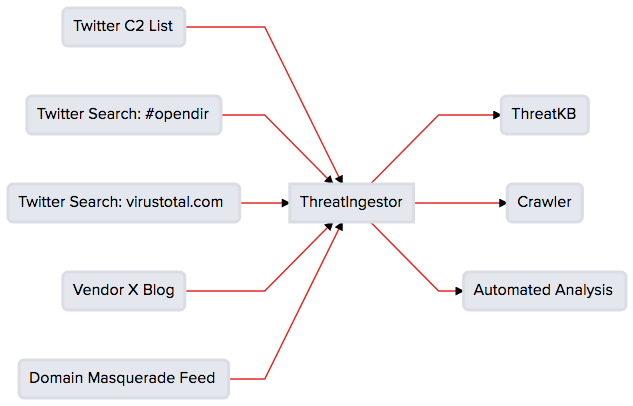
ThreatIngestor is a flexible, configuration-driven, extensible framework for consuming threat intelligence. It can monitor Twitter, RSS feeds, and other sources, extract meaningful information like C2 IPs/domains and YARA signatures, then send that information to other systems for analysis. Use ThreatIngestor alongside ThreatKB or MISP to automate importing public C2s and YARA signatures, or integrate it into your existing workflow with custom operator plugins.
You can download the latest release (v1.0.2) or read further documentation at:
- https://github.com/InQuest/ThreatIngestor/releases/tag/v1.0.2
- https://pypi.org/project/threatingestor/1.0.2/
- https://inquest.readthedocs.io/projects/threatingestor/en/latest/
In recent history we have addressed multiple bug reports, added a new ingestion source for Github.com Gists (Github repos were already supported), and implemented some major feature requests.
XML Sitemap Based Ingestion
This new ingestion method feeds on a website’s XML sitemap. This allows you to scan the website’s sitemap and extract blogs that are not available through the typical RSS feed. Which, unfortunately, is a growing trend in our industry. Here’s a sampling of vendors whose blogs have no RSS feed:
- Blackberry
- Center for Internet Security (CIS)
- Elastic
- Flashpoint
- Palo Alto Networks
- ProofPoint
- Recorded Future
- Red Canary
- SecureWorks
- Splunk
- ZScaler
OCR Sourced Indicator Extraction
Our second new ingestion method allows you to extract IOCs from images using computer vision and the Tesseract OCR engine. This feature currently allows for both local and remote extraction, meaning you can collect data from an image on your host system or link to an external image. In upcoming releases we will have support for passing images discovered in blogs, down the OCR IOX extraction pipeline as well.
Users of InQuest Labs IOCDB automatically benefit from these enhancements as ThreatIngestor is a core component of our system!
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge, for 30 days.