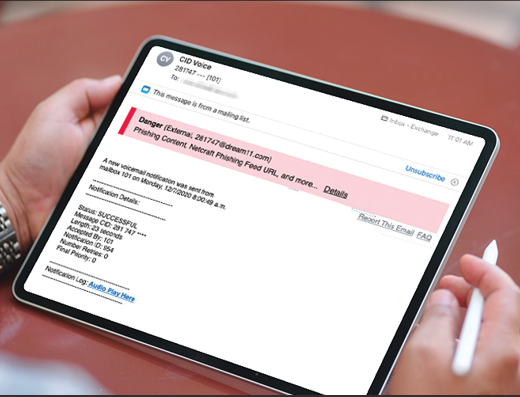
One of InQuest’s most distinguishing features is its banner system. While most of InQuest’s work detecting phish takes place “under the hood,” the banners are what recipients see. These distinctive yet unobtrusive signposts tell the reader where each email sits on the safe-dangerous spectrum. The color (gray, yellow, and red) gives a general impression. The brief text phrases explain why InQuest marked the email that way. The links in the banner allow the recipient to inquire further or report the mail to InQuest staff for further analysis.
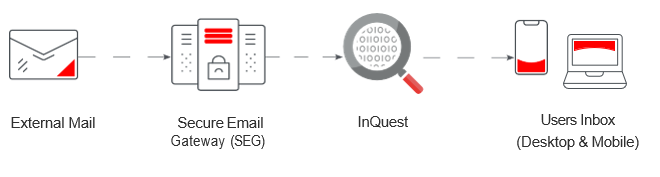
Putting banners in emails to alert recipients to the potential dangers lurking in messages is a highly effective way to keep employees safe from phishing attacks. A lot of specialists in anti-phishing technology fall into a category analyst firm Gartner calls Cloud Email Security Supplements (CESSs). Every one of these firms uses Microsoft’s application programming interface (API) to access Office 365 (O365), which accounts for the vast majority of cloud-based email systems. However, using API access means that none of these firms can insert a banner into an email before it reaches the recipient.
InQuest – because it eschews the API approach and instead sits inline between the secure email gateway (SEG) and the recipient’s inbox – can insert a simple banner into each email after performing its in-line analysis.
Banners serve two main purposes: they educate the user, and they let the user educate the system.
lnQuest itself is a group of interacting modules, each of which has a particular job. They are all unleashed on an email at the same time. This parallelism allows them to do their analysis in less than two seconds, thus minimally interfering with mail flow. Modules do things like answer the question, “Has this sender ever sent email to this recipient before?” or “Is this email trying to look like it comes from Microsoft? Some of the modules are quite complex.
At the end of the analysis, an aggregator module collects “scores” from the other modules to reach a total. It is this total that determines what color the lnQuest banner for a particular email will be – gray for safe, yellow for caution, and red for dangerous.
