporting and visualization. More recently we’ve seen a rise in security orchestration products which provide a framework to actively mesh across and plumb data between security products.
There’s an undeniable benefit to correlating output from a variety of sources to reach a security consensus. We’ve been doing it for years as SOC analysts and that’s evident in our product through our mantra of “play nice with others”. Towards that effect there are a variety of active integrations that we support. By “active” we mean that the results from the integration are factored into the threat score generated by InQuest.
We have active integrations for MultiAV, sandboxes, and reputation feeds. We also offer passive integrations with SIEM, WCF and IPS. In this article, we’ll focus specifically on our experiences with sandboxing or detonation technologies.
Along with this post, we are announcing the release of our open source Python multi-sandbox API library. Read below for more information.
Sandboxes
The general idea behind automated malware analysis systems, commonly known as sandboxes, is to execute malicious software in an environment where it can’t cause any harm, and monitor its behavior. This can serve as a starting point for a more thorough investigation by a malware analyst, an automated extraction tool for indicators of compromise (IOCs) that can be used to write signatures, a way of detecting characteristics attributable to known threat actors, or as one line of defense with the ability to alert on malware. All the sandboxes we’ll discuss have a similar baseline of features useful for dynamic analysis. They track network, registry, API calls, file activity, conduct complete memory analysis, collect screenshots of the malware as it runs, perform static analysis of submitted files, and more. They then aggregate all of this information and provide a comprehensive report. By executing (or “detonating”) samples and looking for suspicious behavior, these sandboxes can find “zero-day” malware that passes static anti-virus signatures. Analysts can then use the IOCs derived from this analysis and high-level techniques extracted from the malware to write signatures for antivirus and intrusion detection/prevention systems, as well as track malware authors and even attribute attacks to a malicious actor or group.
For a recent example of a case where sandboxes would be an invaluable asset, we can look at DDE. This macro-less technique allows attackers to execute malicious code through Word documents, Excel spreadsheets, and even Outlook emails. At the time of its initial public reveal, no antivirus vendors had signatures that would catch such attacks. However, sandbox systems simply open the document, automatically click through the warning prompts, and execute and analyze the malicious payload.
Another similar example is this CSV injection technique. Again, existing antivirus signatures would not detect these malicious spreadsheet documents, but a dynamic sandbox approach would have no problem alerting on the spreadsheet software suddenly spawning external processes.
Sandbox Detection and Evasion
One issue that has grown alongside the popularity of sandboxes is sandbox-aware malware. Since malware authors typically do not want security researchers picking apart their handiwork, they will often include sandbox detection and evasion techniques in the malware they create. By looking for debugger hooks, virtual machine or sandbox artifacts, or even trying to detect human interaction and wear and tear, this malware attempts to determine whether it is being run inside a sandbox; if so, it shuts down or changes its behavior to hide its tracks and prevent analysis.
There are innumerable techniques for sandbox detection, and researchers as well as malware authors will no doubt continue to find more. The most popular and widely used techniques are documented by tools like Paranoid Fish (“pafish”), Virtual Machines Detection Enhanced (VMDE), and Anticuckoo. By studying the techniques used by these tools and sandbox-aware malware samples, sandbox authors are often able to develop ways to hide their traces and trick malware into executing normally. Many of the sandboxes we discuss in this post include such “anti-evasion” technology. The presence of evasion techniques themselves are often used as a detection mechanism – sandboxes will flag a sample as suspicious if it seems to be looking for traces of being run within a sandboxed environment.
We’ll explore in more detail some of the most popular automated malware analysis systems: Cuckoo Sandbox, the FireEye AX Series, Joe Sandbox, VMRay Analyzer, and Falcon Sandbox (previously VxStream). All of these sandboxes are supported active integrations for InQuest.
