InQuest combines Deep File Inspection® (DFI) and RetroHunt® technology to bring the threat hunting capabilities of VirusTotal Intelligence to your own environment. VirusTotal Intelligence is a malware intelligence service that analyzes almost 2 million files each day. The service has earned its spot in the threat analyst toolbox by aggregating 70+ antivirus engines for static analysis, the VirusTotal multisandbox project for dynamic analysis, as well as 60+ domain reputation feeds. VirusTotal provides analysts with powerful tools to threat hunt against millions of files, domains, and IPs, but has the drawback of not currently offering a self-hosted option for organizations that wish to keep their data private. The InQuest platform provides high throughput data capture, Deep File Inspection, search access to both session and file data, not to mention external integrations with multiple products including VirusTotal, all within the privacy of your own network.
Analysis
The InQuest platform is available on-premises, in the cloud as a virtual deployment, and as a Software as a Service (SaaS). InQuest supports a variety of deployment/ingestion methods:
-
SPAN / TAP / VPC
-
CIFS / NFS / SMB / SSH
-
ICAP
-
API / Manual Upload
The InQuest Manager component is capable of data ingestion via ICAP, data-at-rest, API, and manual upload. The InQuest Collector component is dedicated to native packet capture from a network SPAN or network TAP.
Deep File Inspection (DFI) as an analytical technique is more complex than Deep Packet Inspection, where individual packets or connections are judged to be benign or malicious, faster than the dynamic analysis of sandboxing, which attempts to classify a sample by its effect on a system. This speed advantage allows DFI to be deployed in scenarios where large network volume demands rapid triage of traffic. A file can be evaluated as benign, suspicious, or malicious in a matter of seconds rather than minutes. Additionally, file evaluation by way of DFI can be done with a high degree of parallelism. Sparing cycles of expensive integrations through the application of a waterfall method, ordered from the most to least expedient analysis technique. By characterizing the files, we can index which features of the specification are going to be used. This can help isolate unusual functionality that attempts to activate vulnerable sections of a program’s code in the case of CVEs and 0-day vulnerabilities.
The static analysis capabilities of DFI are augmented by the dynamic analysis provided by sandbox detonation of potentially malicious files, along with secondary detection from anti-virus vendors using a number of external integrations. InQuest currently supports the following integrations:
Sandboxes
-
Cuckoo Sandbox
-
Falcon Sandbox
-
FireEye AX
-
Joe Sandbox
-
Wildfire Sandbox
-
VMRay Analyzer
-
Anti-Virus Engines
-
OPSWAT Metadefender Core
-
VirusTotal
-
For a more in-depth look at the sandbox integrations available to the InQuest platform, check out our blog post Defense in Depth: Detonation Technologies. For more information on the InQuest partnership with OPSWAT, take a look at our guest blog post on their site InQuest: The Malware Magnifying Glass.
Search and RetroHunt
The InQuest platform allows analysts to search sessions and file data captured by the InQuest components. Session data includes network session information, headers, and metadata. Session metadata and headers are searchable from the InQuest UI by way of quick and advanced searches. Advanced search allows analysts to create complex boolean searches across a variety of fields such as HTTP/SMTP headers, SRC/DST IP, VLAN ID, etc. Files discovered on your network as well as those derived from the DFI process are also searchable.