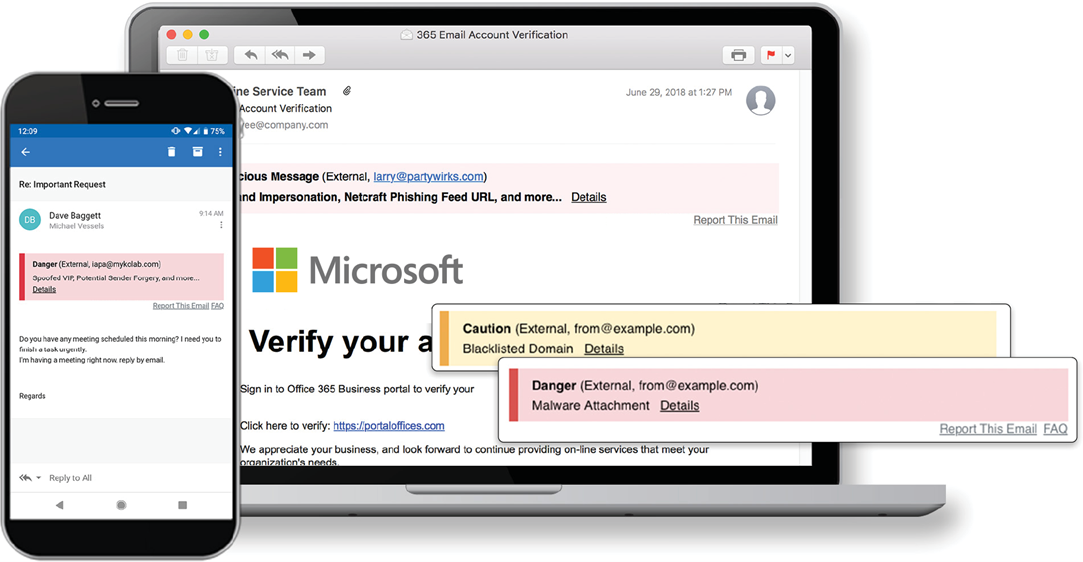
From our customers, we have learned that banners are highly effective at reducing end-user click-through on links to dangerous locations (i.e., URLs). One customer in the oil & gas sector said that clicks on malicious links by his end users were reduced by 15-20% a few months after lnQuest was installed.
While lnQuest does many things automatically (e.g., if a customer sets policy for it, the system can quarantine any email that would otherwise be given a red banner and delivered), we have found that human interactions are valuable.
The two-way nature of the communication is important. A recipient using the Report This Email link in the banner helps train the system so that future results are more accurate.