Sandbox Comparisons
| Cuckoo Sandbox | FireEye AX | Joe Sandbox | VMRay Analyzer | Falcon Sandbox | |
|---|---|---|---|---|---|
| On-prem | Free | $ | $ | $ | $ |
| Free Cloud | Limited | x | Limited | x | Limited |
| Paid Cloud | x | x | $ | $ | $ |
| Enterprise Support / Consulting | $ | $ | $ | $ | $ |
| Web Interface | ✓ | ✓ | ✓ | ✓ | ✓ |
| Web API | ✓ | ✓ | ✓ | ✓ | ✓ |
| Multiple Report Formats | ✓ | ✓ | ✓ | ✓ | ✓ |
| PCAP Export | ✓ | ✓ | ✓ | ✓ | ✓ |
| Memory Dump | ✓ | x | ✓ | ✓ | ✓ |
| Screenshots/Video | ✓ | ✓ | ✓ | ✓ | ✓ |
| Anti-Evasion Features | x | ✓ | ✓ | ✓ | ✓ |
| Out-of-Band Analysis | x | x | x | ✓ | x |
| Bare Metal Analysis | ✓ | x | ✓ | x | x |
| Windows Analysis | ✓ | ✓ | ✓ | ✓ | ✓ |
| Android Analysis | ✓ | x | ✓ | x | ✓ |
| Mac OS X Analysis | ✓ | ✓ | ✓ | x | x |
| iOS Analysis | x | x | ✓ | x | x |
| Linux Analysis | ✓ | x | x | x | ✓ |
| Document Analysis | ✓ | ✓ | ✓ | ✓ | ✓ |
| URL Analysis | ✓ | ✓ | ✓ | ✓ | ✓ |
| YARA Support | ✓ | ✓ | ✓ | ✓ | ✓ |
| 3rd Party Integrations | ✓ | ✓ | ✓ | ✓ | ✓ |
Cuckoo Sandbox

Cuckoo Sandbox is the de facto open source automated malware analysis platform. It is extremely flexible in that it can run with most virtualization software (VirtualBox, VMWare, etc), and leaves setup of the virtual machines used for sandboxing entirely to the user. Cuckoo can also be extended with custom YARA rules and its complete Python plugin system to add whatever functionality you might find missing.
Cuckoo Sandbox’s user-mode agent and use of widely available virtualization technology leaves it open to common sandbox evasion techniques, so it is up to the user to take steps to enhance their VMs if they wish to analyze evasive malware without being detected.
Cuckoo Sandbox offers a free online version with some limited functionality at malwr.com, and has consultancy services available for those who need enterprise support, training, or other technical assistance.
Cuckoo Modified
In 2014, Brad Spengler and Optiv released a fork of Cuckoo with a number of improvements over the mainline 1.x version. Many of these improvements have since been reimplemented upstream, and Cuckoo 2.0 contains many new features and improvements that are not found in the fork. For more information, see the Optiv blog post, and the fork’s GitHub repository.
FireEye AX Series
The FireEye AX Series are physical appliances designed to perform automated malware analysis in support of large enterprise environments. Their software integrates with other FireEye products and third-party antivirus suites, and supports custom YARA rules. The analysis technology, FireEye Multi-Vector Virtual Execution, or MVX, is “not a sandbox,” but a “Virtual-execution based detection engine.” In short, FireEye aims to bypass the evasion problems that plague sandboxes by implementing a proprietary hypervisor specifically designed to avoid detection.
Joe Sandbox
Joe Security offers a number of different sandbox options for different needs. For the purposes of this post, we’ll refer to these products collectively as “Joe Sandbox”; note that they are listed separately on the Joe Security website as “Joe Sandbox Cloud,” “Joe Sandbox Complete,” “Joe Sandbox Ultimate,” etc.
Joe Sandbox is based around the idea that putting together the best parts of a number of different analysis techniques will provide the best results. To this end, they employ hypervisor-based monitoring from a kernel-mode agent, static and dynamic code analysis, C decompilation, execution graph analysis based on malware control flow, generic static instrumentation which modifies programs before runtime in order to better track its internals and avoid detection, and many other features. All of these different types of analysis come together in a consolidated report to give analysts a complete understanding of the analyzed samples actions.
Joe Security offers a free online version with some limited functionality at joesandbox.com. There are also some public sample reports available on their website.