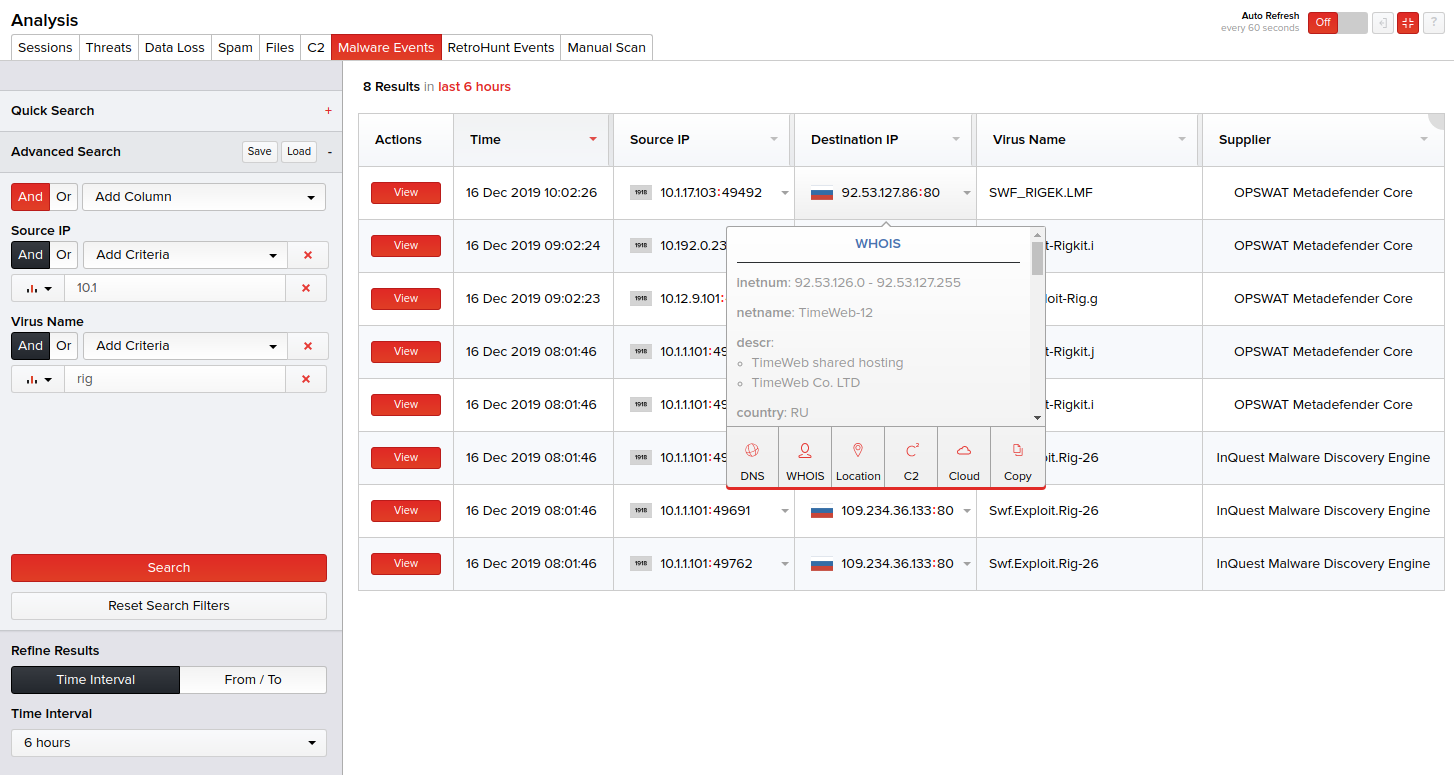
In this example, we build a simple advanced search query using the source IP, virus name, and time parameters. The results contain files that were retrieved by an IP address that contains the strings “10.1” and “rig” within the name of the malware discovered by AV suppliers. DNS lookup, WHOIS, and location information are automatically provided for each IP address within the InQuest UI, providing analysts with the data they need to threat hunt effectively.
InQuest RetroHunt ™ provides your analysts with the ability to retroactively search through mass amounts of sessions and files previously captured from your network using newly created and/or updated signatures. Weekly releases of new InQuest signatures ensure we stay on top of the latest threats and exploits, while InQuest RetroHunt ™ ensures your team is alerted if they appear in your environment.
VirusTotal Retrohunt functions a little differently than InQuest RetroHunt™. VirusTotal Retrohunt allows for user-defined YARA rules to retroactively search through up to one year worth of files submitted to VirusTotal. Each VirusTotal Retrohunt consumes one credit from your monthly Retrohunt quota. Although powerful, analysts need to choose wisely which YARA rules to use their Retrohunt credits on.
One common use case shared by both InQuest RetroHunt™ and VirusTotal Retrohunt is its use of signature development. InQuest RetroHunt ™ performs a retroactive search using every signature within the InQuest Labs signature set (sigpack), as well as any user-defined signatures created by your team. Candidate user-defined YARA signatures can be created and tested against data captured from your own network. InQuest RetroHunt ™ runs automatically whenever a new InQuest Labs sigpack is released and can also be configured to run on a schedule by your team or run manually at any time for any signature to help tune signature accuracy and/or performance. By default, RetroHunt ™ will scan 2 weeks of historical data captured from your network and that timeframe can be modified or even disabled by a system administrator. For further details about InQuest RetroHunt ™, see the InQuest RetroHunt Whitepaper.
References
Defense in Depth: Detonation Technologies | InQuest