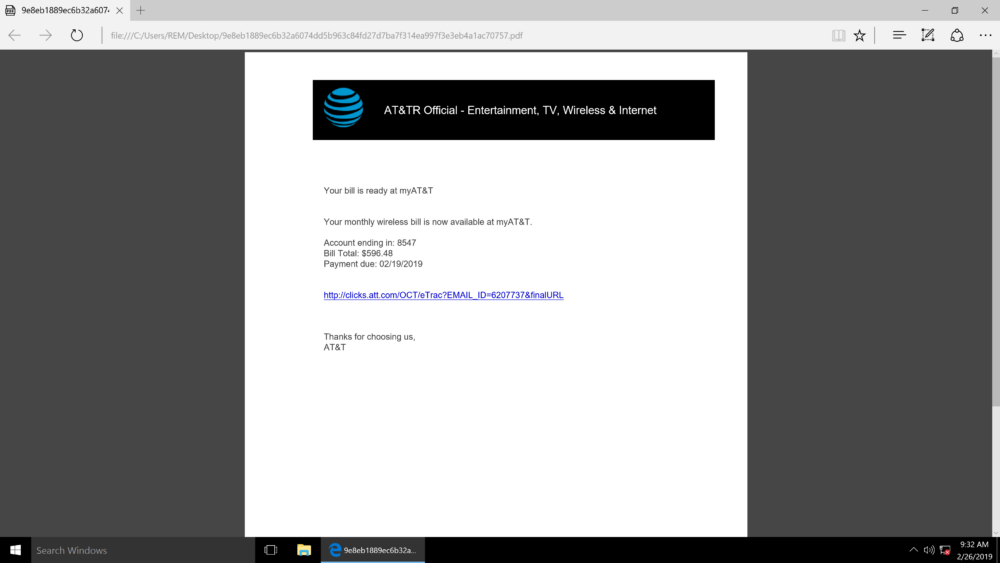
The InQuest platform is fully open in the sense that all analytical areas are extensible via customer defined intelligence which can include keywords, hashes, standard IOCs, and fully fledged YARA rules. This article covers the analysis of an interesting customer malspam encounter that was identified with a customer-defined YARA signature focusing on abnormally high levels of entropy within the semantic context of document files. This attack occurred at an undisclosed customer site and specifically targeted three different individuals across the organization. Before we dive into analysis, here are the details of the original file.
AT&T_Account_02_19_19.pdf
——————–
|
File name File size MD5 SHA-256 |
AT&T_Account_02_19_19.pdf 24.78 KB 0f627a1450851494145328fcdeb12195 9e8eb1889ec6b32a6074dd5b963c84fd27d7ba7f314ea997f3e3eb4a1ac70757 |
The sample is made available on our github malware repository:
[9e8eb1889ec6b32a6074dd5b963c84fd27d7ba7f314ea997f3e3eb4a1ac70757](https://github.com/InQuest/malware-samples/blob/master/Quick-Analysis-of-a-Customer-Malspam-Encounter/9e8eb1889ec6b32a6074dd5b963c84fd27d7ba7f314ea997f3e3eb4a1ac70757)
Entropy analysis is one of the methods that can be employed for detecting this campaign and is our primary focus. Many readers will already be familiar with file entropy but entropy is a concept with applications ranging from computer science to thermodynamics. Under our context (Shannon) entropy is a measure of randomness in information. Measuring entropy of code, for example, helps malware researchers determine if a sample of malware has been compressed or encrypted. The most common measure entropy is at the byte level, which results in a scale ranging from 0 to 8. The lower the entropy, the lower the chances are that the code has been obfuscated in any way. The higher the entropy, the greater the chances are that the content is compressed or encrypted. High 7’s are a good indicator that some compression or encryption is present in the underlying data.
In this case study, we’re not analyzing code entropy. Rather, we’re looking for anomalies in the entropy of semantic text (specifically the English language). Here is a glimpse of the user-defined rule courtesy of the analyst that wrote it for use in a [retrohunt](http://blog.inquest.net/blog/2018/05/09/retrohunting-with-inquest/) operation. (Note: This rule is tuned for the English language and utilizes InQuest Deep File Inspection to focus on the semantic content of the file)
rule suspect_semantic_entropy_v3
{
strings:
$magic = "INQUEST-PII=cat" // InQuest DFI Marker
$long = /w{128,}/ nocase // long string
condition:
filesize > 1024 and
$magic in (filesize-30..filesize) and
math.entropy(0, filesize) >= 5.75 and
$long
}Commonly, English text has an entropy under 2. A much higher threshold of 5.75 was utilized here to reduce false positives. Additionally, at least one single long string must be found.
