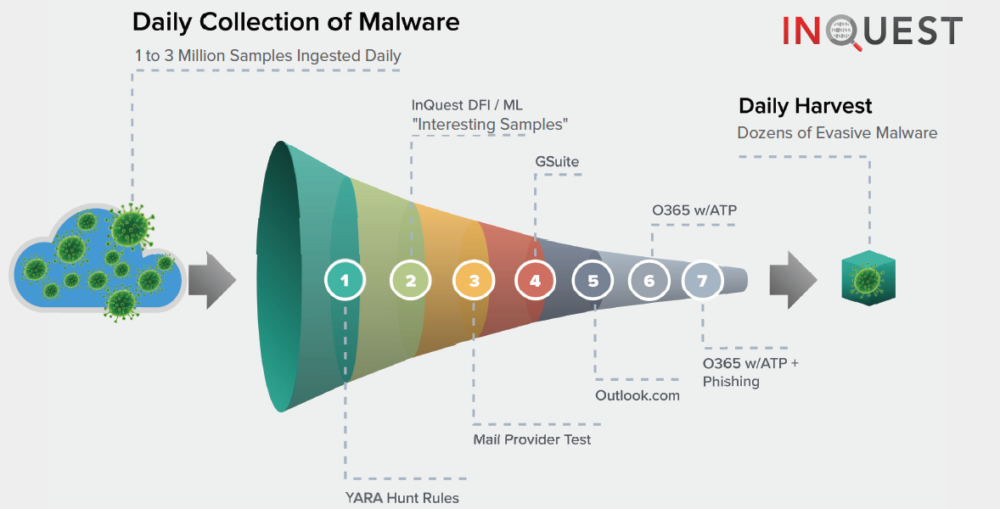
It’s no secret that client-side attacks are a common source of compromise for many organizations. Web browser and e-mail borne malware campaigns target users through phishing, social engineering, and exploitation. Much of the industry is focused on executable malware, of which there’s been an explosion in volume. Instead, we look further up the chain at the malware carriers used to gain the initial foothold on target systems. At InQuest, we’re fanatical about malware analysis and ingest real-world samples at-scale, dissecting millions of files daily. We leverage a combination of our Deep File Inspection® (DFI) analysis engine and a proprietary machine-learning apparatus to distill a daily volume of millions of samples down to a harvest consisting of dozens of “interesting” samples. These samples are verified to bypass all of Google’s and Microsoft’s available security features combined. We then innocuously “loop” this daily harvest of malware through your e-mail stack and provide you with a daily report assessing your detection gap for bleeding-edge real-world malware. The purpose of this assessment is to serve as a continuous validation of your e-mail security.
The Trystero Project
This recorded webinar serves as a sneak peek into an experiment we’ve been running at InQuest to assess and compare the major SaaS e-mail providers’ security efficacy. The common providers being examined include Microsoft, Google, and Amazon. The webinar discusses the experiment and what preliminary results look like. Mail comparison provider results have been shown that some providers are more effective at blocking a specific type of threat. However, week after week, there isn’t always a clear winner. Sometimes Microsoft is more effective, and sometimes Google takes the cake.
Comparison Metrics
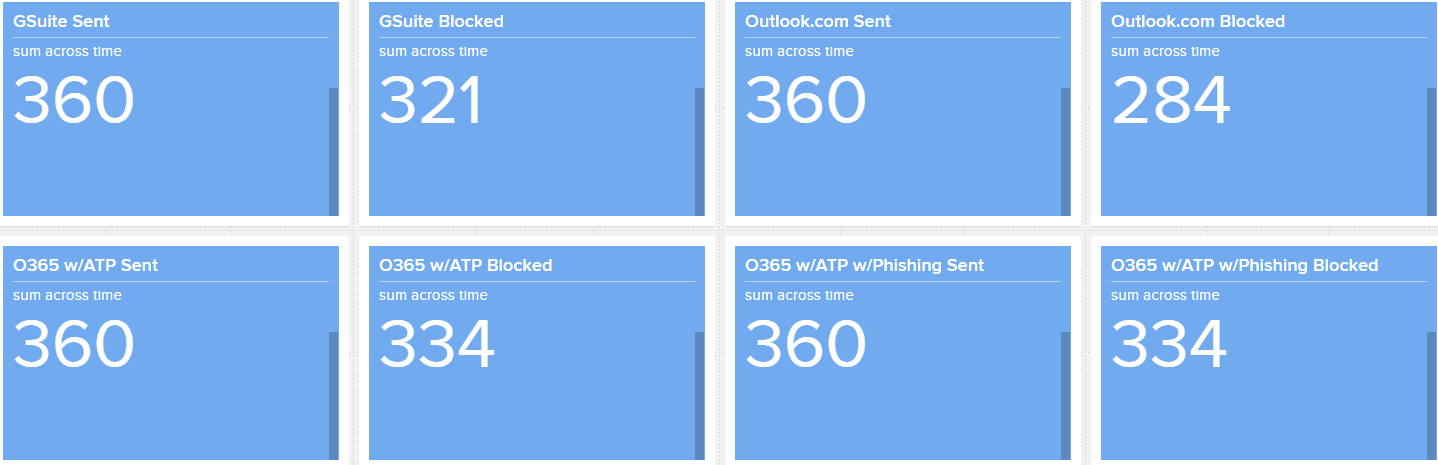
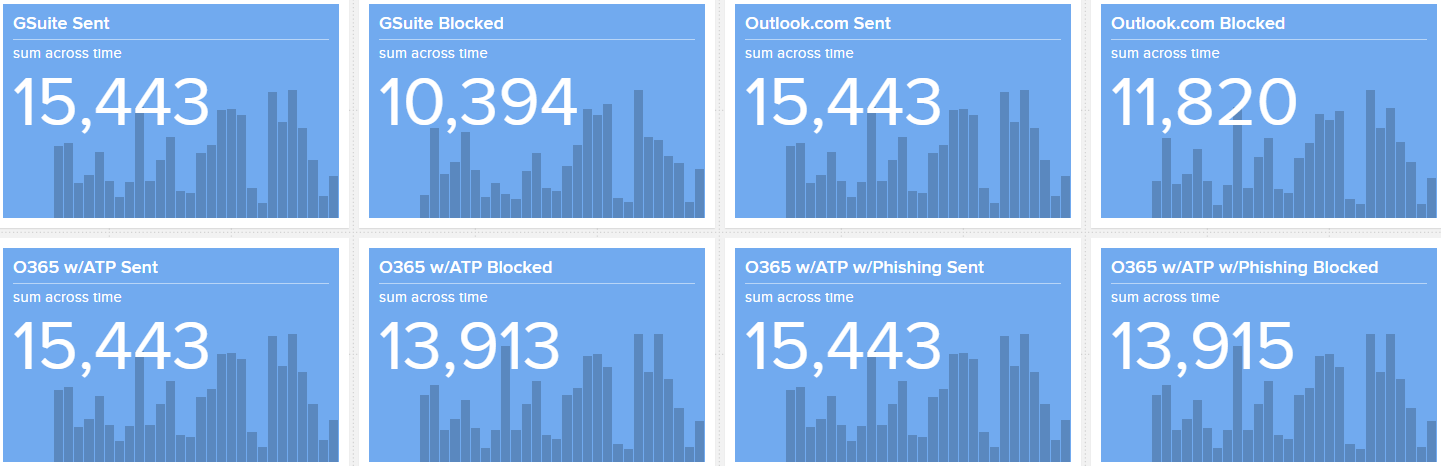

Over the course of March 2021, 1165 files bypassed the mail providers that were tested. Here are some specifics of that sample set. MIME Type
Key|Ct (Pct) Histogram
application/pdf|680 (58.37%) -
application/cdfv2|186 (15.97%) -
application/vnd.openxmlformats-officedocument.spreadsheetml.sheet|152 (13.05%) -
application/vnd.ms-excel| 43 (3.69%) -
application/vnd.openxmlformats-officedocument.wordprocessingml.document| 27 (2.32%) -
application/msword| 23 (1.97%) -
application/gzip| 23 (1.97%) -
application/x-msi| 14 (1.20%) -
text/rtf| 7 (0.60%) -
application/zip| 6 (0.52%) -
image/gif| 1 (0.09%) -
application/vnd.openxmlformats-officedocument.presentationml.presentation| 1 (0.09%) -
