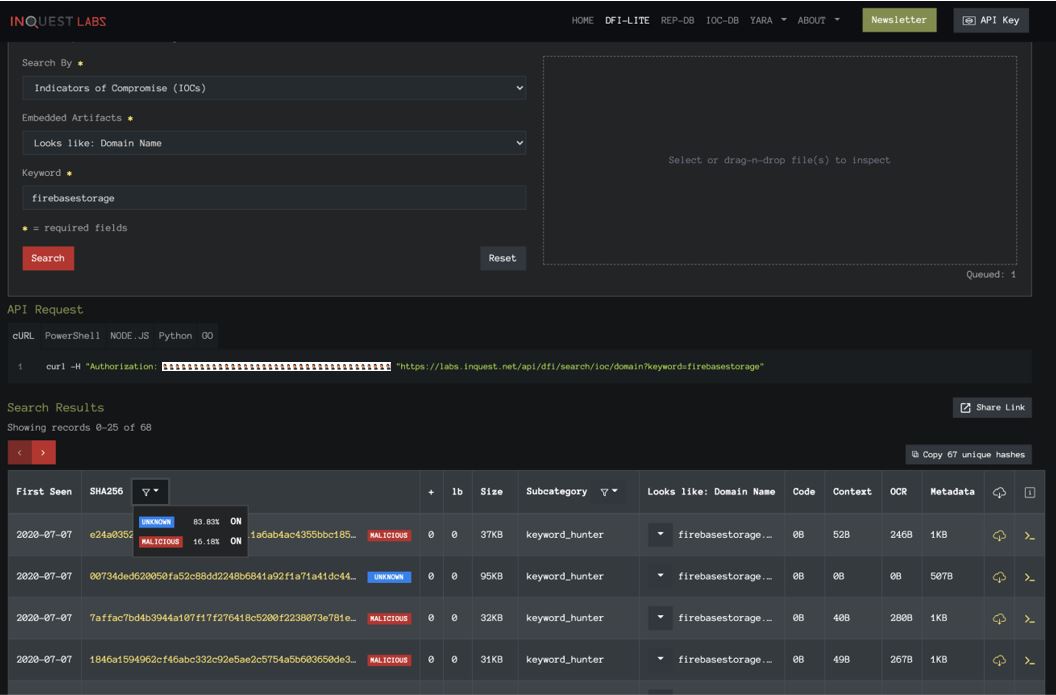
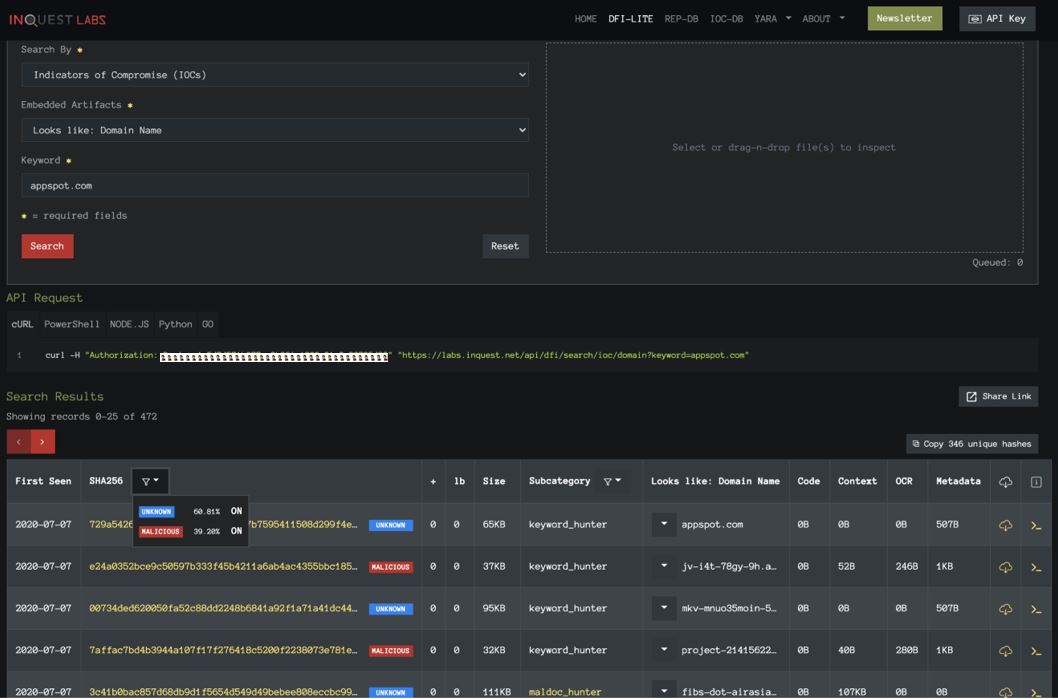
A common tactic seen used in Phishing campaigns today is to embed the Phish within Google’s Firebase Cloud Storage platform called Firebase. By doing so, attackers are leaning on the reputation of the Google subdomain firebasestorage.googleapis.com. Part of the InQuest Deep File Inspection® (DFI) process is to extrude embedded layers and subsequently any discovered IOCs. We can search the InQuest Labs file corpus for those that reference any domains with the word firebasestorage or appspot.com. See the links / screenshots below:
firebasestorage query
appspot.com query
Using InQuest Labs, it is convenient to copy the hashes to the clipboard and then paste into a file.