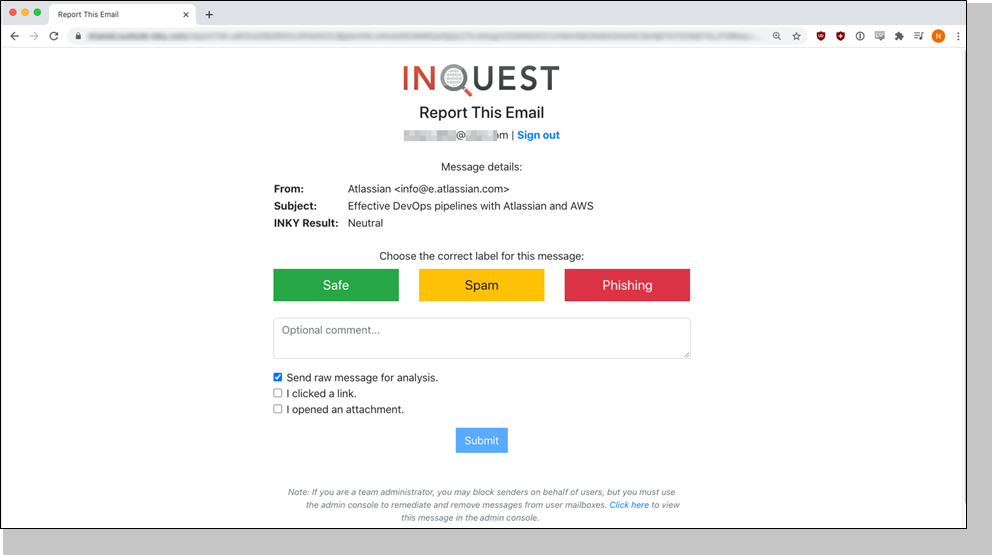
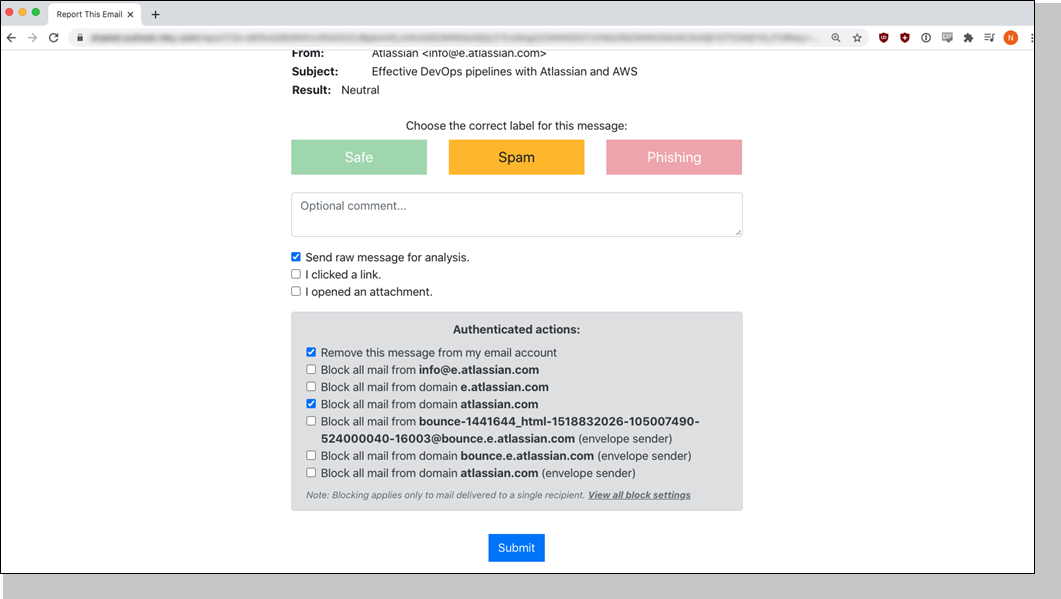
For authenticated email addresses, there’s also an ability on the Report This Email screen to mark something spam and block its address and even its domain (a superpower some customers just love!).
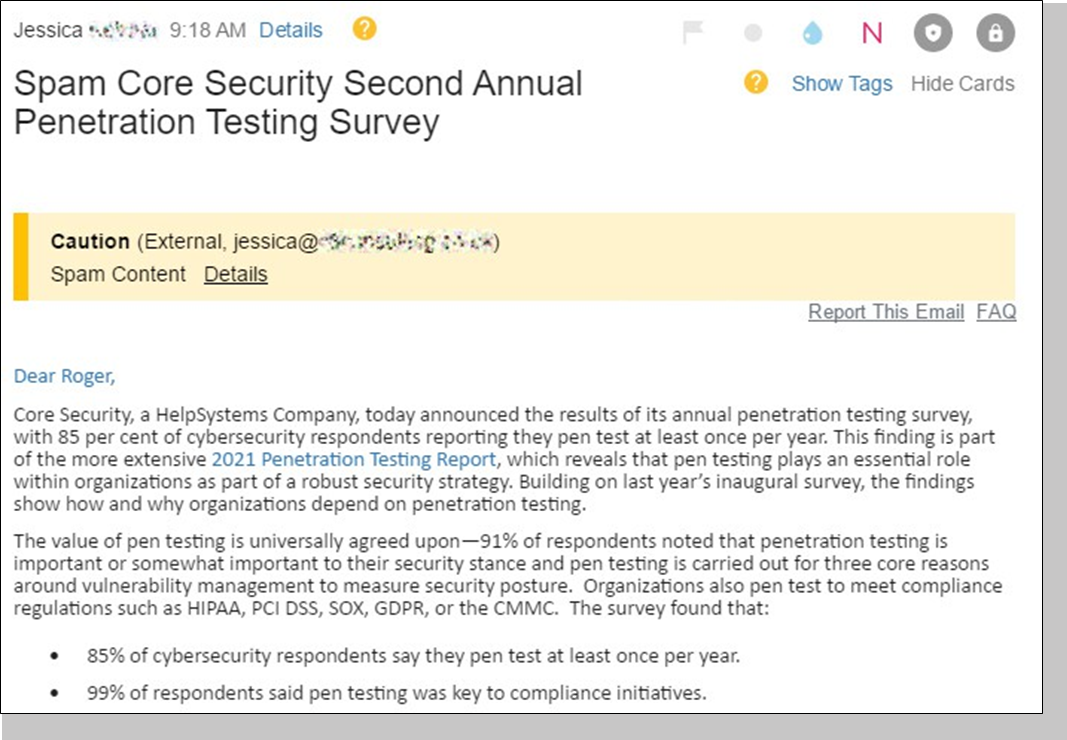
On the inbound side, the banner text teaches the recipient what to look for by explaining why lnQuest flagged an email. Each banner has one or more text phrases. These phrases represent the output of the various lnQuest modules. lf only one threshold gets tripped, only one text phrase is displayed.
