InQuest discovered an open directory hosting several Agent Tesla payloads, as well as several separate web panels for the administration of different Agent Tesla malware campaigns. We decided this was a good time to have a quick look at this malware family, it’s capabilities, and the artifacts found in the open directory.
Agent Tesla is a malware family written in .NET for Microsoft Windows systems and has much in common with spyware in it’s capabilities. It has many spyware like capabilities such as stealing credentials, keylogging, collecting screenshots, capturing web camera images, and gathering clipboard data, but it is often seen in more standard malware campaigns and uses common malware techniques for obfuscation, unpacking, and data collection. Recently, Agent Tesla has been distributed in the wild through phishing emails and malicious Word documents containing macros to drop and execute the malware.
While not directly related, Agent Tesla could almost be considered an evolution of the Pony/Fareit malware family in that it is most often used in campaigns by being coupled with another primary malware payload and its main use is for information collection from infected hosts while the primary malware performs it’s designated task.
Field Notes
Field Notes is a new blog post series meant to quickly share threat data, Indicators of Compromise, commentary on current events, or other brief types of analysis with the community at a higher level without performing in-depth reverse engineering or deep dives into a given campaign, actor, infrastructure, or otherwise. Many researchers often post short briefs on campaigns or threats as Pastebin posts, GitHub Gist’s, or Twitter threads but we feel this blog format is a great medium to get across not only the technical analysis and indicators but also some contextual information on the threat or event of focus. The complete series can be browed by tag:field-notes.
Agent Tesla Execution
Once an Agent Tesla payload gets executed, it creates a second process/payload and ultimately transfers execution to this process in a rather standard way. The second process gets created in a suspended state, and executable code is written to it using the WriteProcessMemory call. Once completed, the ResumeThread function gets called, and the secondary payload runs.
After extracting the unpacked version of the secondary payload, we can analyze the final .NET malware. Using conventional analysis tools for .NET like Reflector and dnSpy reveal mangled function and class names, paths that lead to nowhere, and overall a highly obfuscated application.
During some analysis attempts within my Windows Virtual Machine, Reflector itself would crash when attempting to decompile certain sections of the source code. After moving to other analysis applications, dnSpy and ILSpy, I was able to dig through the code without further issue. Even though the code is highly obfuscated, manually digging through the code can give you the overall idea of what each function does, and you begin to understand the bigger picture. At this point, I began renaming functions to more suitable names that explained their use, such as “DecryptString” or “SendC2Message”.
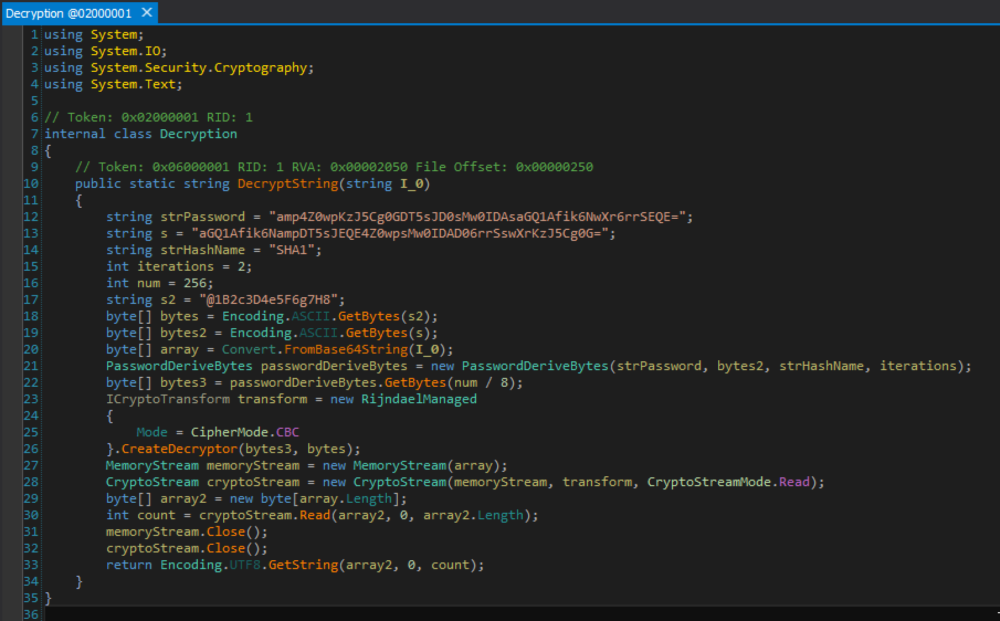
Below is a screenshot of the function used to decrypt strings throughout the malware. This particular decryption routine is used in almost every function throughout the samples for strings such as Command and Control addresses, HTTP methods, C&C commands, Windows Registry entries, directory names, and more.