Selected Hashes
00734ded620050fa52c88dd2248b6841a92f1a71a41dc44e2d6c2d0642b3de34
028c5b04b442a33088aca7af15808c313c7ec58da2fa8c551d9e21906acd6e9c
064dae57f0ef6faa0169af15f97d734cbc9a3fbad68acfff20f22416da198fdd
0ca72696e3393a5e32e9a5a642ea7672a81aeb6e32ac15f884cfd0b080bf062c
0fb683ae8d90973695c73561ee14ce4c0372340c1efb61fd04599e53377d2200
11aafdc27ba11fb2498d57031d95a1b06c30e71f75e9e6aba4dbe4e45e5defd3
1846a1594962cf46abc332c92e5ae2c5754a5b603650de3d2c4f49dc8acbbae1
18c91cdb9a7e5e1f0611260f1dd1d3c76f71fd22c76b8c58f89f1a1c9e658d4c
1aa2c41f5b2b80e68177931551208562b10eccccfa33fbb4ba0b782b20ba26b6
2259385e72f954820fcd3d833027502c5efeb6ea3c7ef8cc39cbe3c806de2cc4
22fa4747d424699ed6a9ee7cc3067c35e30d85eae49e1c9f48f1721535f3d3ea
230c2326500dac5a98e7f2ff2117c60facd77a263b2a693844bd25cf6701e38a
24cc337aab81f27736f49e0bd12b482f792f49a4de315af8172792f948bc1111
257bd0d059caaafc105a70f13903fb6db2bb0e77e7572039cab0bae17621475b
2d9504c4c0c6e4333530d0c170f655229172dd0ca85c99d6ed975bb2673d990d
2dfb1f8488dbad21af804dab9d6acf9d4abc0cf943b4d57bc09de94070266824
31c80c1a244aea95541a6e5880c23d84c36aba55b6c2f45db6cc31dbdf97da37
35736646e45f81a9fa36d20b28e2b50d4b4d4e1bcaa8c18802fdd0ee559d3276
35b0cd91c522541c038e0df6c1d1212a359d7dc42cf6c0df86924e1419826320
37cffc94bab71f60bd41bd727e24d9b32f2d784ba41ea53edd1f252981367f59
3bd0e0e3ba238c9de6561e3195d737eea10b2e246444a87323f7cc1c84ab2f9a
3cb233edb8c72ec12bd560e944d8b896d9f2c5ba2b4ab4d1e6c19e01ca6167d6
431725b053260bca08c0ee0175fc8b0a971a30be2f88e5b036cc81293098ba63
447f5be8d025066b90729cc7b24cb0cdc1ecdc742e1fdbd909ee3ae806791cb3
4cbf8f6f4802a6b85221f6167011a2813380aa42541262301111a640d91e4bed
4ea2a8adc8efd3b1d5fcfdfb31a8ec1d44dda6f89912f76090612758d941e7f4
5683055b8a736c9c07ca60cb04e4aa368de37e65af416b94b3f7295951e73226
56ba5d48bc623f3cdf12a2e297c8f0b21da6732f1fdf6c0d1844a437f735b357
5986c56a4ddd3b340b08ee7741e8d9331990fb4b23deafff4c2793a4f8debc03
619233a7b313fde2897dbe93a8311f75f95fa4eb53557b99d2fdc4552d63099e
61d35d21cf4bb5cd61269d17bda1d1501175a027ed0460bd53a97917714c2f8b
653144cf87fd8525a51d01060f41d7faf8301775bb55d9a7cd17d1a8f955648c
65514e0a471f643d28785702b42b2545f3839a346363ebabf6062d3fdca08260
67901d590ba04c0c689267e6853af3a09c17ebc0d7b9b7ce902d779d4a3305d8
6e6ee8635bc6bfa27faf264142e4decf3b8ccb97922afdae9d0c70a449f822ea