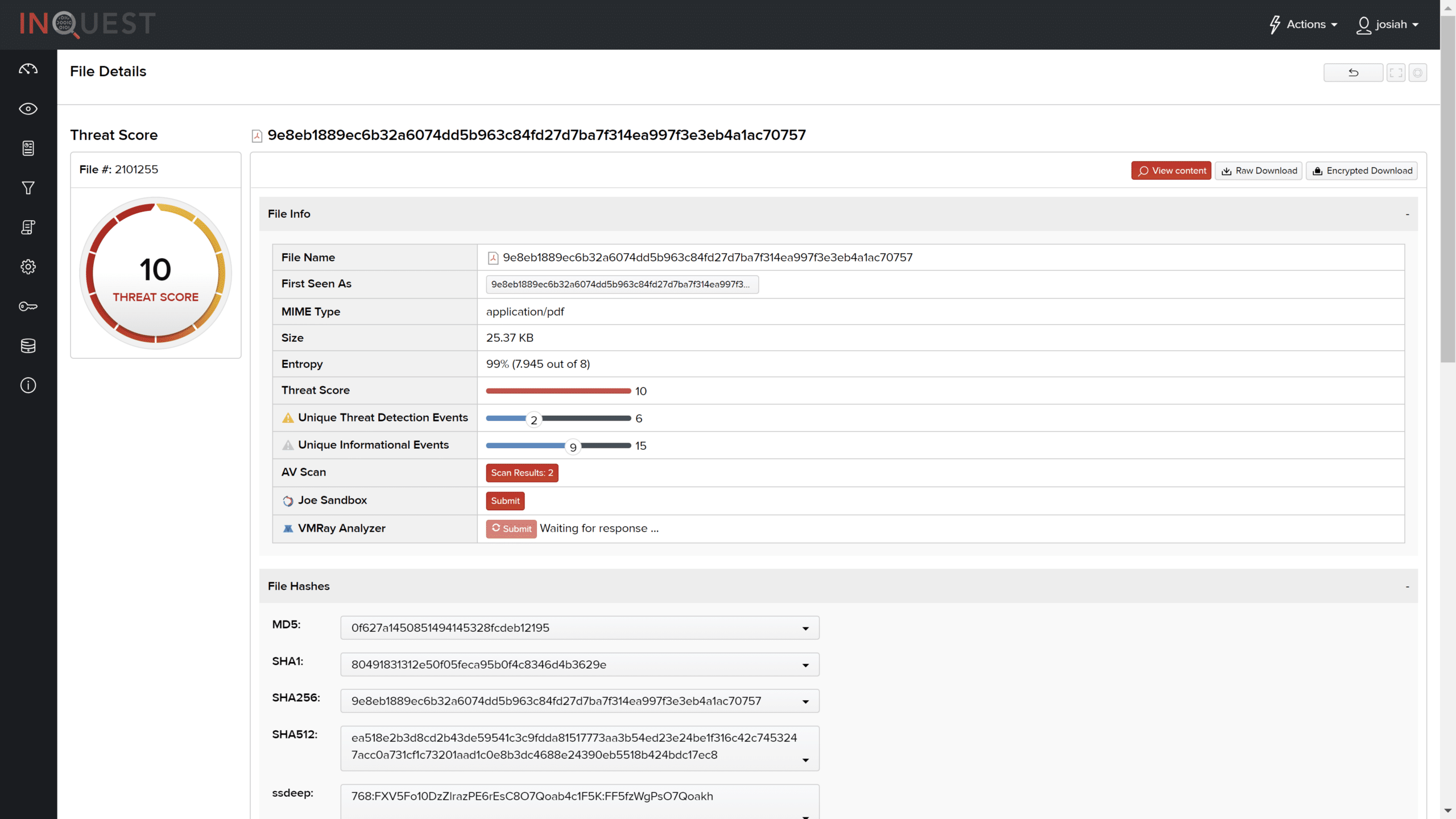
The InQuest platform appropriately identified the file with a threat score of 10. Notice the file entropy is ~7.9 and results form the previously discussed user-defined signature.
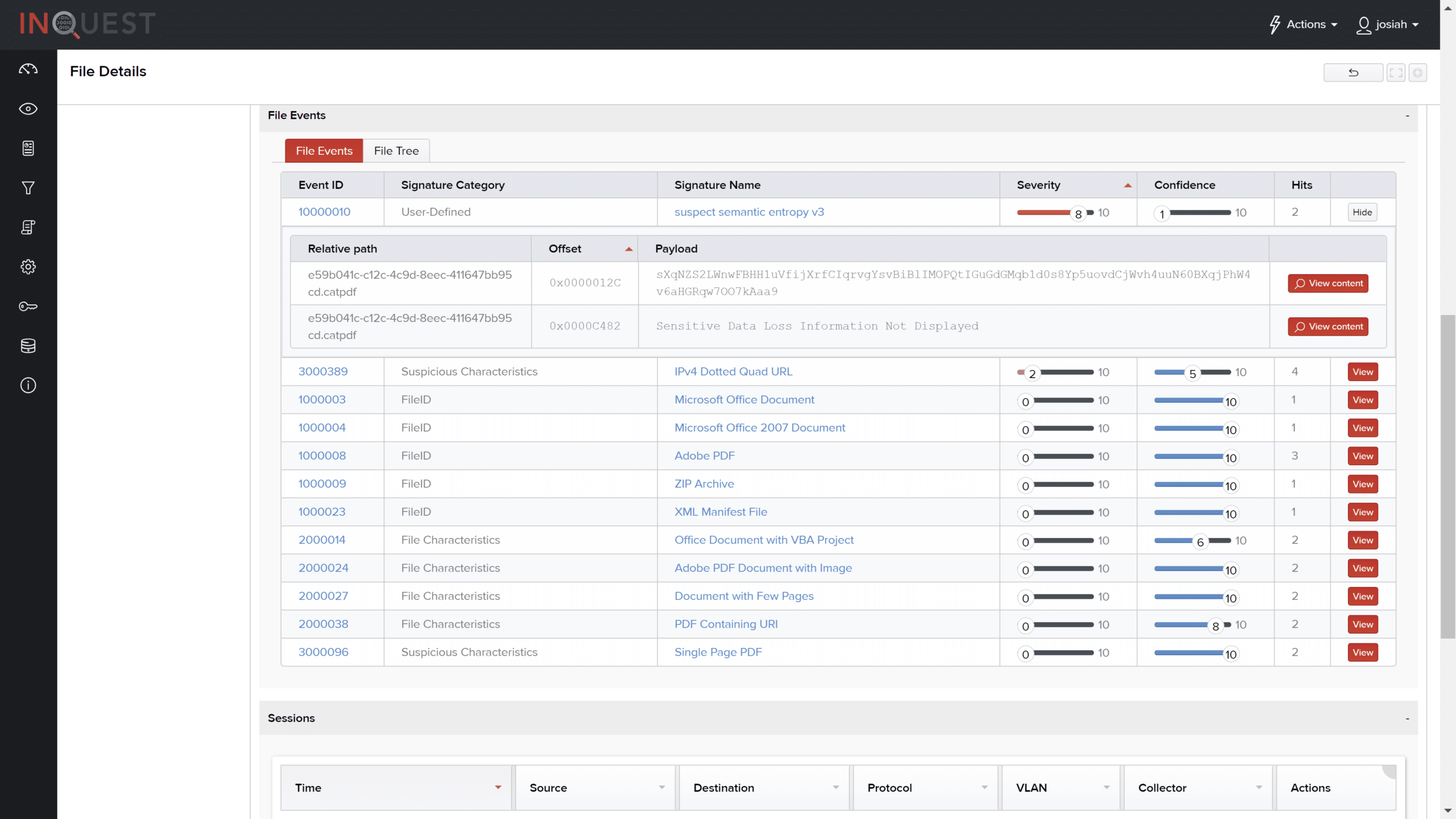
The following screenshot details the different File Events (signature hits) that resulted from analysis of the file. Notice the seemingly random text discovered by the `suspect_semantic_entropy_v3` signature defined above. This content is indicative of obfuscation techniques used by malware authors.
