Dive Into Cobalt Strike
A few days ago, someone uploaded an interesting OLE file to VirusTotal. It abuses the Kaspersky brand, and it is written in Russian and English language. Unfortunately, the original document uses a coercive lure, and the macros contain logic to download weaponized artifacts. File Type: Microsoft Windows Document MD5 at InQuest Labs: [3272df3f79a0fa8c2ba601c4771b99e4](https://labs.inquest.net/dfi/sha256/0a4315aced819ab564058480ffeeeb059756030d8c056605f2e0c6fc88b8b2f5)

At the time of submission, the document had low consensus on AV detection.
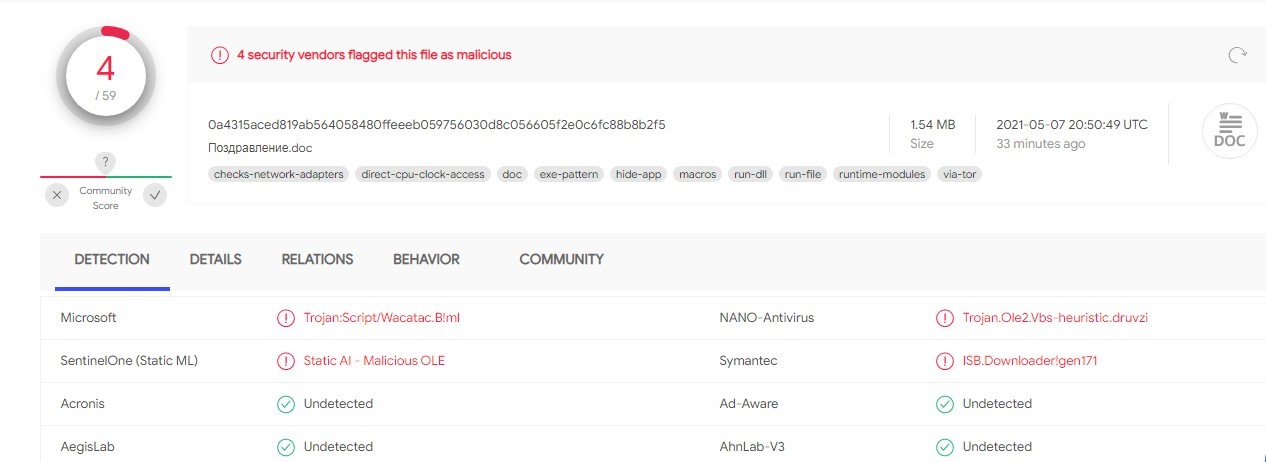
According to VirusTotal, someone using TOR submitted the file on May 7th, 2021. The original file’s name is “Поздравление.doc” Which translated to English means “Congratulations.doc” A quick analysis shows that the document contains macros with functionality to drop new artifacts to the system:
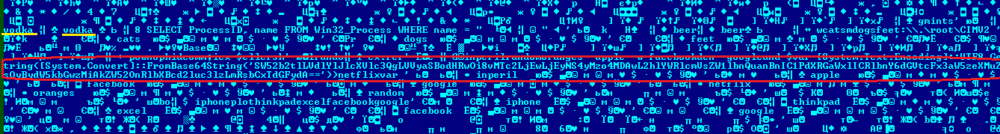
Decoding the URL that was hardcoded in the file results in hxxp://176.10.125[.]23:8000/headerelement[.]jpg According to public Whois data, it’s a server located in Switzerland and belongs to a hosting company. Shortly after the initial attack, the threat actor