Agent Tesla also includes the capability to avoid analysis by sandboxes or within Virtual Machines. For example, the following DLL’s and system artifacts can be checked for to determine if the malware is running inside a sandbox or VM, if specific Anti-Virus software is being used, or the system is otherwise being monitored:
- avghookx.dll
- avghooka.dll
- snxhk.dll
- dbghelp.dll
- api_log.dll
- dir_watch.dll
- pstorec.dll
- vmcheck.dll
- wpespy.dll
- Sf2.dll
- cmdvrt32.dll
- SxIn.dll
- VirtualBox
- vbox
- vmware
Many of the DLL’s listed come directly from the Al-Khaser application which is meant to test malware analysis environments to ensure the sandbox environment is well disguised from commonly looked for virtualization or analysis tools that legitimate malware often checks for.
Another notable attribute of the analyzed samples was the shared PDB of “C:UsersAdminDesktopIELibraryIELibraryobjDebugIELibrary.pdb”. This PDB was found across all samples, and upon some minor OSINT, it was discovered this same PDB is in many malicious files in the wild that all contact similar Command & Control URLs.
Functionality Agent Tesla has many malicious features common to most malware, including:
- Recording keystrokes
- Copying clipboard data
- Capture screenshots
- Capture Webcam recordings
- Steal credentials from browsers and other installed applications
Credential theft occurs against the following applications if installed, and send the resulting data back to the C&C server using one HTTP request per stolen credential set:
- Mozilla Firefox
- Google Chrome
- Internet Explorer
- Apple Safari
- Opera
- Torch Browser
- SeaMonkey
- UC Browser
- ComodoDragon
- FileZilla
- FTPCommander
- WinSCP
- SmartFTP
- WS_FTP
- CoreFTP
- Internet Download Manager
- JDownloader
- Microsoft Outlook
- Mozilla Thunderbird
- Opera Mail
- TheBat!
- Fox mail
- Eudora
- PocoMail
- Pidgin
- Paltalk
Web Panel & Open Directory
Recent campaigns of Agent Tesla appear to be using the C&C URL of /WebPortal/api.php and this case is no different. In the open directory, we found this same file and several samples discovered in the wild were reporting back to the same URL at their own Command & Control servers.
The analyzed payloads can also communicate with a C&C server over SMTP, instead of HTTP, but this was not used in any of the samples. Remnants of the email messages that would have been crafted can be seen in names such as “set_Subject”, “set_Body”, and “SmtpClient”. Other unused functions include the ability to collect system information such as processor information, total memory, and total free disk space.
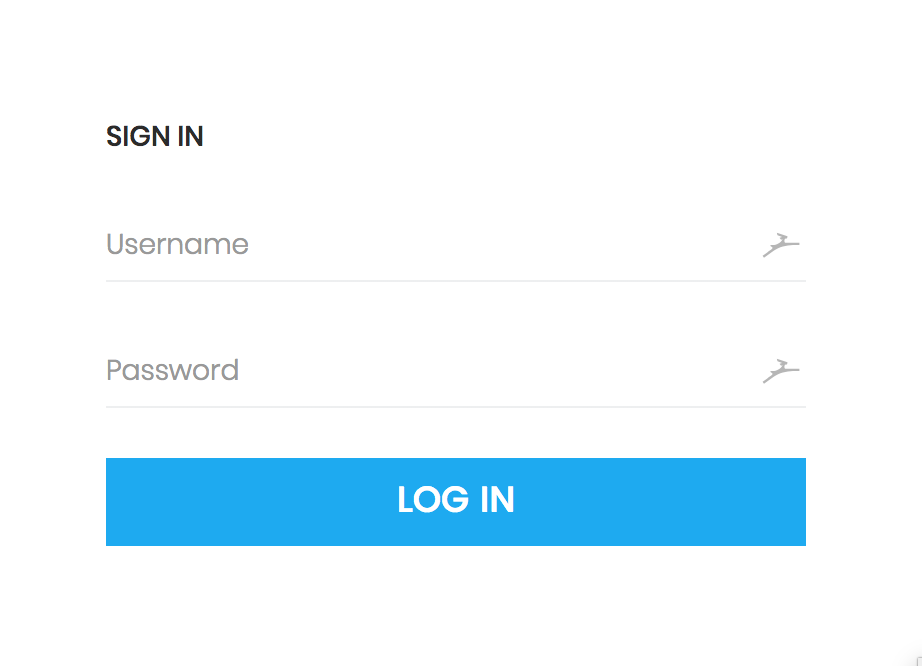
The screenshot below shows what the login page of the administration web panel looks like:
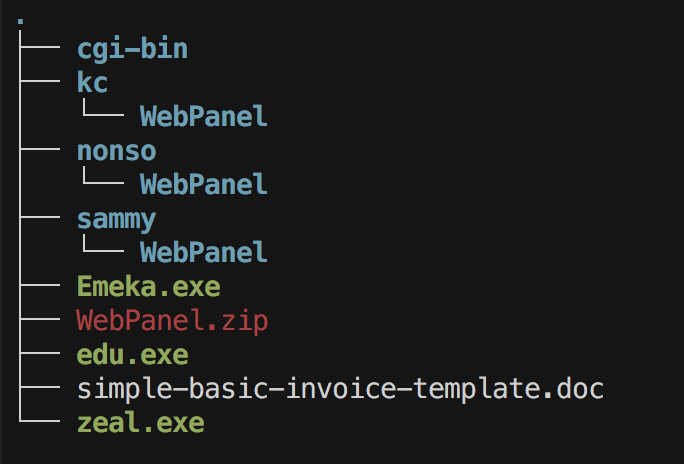
Open Directory Once we discovered the open web directory, we immediately crawled the site to pull down the contents for examination. The screenshot below provides a high-level view of the directory structure and shows the numerous other Web Panels hosted on the same C&C server.
