The third year of the #100DaysOfYARA challenge has wrapped! Check out our midway point write-up from February 19th,
100 Days of YARA 2024: Halfway Point, where we covered an overview of the challenge and highlighted various contributions from the community.
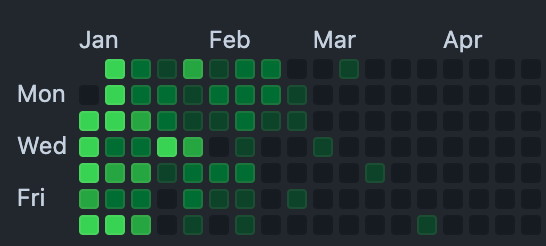
100 days of community contribution is certainly a challenge. This is visually evident from the contribution graph on the official Github repository here:
In the second half of the challenge, the conversation on Twitter is almost completely dominated by the following three participants:
- Denice Ꭰenicᴇ (@de3ev) / X
- Peter Stewart twitter.com/petermstewart
- Yashraj Solanki twitter.com/RustyNoob619
Major kudos to them on their stamina 👏. For a full (or at least an attempt at it) list of contributors, see our Twitter list 100DaysOfYARA Participants.
Second Half Contributions
The XZ backdoor (CVE-2024-3094) has dominated the news cycle as of late. If you’re looking to read about it my favorite resources are this timeline from this Evan Boehs and this ongoing Gist from smx-smx. Some relevant YARA rules that surfaced around this matter:
There was a nice write-up on Byakugan malware identified by @FortiGuardLabs, adding on top of this work Yashraj Solanki created the following detection rules: @RustyNoob619 April 5th.
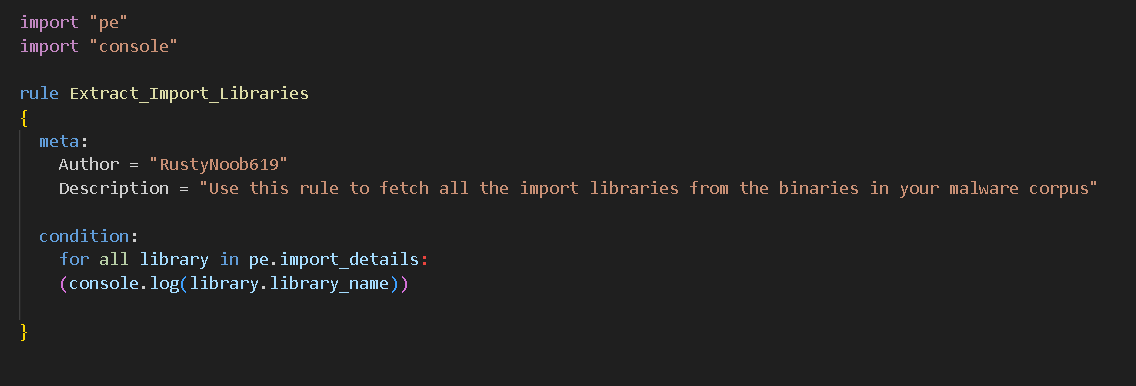
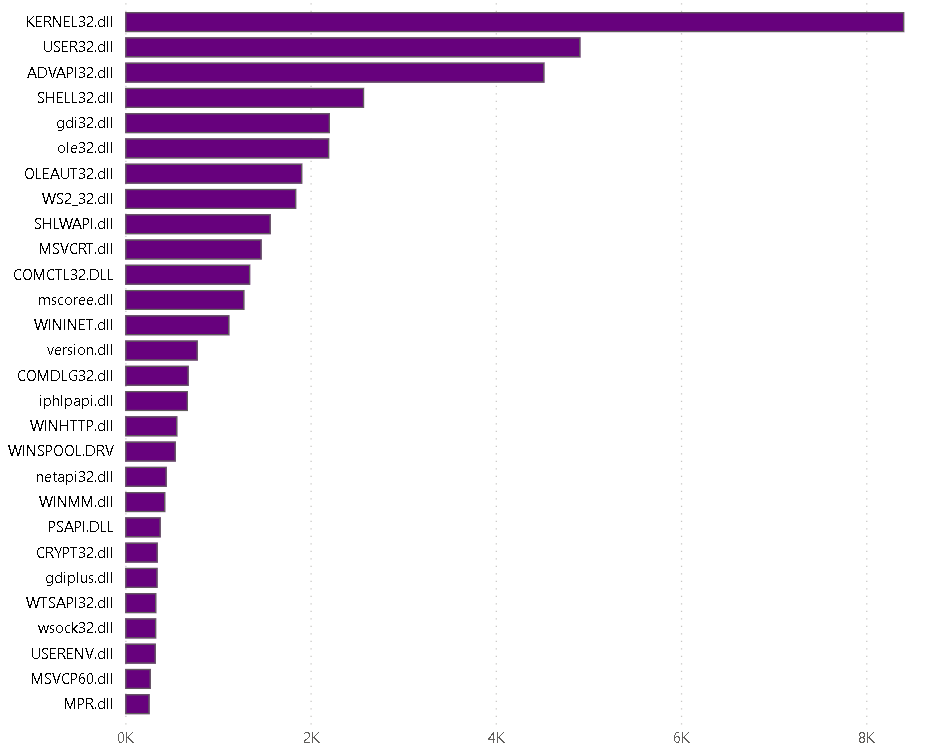
Another interesting tactic that Yashraj employed is to leverage the “console” import to produce data This is an interesting usage of the “console” import to produce data about a corpus of files:
Thomas Roccia dropped out of the challenge but he made some major contributions in the first half by way of YaraToolkit and DocYara (LLM RAG), which you can read more about in his blog.
