Originally posted on Bleeping Computer here
Fact, most successful cyber attacks begin with a simple email. Generically, the industry has conformed to the term Business Email Compromise (BEC) to capture this swath of threats, including impersonation, phishing, spoofing, and in more advanced cases, by way of a malicious attachment, including Adobe and Microsoft Office documents.
Email is typically the first stage of a multi-pronged malicious campaign, with each stage of the attack containing a variety of indicators (IOCs), or tells, for detection. Additionally, email-borne attachments may contain an exploit for known (n-day) or unknown (0-day) vulnerabilities.
Additionally, the possibilities for detection evasion are endless. Consider, for example, encrypted attachments where the password is embedded within the email in an obfuscated manner.
Threat actors have an asymmetric advantage. They only have to get it right once, whereas defenders must be right 100% of the time. To make matters worse, while the volume of threats increases year-over-year, so does the talent gap.
There’s a scramble among investors and inventors to close this gap with Artificial Intelligence (AI) and Machine Learning (ML), but we’re not quite there yet. In reality, optimal performance is achieved through a combination of man and machine.
Introducing InQuest Labs
To help address this gap, we launched InQuest Labs, a free research portal designed to crowdsource the discovery of emerging threats. Four main components drive this platform:
- Deep File Inspection (DFI), a lightweight version of our static analysis engine. Capable of extracting embedded code, metadata, context, IOCs, and more. Microsoft and Open Office documents are fed into the platform daily from a variety of sources.
- Reputation Database (REP-DB), a single pane of glass for determining if a given indicator was reported to one of many public reputation feeds.