But if a lot of modules’ thresholds’ are tripped, they all report. Thus, the recipient gets a lot of information about what lnQuest saw and didn’t like. A screaming red banner stuffed with an array of warnings is usually enough to cause a recipient to pause and contemplate why lnQuest was so offended by that particular email. It’s not without good reason.
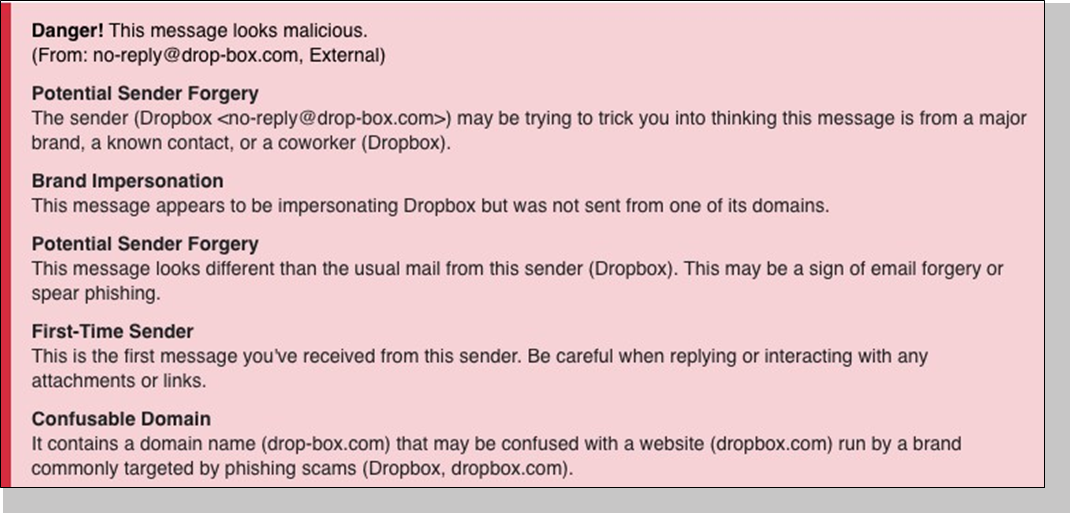
And the experience can be quite ominous when a perfectly crafted phishing email that looks completely innocuous is topped with an armada of bright red alarms.