VMRay Analyzer
VMRay Analyzer sets itself apart from the rest by taking an agentless approach to sandboxing. Where other sandboxes have an agent running within the target system to record malware activity and communicate with the sandbox server, VMRay is implemented at the hypervisor level, outside of the system being monitored. Since there are no agents or hooks inside the VM, the sandbox itself is undetectable by malware. On top of that, VMRay includes a number of features meant to counter common VM detection and evasion methods; their system passes all the standard checks implemented by pafish, VMDE, and anticuckoo.
Although VMRay currently only supports Windows analysis, Android and Mac OS X support are roadmapped for future versions.
There are a few publicly available sample reports on VMRay’s website.
Falcon Sandbox
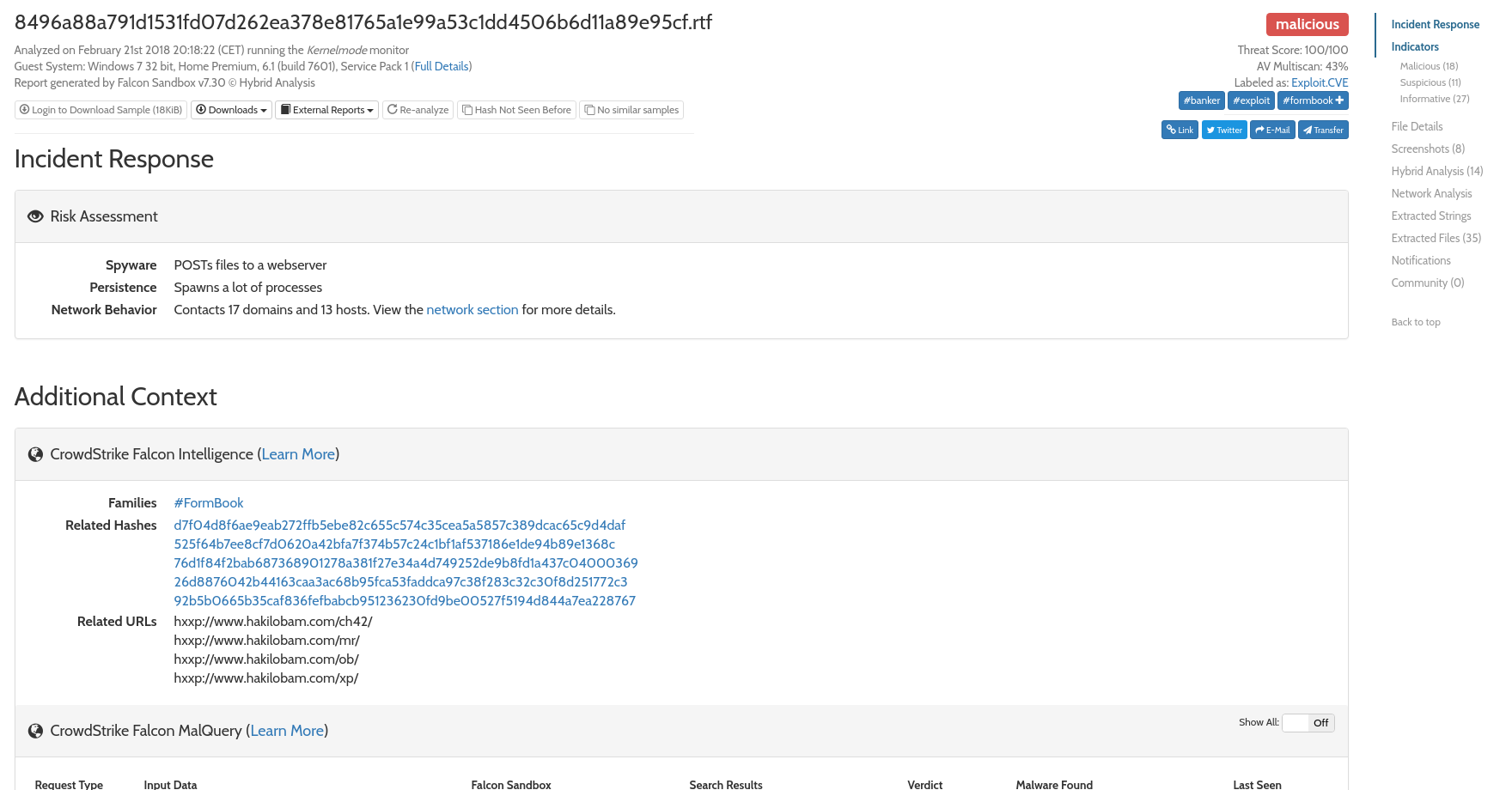
Falcon Sandbox (formerly VxStream) is a proprietary system created by Payload Security (recently purchased by CrowdStrike). It uses a kernel-mode agent to monitor malware behavior, and includes a number of anti-evasion techniques to help process even sandbox-aware malware. Falcon also uses a technology they call “Hybrid Analysis,” which combines static analysis with “fine-grained memory dump snapshots” to gain a deeper understanding of samples being analyzed, and detect malicious code even if it never actually executes.
