InQuest has just released a new analysis suite for the researcher and hobbyist. Welcome to InQuest Labs!
Our CTO, Pedram Amini, presented Worm Charming: Harvesting Malware Lures for Fun and Profit at Blackhat USA 2019. During this talk, Pedram detailed the harvesting mechanism that drives the DFI portion of InQuest Labs. Capable of ingesting malware at scale, samples are fed through a lightweight and less featured version of Deep File Inspection to extract embedded logic, semantic content, metadata, and IOCs such as URLs, domains, IPs, e-mails, and file names.
Currently, Microsoft and Open Office documents, spreadsheets, and presentations are available for search and download. In the future, we will expand the public data set to include Adobe PDF documents, Java / Flash applets, and scriptlets, such as Powershell. You can search extracted layers and IOCs by keyword. Download samples. Pivot between samples by heuristic detections and IOCs. And more… either interactively through the web interface, or programmatically through our open API. Result sets from the API are limited to 1337 results at a time. Contact us directly if you wish to gain unfettered access.
Some of the capabilities found within InQuest Labs are:
Deep File Inspection (DFI-LITE)
Upload common malware lures for Deep File Inspection and heuristic analysis. Explore the embedded logic, semantic context, metadata, and millions of artifacts harvested from this growing corpus of files. You can also download samples for research purposes.
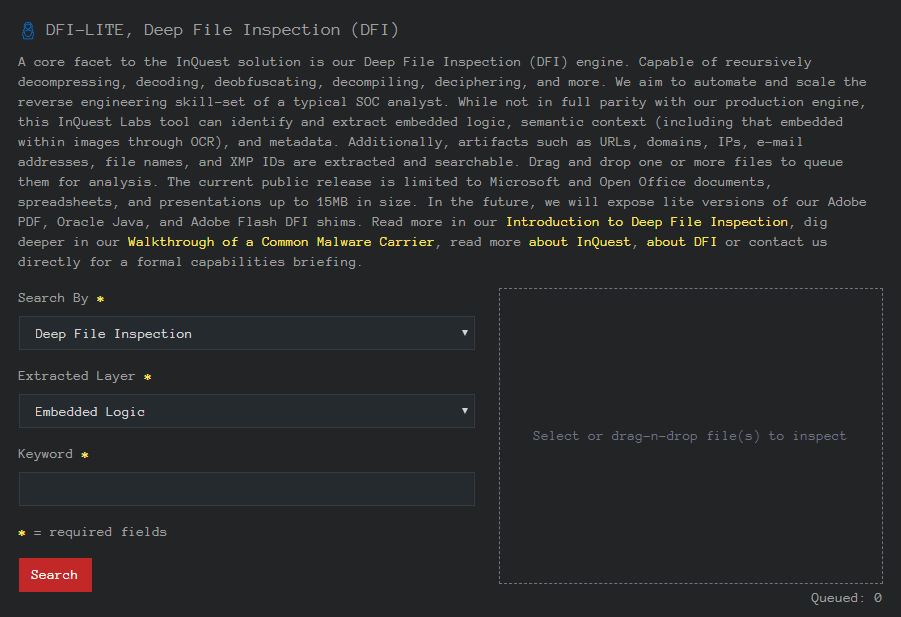
Indicators of Compromise Database (IOC-DB)
The newest addition to InQuest Labs, discover IOCs and artifacts published by individuals and teams through mediums such as Twitter, Github, and blogs. Data types include URLs, domains, IP addresses, file hashes, and YARA rules.
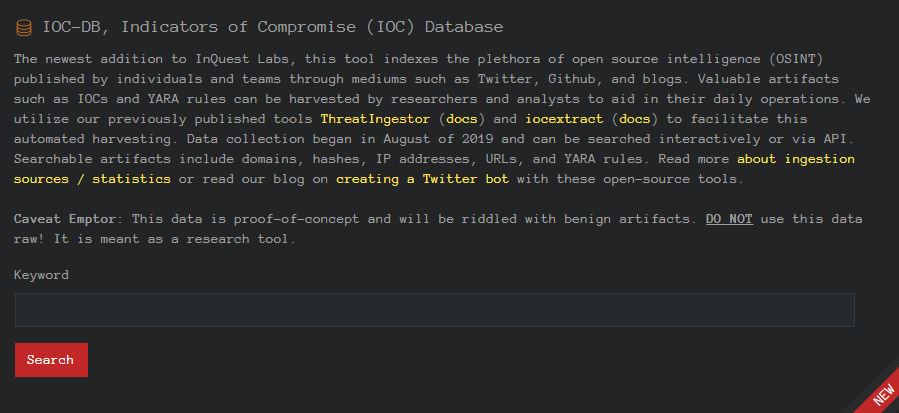
Aggregate Reputation Database (REP-DB)
Search a catalog of IP addresses, ASNs, URLs, and domains aggregated from over two dozen public reputation dissemination feeds. Pivot from these indicators through other tools like Shodan, Greynoise, DomainTools, VirusTotal, and PacketTotal.
