Cybercriminals and threat actors continually evolve their tactics to deceive and exploit users. One of the most persistent threats is smishing—a blend of SMS (text message) and phishing attacks. Recently, smishing campaigns have increasingly leveraged themes from the United States Postal Service (USPS), making them particularly dangerous and difficult to detect when targeted directly at users via text message.
How does this attack work?
First disclosed in late June of this year, users recently received social engineering messages via mobile SMS with USPS-themed lures using this basic format:
[USPS Notice]: Your shipment has been processed at our facility but is currently on hold due to incomplete address information. To facilitate timely delivery, we request you verify your address through the link provided below: hXXps://cutt[.]ly/kefjZuIG?KrK=agsoqsnEdd?spt=dKfL5GVQaY
Wishing you an exceptional day from the USPS team.
The URL shortener link redirects to an attacker-operated site:
hXXps://usoo.qygwdvpr[.]top/?session=256196fd967slv&user=193
>> hXXps://usoo.qygwdvpr[.]top/4b8ee6/GOEAEZ/CxJPFKuAA4A_Vh8PPl/AESkk4e?9_IkyAH/mN4XAhHeAEiTAK95suA_tkAKAAVTnAGpuIn terms of the mechanics of the exploit itself, urlscan.io captures the redirector and landing page for the phishing site, which presents a USPS Online lure.
https://urlscan.io/result/6770bd32-a452-43ee-ac7d-80946ad5ae8c
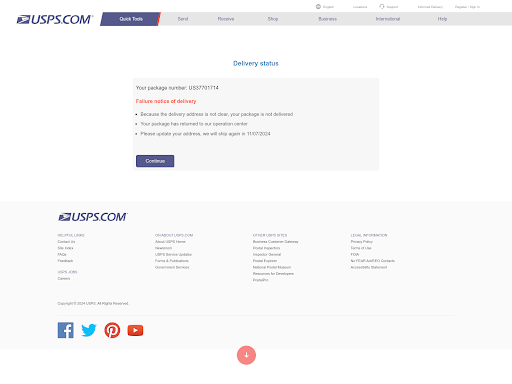
The page requires the user to click the Continue button to progress forward in the phishing kit. The next page solicits personal information from the user, including shipping address and phone number. Further interaction may also prompt the user for more sensitive information, such as login credentials and personally identifiable information under the guise of verification of identity.
From this landing site that the attacker controls, they can compromise the intended target in any number of ways – by having the victim enter their personal information into a form, by asking them to download malicious files, or even drive-by downloads on vulnerable browsers.
The real danger presented by this kind of attack is that it leverages the victim’s trust in a public institution like USPS and presents a landing site that is convincing enough to appear legitimate. Package and order delivery lures are commonplace in the threat landscape, given that many people may be expecting a purchase to arrive at any given point. Common clues that could trigger suspicion—like grammatical errors or odd page layouts—are not present. As a result, this kind of smishing can be devastatingly effective.
The Role of Threat Intelligence
In cases like these, threat intelligence is an important tool for stopping bad actors by focusing on the infrastructure and domains they use. Forcing bad actors to rebuild their infrastructure by disrupting their normal patterns drives up the cost of these campaigns and slows them down.
InQuest’s research uncovered some of the domains and proxies used by this group. Domain registration details and resolution show that the threat actor is abusing Cloudflare as DNS hosting and cloud proxy:
QYGWDVPR.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
qygwdvpr.top. 1800 IN SOA jean.ns.cloudflare.com. dns.cloudflare.com. 2344052238 10000 2400 604800 1800
qygwdvpr.top. 21600 IN NS margo.ns.cloudflare.com.
qygwdvpr.top. 21600 IN NS jean.ns.cloudflare.com.
usoo.qygwdvpr.top. 300 IN A 104.21.72.55
usoo.qygwdvpr.top. 300 IN A 172.67.175.168
104.21.72.55 AS13335 | US | CLOUDFLARENET
172.67.175.168 AS13335 | US | CLOUDFLARENETThe domain has been utilized as far back as June, with the operator using another subdomain:
emv1.qygwdvpr.top 104.21.72.55 ip A 2024-06-16T10:19:27 2024-07-11T12:40:38
emv1.qygwdvpr.top 172.67.175.168 ip A 2024-06-16T10:19:27 2024-07-11T12:40:38Nameserver analysis provides a set of domains with matching attributes that may be associated with this same cluster of activity:
twqkztxr.top
jgjqqkow.top
mrbtrzqz.top
jdsdgfrp.top
ievksdde.top
mtzcoets.top
ffohrmuv.top
mqeuwcve.top
qvmqfkyy.top
tvebrkvj.top
bezizesf.top
kwwqwtgl.top
mfqyzqaf.top
wrofpeqe.top
jmfllkrr.top
udwmarew.top
TWQKZTXR.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
JGJQQKOW.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
MRBTRZQZ.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
JDSDGFRP.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
IEVKSDDE.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
MTZCOETS.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
FFOHRMUV.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
MQEUWCVE.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
QVMQFKYY.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
TVEBRKVJ.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
BEZIZESF.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
KWWQWTGL.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
MFQYZQAF.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
WROFPEQE.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
JMFLLKRR.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]
UDWMAREW.TOP 2024-06-16 Gname.com Pte. Ltd. ns.cloudflare.com REDACTED FOR PRIVACY [email protected]Conclusions
Smishing attacks, especially those leveraging USPS-themed lures, represent a growing threat in the cybersecurity landscape. These attacks are designed to exploit users’ trust in well-known institutions like the USPS, making them particularly effective and dangerous.
Recognizing and understanding these smishing techniques is the first step in defending against them. By staying informed and cautious, users can avoid falling victim to these sophisticated scams. Furthermore, leveraging threat intelligence to uncover and disrupt the infrastructure behind these attacks is essential in mitigating their impact.
InQuest InSights Threat Intelligence Feeds
InQuest continually monitors the cyber threat space, broadly collects indicators of compromise, and curates them for incident response and threat intelligence use cases. Our InQuest InSights threat intelligence feeds provide bulk download or API query access to our actionable indicator data. Contact us for access to these and thousands of other active, relevant indicators to help your defenders uncover evil and reduce risk today!