application/vnd.ms-outlook| 1 (0.09%) -
application/encrypted| 1 (0.09%) -
VirusTotal Positives
Key|Ct (Pct) Histogram
3|220 (18.88%) ----------------------------------------------------------------
2|165 (14.16%) ------------------------------------------------
11|157 (13.48%) ---------------------------------------------
10|119 (10.21%) -----------------------------------
12| 84 (7.21%) -------------------------
4| 74 (6.35%) ----------------------
13| 59 (5.06%) -----------------
8| 58 (4.98%) -----------------
9| 43 (3.69%) -------------
6| 30 (2.58%) ---------
14| 30 (2.58%) ---------
5| 27 (2.32%) --------
7| 20 (1.72%) ------
24| 14 (1.20%) -----
20| 11 (0.94%) ----
InQuest Threat Score
Key|Ct (Pct) Histogram
9|475 (38.43%) ----------------------------------------------------------------
8|349 (28.24%) -----------------------------------------------
7|138 (11.17%) -------------------
10|129 (10.44%) ------------------
6|102 (8.25%) --------------
5| 43 (3.48%) ------
Breach and Attack Simulation
The InQuest Breach and Attack Simulation utilizes files from the Mail Provider Comparison and are used to validate an e-mail security stack’s ability to detect currently emerging, real-world threats are harvested from the wild. InQuest gathers unique malware daily and validates the detection efficacy of common cloud e-mail providers (GSuite, O365). Collectively (stacked on top of one another), the providers’ default security stacks can detect between 85% and 95% of these novel attacks. The samples capable of bypassing these stacks are candidates for the InQuest Email Security Assessment. Breach and Attack Simulation customers can expect to receive several dozen e-mails a day with malicious attachments that have been shown to bypass multiple e-mail security solutions. These specific files have been sourced from millions of daily samples presented through customer networks, crawler infrastructure, and partner organizations. InQuest ingests millions of these files daily and processes them with our proprietary Deep File Inspection (DFI) engine and Machine Learning models. This process distills them into thousands of more interesting samples. These more interesting samples are then looped through multiple e-mail services, allowing InQuest to derive the files that multiple providers do NOT block. The resulting malicious files generally count several dozen and will be sent through your organization’s security stack to validate your e-mail providers’ security coverage. The daily breach & attack simulation and associated results are then summarized, packaged, and provided to you in a daily report.