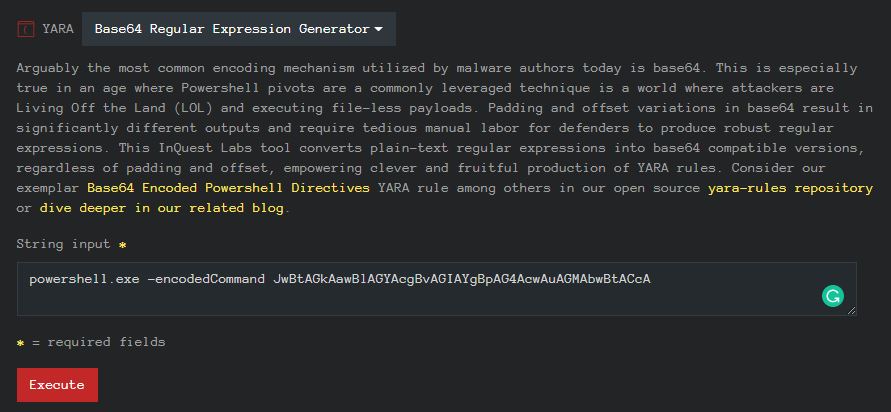
YARA Tools:
Base64 Regular Expression Generator
Save time and avoid tedious manual labor by automatically converting plain-text regular expressions into their base64 compatible form.
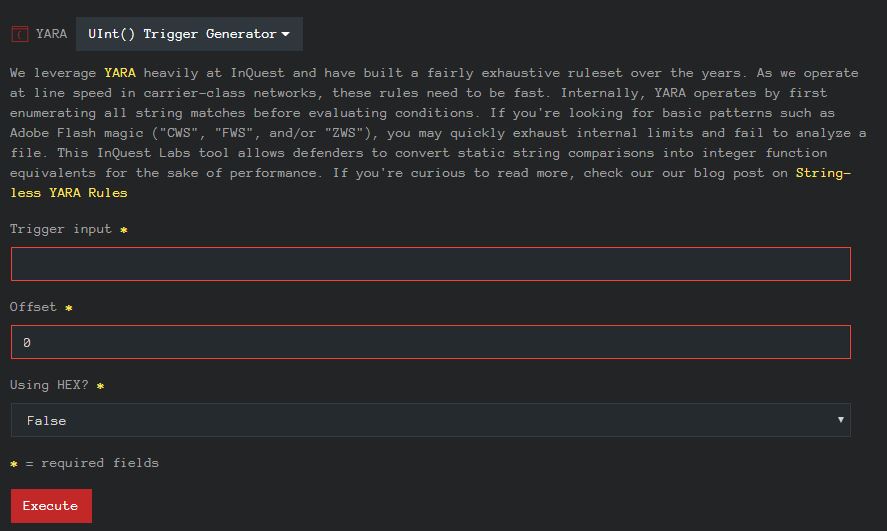
Mixed Hex Case Generator
Translate hex encoded strings into a regular expression form that is agnostic to MixED CaSE CharACtErS.
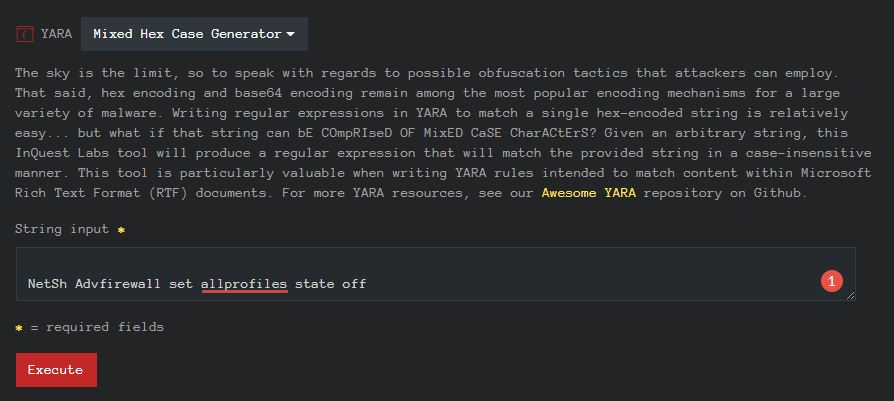
UInt() Trigger Generator
Improve the performance of your YARA rules by converting string comparisons into unsigned integer pointer dereferences.
