In the first part of our series on shifting left in cybersecurity, we discussed the importance of balancing detection and prevention measures to achieve a more robust security posture. In this second part, we’ll dive into practical ways your organization can implement the shift left approach to strengthen your defenses against cyber threats.
Practical ways to shift left in your organization
Companies can take many steps today to evolve their capability to shift left. To name a few:
- Reduce the risk of exposures in deployed software by addressing known exploited vulnerabilities (KEV).
- CISA publishes the Known Exploited Vulnerabilities Catalog (KEV), a compendium of software vulnerabilities known to be targeted and exploited in threat actor playbooks.
- “The KEV catalog sends a clear message to all organizations to prioritize remediation efforts on the subset of vulnerabilities that are causing immediate harm based on adversary activity. Organizations should use the KEV catalog as an input to their vulnerability management prioritization framework.”
- Organizations can shift left by focusing vulnerability management efforts toward those vulnerabilities for software in their environment that intersect with intelligence on threat actor exploitation. While many vulnerabilities are documented every year, relatively few of them are utilized in active intrusions.
- Research emerging threats and identify effective attack surface reduction mitigations.
- As new research is published on intrusion activity, analyze the intelligence and document elements that can likely be prevented in your environment by using mitigation strategies at your disposal. Every organization is different, and depending on your maturity, deployed solutions, and expertise, you may have your own unique set of capabilities.
- Identify gaps in controls that would be impactful, but that you can’t achieve today. Set engineering priorities for efforts that can help provide those capabilities in place in the future.
- These same analysis efforts can also fuel other elements of your defensive program, including actor, capability and infrastructure tracking (threat intelligence), identifying elements of successful intrusions that went unnoticed (threat hunting), and uncovering direct indicators that can lead you to mitigate that impact in your environment (incident response).
- Implement effective controls at identifying and blocking threats at inbound gateways and choke points in your environment.
- Despite some industry efforts to suggest otherwise, the perimeter is not completely eroded today and many organizations retain key strategic choke points for monitoring and blocking threats upstream from their users and endpoints. This can even be the case in environments that are heavily adjusted to zero-trust architecture.
- For example, nearly all organizations use email today, with nearly all commonly used email service providers supporting some form of email security features. Leading providers support antispam, anti-phishing and malware filtering for users. Like many controls, gaps may exist and additional opportunities can allow organizations to reach a robust level of threat mitigation. At the very least, inbound delivery infrastructure provides a powerful central point for visibility, policy enforcement and threat mitigation for today’s most common threat vector – electronic mail.
- A simple way to start with mitigation at this layer is to determine an inbound email policy that fits risk tolerance to your organization. Identify business processes that rely on receiving certain attachment types via email. It is worth noting that many data transfer systems today work outside of email, using SFTP or APIs or block storage like Amazon S3 to transfer business data, so these data transfer systems may not be tied to email at all. From here, you may opt to policy block any email that attempts to deliver high risk file attachments. For example, most organizations shouldn’t expect legitimate email message deliveries for the following file types: .7z, .exe, .gz, .hta, .img, .iso, .js, .jse, .lnk, .one/.onepkg, .ps1, .rtf, .scr, .vbs, .vbe, .vhd/.vhdx, .wsf. Blocking or quarantining these file types, either as direct attachments or as nested attachments in archive files, can be an effective shift-left tactic. Another high risk file attachment that many organizations can likely block is .htm/.html, frequently abused to carry content such as phishing pages and other content encapsulated using HTML smuggling. Combined with advanced email threat detection technology that integrates with this layer, defenders can inspect messages and attachments and block files that show signs of having been weaponized by attackers to deliver malware or phishing threats. When adversaries use files as containers to hide files inside other files, basic policy rules are insufficient. Email content filtering must be able to see inside of attached and downloaded files, extracting inner layers and analyzing the nested file content. This approach exploits a weakness in attacker tradecraft; outer layers are armored, while inner layers typically contain the real payloads and trust that outer layers to provide protection.
- Take away attackers’ ability to use benign infrastructure against you.
- An important part of many adversary playbooks is the abuse of otherwise benign network and cloud service infrastructure in stages of the attacks. A completely open internet is an internet that can provide an unlimited number of vectors for attacks. Identifying classes of services that can be evaluated by risk, and restricting access to those portions that are not used by end users can be an effective strategy to reduce attackers’ options during operations.
