We’re halfway through (yes it’s already the 50th day of 2024) the third year of the “100 Days of YARA” challenge, represented on Twitter via the hashtag #100DaysOfYARA. If you’re not familiar with the effort, it was inspired by #100DaysOfCode and encourages participants to engage with YARA for the first 100 days of the year. The challenge involves contributing to the community in any way, shape, or form. Some examples:
- Writing and sharing one new YARA rule each day for 100 days.
- Working on YARA source code or other tooling.
- Generally helping to educate folks about YARA.
- Sharing detection engineering tips and tricks, like this excellent thread from Karsten Hahn.
If you’re new to this all and looking to get started, consider the following springboards:
- Find some relevant folks to follow and engage with on Twitter via our #100DaysOfYARA Participants list.
- Join the conversation via the formal Discord channel.
- Watch the official Github repository where rule submissions are collated.
Large Contributions
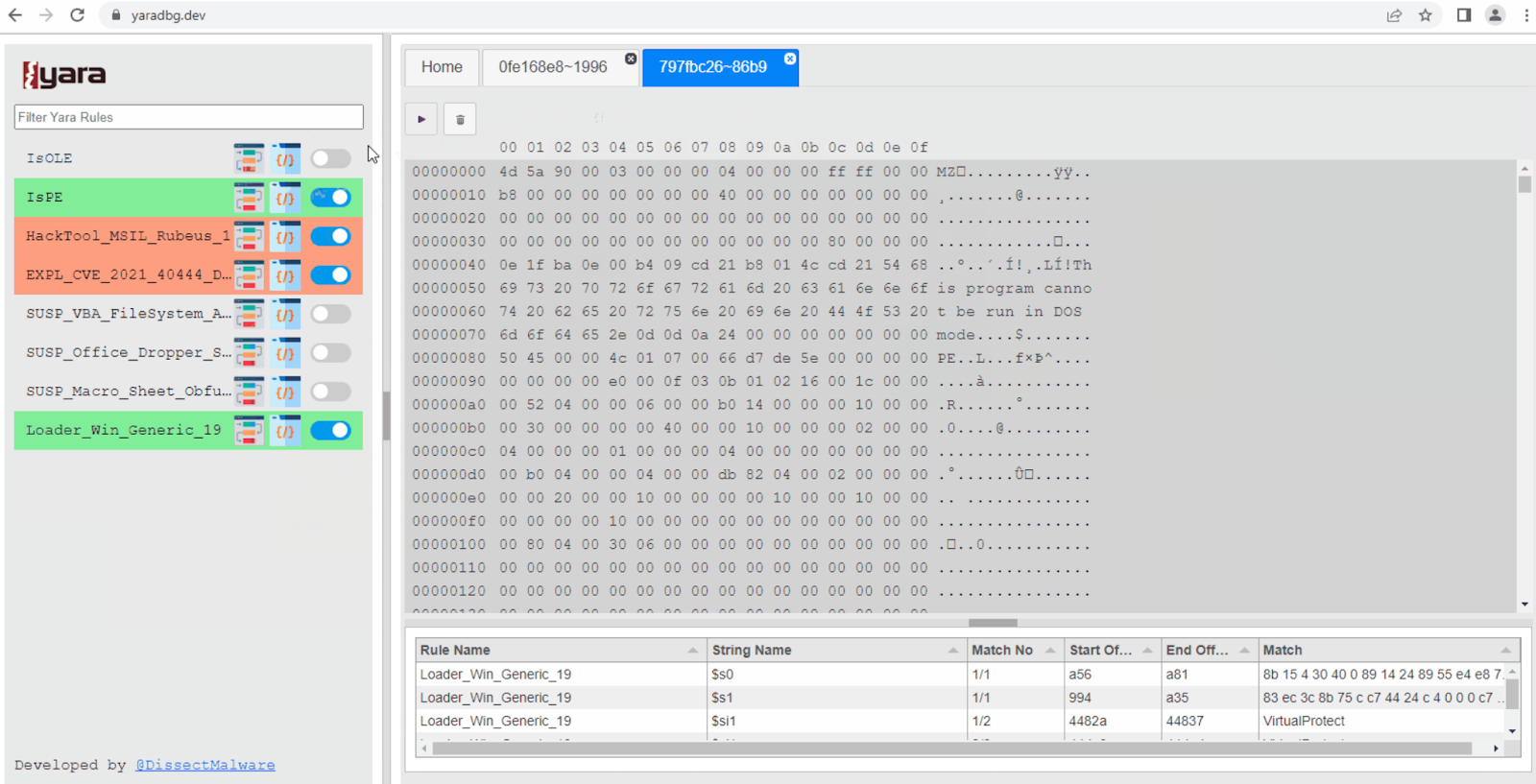
