What we all need now and again is some exciting news, and since we have some, we wanted to make an article to share it! Earlier this month, our friends at Abuse.ch officially announced in a tweet that their MalwareBazaar project has integrated with InQuest’s Deep File Inspection® (DFI) analysis stack. Since this might not seem like much more than an announcement to some, we felt the need to explain why this integration is beneficial to the security community. That being said, we will dive into some further explanation on our system and how this can help the security community.
Open Data Exchange
InQuest utilizes this open exchange by processing all files from the MalwareBazaar platform, performing a file analysis and responding back with our results, which are visible to the public. The analysis we expose to the public is a small taste of our ruleset to explain the outcome of the analysis without giving away too much of our secret sauce. Some may have seen our analysis on MalwareBazaar already and even may have observed a link back to our own analysis platform. InQuest Labs) Looking at one of the latest files on MalwareBazaar, we found an excellent example that will familiarize and clarify the significance of this integration. Here is a recent sample for those not yet familiar with either platform. The image below is from the MalwareBazaar platform and can be visited by clicking this link. The malware document, for those who want to know, is connected to TA551 (aka IcedID).
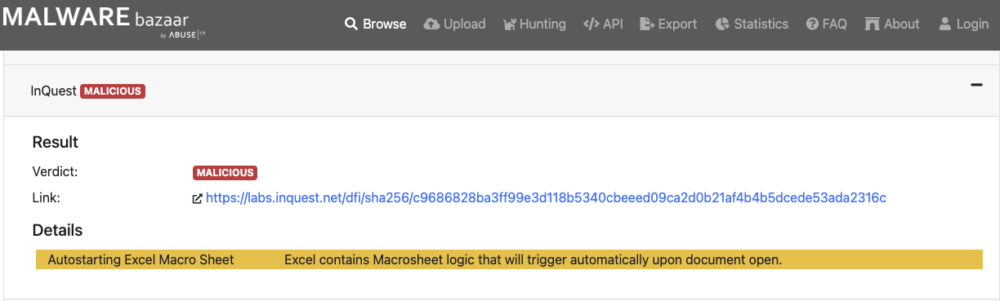
The following image shows our InQuest Labs platform, utilizing InQuest’s Deep File Inspection (DFI) with the same malware document. Click here to view the analysis.
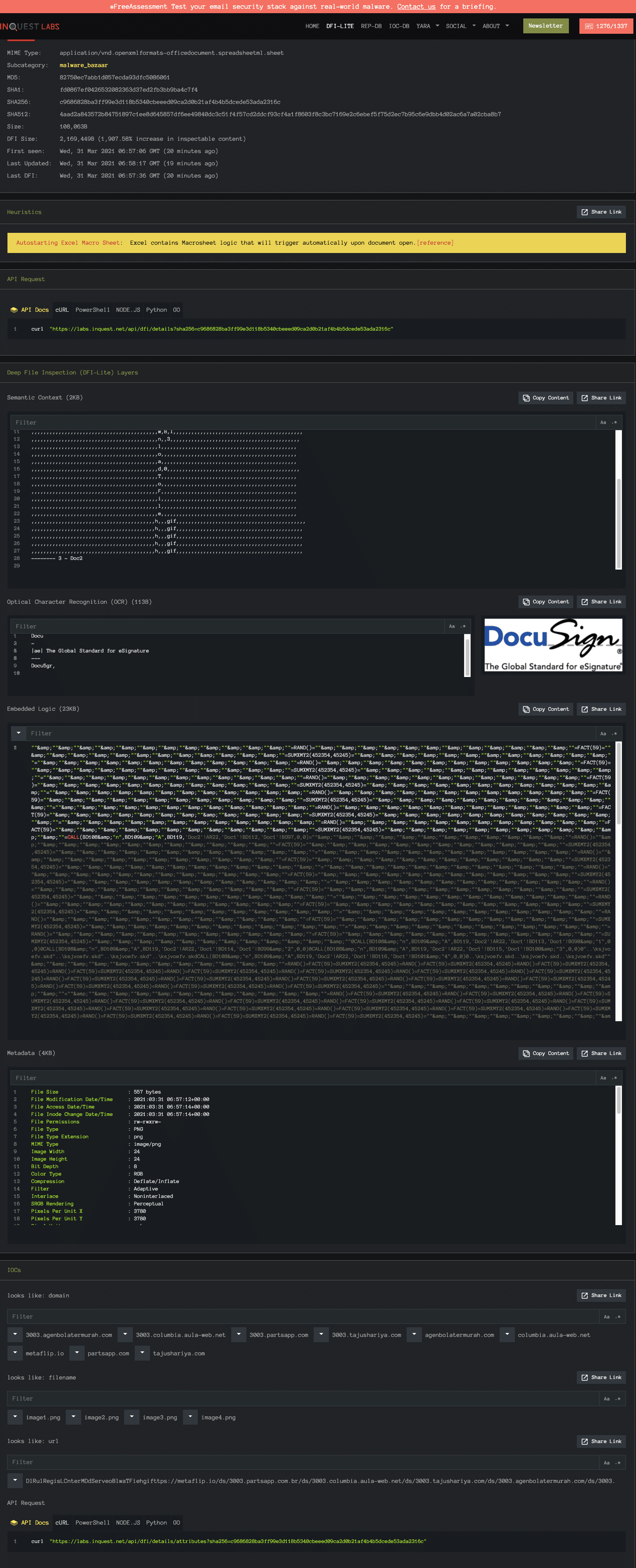
One thing that is important to note is that we specialize in malware document carriers, but we can and do process all file types that come our way. Anything that has gone through our system will go through DFI and if it is a document file type we expose, there will be a link from MalwareBazaar to InQuest along with a note on the InQuest Labs analysis showing the source of the content (which can bee seen in the 2nd image under sub category).
Deep File Inspection® (DFI)
There are many vendors taking part in the MalwareBazaar project, each with their own methods and strengths for detecting malicious content. Some files may be executed in sandbox environments which can be rather slow to execute and output useful data. Other methods include traditional antivirus definitions, which provide quick results but can miss the current day’s prolific malware variants due to lack of definition updates. Next is the use of ML (Machine Learning) models against the files, which are also a great way to detect some known malicious content depending on the model being used. Then finally we come to InQuest’s DFI (Deep File Inspection) analysis stack which is quite different from previously described methods and comes with a unique angle to examining files. DFI is designed to squeeze as much information as possible out of a given file: archives are expanded, text is extracted from documents and images, data streams are carved out, and in general data is exposed that otherwise would be left on the table.
How We Utilize the Data
At InQuest we use the exchange data the same way that anyone else would in a vendor’s shoes. We already know that we focus on different areas than other vendors which is what makes this such a great integration. The ability to be able to bounce around individual files and make detections on them and not just the raw (original) files is that we can find something unique in almost every file we can successfully rip apart. There may be something that we have never seen before and most likely others as previously discussed will have to spend some time to be able to visualize some of the elements exposed with our DFI process. That being said, there are a lot of various methods and obfuscations that are being used and without giving away too much, we can usually always find a way to track the campaigns without having to thrash at making new detections.
Conclusion
Last but not least we would like to thank Abuse.ch for the opportunity to be included in the MalwareBazaar project! If you are curious about DFI and how it works, we have a blog post to further explain DFI functionality. Those seeking further context or access to other outputs, feel free to reach out and we can explore solutions tailored to your specifications.