- IOC Database (IOC-DB), aggregation of indicators from Twitter/Github/blogs/etc. to determine if an indicator is being discussed within the community.
- YARA tools to assist in the creation of detection logic.
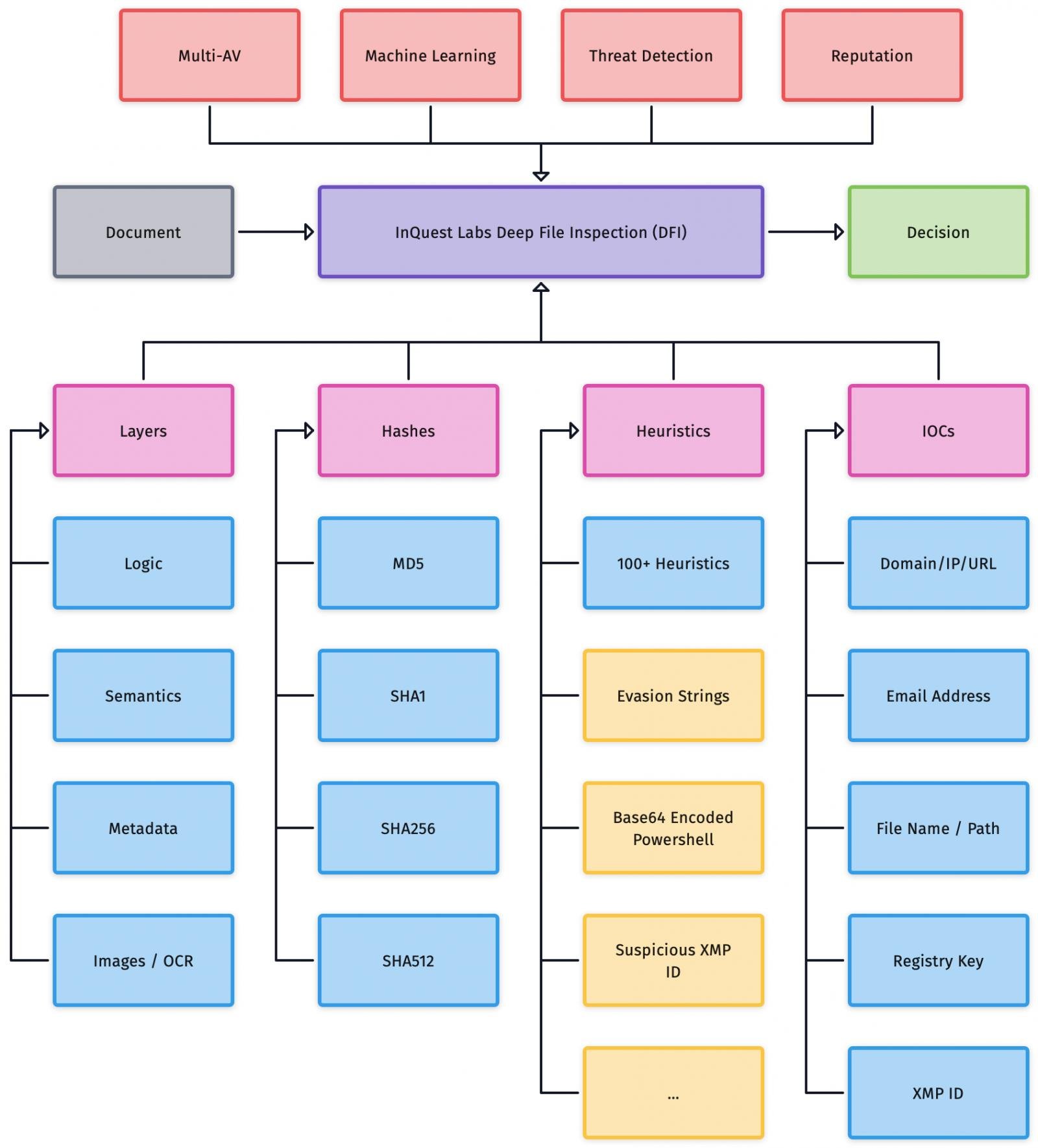
Samples under DFI are labeled as unknown, suspicious, or malicious through a combination of heuristics, multi-AV, reputation, and machine learning models. For a visual overview, see Figure 1 below.
Researchers can register/login via various OAUTH providers to filter/sort results and discover low-detection threats. From there, indicators can be compared against REP-DB and IOC-DB to determine if the campaign has already been “reported” or is currently being “discussed.” If not, there is potential that this is a novel threat worthy of further human dissection.
We dogfood this platform regularly to make the discoveries you can read about on our blog or via Twitter (@InQuest).
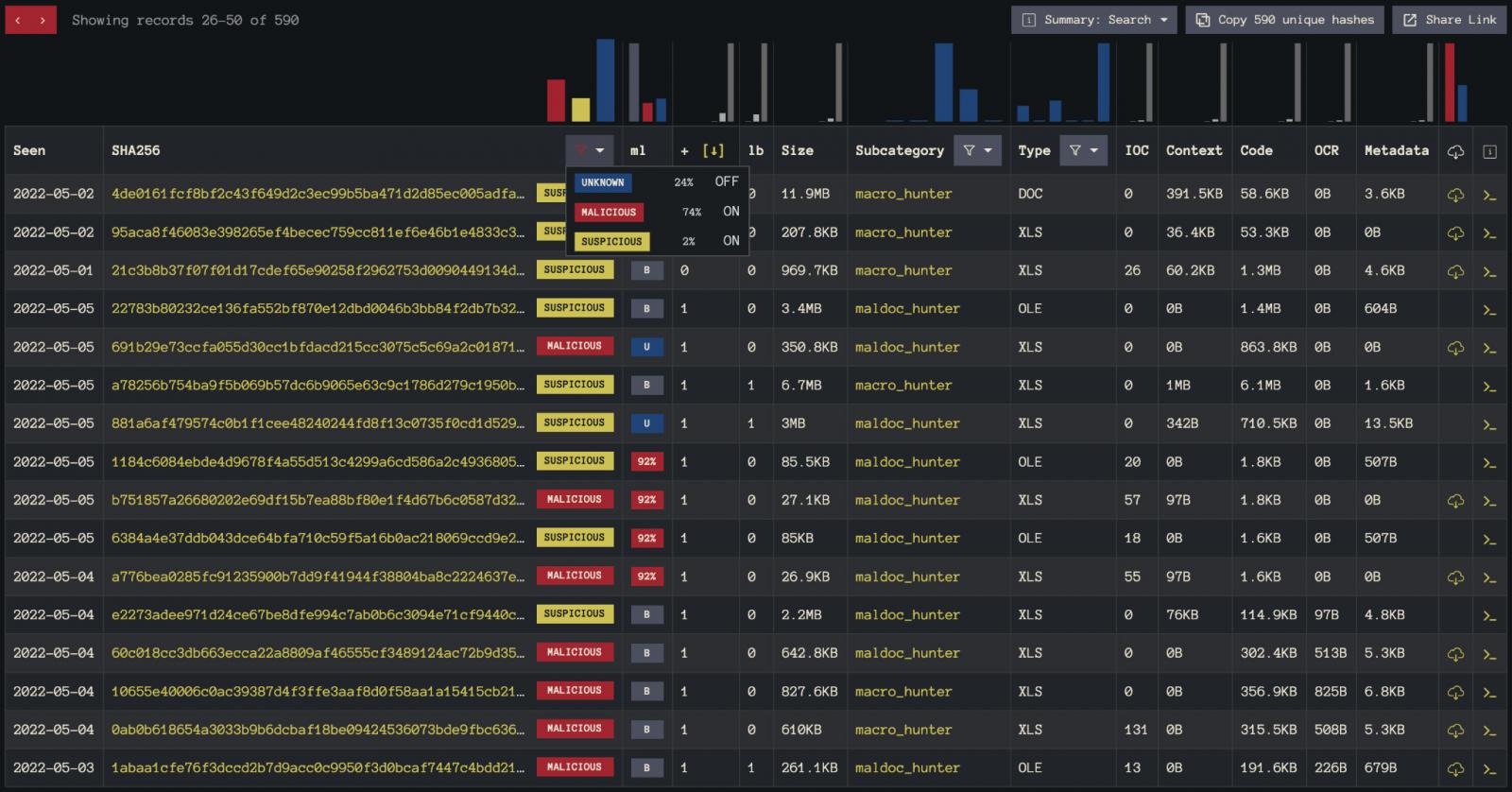