One of the larger single contributions we’ve seen to date was from friend and colleague @DissectMalware who released a tool that he’s been privately working on for some time YaraDbg. If you’ve ever worked with complex YARA rules before you’ll have felt some debugging pains that have remained unsolved for years. YaraDbg helps you track down why your rule is not firing as expected. In addition to hosting the tool as a service, he’s open-sourced the work across two projects, one for the front end and the other for the back end. To install in Docker, simply:
$ docker pull dissectmalware/yaradbg:latest
$ docker run -p 7071:7071 -p 8081:80 -d dissectmalware/yaradbg:latest
And then surf over to http://localhost:8081 to get started, screenshot:
Another large contribution to highlight is from Christian Blichmann (@AdmVonSchneider), who maintains the BinDiff module at Google which they acquired from Zynamics. He open-sourced VxSig, a tool for automatically generating YARA and ClamAV signatures from sets of similar binaries. This is the technology that fueled the former Zynamics VXClass offering, which essentially allowed for binary phylogenetics.
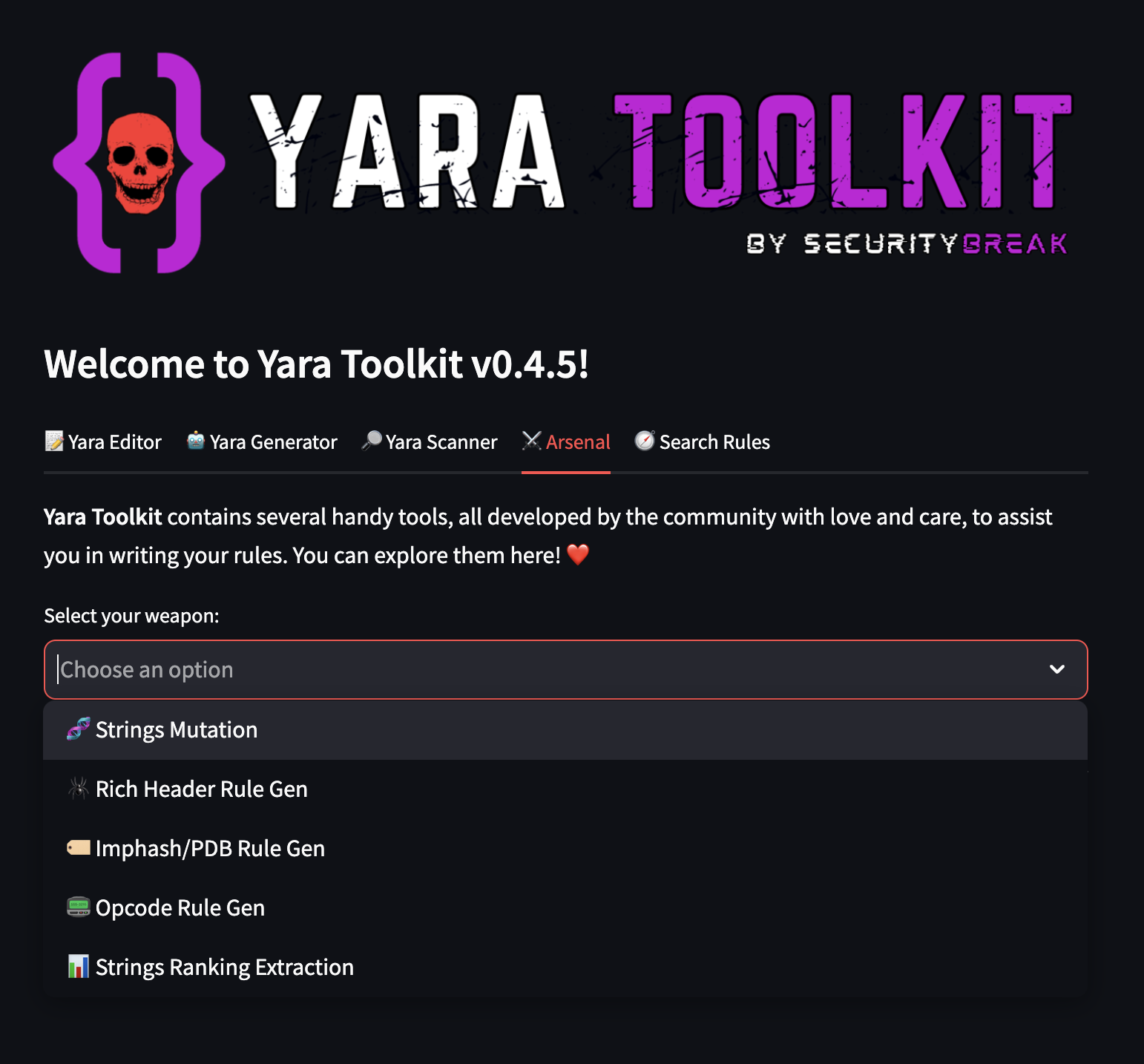
A third large contribution to call attention to comes from Thomas Roccia (@fr0gger), who released the YARA toolkit which includes several web-based tools, including an editor/generator/scanner, a public rule search engine, and a small arsenal of task-specific tools to help detection engineers.
Myriad of Highlights
There’s so much great content this year to highlight and here are just some of the ones that stood out to us…
- Leveraging conditional counts to tease out case abuse.
- Apparently, you can edit and test YARA rules in CyberChef! Here’s an example.
- Detect LNK files that may create scheduled tasks.
- Leverage YARA and some command line kung-fu to enumerate unsigned binaries in Windows 11.
- Explore the VirusTotal NetIOC custom YARA extension. Here’s the relevant blog.
- Take a look at what it takes to make contributions to the official YARA repo.
- @JusticeRage created YARA validator for checking which versions of YARA your rule is compatible with.
- @petermstewart highlights how to use regex to detect Bitcoin and Ethereum wallet addresses
- …and so many more.