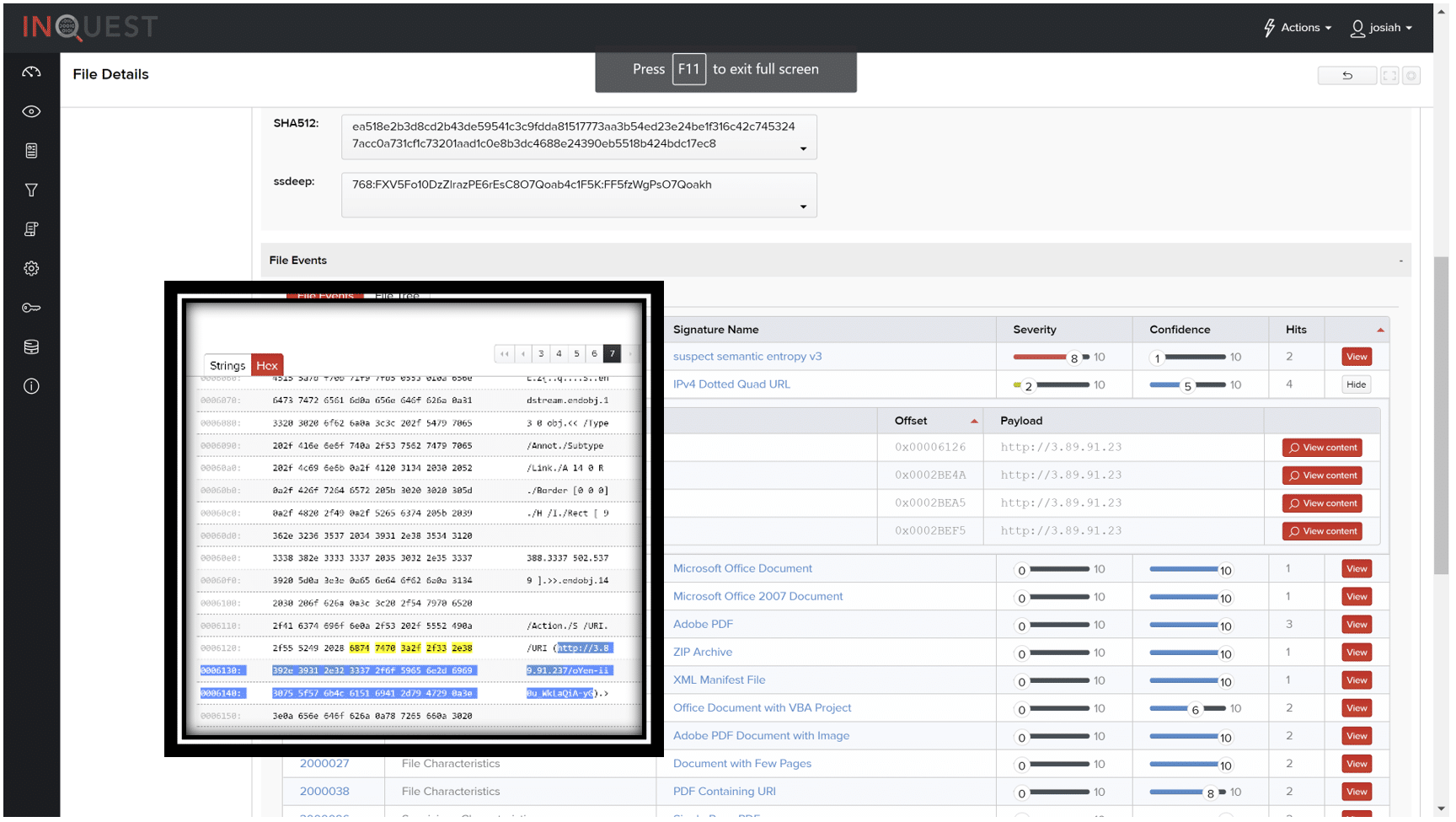
Within the file, there was also instances of an IPv4 Dotted Quad URL. The link `http://3.89.21.23`, when expanded, pointed to the location shown in the strings view.
The PDF below is a view of the document and downloads the following file “INSTR726098292327.doc” when the hyperlink is clicked.