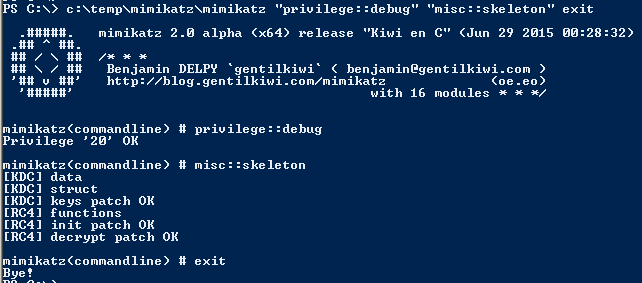
Here’s a clever little rule from Peter Steward for detecting the ASCII art embedded in Mimikatz payloads:
Finally, JPCERT/CC had a great write-up on the malicious PyPI packages used by the Lazarus group, Yashraj Solanki created this detection rule for coverage.
Other YARA News
While not part of the #100DaysOfYARA challenge, we caught an interesting Tweet this week from VirusTotal’s Victor Alvarez regarding YARA-X. For those that are unfamiliar, YARA-X is a complete re-write of YARA in Rust. Still in development, the project is rapidly evolving and slated to replace YARA in the future. What’s interesting about the bifurcation of the pattern matching swiss army knife is that the two implementations can be used to bugcheck one another. Check out this Github issue from Monday that details a false negative in a fairly trivial hex pattern definition for example:
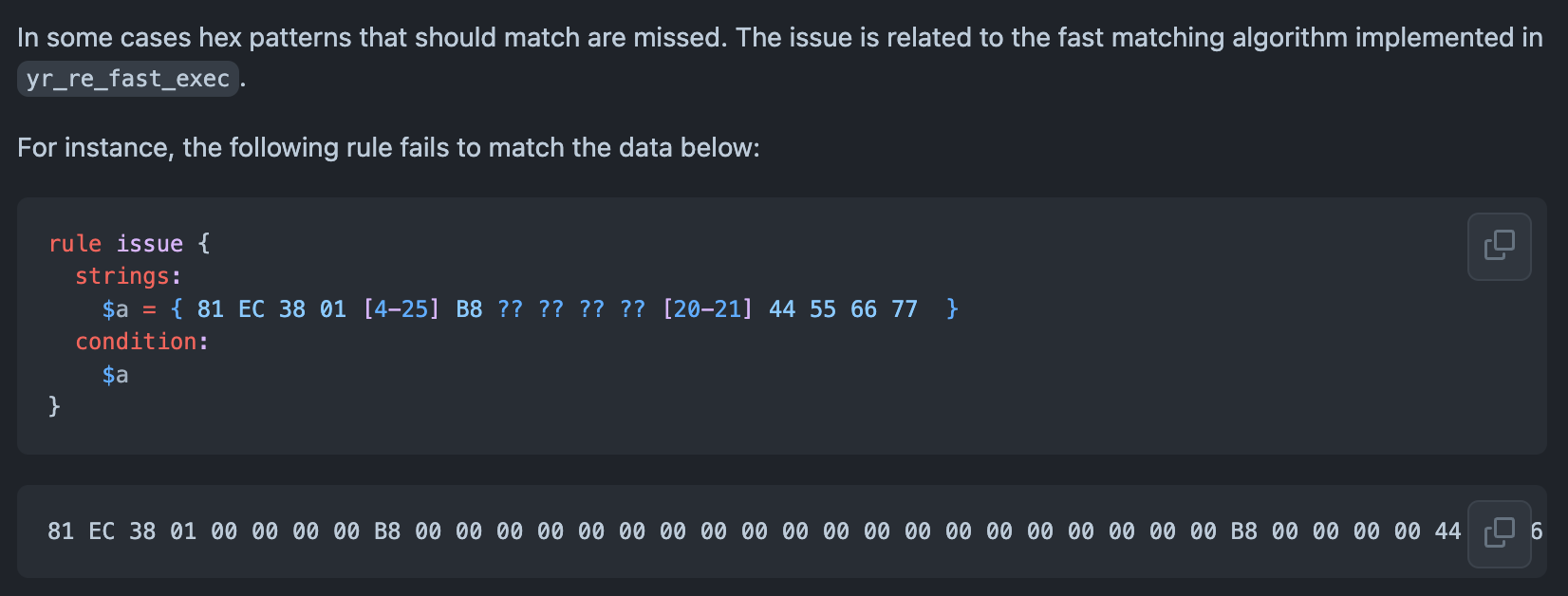
Pretty wild! The reimplementation is Rust should be bring performance enhancements and… it’s what your government wants.
