CVE-2021-40444
Microsoft MSHTML Remote Code Execution Vulnerability

As we roll into autumn and the season changes, so does the threat landscape. The emergence of new CVE signals another arms race with both sides vying for effectively leveraging the exploit and understanding how to mitigate the effects respectively. As with all Common Vulnerabilities and Exposures, comes questions such as “How does this affect me or my organization?” and “What can I do to mitigate this?” The focus of this blog is to explore these concerns as well as provide further context surrounding CVE-2021-40444 and the initial maldoc delivery.
On September 2, 2021, in our Lab, we found several documents with low levels of detection. This was around the time @ShadowChasing1 published the hash of another file, as well as an indicator of infection. Specifically, a “legal document” containing a street address. Upon opening, the file is able to establish connections to download additional components.
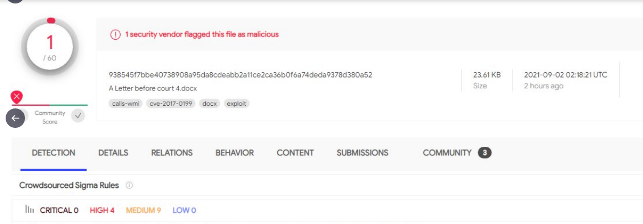


Because infection indicators marked these samples as malicious, our clients were protected from intrusion attempts using these files. We also published other hash sums and indicators on the same day.
As we began to investigate further, we did not suspect that we had stumbled upon a serious critical vulnerability announced by Microsoft on September 7th. In this blog, we have compiled information that can help security engineers mitigate the potentially devastating effect of this vulnerability being exploited on targeted systems.
This in-the-wild 0day exploit targets a vulnerability in Microsoft MSHTML and can be reached via a malicious Microsoft Office document. The end result is Remote Code Execution on the infected host. The vulnerability was assigned CVE-2021-40444 and for those curious to see some real-world samples, they can be found here on InQuest Labs:
If you’re looking for real-world samples that exploit the Microsoft MSHTML Remote Code Execution Vulnerability (CVE-2021-40444), check out the files listed here:https://t.co/dCLZIHhGgVhttps://t.co/XjWWwxV0zY
— InQuest (@InQuest) September 9, 2021
In both of these cases we are “pivoting” on two of the multiple domains observed as part of this campaign. We highly recommend folks implement the registry based mitigations (available below in the Mitigations section) for this vulnerability as it is bound to be the exploit of choice for malicious actors for months if not years to come. Possibly dethroning the old favorite CVE-2017-11882, a vulnerability in Microsoft Equation Editor which is again accessible by way of document and email-borne malware lures.
What follows is a timeline of notable tweets providing insight into CVE-2021-40444 as it unfolded: Twitter Collection
Detection
In this section we have included a few different methods of detection for spotting instances of this exploit. While the “meat” of this exploit relies on abusing ActiveX controls, our initial discovery found documents attempting to leverage a feature within Internet Explorer known as MIME Encapsulation of Aggregate HTML documents; or simply MHTML.
Some information about this feature: https://insert-script.blogspot.com/2016/02/mhtml-x-usc-feature-from-past.html
As with most common email-borne malware, a malicious document is included containing functions to download the next step within the attack chain. In this case, we are looking for documents containing URLs structured as such:
mhtml:http://somedoma.in/some/uri/pattern!x-usc:mhtml:http://badguydoma.in/next/stage/malware/files
While this feature has been around for quite some time, utilizing it for malware delivery and security evasion is something of a new beast. Over the course of a few days, malware authors and researchers alike have experimented with different ways to include download URLs while tossing out “mhtml:” and/or “!x-usc:” to see what still sticks.
While these proved instrumental to uncovering the vulnerability initially, as mentioned earlier, threat actors as well as fellow researchers are quickly discovering valid ways of achieving execution of this exploit by obfuscating or even omitting some of these detection methods. We have confirmed that the “mhtml” and “x-utc” strings can be omitted, making static detection alone to be impossible. Observing URI patterns, dropped payloads and obfuscation methods in future samples will lead to threat actor attribution as different groups tailor this tactic to fit their campaigns. Pivoting on the observed threat actor domains mentioned earlier, we noticed samples dating back to mid last month; indicating a connection to ongoing campaigns. One sample sharing the same document lure as variant 2 seen previously, but first seen on VirusTotal on the 19th of August, was caught by our detection signatures and marked malicious that same day.