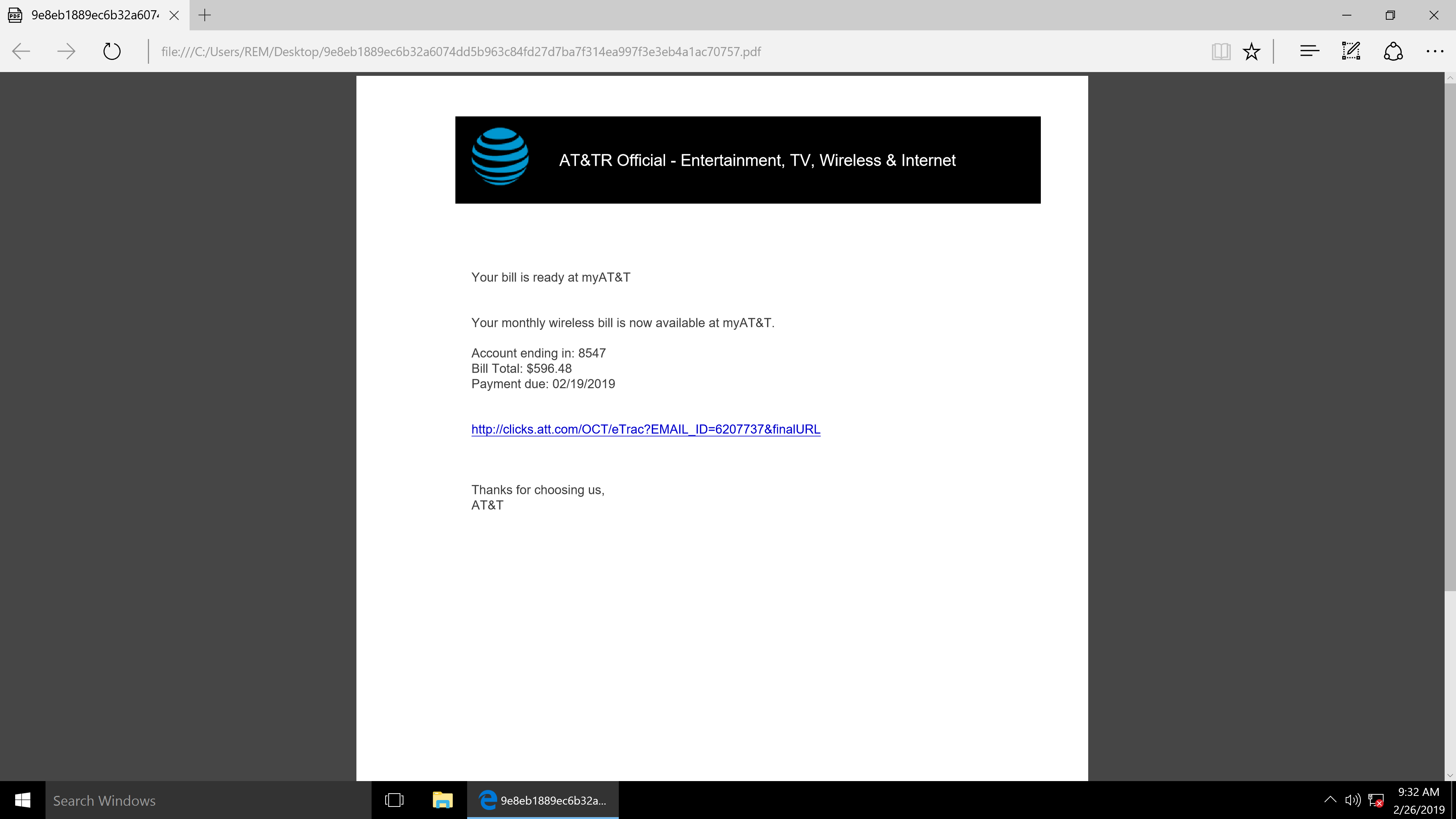
HTTP GET Requests
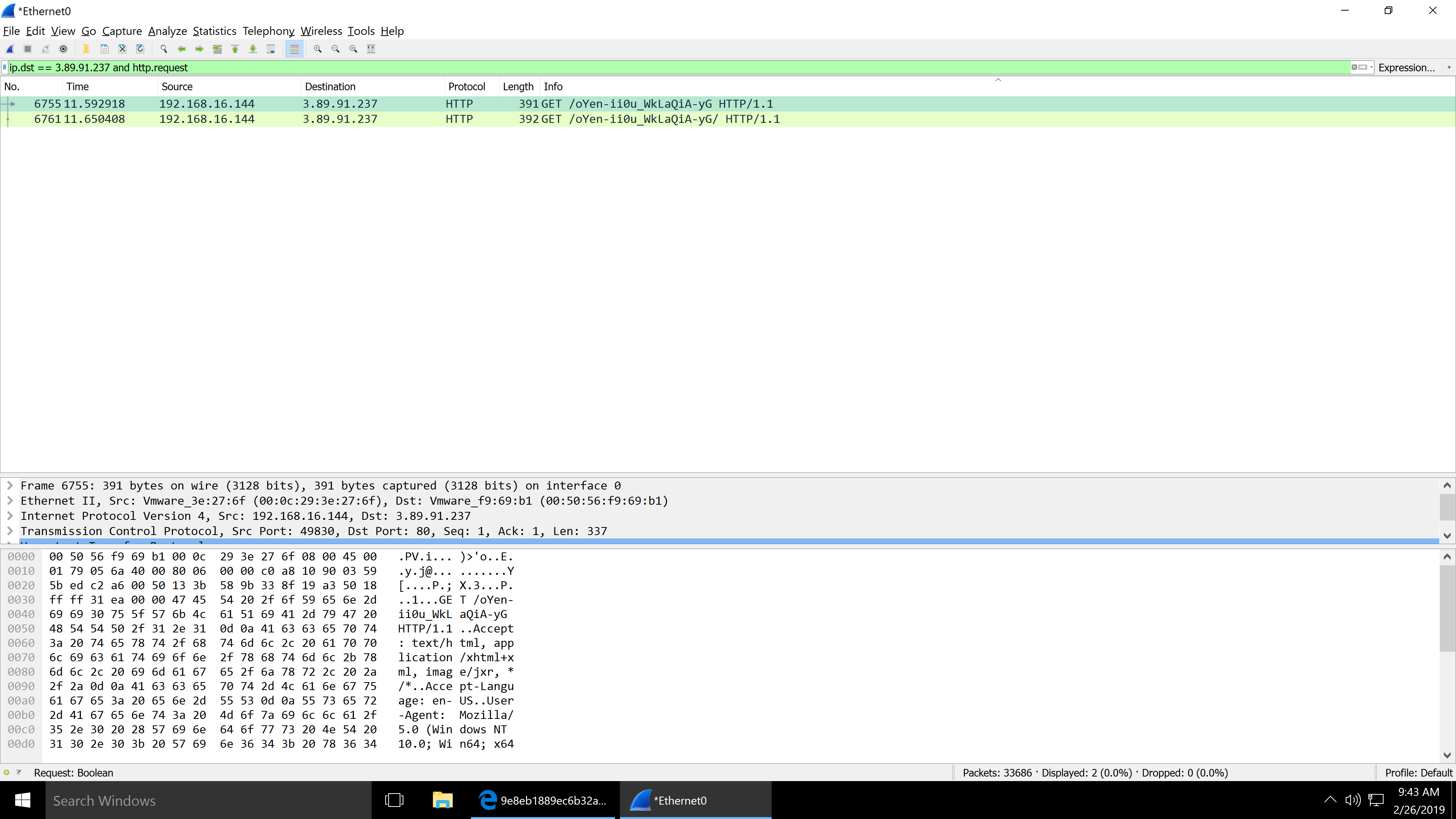
TCP Stream showing the file that was downloaded.
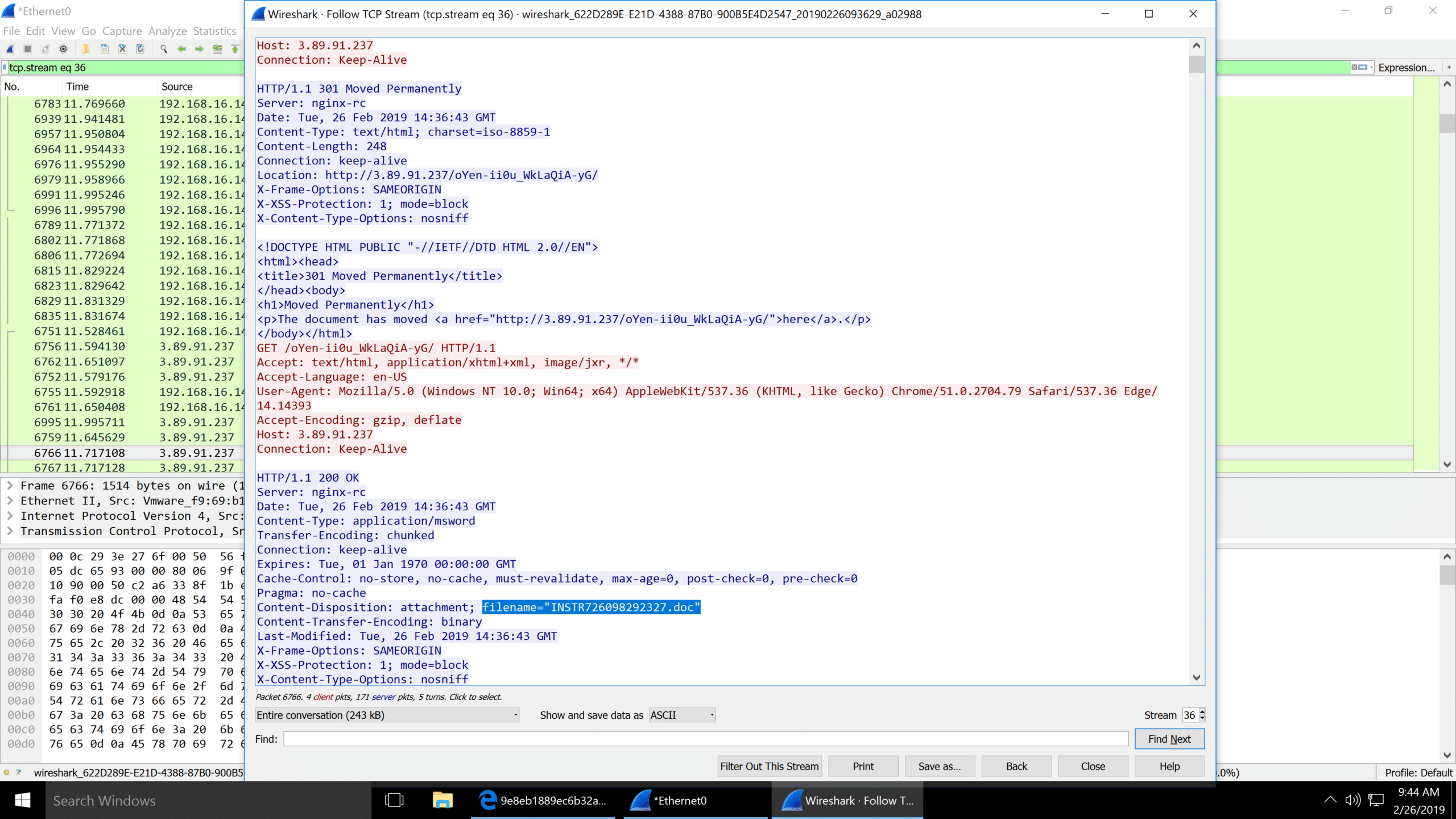
Here is a sample of INSTR726098292327.doc located in the InQuest malware repository: [e6ba4bd149bfa84ab57c7926c7635e162e459d0e9e419bb3c8d8af8e41c043c9](https://github.com/InQuest/malware-samples/blob/master/Quick-Analysis-of-a-Customer-Malspam-Encounter/e6ba4bd149bfa84ab57c7926c7635e162e459d0e9e419bb3c8d8af8e41c043c9)
VMRay happened to have a detailed report on this Word Document that is available [here.](https://www.vmray.com/analyses/e6ba4bd149bf/report/vti_score.html)
INSTR726098292327.doc
——————–
InQuest was also able to detect the threat within this file with a score of 9 out of 10.