Definitely check out InQuest Labs and let us know what you think! And note all samples are freely downloadable.
REP-DB & IOC-DB
This announcement blog is part 1 of a 3 part series showcasing tools within InQuest Labs. Part 1 contains the overview and examples of REP-DB & IOC-DB. Expect additional writing in the foreseeable future discussing the YARA tools and DFI-LITE.
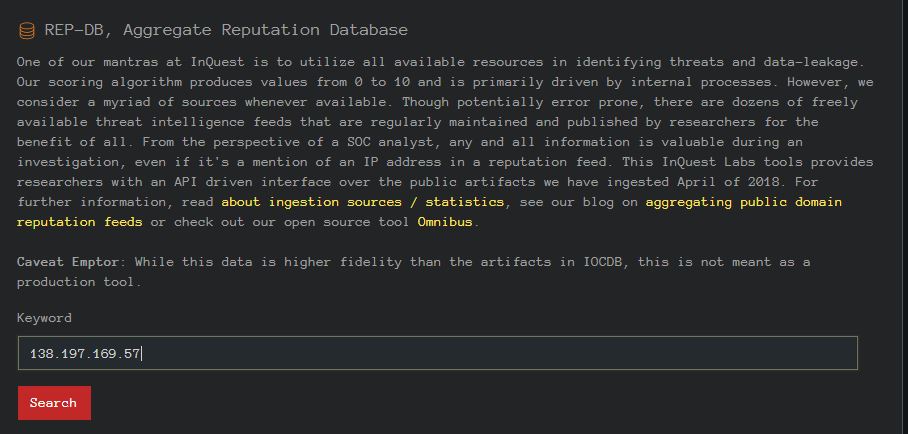
One of our mantras at InQuest is to utilize all available resources in identifying threats and data-leakage. Our scoring algorithm produces values from 0 to 10 and is primarily driven by internal processes. However, we consider a myriad of sources whenever available. Though potentially error prone, there are dozens of freely available threat intelligence feeds that are regularly maintained and published by researchers for the benefit of all. From the perspective of a SOC analyst, any and all information is valuable during an investigation, even if it’s a mention of an IP address in a reputation feed. This InQuest Labs tools provides researchers with an API driven interface over the public artifacts we have ingested April of 2018. For further information, read about ingestion sources / statistics, see our blog on aggregating public domain reputation feeds or check out our open source tool Omnibus.
A variety of both open source and commercial IP/ASN and URL/domain reputation feeds exist which can assist defenders in standing setting automated blocks, and help analysts looking to add context to an investigation. In May of 2018 we published a blog detailing a number of open source feeds, the kinds of data they contain, and their update frequencies. We outlined a variety of open source tools, including some published by InQuest (ThreatIngestor, IOCExtract), for aggregating such feeds. While this data is publicly available for anyone to aggregate, we created this tool for researchers who wish to skip that step and simply explore the data interactively or query against our open API. Result sets from the API are limited to 1337 results at a time from the past 6 months. Contact us directly if you wish to gain unfettered access.
Below you’ll find the list of sources that feed into this database. In addition to the crawled artifacts, we derive secondary information… ASNs from IP addresses and domains from URLs for example. Following the list of sources you’ll find the aggregate statistics for all harvested artifacts across all sources since collection began in April of 2018.