Further Resources
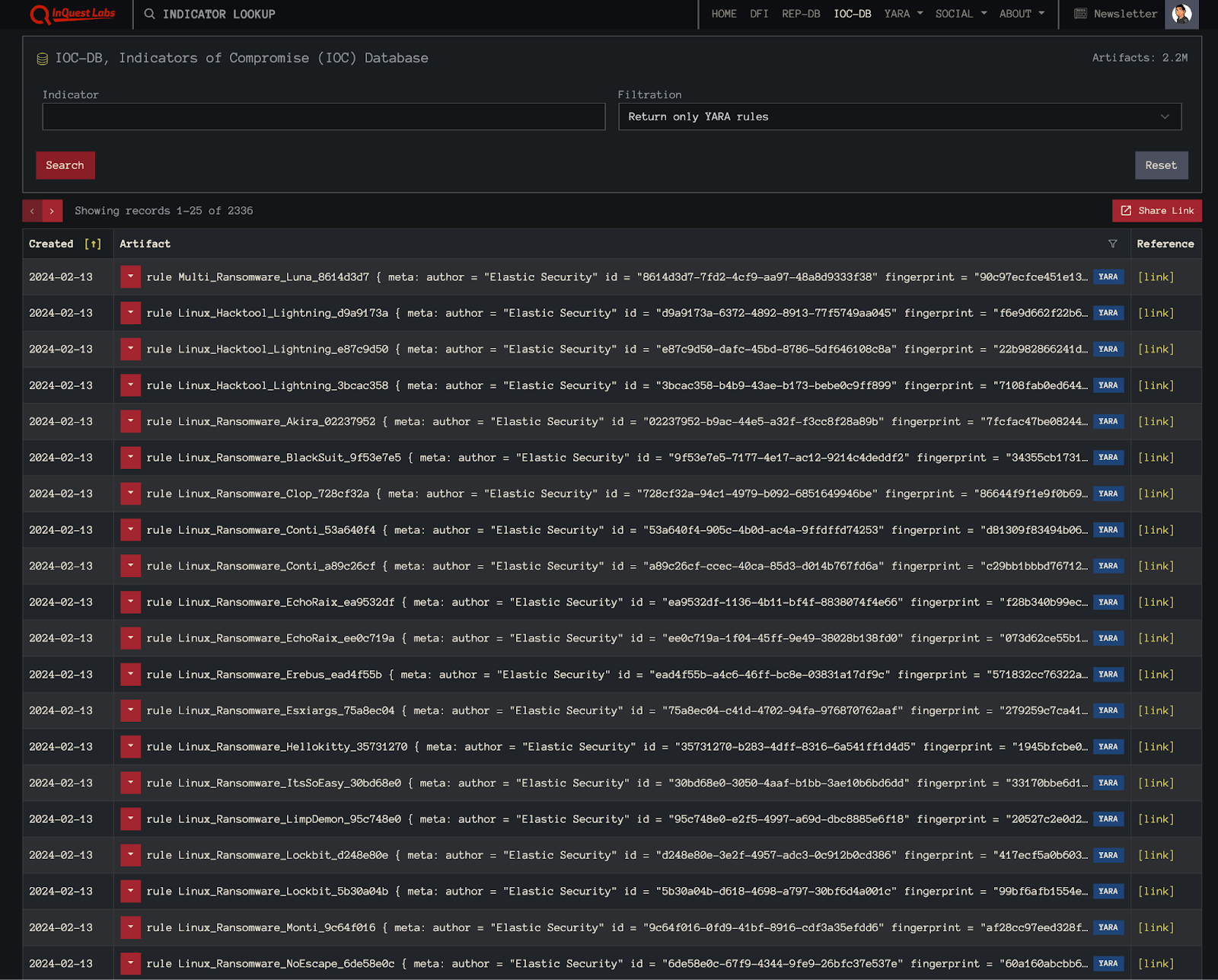
If you’re looking for YARA resources and/or rules, we highly recommend checking out the Awesome YARA project on Github that aggregates all of the things YARA… including rules, tools, services, people, and more. Furthermore, check out InQuest Labs, specifically the IOCDB panel which allows one to search for YARA rules from a plethora of sources (note a free login is required to return only YARA rules in this view):
We’d like to express our sincere gratitude to everyone involved in the 100 Days of YARA initiative. Your dedication and hard work are truly commendable. As the challenge progresses, we’ll be keenly observing and look forward to sharing a comprehensive update upon its conclusion. If you’re a security practitioner looking to leverage the power of YARA in your environment, get in touch. The entirety of the InQuest product line (FileTAC, MailTAC, and NetTAC) supports YARA pattern matching across session, header, and file content. Critically, InQuest Deep File Inspection® (DFI) exposes and normalizes embedded file content allowing detection engineers to apply YARA to otherwise hidden layers of data. In addition to real-time YARA alerting, InQuest RetroHunting® empowers analysts to leverage the power of hindsight by applying YARA to historical data. This pairing facilitates a proactive approach toward adopting a Zero Trust security framework.