By taking a look at the source code of the Web Panel, we can see it is PHP as are most malware web panels and is encoded using the popular IonCube encoding method. While we won’t be de-obfuscating this here, even having a quick look at the pages available to the malware administrators is useful to get a glimpse into what they see when controlling infected hosts. Below is the screenshot showing the first level extracted contents of WebPanel.zip and the files within the “pages” directory, which sheds some light on the functionality available to an administrator of this malware.
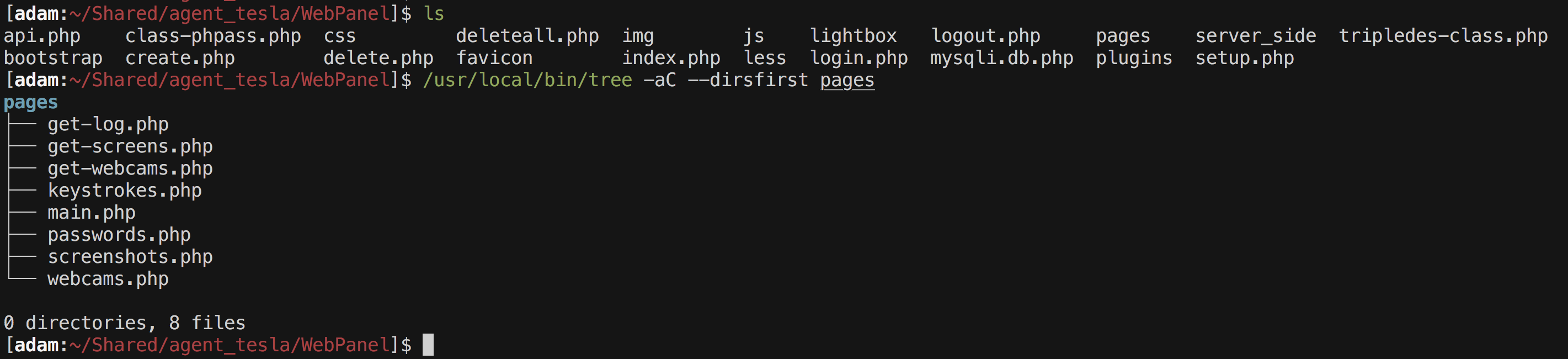
From here we can see there is the central panel from which they can capture and view screenshots, web camera video, view victim keystrokes, and view collected passwords.
File Artifacts The following information details the executable files and zipped web panel found within the open directory we discovered. Each executable is it’s own Agent Tesla payload, while WebPanel.zip contains the PHP and HTML that compromises the administrative panel for the malware itself.
- File:
Emeka.exe - Size:
481280 - MD5:
059bb09924b0d8cb7a8cffb72fd0bb03 - SHA1:
87a02be494bc914211d91a45a9ccbf4d47238566 - SHA256:
0abb52b3e0c08d5e3713747746b019692a05c5ab8783fd99b1300f11ea59b1c9
- File:
edu.exe - Size:
479744 - MD5:
32b2668174be406d98bde8c055e809d6 - SHA1:
62470fb3bec370be380172d6162674dda8d70f17 - SHA256:
cdae984bddb747f11d7d3a8708fd7e3bcaa4c295d3441899a33b4ae9f6db5aba
- File:
zeal.exe - Size:
480256 - MD5:
732ad6e95c86b3be894fe6ffa27eb683 - SHA1:
e126335f8c59c50dffa83ba5a42f9aff76c1752a - SHA256:
e10a98e2aa34d0ed7f5cf78717efdc809d3084bd7ca29f3a5905a3c1a22ae118
- File:
WebPanel.zip - Size:
16249161 - MD5:
5d67a46d1b82e723390f1a53473bb14c - SHA1:
0824db44e395c377716232669f25aba95289b8d9 - SHA256:
7f131248a23e3a8ee00753941f31479f72bb6284f01fb572459654306c6c26fd
These samples have been made available to the public on our GitHub repository malware-samples.