removed the file 2nd stage malware. However, we were able to get it before they wiped it out from the Internet. The executable file contains a large block of ciphertext. It’s decrypted during execution using the AES-256(CBC) algorithm. The encryption key is also hardcoded in the payload. File Type: PE32+ executable for MS Windows (GUI) Mono/.Net assembly MD5: ACFBDC828CE6D121CDAEE18A29084A5A
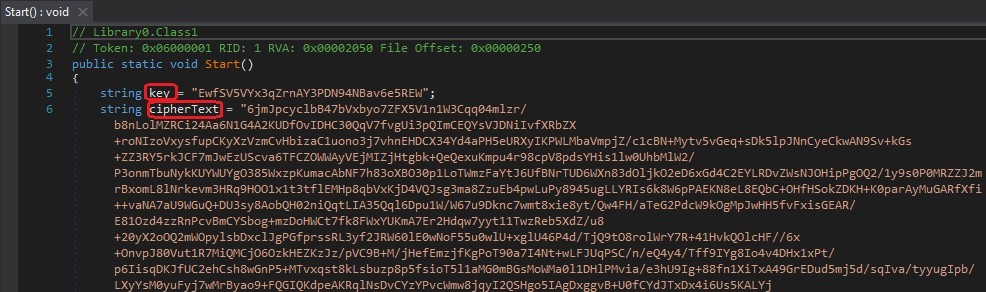
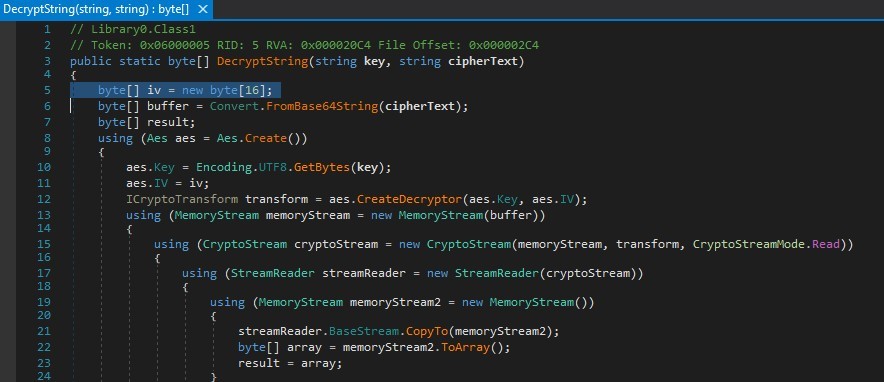
Now with the key on hand, it drops to the system the final payload.
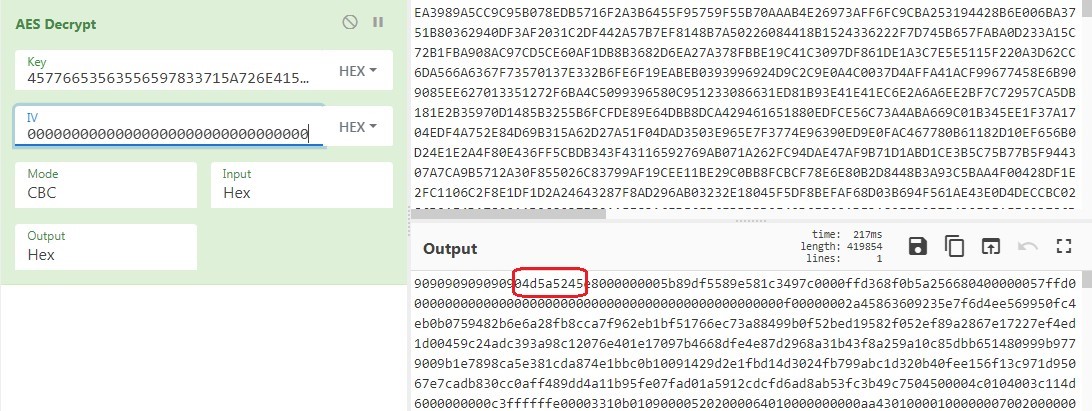
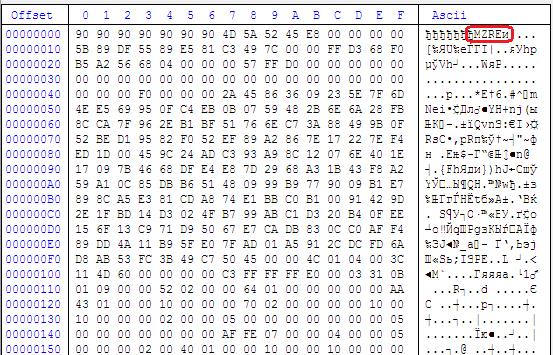
File Type: Portable Executable 32 MD5: 42DE14F600C0C73F10DFAFE2A34BC8FC
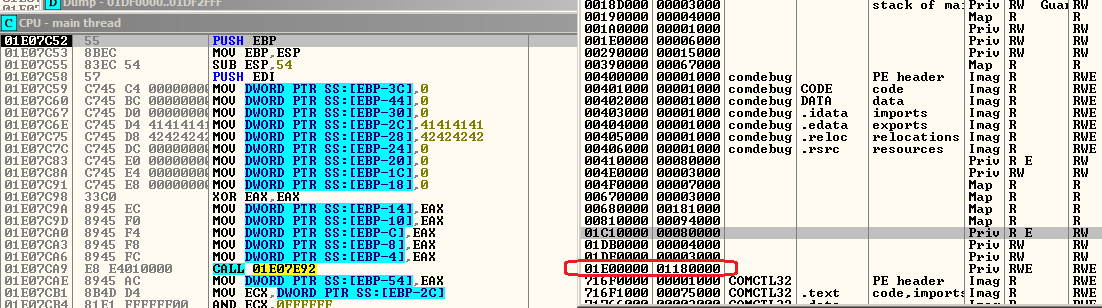
The executable file is obfuscated and the payload is executed exclusively as a decrypted shellcode. Static analysis shows that some of the data is encoded using xor 0x2E. This encoding is indicitive of Cobalt Strike.
{ "BeaconType": [ "HTTP" ], "Port": 80, "SleepTime": 45000, "MaxGetSize": 1864877, "Jitter": 43, "C2Server": "176.10.125.23,/mobile.js", "HttpPostUri": "/staff", "Malleable_C2_Instructions": [ "Remove 737 bytes from the beginning", "Base64 decode", "Base64 