History
Cybersecurity Awareness Month was launched by the National Cyber Security Alliance (NCSA) and the U.S. Department of Homeland Security (DHS) in October 2004 as a broad effort to help all Americans stay safer and more secure online.
When Cybersecurity Awareness Month first began, the awareness efforts centered around advice like updating your antivirus software twice a year to mirror similar actions around changing batteries in smoke alarms during daylight saving time.
Since NCSA and DHS’s combined efforts have been taking place, the month has grown in reach and participation. The month’s effort has grown to include the involvement of many industry participants that engage their customers, employees, and the general public in awareness, as well as college campuses, nonprofits, and other groups.
Between 2009 and 2018, the month’s theme was “Our Shared Responsibility.” The theme reflected the role that we all – from large enterprises to individual computer users – have secured the digital assets in their control.
In 2009, DHS Secretary Janet Napolitano launched Cybersecurity Awareness Month at an event in Washington, D.C., becoming the highest-ranking government official to participate in the month’s activities. In subsequent years, leading administration officials from DHS, the White House, and other agencies have regularly participated in events across the United States.
In 2010, the kickoff of Cybersecurity Awareness Month also included the launch of the STOP. THINK. CONNECT. Campaign. The White House’s proclamation for the month consists of STOP. THINK. CONNECT. is the national cybersecurity education and awareness message.
Starting in 2011, NCSA and DHS developed the concept of weekly themes during the month. This idea was based on stakeholders’ feedback that the many aspects of cybersecurity should be better articulated, making it easier for other groups to align with specific themes. Themes have included education, cybercrime, law enforcement, mobility, critical infrastructure, and small and medium-sized businesses.
The collaboration of NCSA and DHS on Cybersecurity Awareness Month is one of the many successful public-private partnerships critical to cybersecurity.
CISA and the National Cyber Security Alliance (NCSA) announced this year’s theme:
“Do Your Part. #BeCyberSmart.”
This theme encourages individuals and organizations to own their role in protecting their part of cyberspace, stressing personal accountability, and the importance of taking proactive steps to enhance cybersecurity.
NCSAM emphasizes “If You Connect It, Protect It.”
Throughout October, CISA and NCSA will focus on the following areas in our promotions and outreach:
Week 1: If You Connect It, Protect It
Week 2: Securing Devices at Home and Work
Week 3: Securing Internet-Connected Devices in Healthcare
Week 4: The Future of Connected Devices*
Creating an Awareness Program
Your employees are your first line of defense against cyber threats, so it is imperative they are equipped with all the knowledge to protect your organization. A comprehensive Cyber Security Awareness program is the best way to educate staff and create a security-first culture.
1. Identify Risks
The first step in creating an effective cybersecurity awareness program is evaluating the threat landscape and identifying your top risks. If employees are targeted with the wrong training, it can result in information overload, or more worryingly, organizations can leave themselves vulnerable to attack. Every organization has a different threat profile, but some of the board’s biggest threats include phishing, malware, and poor security practices. Phishing is behind the majority of all cyber attacks worldwide, and unfortunately, the common denominator behind all these attacks is human error. No matter what threats your organization is facing, taking time to correctly identify the risks will help shape the messaging, delivery, and effective targeting of your Cyber Security awareness program.
2. Change Behavior
Within the last decade, training methods have changed dramatically. Organizations are no longer restricted to classroom-based training or a tick-box one day course to demonstrate Cyber Security compliance. And quite simply, these methods no longer cut it. Employees need to become engaged with the training to fully understand what is required of them and the importance of their role in the organization’s overall security. For training to resonate, it needs to be role-specific, tailored, fun, and address the challenges that staff face daily. Providing your employees with easy-to-consume content relevant to their role is a critical step in changing their behavior. The best way to achieve this is through a comprehensive cybersecurity awareness program that leverages various tools and techniques. Engaging videos, realistic scenarios, quizzes, policies, and real-world phishing simulation tests will ensure that staff is fully trained to recognize and identify the most up to date threats. Organizations can also utilize communications and marketing tools such as blogs, awareness posters, and real-life case studies to reinforce key messaging. A comprehensive and varied cybersecurity awareness program is key to mitigating risk and positively impacting employee behavior.
3. Schedule Delivery of Training
Security awareness training should be an ongoing process and conducted at regular intervals throughout the year. Training employees once a year on Cyber Security is not enough to equip them to deal with the myriad of evolving threats. Security policies could be rendered useless unless organizations have thorough and continual monitoring of Cyber Security compliance. Cybercriminals launch scams to coincide with seasonal and monthly events, so unless your employees are receiving regular training on the most up to date security threats, they will not be able to recognize new attack methods used to target them. To effectively change employee behavior and create a culture of enhanced Cyber Security awareness, organizations should make an annual security awareness campaign that encompasses engaging videos, policies, quizzes, surveys, and simulated phishing. This will help keep staff engaged and prevent them from getting fatigued with the same repetitive content. Organizations can tailor different awareness materials to other groups of users depending on the specific threats they face.
4. Test Effectiveness of Training
At the very start of a Cyber Security awareness program, organizations should conduct an initial baseline assessment to determine where the risks lie. Once this has been established, regular phishing simulations can be conducted to determine how susceptible the company is to fraudulent phishing emails and help identify staff that requires additional training. Controlled simulation tests will help employees recognize, avoid, and report potential threats that could threaten the organization’s security. However, to truly improve employee behavior, organizations should run a full educational program in conjunction with simulated phishing campaigns. Quizzes and tests can be added to training videos to help reinforce critical messaging and reduce risk.