abuse.ch
alienvalut
bambenek
binarydefense
blocklist
botscout
bruteforeceblocker
cleantalk
csirtg
cybercrime-tracker
cybersweat
dataplane
feodotracker
greensnow isc.sans
myip
openphish
packetmail
data.phishtank.com
spamhaus
sslbl
stopforumspam
talos
threatweb
urlhaus
viriback
vxvault
zeus
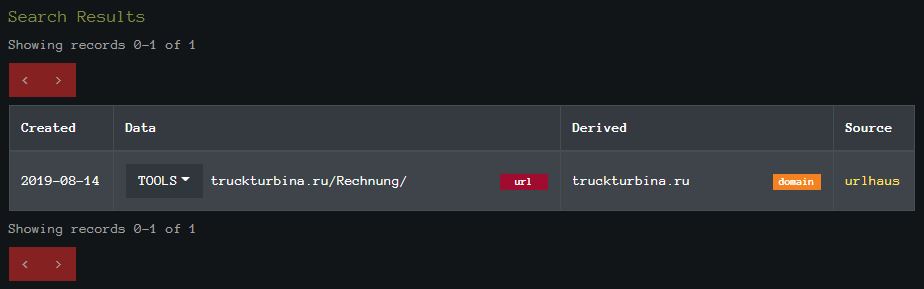
Example in REP-DB “truckturbina[.]ru”
Automate your analysis from REP-DB with different API Requests including:
- cURL
- Powershell
- NODE.js
- Python
- GO
import requests url = "https://labs.inquest.net/api/repdb/search?keyword=truckturbina.ru" response = requests.request("GET", url) print(response.text) You can also pivot to DomainTools, PacketTotal, and VirusTotal.
The newest addition to InQuest Labs, this tool indexes the plethora of open source intelligence (OSINT) published by individuals and teams through mediums such as Twitter, Github, and blogs. Valuable artifacts such as IOCs and YARA rules can be harvested by researchers and analysts to aid in their daily operations. We utilize our previously published tools ThreatIngestor (docs) and iocextract (docs) to facilitate this automated harvesting. Data collection began in August of 2019 and can be searched interactively or via API. Searchable artifacts include domains, hashes, IP addresses, URLs, and YARA rules. Read more about ingestion sources / statistics or read our blog on creating a Twitter bot with these open-source tools.
The IOC database is comprised of artifacts harvested from both Twitter and blogs. This data isn’t as high-fidelity as the reputation database, but is interesting and valuable in its own right. Artifacts include URLs, domains, IP addresses, file hashes, and YARA signatures. The list of Twitter handles that we harvest these artifacts from can be found in our IOC-feed Twitter list. If you have recommendations for users to add, reach out to us. Additionally, we harvest artifacts from the following RSS feeds. Again, if you’d like to recommend a new source, do not hesitate to reach out. The data is available for search interactively as well as through our open API. Result sets from the API are limited to 1337 results at a time from the past 6 months. Contact us directly if you wish to gain unfettered access. Following the list of blog sources, you’ll find aggregate artifact statistics across all sources.
anomali
baesystemsai
carbonblack
citizenlab
clearskysec
fireeye
fox-it
inquest malwarebytes
malwaremustdie
riskiq
securelist
shadowserver
talos
thembits threatconnect
trendmicro
twitter
unit42
us-cert.gov/ncas/alerts.xml
volexity
vxsecurity
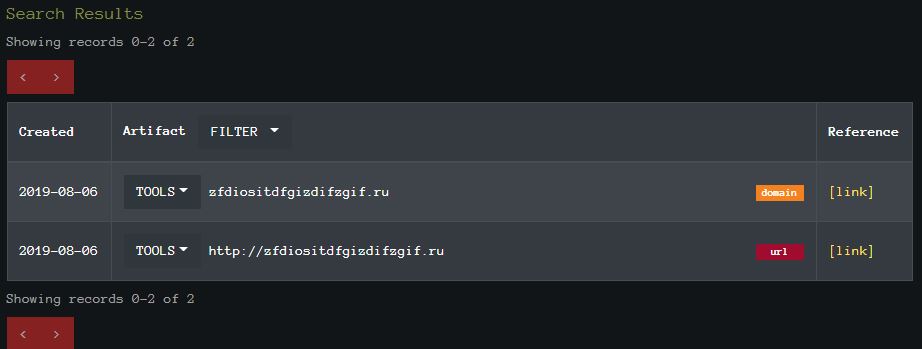
You can also autmoate your research using the IOC-DB. For example, this GandCrab associated domain (zfdiositdfgizdifzgif[.]ru) retrieves some artifacts from the db. As eluded to earlier, this API example is in PowerShell. $uri = 'https://labs.inquest.net/api/iocdb/search?keyword=zfdiositdfgizdifzgif.ru' $result = Invoke-req -Uri $uri Write-Output $result.content
The IOC-DB also links the reference within the search results!
We hope you enjoy InQuest Labs. Please drop us a Tweet to let us know what you think!