On a final note, the Cerbero Suite was just today updated and includes a new YARA Package that bundles features for downloading, scanning with, creating, editing, and testing YARA rules.
Further Resources
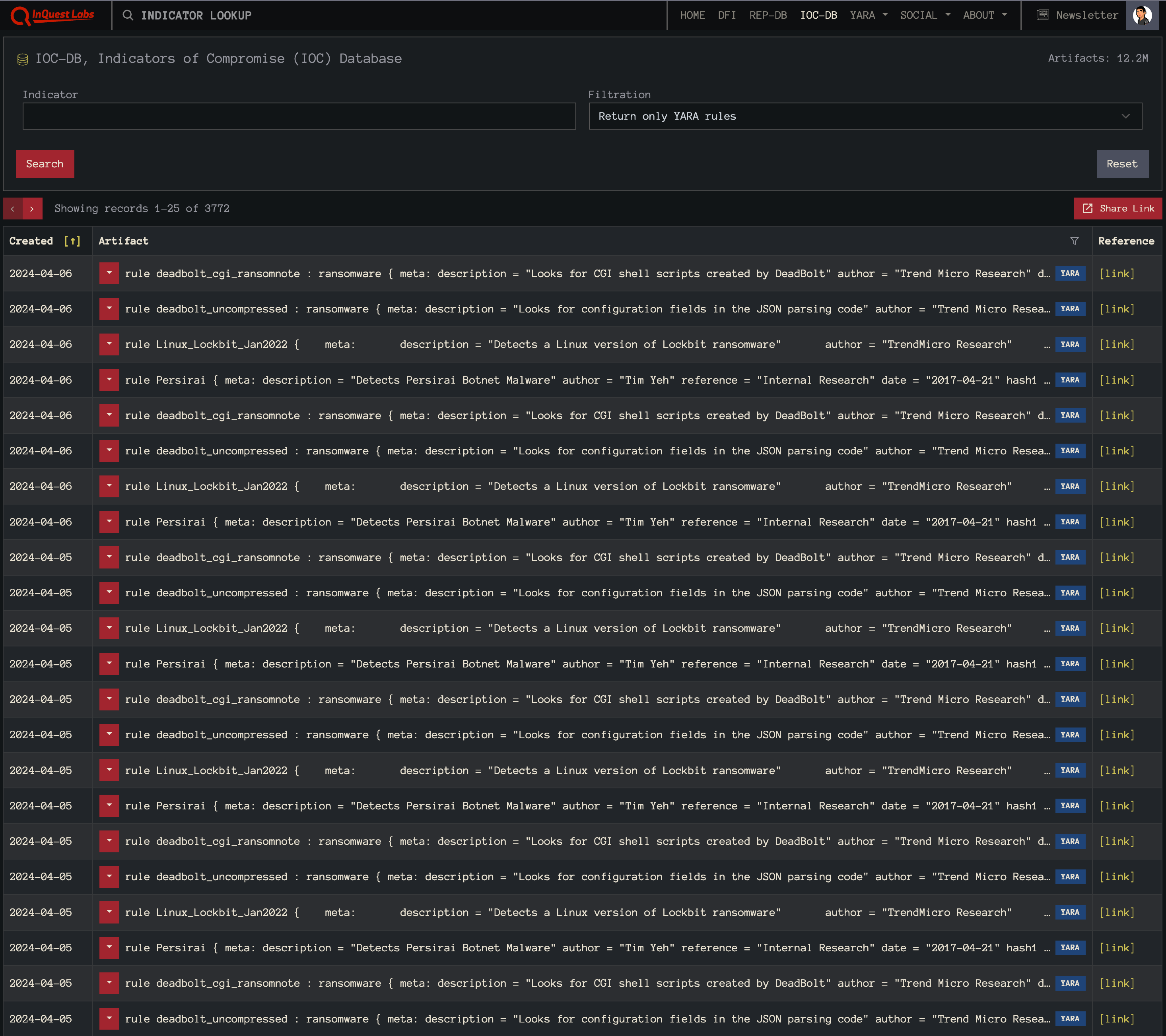
If you’re looking for YARA resources and/or rules, we highly recommend checking out the Awesome YARA project on Github that aggregates all of the things YARA… including rules, tools, services, people, and more. Furthermore, check out InQuest Labs, specifically the IOCDB panel which allows one to search for YARA rules from a plethora of sources (note a free login is required to return only YARA rules in this view):
If you’re a security practitioner looking to leverage the power of YARA in your environment, get in touch. The entirety of the InQuest product line (FileTAC, MailTAC, and NetTAC) supports YARA pattern matching across session, header, and file content. Critically, InQuest Deep File Inspection® (DFI) exposes and normalizes embedded file content allowing detection engineers to apply YARA to otherwise hidden layers of data. In addition to real-time YARA alerting, InQuest RetroHunting® empowers analysts to leverage the power of hindsight by applying YARA to historical data. This pairing facilitates a proactive approach toward adopting a Zero Trust security framework.