75e08ae2785d0f9bb481ab1f6e6c9099910671df2bc2b5bbe7108da4330fc990
7679335f8cd3ee4c19d33ab42c9e469a9da3a26d04c4698005b3075f0298bbe3
77ed632237ca8f7ff69c03c5db4ac6c2c42316bf9b30ce61c5f760d263eeb584
7affac7bd4b3944a107f17f276418c5200f2238073e781e1d7086c92d07099eb
9355e72f6f800b1f783afb3be4c93f85c3acab188fc6f6446afd52c4466b3348
aa4885a45d1a6faf3a99f7211aec839db03dce00b1587e9beae86d76aea971c2
aea99693704cd156dcd163a22c0f3487f6299162b8f27d9fe814f906396c70f4
afc4a78a78af190783c0c563855e11107b969c2b5be6aa6a881b572030e8d633
b354aef559556b9c3904e1cf996e5a917d960ceda209da5c632220ff81fb253e
b4cc6a228791d156bb0076ed18de91118db2ebbdac50ebb74ceedfe4d65c5727
bb18d212b1bdf427930b90f5eb32827bb5f9ba5bcb2795c8e50363bbf2db96d2
bb481a653a82664041dfb90c2b55f8f646a2b523631c94294a4b37757e44550f
c8f0a280b860f007795298abf7486e66ae4200b215bacade4611aaada6cdfbb7
ce2e197100fb928b335932781b3f469446c394a32a48495a240dd2ab2f5e5279
d079508e51d1e33096d69d5a0d44f2a2d7bdc2bfff4d02c3e0ed31b7fffb60da
d0bc5925a293a48c8b00191ddc6bcf6f672e6730e8e96728bdcf655c02f300f7
d26b4880ba53d23cbcb58b0843bf6ff195aac2b10130a2cb03e65fef55438331
d31abdb9b76c8f6a21d7e24f47585f15a7e7d4ac56a97d114f91627e763be81a
d338d83e22dd85aef6666b8cda34eb2acf117de24f840c5a273a0f971a26ec3b
db9126f88f4cc8df9e0f0e8203f3f765c4b9b65b69ed037ebcfc558d541df2de
dc5e106543cdda86501cdcfa00fa550d46e1bbd4d3d4f5a857c19f3264d22d9b
dfe19cba116cc1b8f339e02ccfde1520dcc1396b2236f6b58d29c4633ee3a72a
e24a0352bce9c50597b333f45b4211a6ab4ac4355bbc1859bffdfc794eb9c661
e2c57e00a950474c83ed8de82a1230f20a5b0cc1525fcbb298accfccf05b3593
e39e26400060f5d55f3c13842789947ec07b6c86c3b5615ea27fe27ebc37812e
e938973eed8e245675ef813881b051faa5242e970045c4bc3c614975dbd172e1
f28e86448b83f59aa598d7d07981174aa53cc43abd8eb521cc991aa97f941adb
f71a5cea1b1929a7c4906f54c408c969ababa64be3e65bfd5dfa6551b6ebe871
f85debcd02e4f07f87e13b63927d6ac1f339046a2f37f037bb5cf0220190fdd3
fd7961b7b613c15dd453114d515bd030fc4f6f51de03ca6b703c95b31f1dbc0c
ff885150a9f02a89a4a0ee19c8c7169815dfc7bbd4a56dd23b63b2a5f5922a2c
We’ll then use the InQuest/python-inquestlabs lib/cli tool to for some command-line fu:
$ for h in `cat hashes.txt `;
do inquest_labs dfi attributes --filter=url $h \
| jq -r ".[].value";
done | tee urls.txt
Examining the statistics from the results:
# URLs extracted.
$ wc -l urls.txt
2837 urls.txt
# those with 'firebase' in them.
$ grep firebase urls.txt | wc -l
72
# unique firebase URLs.
$ grep firebase urls.txt | sort -u | wc -l
50
After removing the appspot application name, we see the following list:
adminreview.appspot[.]com
adobepdfonline-719fb.appspot[.]com
awele-5ebd4.appspot[.]com
de-t4-5r-6tygh-u6g-v-h.apps
efh-b4-y5gt-8778-7g.appspot[.]com
exam-net.appspot[.]com
g-ty-frd64es-trcy.appspot[.]com
gbe5mns.appspot[.]com
gfrf-gyh-iuiyu-tyrdt-fg.appspot[.]com
gr-b-46-53g-y5-4t-e.appspot[.]com
gr-nte-rgwea-fbg-nh-yt.appspot[.]com
hg8579hh-9h79.appspot[.]com
hgemememeem.appspot[.]com
homewebsite-e6707.appspot[.]com
j5-yhtejm.appspot[.]com
jpee-c0134.appspot[.]com
jv-i4t-78gy-9h.appspot[.]com
michmichis.appspot[.]com
micrososftoffice365apps.appspot[.]com
mkv-mnuo35moin-5moib-6mo3n5i11.appspot[.]com
mkv-mnuo35moin-5moib-6mo3n5i12.appspot[.]com
newweb-f38b4.appspot[.]com
nirs-42d97.appspot[.]com
owa0s5koo5bxs5ohdk.appspot[.]com
pkkkksksksks.appspot[.]com
project-2141562284063338550.appspot[.]com
project-4821784334140323971.appspot[.]com
project-6870194580473866225.appspot[.]com
safety-fed.appspot[.]com
springboard-eb346.appspot[.]com
teewaya-ae9c5.appspot[.]com
updt-gen-host.appspot[.]com
user3987267105468.appspot[.]com
vhjr-bfeur-fiugib-giu.appspot[.]com
wbebwebprogress.appspot[.]com
xxx-1-c6a5f.appspot[.]com
Next, let’s see how many of these are still active:
$ for url in `grep firebase urls.txt | sort -u`; do wget "$url"; done
xxps://firebasestorage.googleapis[.]com/v0/b/xxx-1-c6a5f.appspot.com/o/fire-b.html?alt=media&token=c637d664-45f5-42ed-aa81-c6831a5cf647
hxxps://firebasestorage.googleapis[.]com/v0/b/xxx-1-c6a5f.appspot.com/o/fire-b.html?alt=media&token=c637d664-45f5-42ed-aa81-c6831a5cf647
hxxps://firebasestorage.googleapis[.]com/v0/b/homewebsite-e6707.appspot.com/o/home.html?alt=media&token=132be9ed-fc2c-42da-b101-8a0fc9e658fd
hxxps://firebasestorage.googleapis[.]com/v0/b/micrososftoffice365apps.appspot.com/o/index.html?alt=media&token=53aa7076-677d-4642-9c68-f6e2c0c07bc5#[email protected]
hxxps://firebasestorage.googleapis[.]com/v0/b/safety-fed.appspot.com/o/ja%2Fdomain.html?alt=media&token=272cc119-412f-4717-83c3-d82bb65e2362&[email protected]
hxxps://firebasestorage.googleapis[.]com/v0/b/michmichis.appspot.com/o/lacreamama.html?alt=media&token=70ce47ff-4f54-4adc-bee8-e1d4db8339a0#[email protected]
hxxps://firebasestorage.googleapis[.]com/v0/b/updt-gen-host.appspot.com/o/mscsq1-t-check-packet.htm?alt=media&token=29357eb4-0d5c-409d-a403-4875969d5e7d#[email protected]
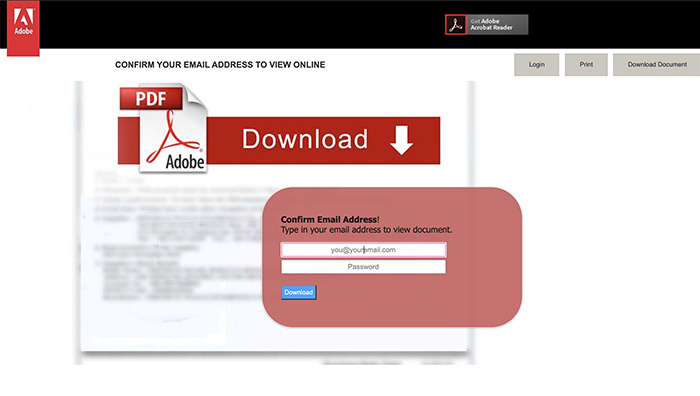
Here are a few screenshots from above, as these campaigns are frequently ephemeral and may be gone as of the time of reading. Note there are two generic templates, one targetting Adobe and the other Microsoft users. The third screengrab is a targeted Phish against Red Bull.