- For example, online file storage and transfer/sharing services are one place to consider impact. There are a large number of these services available, and except for those that may be used for business purposes by your organization, most will not be accessed legitimately by your user base. Businesses should ensure that services they rely on remain accessible, but for the remainder of these types of sites, any access to them by users stand a good chance of being related to intrusion activity. Proactively blocking access to these sites at the DNS, firewall, or cloud proxy level can provide proactive protection.
- Examples of documented attacks featuring these types of services include transfer.sh, OpenDrive, and AnonFiles.
- Utilize available attack surface reduction (ASR) capabilities in deployed software.
- The typical endpoint and user productivity environment often consists of the operating system and applications, most often commodity software that must by default work in all cases for a varied population of users. In the default configuration, this software may be easily exploited as attackers identify ways to misuse features, abuse functionality, and exploit software weaknesses to run code.
- ASR rules can be used to selectively disable or apply mitigations to the features of some widely deployed software, applying hardening by limiting the ability of attackers to abuse or exploit software features. ASR and related rules are a feature in some endpoint detection and response (EDR) software. For example, Microsoft Defender for Enterprise (MDE) provides a rule to “Block all Office applications from creating child processes.”
- Configurations at the operating system level can be employed to limit misuse of built-in features. For example:
- Rely on Microsoft mitigations to block opening embedded file types in OneNote to prohibit attacks using malicious embedded files.
- Prohibit mounting disk image containers in Windows.
Getting ahead of threats with InQuest
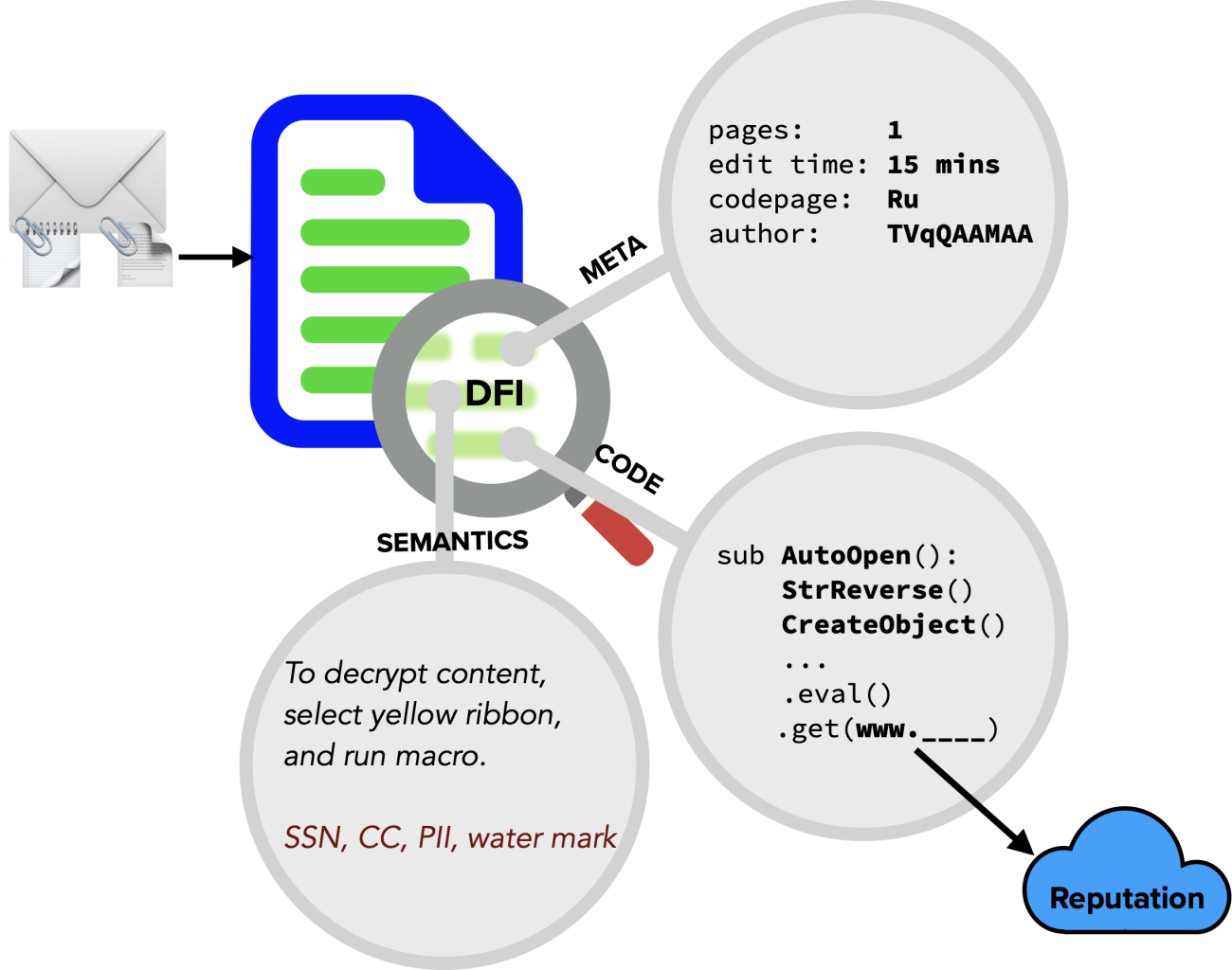
