Key Takeaways:
- TOAD (Telephone-oriented attack delivery) threat actors are still an active threat in Q4 2022 with no indications of attacks diminishing in the near future.
- InQuest believes that attacks will likely increase in frequency as we enter the shopping season.
- Always contact official customer service numbers listed on a company’s official website instead of contacting the number provided via email.
Overview:
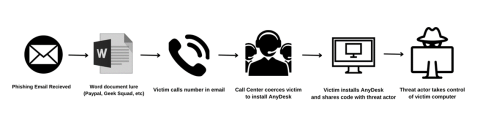
InQuest Labs has observed an uptick in TOAD (Telephone-oriented attack delivery) threat actors targeting personal and business email addresses, presumably in line with the coming holiday shopping season. Based on our research efforts, we have observed that they employ multiple team members to execute this attack. The threat actors refer to these components as “customer support” and “the security team”. The “customer support” team engages with the victim via phone and attempts to convince them that they have been compromised. Then they instruct the victim to install AnyDesk and share the code with him. That code is then passed to the “security team” who connects to AnyDesk, while the “customer support” team instructs the victim to log in to their online banking website. Once the victim does this, several different things may occur, including manipulating the HTML code on the bank webpage to make the account balance appear different. This leads us to believe that this is a call center-based threat with a financial motivation. Their primary objective appears to be direct monetary theft.
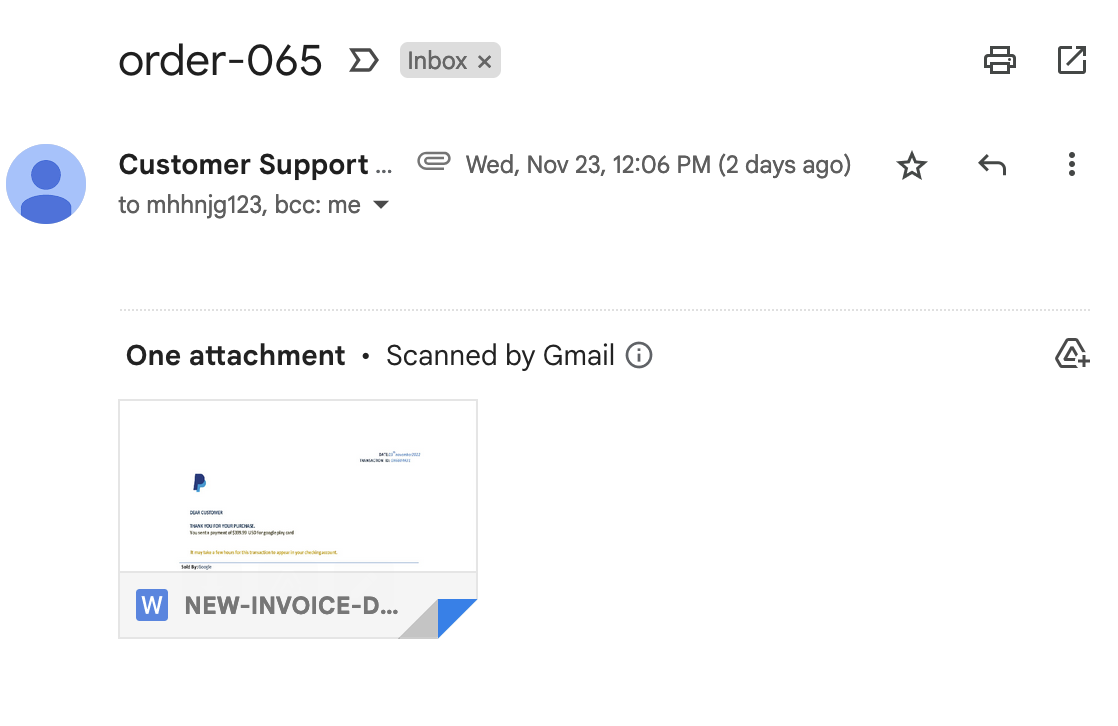
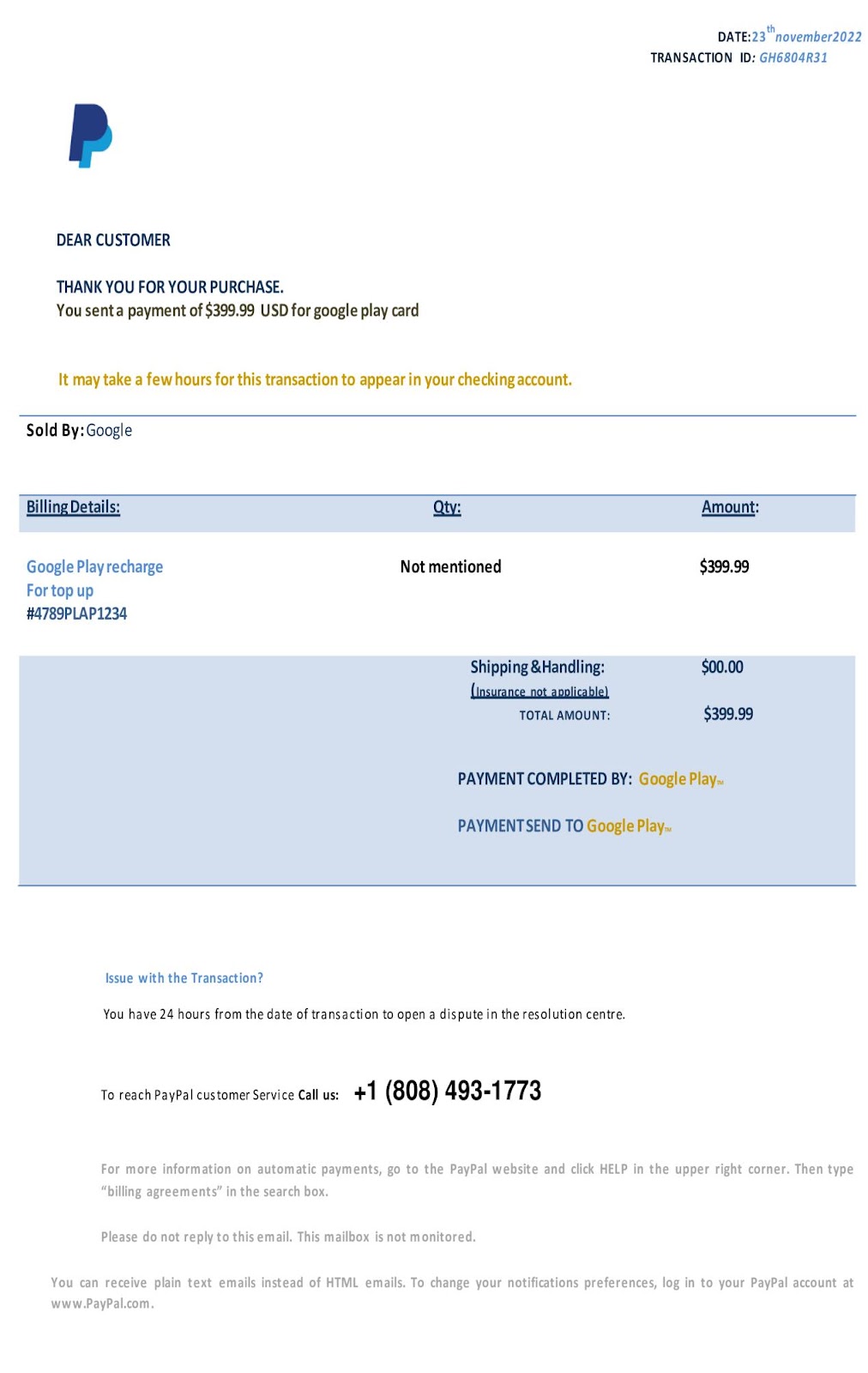
The phishing email arrives using one of the classic subject lines of either “Invoice” or “Order-##” with the lure document attached. Analysis of the document reveals that it does not contain any macros nor does it contain much text at all. It’s primarily an image embedded in the document. OCR (Optical Character Recognition) in InQuest Labs was able to parse out the text in the image, including the unique 12-14 character transaction ID in each attachment. We believe this transaction ID may be used for a sort of metrics system used by the threat actor for campaign tracking.
Telephone Operations:
Upon contacting the telephone number provided in the document, the victim is greeted by an individual with a South Asian accent, who poses as customer service. The “customer service” impersonator seems to be following a script as they inquire if the victim visited malicious websites or used unsecured WiFi. They then ask the customer to confirm the transaction ID and to verify the amount charged. Once the victim does this, the “customer service” individual states that they are talking to “PayPal Security” and asks the victim to hold. Once the threat actor returns to the line, they begin reading a script again to have the victim open up Internet Explorer utilizing the Run console in Windows. They then have the victim go to AnyDesk and install the agent on their machine. Once AnyDesk is installed, the threat actor asks for the code to connect to the victims machine and instructs the victim to click “allow” as the prompts appear. Once the “security team” has successfully connected, the victim is instructed to sign in to their online banking website. After the victim has successfully done that, the threat actor blacks out the screen and manipulates the client side HTML so that the balance appears incorrect after “PayPal” allegedly refunds the transaction for far greater than what was on the receipt. The victim is then instructed to withdraw the money and send it back via gift card or other unusual means.
On The Horizon:
These attacks will likely increase in frequency as we enter the holiday season. With that in mind, here are some tips to stay safe:
- Always contact the official customer service number for any vendor you may have a financial dispute with. Never use the number provided in an attachment or the body of an email.
- For defenders: Block AnyDesk, TeamViewer, and other remote administration tools from running on devices in your organization. You could also go a step further by blocking anydesk[.]com or teamviewer[.]com on your organization’s DNS server. Log attempts to download this software or execute the installer would also be useful. You can also upload suspicious attachments to https://labs.inquest.net/ for analysis.
- Report unexpected invoices and/or other financial-themed emails to your organization’s security team.
IOCs:
2c3cc41fe56e41d1e7302266dca6b59fc5846146dbf0e4b945137c5db4d37e9d
d04636fed3e0301e0e0714729045659bd4044f63d80dab9899b06d2e4d63bd3c
Free On-Demand Webinar: Think Before You Click
Whether sent as an email attachment, sitting in your cloud or traversing the Web, file-borne threats have become a proven favorite for delivering malware and phishing campaigns. View our webinar on-demand and get firsthand tips about how to safeguard your cybersecurity stack with File Detection and Response (FDR) and stop file-borne threats in their tracks.
