Mobile devices as an espionage tool.
With Black Hat and DEFCON around the corner, many folks who plan on attending in person have concerns about mobile security. Some folks will leverage ‘burner phones’, a temporary device they intend to use throughout the duration of the conference, before discarding it completely. Others will reduce their attack surface by disabling WiFi and Bluetooth connectivity. The careless may take no measure at all and perhaps find themselves on The Wall of Sheep. Given the latest headlines around NSO’s Pegasus malware, we thought to take a moment to write about the subject matter.
On March 7th, 1876, an outstanding American scientist/inventor Alexander Bell received a patent for the invention of the telephone. Apart from him, many other engineers also worked on the idea of voice transmission at a distance. In more recent years, society has graduated to the usage of “smart” phones, with adoption quickly approaching the point of ubiquity. Globally, 6.3B out of 7.8B people (~80%) leverage smartphones as part of their daily lives. Arguably, your smartphone is the home to your most private data. Personal photos, your current and historical geographic location, two-factor authentication tokens, and other sensitive contents have made the mobile device the most attractive target for advanced threat actors and nation-states looking to silence their dissidents.
Any modern mobile device has at least a microphone and speaker, access to the Internet, and a camera with GPS navigation. Some devices also have a front camera for video calls. These facets can all be leveraged by attackers successfully to collect information about the owner and surroundings of the device.
The name “implant” was not coined by security experts, rather, it was given by hackers.
In this blog post, we will look at an example of how implant Pegasus and FlexiSpy works.
TrojanSpy.Android Pegasus (SHA256) ade8bef0ac29fa363fc9afd958af0074478aef650adeb0318517b48bd996d5d5
BackdoorAndroidOS.Kresok (SHA256) 263219f185aa2a847bcb4ca981ec4a7c7eff8ded2d3b49d6fb2b4a578b43af60
Pegasus is an advanced cyber-espionage tool that includes plenty of functionality that allows you to spy on mobile users. Cybersecurity researchers are not aware of many of the vectors that the team uses to identify victims. One of them is sending the user a malicious link that exploits a specific vulnerability to install the implant.
It is not a problem for them to know the victim’s location using the GPS locator function. The attackers get access to the phonebook and also to the files stored on the victim’s device. They can read SMS messages and view the call history.
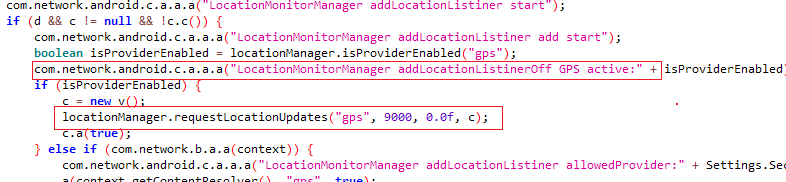
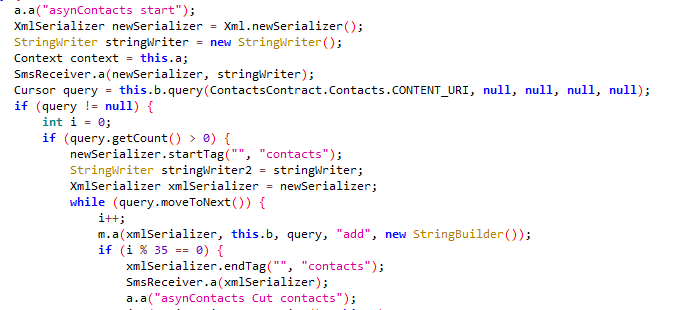
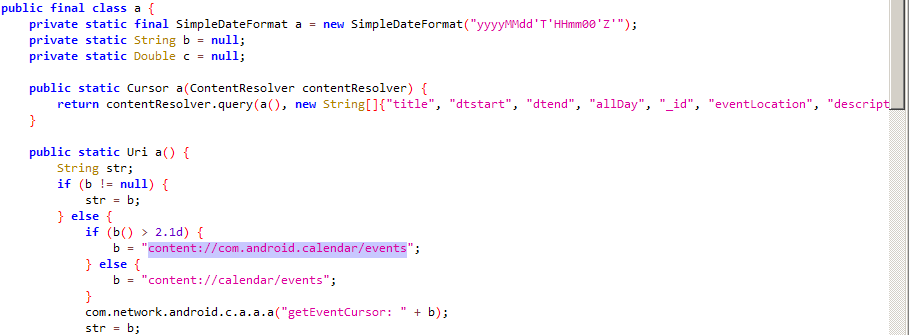
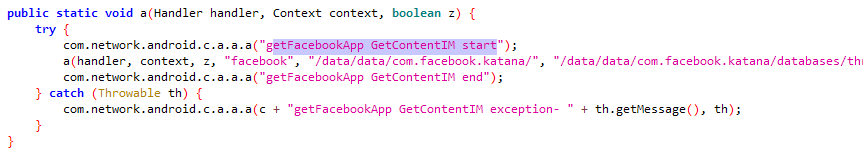
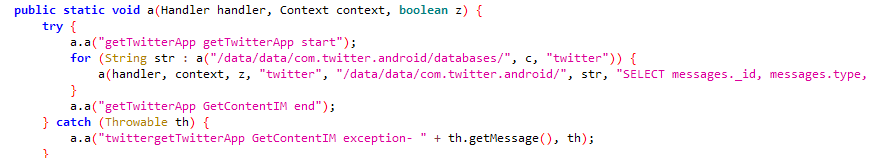