Falcon Sandbox offers a free online version with some limited functionality at reverse.it. There are also some publicly available sample reports on the Falcon website.
InQuest Sandbox Integrations
Each InQuest sandbox integration includes optional automatic and manual submission of files, email notification of sandbox scan completion, and CEF-compatible syslog output for SIEM integrations. The results of the sandbox analysis are factored into the InQuest Threat Score, and full reports from the external sandbox system are retrieved and cached for reference by analysts from within the InQuest UI.
Open Source Software
We have also released an open source Python multi-sandbox library, now available on GitHub and PyPI. The library provides a minimal, consistent interface to all four of the sandboxes discussed in this post, and allows for file submission, checkback, and report retrieval.
Basic usage of the library is as follows:
import sys
import time
import pprint
from sandboxapi import cuckoo
# connect to the sandbox
sandbox = cuckoo.CuckooAPI('192.168.0.20')
# verify connectivity
if not sandbox.is_available():
print("sandbox is down, exiting")
sys.exit(1)
# submit a file
with open('myfile.exe', "rb") as handle:
file_id = sandbox.analyze(handle, 'myfile.exe')
print("file {f} submitted for analysis, id {i}".format(f=filename, i=file_id))
# wait for the analysis to complete
while not sandbox.check(file_id):
print("not done yet, sleeping 10 seconds...")
time.sleep(10)
# print the report
print("analysis complete. fetching report...")
pprint.pprint(sandbox.report(file_id))
Read the full library documentation on ReadTheDocs.
Further Reading
- Mac-A-Mal: Cuckoo Sandbox (legacy) extension and kernel-mode agent for advanced Mac OS X support. Released at Black Hat Asia talk in 2018. (Code)
- Al-Khaser: Public malware techniques used in the wild: Virtual Machine, Emulation, Debuggers, Sandbox detection.
- avet: AV evasion tool with some sandbox evasion features, presented at Black Hat Arsenal 2017.
References
- https://www.cuckoosandbox.org/
- https://cuckoo.sh/docs/customization/packages.html
- https://www.payload-security.com/technology/kernelmode-monitor
- https://www.payload-security.com/technology/hybrid-analysis
- https://www.payload-security.com/products/vxstream-sandbox
- https://www.vxstream-sandbox.com/faq
- https://www.joesecurity.org/joe-sandbox-technology
- https://www.joesecurity.org/joe-sandbox-cloud#key-features
- https://www.joesecurity.org/joe-sandbox-cloud#accounts
- https://joesecurity.org/blog/68779205757215410
- https://www.fireeye.com/products/malware-analysis.html
- https://www.vmray.com/features/
- https://www.vmray.com/blog/a-pafish-primer/
- https://unprotect.tdgt.org/index.php/Unprotect_Project
The Swiss Cheese Model image is a derivative of “Swiss cheese model of accident causation” by Davidmack, used under CC BY-SA 3.0.
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge for 30 days.