As a concrete example that readers can follow, consider the search results depicted in figure-2.
Here we filter results to those that contain both an InQuest ML classification and multi-AV results. We then filter out “unknown” and sort by AV detection count (+), a raw count of AV vendors that labeled the sample as malicious. The samples that appear on this page are great candidates for further dissection.
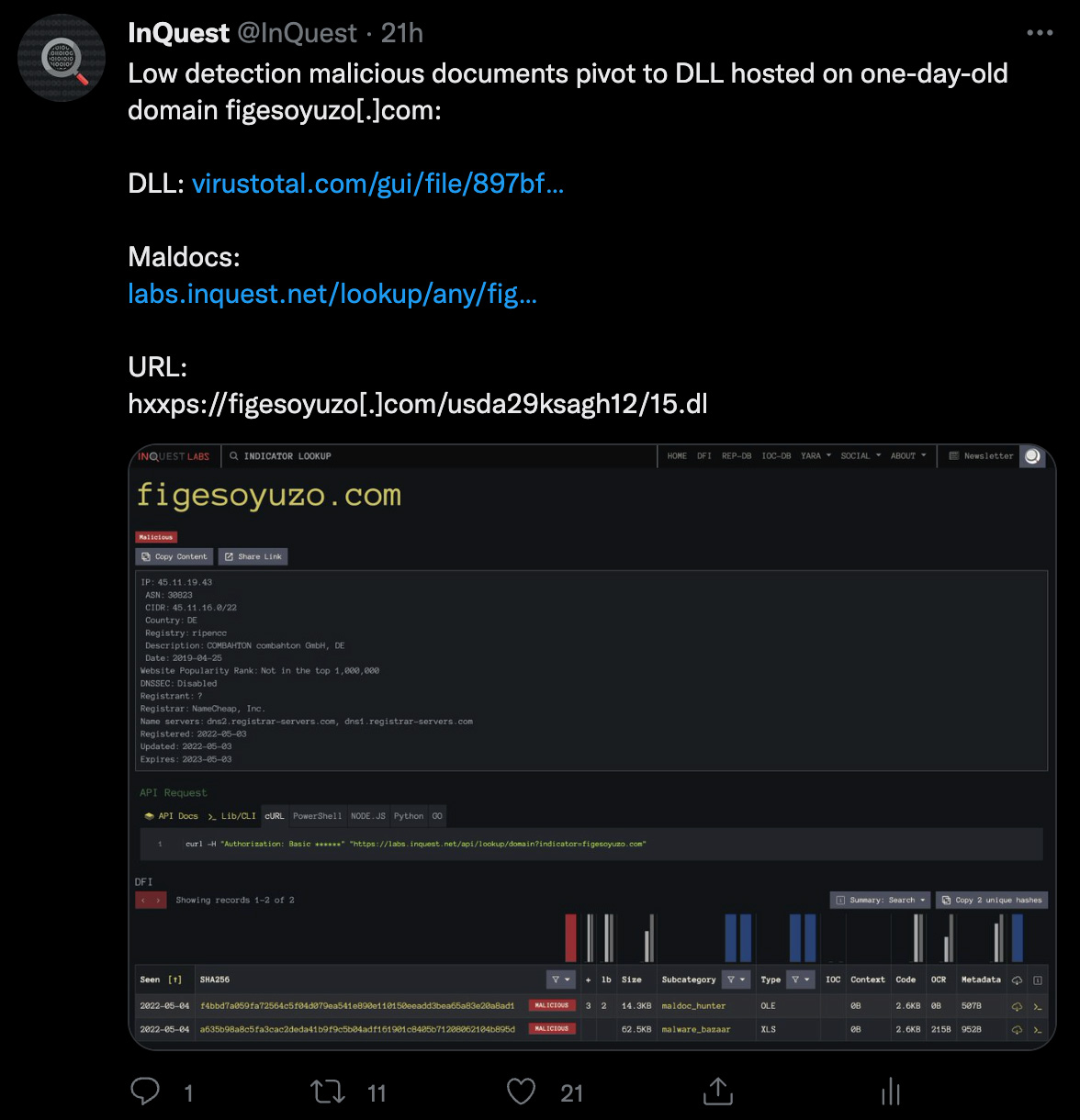
This exact process was used to discover the “BumbleBee” sample seen Tweeted in Figure 3 below.
Drill into the details pane for any sample from the list/search view, and you’ll see the various DFI layers. In addition, there are dropdowns on the logic layer for highlighting interesting lines or suppressing superfluous ones.
Text can be highlighted and shuttled over to the industry favorite, CyberChef, where IOCs are enumerated and can be pivoted on, as depicted in Figure 4, as shown below.