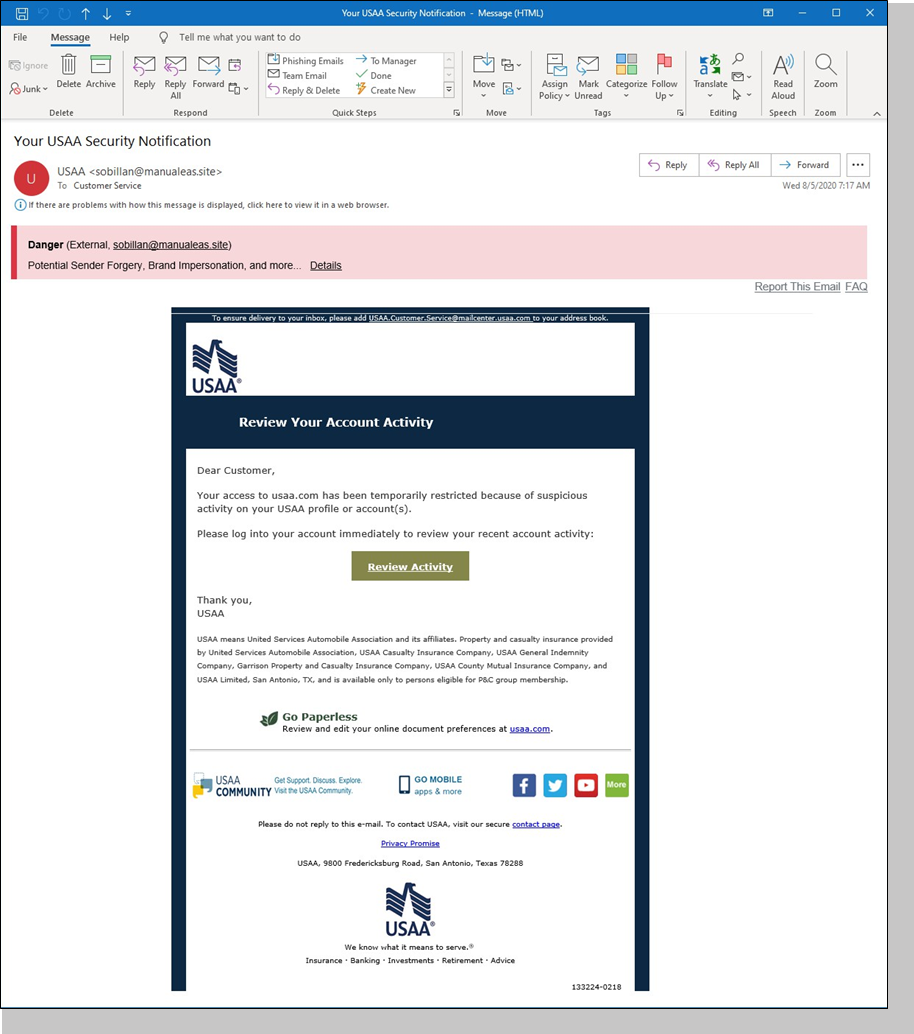
Such a display should give the recipient pause, preventing them from falling for the ruse. But it also lets them know that just because an email looks good doesn’t mean that it is. It’s not the Nigerian Price scams that most people fall for. Those tend to sink to the level of spam, and unwanted mail. It’s the ones that really do look like your boss (or the HR department, your Internet service provider, your colleague from another company, your bank, American Express, DocuSign, or the U.S. Treasury) sent them that can let phishers into your organization and trigger a whole chain of events that leads to a ransomware shutdown, theft of intellectual property, pilfered identities, stolen money, disrupted operations, or a damaged reputation.
Why InQuest?
InQuest provides the most comprehensive malware and email phishing protection available.
InQuest uses a proprietary blend of Machine Learning and Artificial Intelligence that blocks even the most sophisticated phishing attacks that get past other systems.
InQuest uses proprietary technology and algorithms to “see” each email as the recipient would. Unlike a person, however, it can detect an email forgery and/or malicious or suspicious content. Once detected, it can redirect the email to the quarantine area or deliver it with disabled links and warnings.
Alerts show within the email itself, which allows it to be viewed on desktop or mobile. This is a significant difference from other systems, which display warnings in headers and may not render properly in mobile applications.
InQuest sits downstream of any email system, including Microsoft Office 365 and Google Suite.
InQuest scans every sent and delivered email automatically and flags malicious emails.
A comprehensive dashboard allows admins to both see the bigger picture and drill down to specific attacks, individuals, and unique messages. A robust search allows for detailed reporting at the granular level.
It can be set up and ready to go in just a few hours.