decode" ], "SpawnTo": "idYKSm+iuVOAjCzm9Iy8bw==", "HttpGet_Verb": "GET", "HttpPost_Verb": "POST", "HttpPostChunk": 0, "Spawnto_x86": "%windir%\syswow64\svchost.exe -k secsvcs", "Spawnto_x64": "%windir%\sysnative\svchost.exe -k secsvcs", "CryptoScheme": 0, "Proxy_Behavior": "Use IE settings", "Watermark": 1639584573, "bStageCleanup": "True", "bCFGCaution": "False", "KillDate": 0, "bProcInject_StartRWX": "False", "bProcInject_UseRWX": "False", "bProcInject_MinAllocSize": 5517, "ProcInject_PrependAppend_x86": [ "QkpFTUpCQko=", "Empty" ], "ProcInject_PrependAppend_x64": [ "/8D/yP/A/8g=", "Empty" ], "ProcInject_Execute": [ "ntdll.dll:RtlUserThreadStart", "SetThreadContext", "NtQueueApcThread-s", "kernel32.dll:LoadLibraryA", "RtlCreateUserThread" ], "ProcInject_AllocationMethod": "VirtualAllocEx", "bUsesCookies": "True", "HostHeader": "" }
IOCs
42DE14F600C0C73F10DFAFE2A34BC8FC
3272df3f79a0fa8c2ba601c4771b99e4
176.10.125[.]23/mobile.js Conclusion
Targeted attacks using the Cobalt Strike penetration tool are occurring more and more frequently. Analysts need to know precisely how such campaigns are carried out to protect their clients and ensure the information security of their corporate networks.