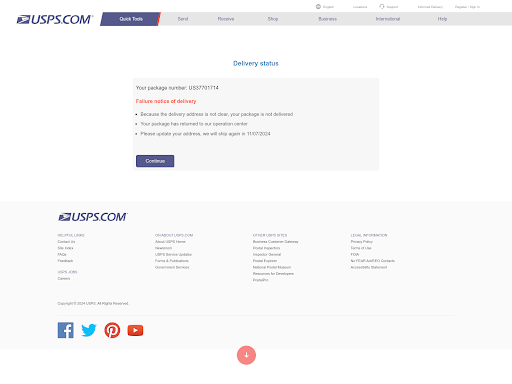
Welcome to the
InQuest Insider!
Short And To The Point
Look, we know how valuable your time is. That’s why we’ve designed our newsletter to provide you with the most impactful information possible to keep you informed with minimal time investment.
Each issue crams a month’s worth of carefully curated content into a concise, powerful resource that will keep you up-to-date on the latest trends, threats, and cybersecurity advancements.
Explore our library of newsletters below.
By signing up for The InQuest Insider, you’ll join a community of industry professionals, thought leaders, and cybersecurity experts searching for and sharing their most valuable insights, perspectives, and resources.