Mitigation
While efforts are ongoing, there is a growing need for numerous patches to successfully remedy this issue, by our predictions. Because ActiveX controls are abused to achieve RCE, disabling installation of new ActiveX controls within Internet Explorer will not expose this vulnerability while allowing previously installed controls to continue to run.
The details concerning this CVE as shared by Microsoft are as follows:
- The Microsoft patch will be available for “Patch Tuesday”, September 14.
- Microsoft Bulletin: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-40444
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3]
"1001"=dword:00000003
"1004"=dword:00000003
As remote code execution is the end result of this exploit, any currently prolific threat may be distributed in this manner. We expect to see several of the usual suspects as Cobalt Strike payloads have been one of the first observed in recent samples.
09/14 Update:
With the latest Windows patch KB5005565, released out-of-band after the expected Tuesday patch, known methods of abuse for this vulnerability appear to be resolved. As expected of threat actors, continued efforts to work around the patch and achieve RCE will be their next goal while taking advantage of the time between rollout and patching affected systems.
Special thanks to @BouncyHat and @Ledtech3 for their major contributions to this topic.
We would also like to thank all who were involved within our InQuest Labs community along with the security community as a whole for the combined effort towards combating this new threat.
Indicators:
Documents: (Sample set)
- 3bddb2e1a85a9e06b9f9021ad301fdcde33e197225ae1676b8c6d0b416193ecf (August sample)
- 938545f7bbe40738908a95da8cdeabb2a11ce2ca36b0f6a74deda9378d380a52
- 199b9e9a7533431731fbb08ff19d437de1de6533f3ebbffc1e13eeffaa4fd455
- 0f44ee1436a84364a86e610b834543022f2dd56a936790518426e102f77c1a8d
- 5b85dbe49b8bc1e65e01414a0508329dc41dc13c92c08a4f14c71e3044b06185
- a5f55361eff96ff070818640d417d2c822f9ae1cdd7e8fa0db943f37f6494db9
- d0e1f97dbe2d0af9342e64d460527b088d85f96d38b1d1d4aa610c0987dca745
- 1a8ea3cc10315c8f640d6d6b0a1a402c5e8aa23cf51d4ffe72d5bef1b0cb13bb (Test Doc)
Domains:
- dodefoh[.]com
- hidusi[.]com
- joxinu[.]com
- macuwuf[.]com
- pawevi[.]com
HTML (with Obfuscated JS) :
- d0fd7acc38b3105facd6995344242f28e45f5384c0fdf2ec93ea24bfbc1dc9e6
Malware:
Cobalt Strike
- 3834f6a04b0a9cca41653967e46934932089adaa4de23ff5cfeecdd0e9258e72
- 6eedf45cb91f6762de4e35e36bcb03e5ad60ce9ac5a08caeb7eda035cd74762b
- bd4b9f4b79f8a9eedc12abe3919cecb041c61022485b87b3a5cdfd1891e30670
- cb091dbfd10645ba4ebf06d272e98cd98a2359bc0a0e115bf1ae6ad0073461e0
OSINT
The following information has been found to be helpful and will continue to be updated as this threat evolves. #CVE202140444
- https://twitter.com/InQuest/status/1437465946612973572
- https://twitter.com/ShadowChasing1/status/1433252128106029061
- https://bazaar.abuse.ch/browse/tag/CVE-2021-40444/
- https://twitter.com/search?q=CVE-2021-40444
- https://pastebin.com/jpu4QF9i
- https://insert-script.blogspot.com/2016/02/mhtml-x-usc-feature-from-past.html
- https://twitter.com/buffaloverflow/status/1435607956205326336
- https://twitter.com/jq0904/status/1436155700212744211?s=21
- https://twitter.com/decalage2/status/1436085507663056898?s=21
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge for 30 days.