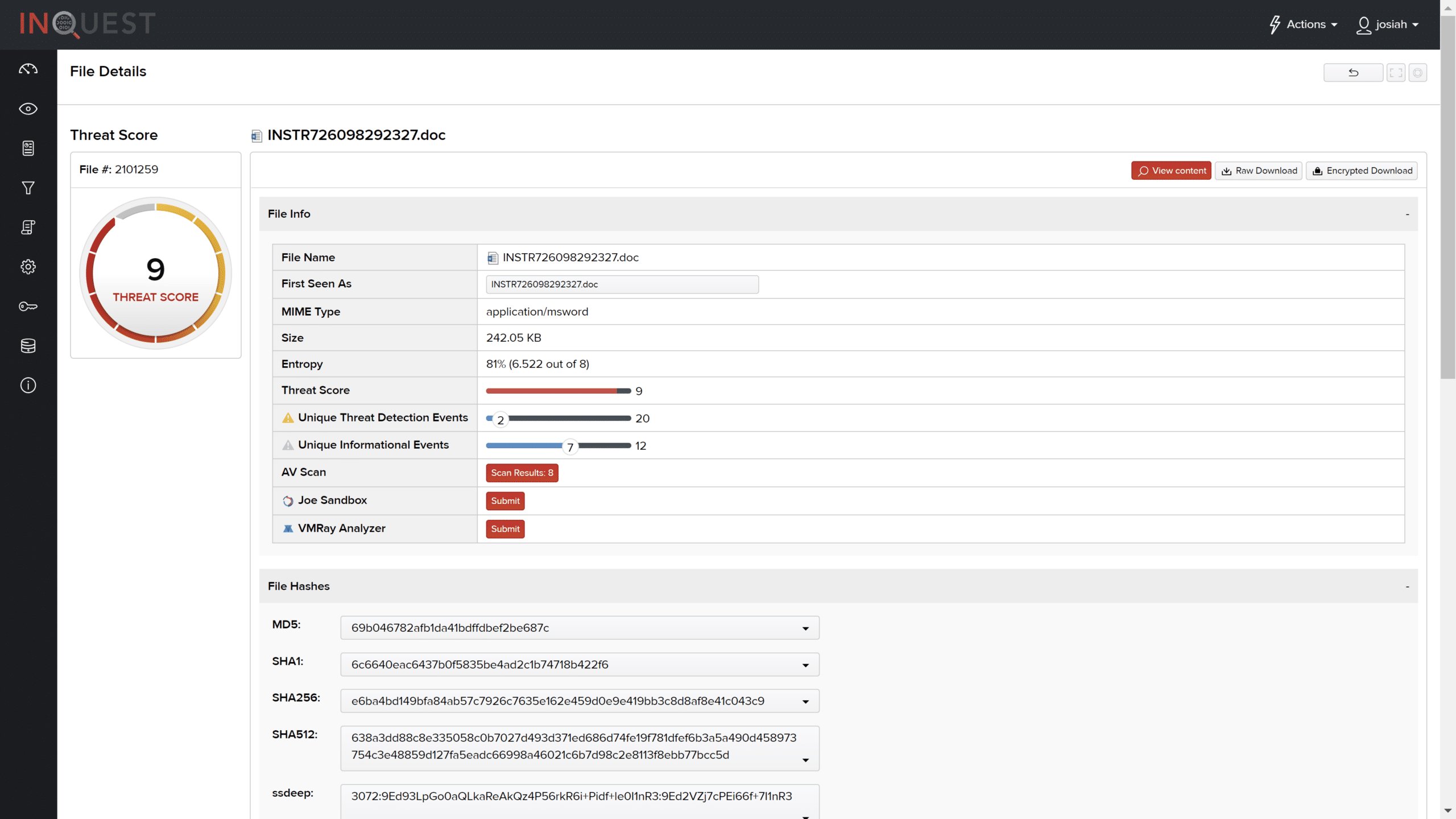
Of note, a malicious characteristics signature detecting an “Embedded VB Macro” and a signature identifying suspicious “Microsoft Office Macro with Suspicious String.”