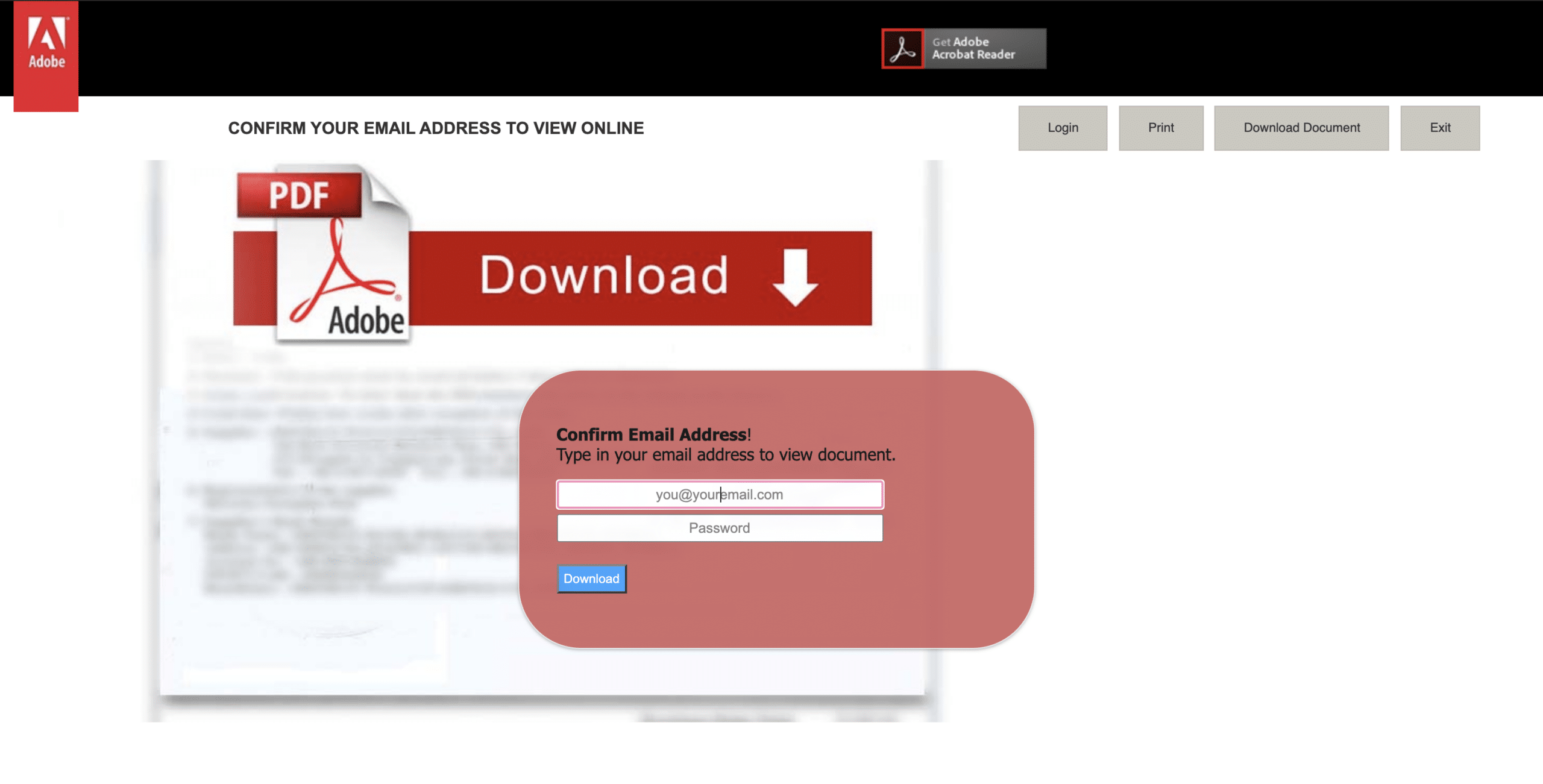
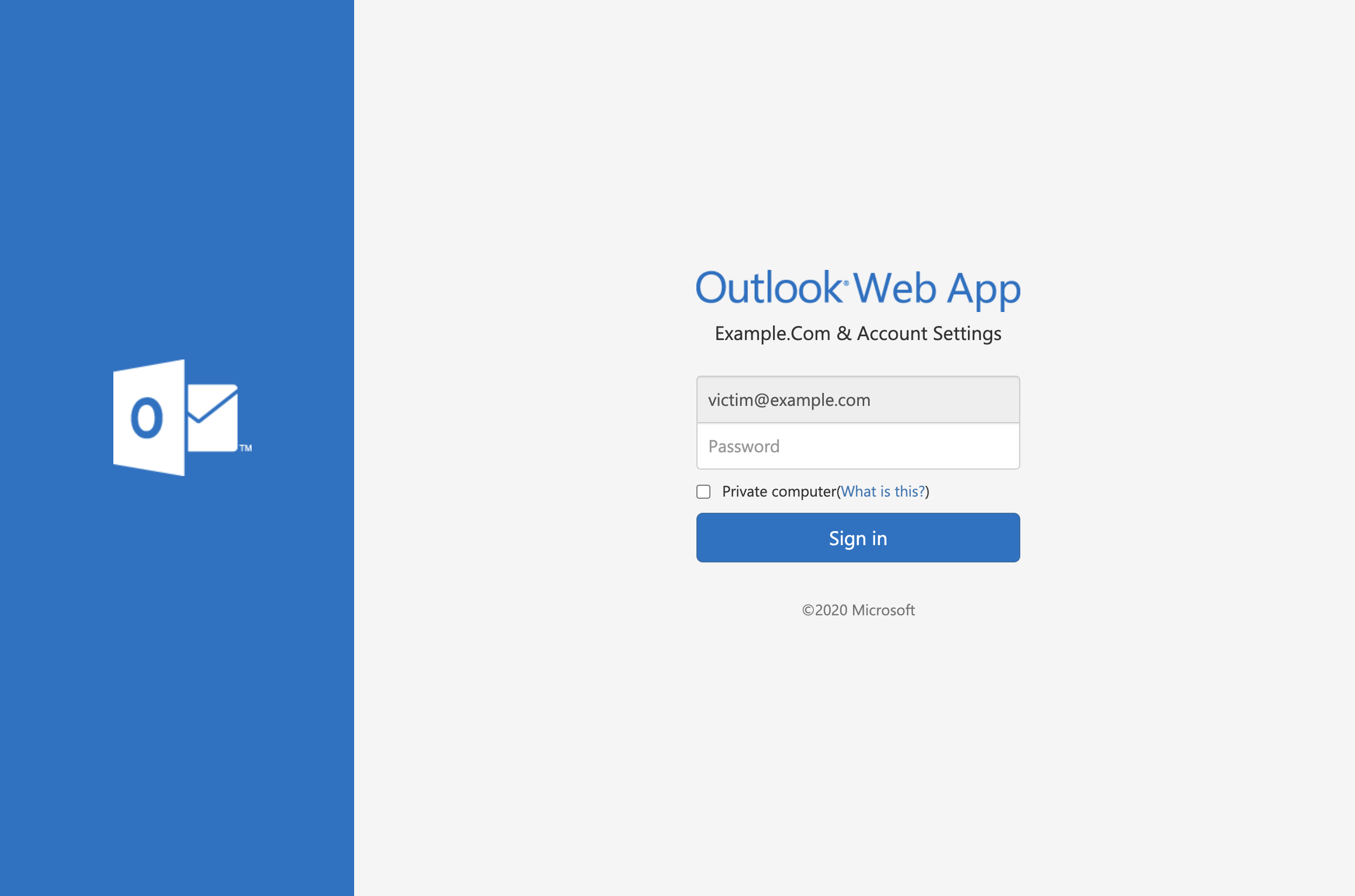
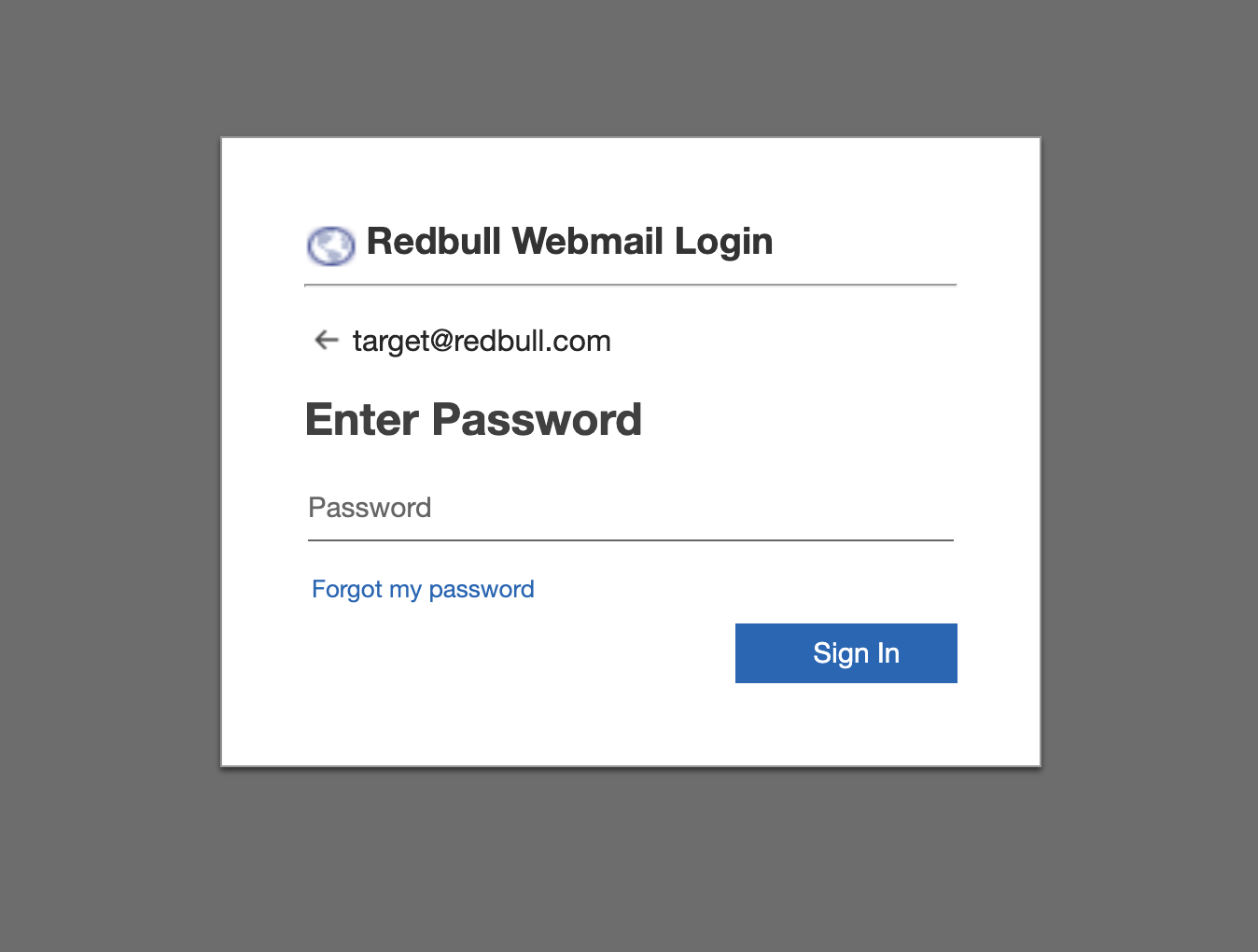
On a final note, the REP-DB and IOC-DB data stores also provide value with these pivots:
- REP-DB
- IOC-DB
For some additional reading with content driven from InQuest Labs, have a look at these blogs! - ZLoader 4.0 Macrosheets Evolution
- Detecting Coercive Lures with OCR