5. Track Metrics
To determine if your Cybersecurity awareness program is effective, your organization will need to track the metrics and act accordingly. A detailed reporting structure will provide information on participation, engagement, and help assess employees’ progress or specific departments across the entire organization. Metrics will enable you to identify which areas employees are struggling with and determine which staff members could handle more advanced training. This data can be used to shape future training by providing feedback on what’s working and what’s not. For example, if your organization is not seeing a decrease in security incidents, you may need to re-evaluate your approach and try a different method despite a security program in place.
Road Map / Maturity Model
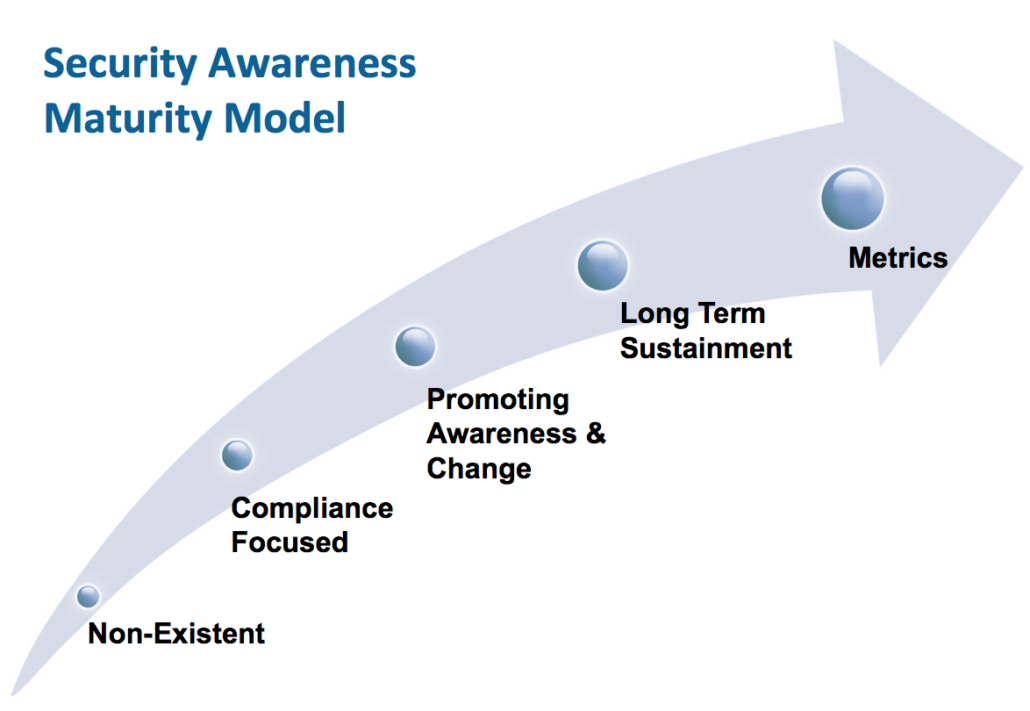
Designed to help your organization build, maintain, and measure a thriving security awareness program, over 200 awareness professionals collaborated to develop the SANS Security Awareness Maturity Model. This model enables organizations to identify where their security awareness program is currently at, where a qualified leader can take it, and outlines the path to get to where they want to be. The model is based on five distinct stages, each building upon the previous stage.
No Awareness Program
The program is non-existent. The workforce has no idea that they are a target, do not know or understand organizational security policies, and can easily fall victim to attacks or their own mistakes.
Compliance Focused
The program is designed primarily to meet specific compliance or audit requirements. Training is limited to an annual or ad-hoc basis. The workforce is unsure of organizational policies, their role in protecting their organization’s information assets, and how to prevent, identify, or report a security incident.
Promoting Awareness & Behavior Change
The program identifies the training topics that have the greatest impact in supporting the organization’s mission and focuses on those key topics. The program goes beyond annual training and includes continual reinforcement throughout the year. Content is addressed in an engaging and positive manner that encourages behavior change at work and at home. This helps the workforce understand and follow organizational policies and actively recognize, prevent, and report incidents.
Long-Term Sustainment
The program has processes and resources in place for a long-term life cycle, including (at a minimum) an annual review and update of both training content and communication methods. The program goes beyond just changing behaviors and begins to change the culture of the organization.
Metrics Framework
The program has a robust metrics framework to track progress and measure impact. As a result, the program is continuously improving and able to demonstrate return on investment.
Cyber Safety Tips Courtesy of FBI
- Keep software systems up to date and use a good anti-virus program.
- Examine the email address and URLs in all correspondence. Scammers often mimic a legitimate site or email address by using a slight variation in spelling.
- If an unsolicited text message, email, or phone call asks you to update, check, or verify your account information, do not follow the link provided in the message itself or call the phone numbers provided in the message. Go to the company’s website to log into your account or call the phone number listed on the official website to see if something does in fact need your attention.
- Do not open any attachments unless you are expecting the file, document, or invoice and have verified the sender’s email address.
- Scrutinize all electronic requests for a payment or transfer of funds.
- Be extra suspicious of any message that urges immediate action.
- Confirm requests for wire transfers or payment in person or over the phone as part of a two-factor authentication process. Do not verify these requests using the phone number listed in the request for payment.
Conclusion
Human error and mistakes are significant factors in cybersecurity breaches, where trusted but unsuspecting insiders are to blame. From phishing emails to lost or stolen devices, mistakenly confidential data sent to insecure home systems, or stored within public clouds, such mistakes can be very costly for a company. Security awareness helps to mitigate these risks by educating users of the threats before they impact an organization. Cybersecurity awareness month has come a long way over the years, but following an implementation plan and maturity model are still necessary to achieve the desired results.