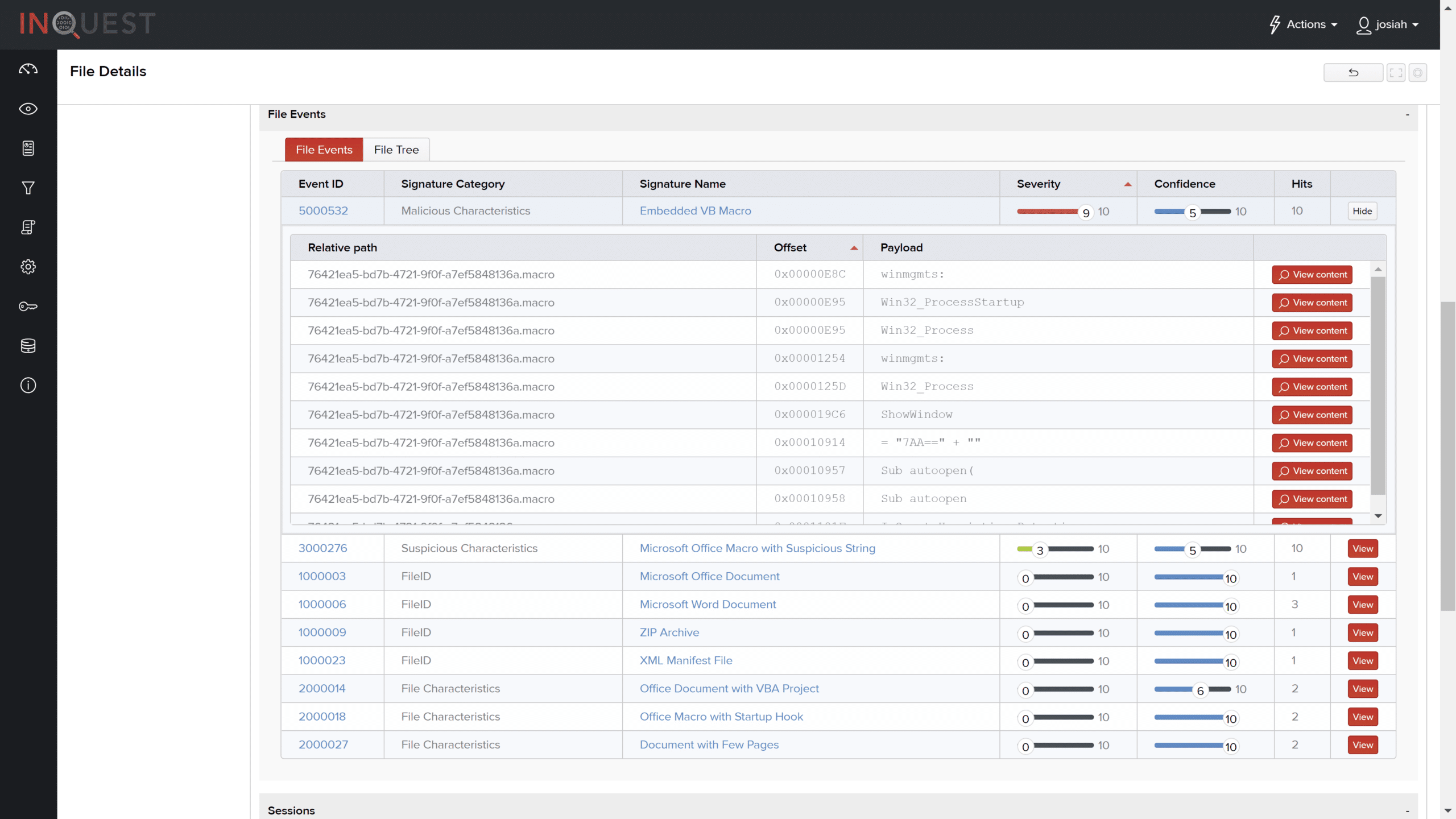
Within that file, there is a rather convincing statement to enable the macros.
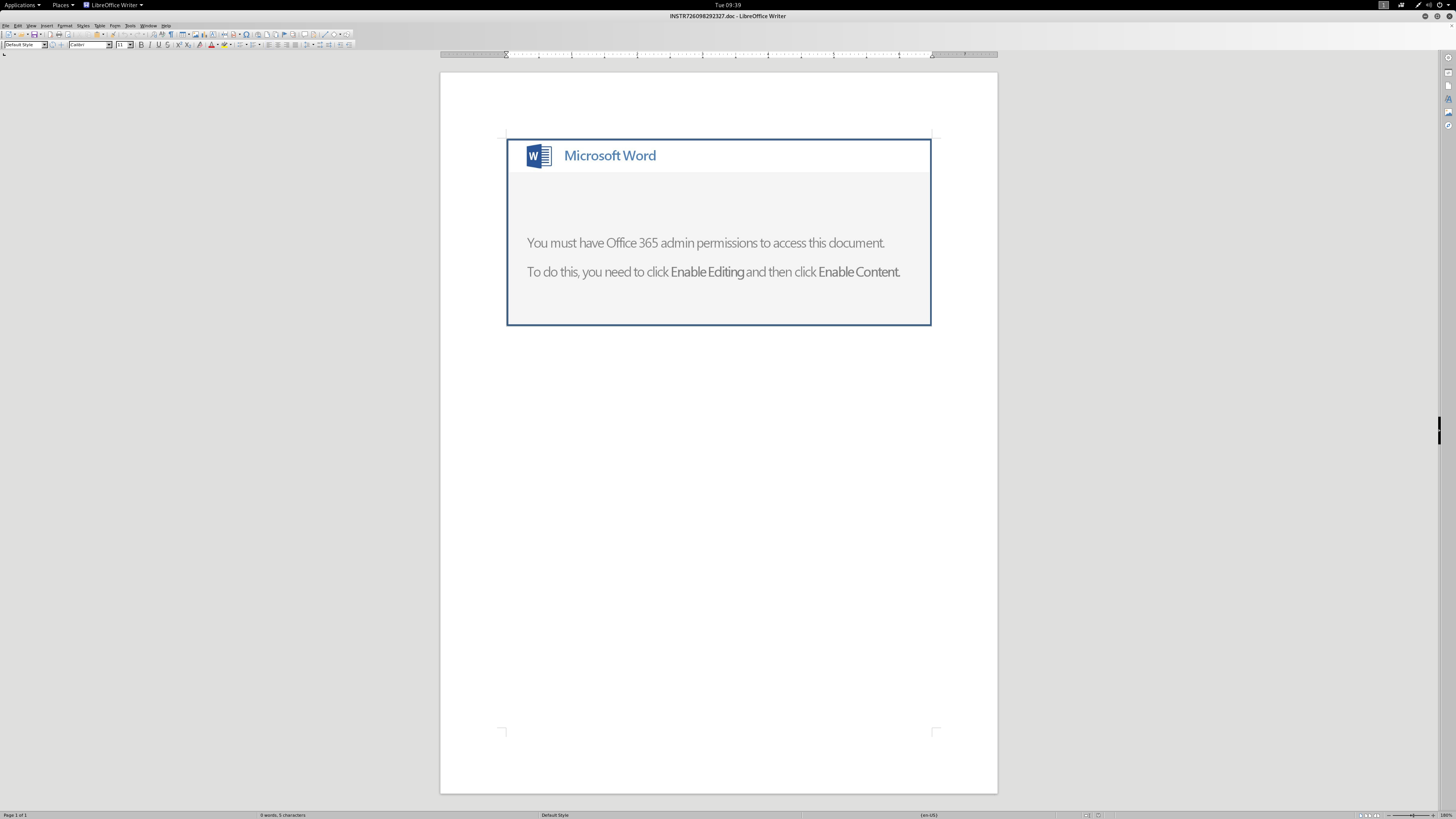
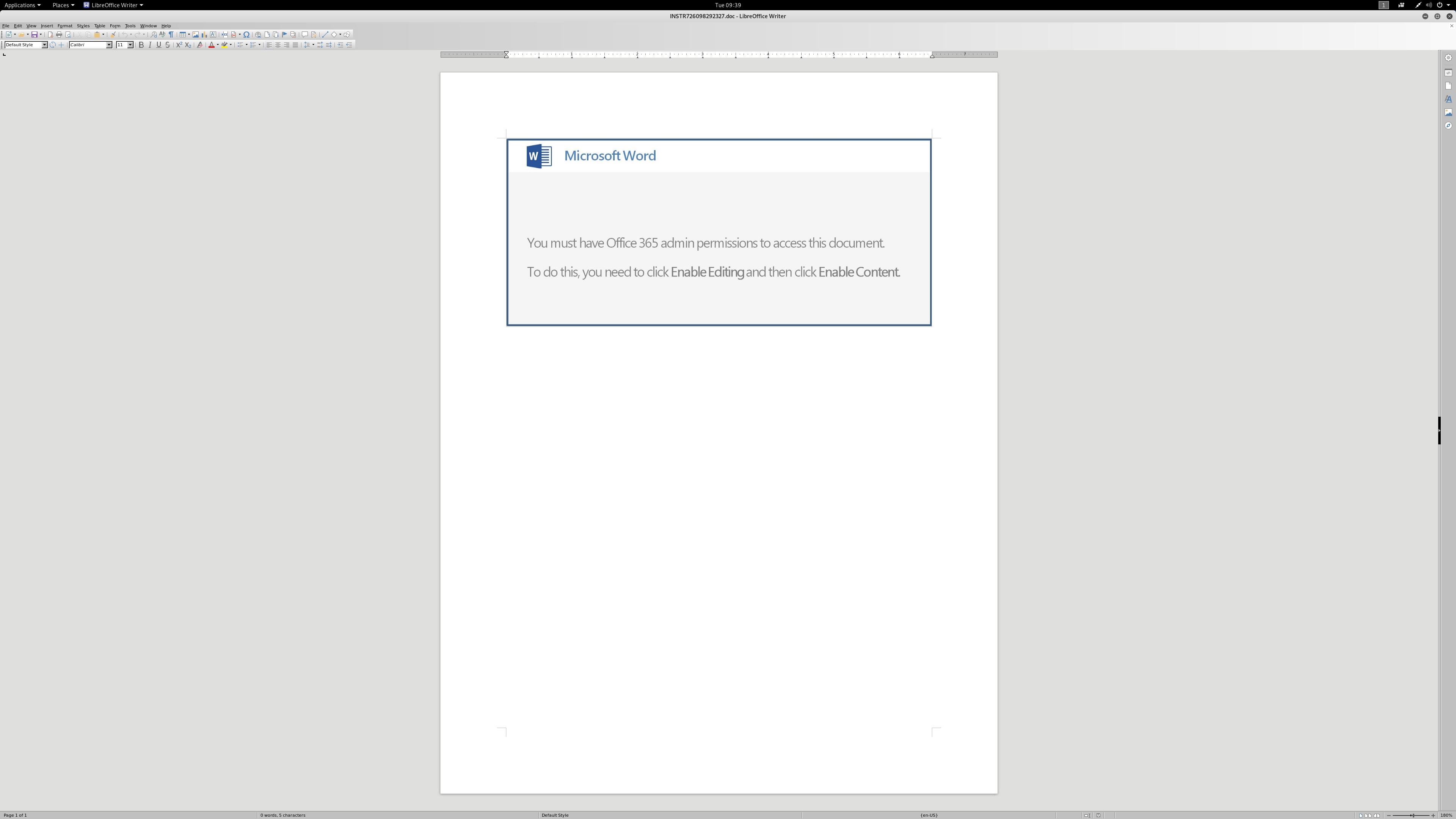
Looking through the macro, it is heavily obfuscated.
When the macro is enabled, the document downloads and executes a variance of the Emotet Banking Trojan.
2dc18b533e82b6bfe4ca849a61197806714d541d8a77ad8feeb02342baa83854
In this scenario, a user-defined signature combined with our proprietary Deep File Inspection (DFI) engine exposed a myriad of additional context to aid in detecting threats.
.