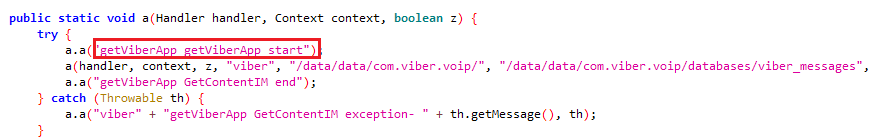
Mobile implants have the ability to steal data from many instant messengers.
Let’s look at an example Android implement known as FlexiSpy:
BackdoorAndroidOS.Kresok (MD5 39be87178c84d4afd07a80323a1d4b91)
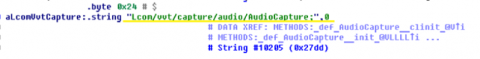
Simple string examination of the payload exposes some of its functionality. For example, the following screen excerpt reveals the ability to remotely activate the microphone for recording and exfiltration of audio data:
Encryption and mobile implants
Not so long ago, in mobile messengers, the use of point-to-point encryption began. Such a cryptographic protocol provides for encryption of messages on the sender’s device and decryption of messages on the recipient’s device. This protocol is a fairly reliable solution for the transmission of information. Was the “point to point” encryption method a solution of all problems of confidence? Unfortunately no, attackers gain access to the messages before they are encrypted and sent.
The screenshots below show examples of how hackers gained access to some popular messengers.
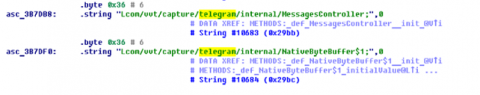
The screenshot shows how the implant tries to access the messages in Telegram.
The following screenshot shows how the implant accesses messages in WeChat.

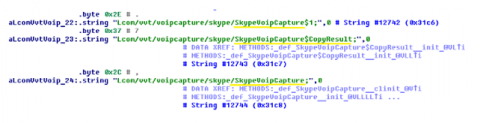
Voice communication through messengers has long become very popular. Attackers are interested in the victim’s talks through popular means of communication such as Line and Skype. Below is a short code in which there is a trespass interception of the VoIP calls.
The screenshot shows the code that provides access to calls via Skype.
The Line Messenger is very popular. The Implant intercepts calls made through it.
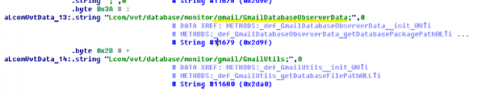
E-mail is also interesting for attackers. The screenshot shows the code that receives the data of the client Gmail.
In fact, it is not important what messenger you use. But rather, how much the attacker is interested in you.
Hardening recommendations.
Several tips that will help you avoid infection with mobile implants.
- Install adequate antivirus software.
- Do not charge the electronic device from the computer.
- Do not connect to an open network unknown to you.
- If you often maintain confidential correspondence, use only messengers that do not save the message archive or metadata and also uses point-to-point encryption.
- If possible, try to use different messengers to communicate.
How Effective Is Your Email Security Stack?
Did you know, 80% of malware is delivered via email? How well do your defenses stand up to today’s emerging malware? Discover how effectively your email provider’s security performs with our Email Attack Simulation. You’ll receive daily reports on threats that bypassed your defenses as well as recommendations for closing the gap. Free of charge for 30 days.