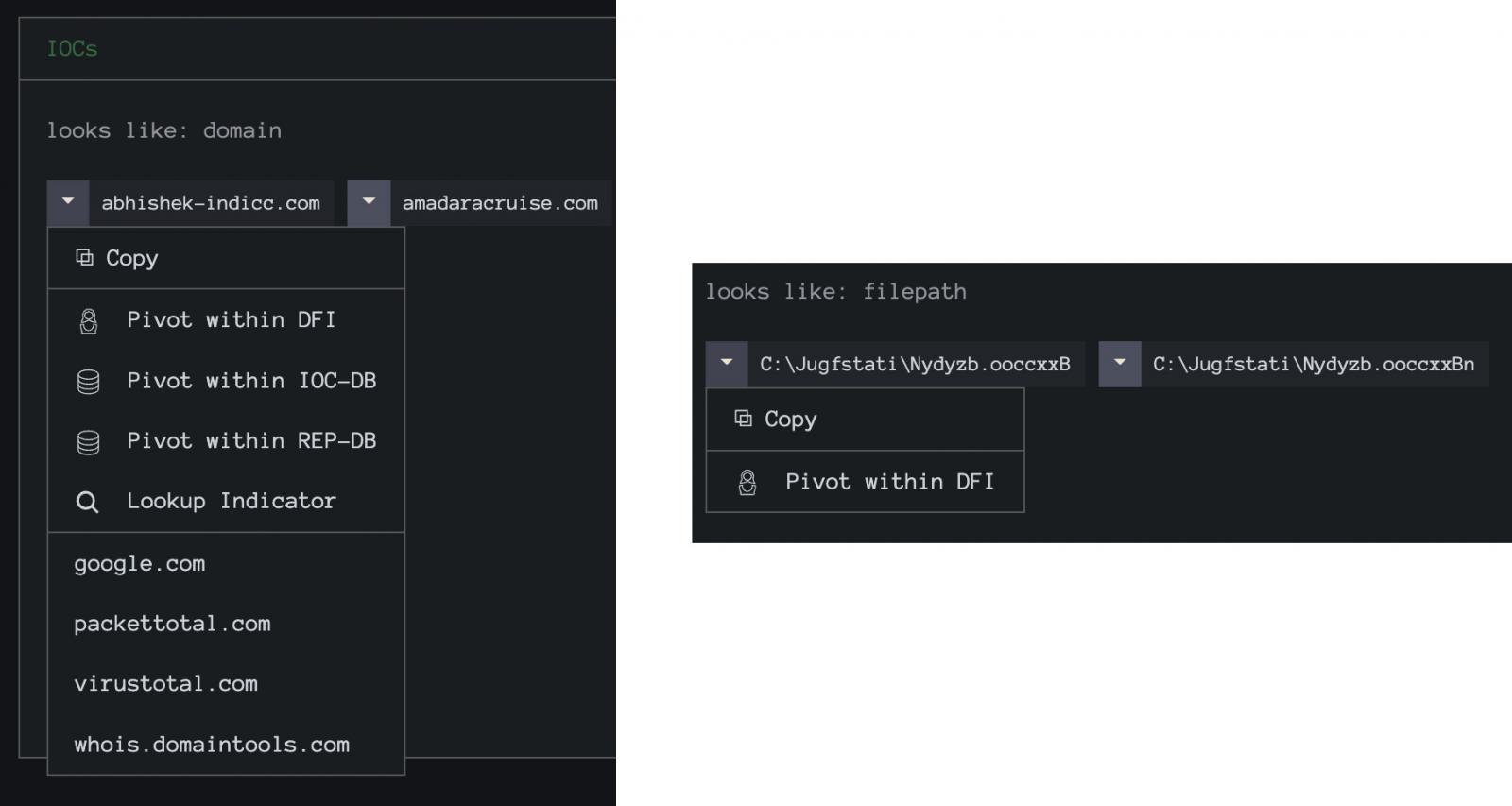
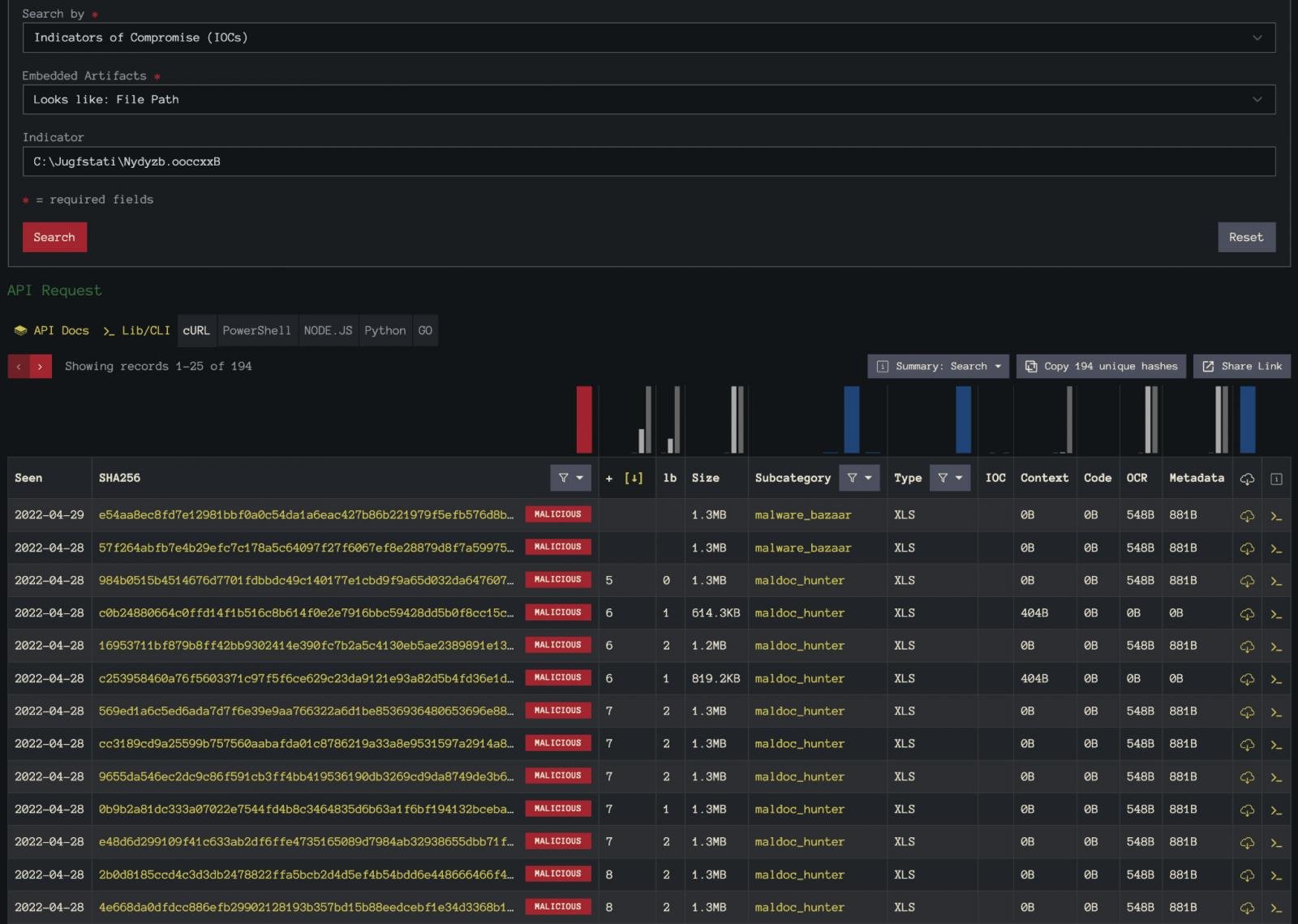
In the filepath example from Figure 4, we’re looking at a QBot sample. By pivoting on this unique-looking filepath, we can aggregate almost 200 additional samples for analysis. The results of this pivot are shown in Figure 5.
You can leverage our Labs API to automate the extraction of the network-related IOCs from all of these samples to shine a light on the overall infrastructure being used for this campaign.
Another approach towards discovering interesting malware is through a newer component of InQuest Labs, the Trystero project, where we measure the efficacy of the major mail providers in blocking emerging threats. For example, DFI samples found to bypass Microsoft O365 and/or Google Workspace are available for researchers to dive into and glean from.
All-in-all, the intent of InQuest Labs is to provide the information security community with both accessible technology and data to discover and thwart emerging threats.
Registration and usage are free. Feedback is welcome.
We host a number of power users in a community Slack, so feel free to reach out to us if you’re interested in Joining the Hunt.