At InQuest, our Deep File Inspection (DFI) technology supports the “shift left” methodology by thwarting malicious content from reaching end users. DFI goes above and beyond in stopping file-borne breaches and incidents, as well as dramatically improving threat hunting for attacks that have circumvented defenses. The DFI process is so thorough in its analysis, it typically results in 4X the amount of analyzable content relative to original file size. DFI also provides substantial benefit by reducing cybersecurity capital spend, reducing operating costs, and driving up the efficacy and value of adjacent security solutions.
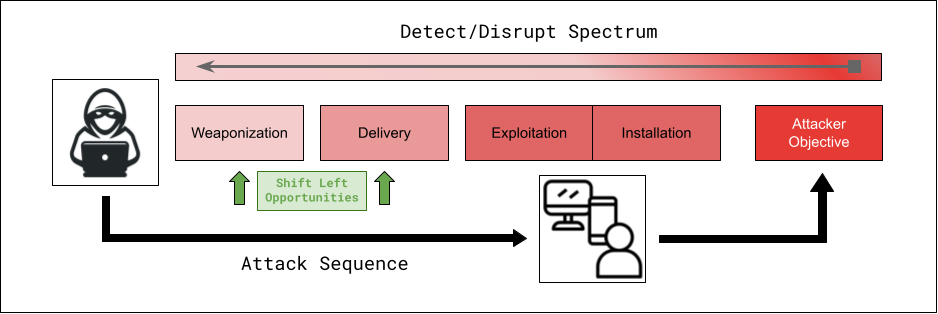
Our mission is to enable organizations to shift left in the sense that we enable them to detect malicious content earlier on in the threat sequence, addressing many threats prior to them gaining a foothold in the environment and requiring costly post-exploit detection, analysis, hunting and response cycles to address them. “Shift left” is a term that leading organizations embrace and is effective when scoped properly in terms of prevention. While we know we can’t prevent all threats, every organization can take opportunities to reduce risk by implementing controls that reduce threat actor options for various phases in the kill chain.
By implementing these practical steps to shift left in cybersecurity, organizations can proactively protect their environments and minimize the resources required to address cyber threats. Balancing detection and prevention measures is key to maintaining a strong security posture in the face of an ever-evolving threat landscape.
References
- https://www.cisa.gov/known-exploited-vulnerabilities
- https://www.cisa.gov/known-exploited-vulnerabilities-catalog
- https://labs.inquest.net/trystero
- https://www.dshield.org/diary/Malware+Delivered+Through+Free+Sharing+Tool/28474
- https://www.microsoft.com/en-us/security/blog/2022/12/06/dev-0139-launches-targeted-attacks-against-the-cryptocurrency-industry/
- https://blogs.blackberry.com/en/2022/11/arcrypter-ransomware-expands-its-operations-from-latin-america-to-the-world
- https://learn.microsoft.com/en-us/deployoffice/security/onenote-extension-block
- https://inquest.net/blog/2023/02/27/youve-got-malware-rise-threat-actors-using-microsoft-onenote-malicious-campaigns
- https://malicious.link/post/2022/blocking-iso-mounting/
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge for 30 days.