Detections, Mitigations, and Remediations
Agent Tesla may seem like common malware, but with its recent campaigns, it may be a formidable malware family that defenders need to begin to pay attention to more closely.
The likely vectors of infection for this malware include the common vectors such as through phishing email lures, malicious documents, and potentially Exploit Kit delivery.
Indicators of Compromise
C&C Servers
hxxp://78.128.76.165/~t1onishl/kc/WebPanel/api.phphxxp://78.128.76.165/~t1onishl/nonso/WebPanel/api.phphxxp://78.128.76.165/~t1onishl/sammy/WebPanel/api.phphxxp://firstshipone.com/WebPanel/api.phphxxp://31.220.40.22/~idoyrddf/mavlad/WebPanel/api.phphxxp://31.220.40.22/~akatisgc/chibu/WebPanel/api.phphxxp://www.apexlogisticscompany.com/uber/WebPanel/api.phphxxp://37.72.171.98/WebPanel/api.phphxxp://varsolar.com/wp-content/upgrade/WebPanel/api.php
The above list is a non-exhaustive list of C&C servers for Agent Tesla, although a useful resource for keeping track of new instances is the CyberCrime-Tracker. That URL provides a search specifically for these types of Command and Control servers, and the website itself is generally highly reliable in its data.
Payload MD5 Hashes
059bb09924b0d8cb7a8cffb72fd0bb0332b2668174be406d98bde8c055e809d6732ad6e95c86b3be894fe6ffa27eb683
YARA Signature InQuest would like to provide the following YARA rule as a detection measure for Agent Tesla. This rule is based on the samples analyzed above and may not be indicative of every variant, but it has been yielding several results during our hunting process. Hopefully, this helps the defenders out there get a step ahead and take action if this YARA signature triggers in their environment.
We recommend deploying this rule in a way that it scans network traffic as well as on disk, that way it may be possible to detect the malware in-transit as opposed to after an asset is already infected. This YARA rule can also be found in our GitHub repository of open sourced rules located at https://github.com/InQuest/yara-rules.
rule InQuestLabs_AgentTesla
{
meta:
author = "InQuest Labs"
source = "https://www.inquest.net"
created = "05/18/2018"
TLP = "WHITE"
strings:
$s0 = "SecretId1" ascii
$s1 = "#GUID" ascii
$s2 = "#Strings" ascii
$s3 = "#Blob" ascii
$s4 = "get_URL" ascii
$s5 = "set_URL" ascii
$s6 = "DecryptIePassword" ascii
$s8 = "GetURLHashString" ascii
$s9 = "DoesURLMatchWithHash" ascii
$f0 = "GetSavedPasswords" ascii
$f1 = "IESecretHeader" ascii
$f2 = "RecoveredBrowserAccount" ascii
$f4 = "PasswordDerivedBytes" ascii
$f5 = "get_ASCII" ascii
$f6 = "get_ComputerName" ascii
$f7 = "get_WebServices" ascii
$f8 = "get_UserName" ascii
$f9 = "get_OSFullName" ascii
$f10 = "ComputerInfo" ascii
$f11 = "set_Sendwebcam" ascii
$f12 = "get_Clipboard" ascii
$f13 = "get_TotalFreeSpace" ascii
$f14 = "get_IsAttached" ascii
$x0 = "IELibrary.dll" ascii wide
$x1 = "webpanel" ascii wide nocase
$x2 = "smtp" ascii wide nocase
$v5 = "vmware" ascii wide nocase
$v6 = "VirtualBox" ascii wide nocase
$v7 = "vbox" ascii wide nocase
$v9 = "avghookx.dll" ascii wide nocase
$pdb = "IELibrary.pdb" ascii
condition:
(
(
5 of ($s*) or
7 of ($f*)
) and
all of ($x*) and
all of ($v*) and
$pdb
)
}Free Email Hygiene Analysis
Solid email security begins with proper email hygiene. There are a variety of email hygiene technologies and wrapping one’s head around them all is challenging. Try our complimentary Email Hygiene Analysis and receive an instant report about your company’s security posture including a simple rating with iterative guidance, as well as a comparison against the Fortune 500. Try it today!