IQ-FA008:Remcos Maldoc Utilizing Macrosheets
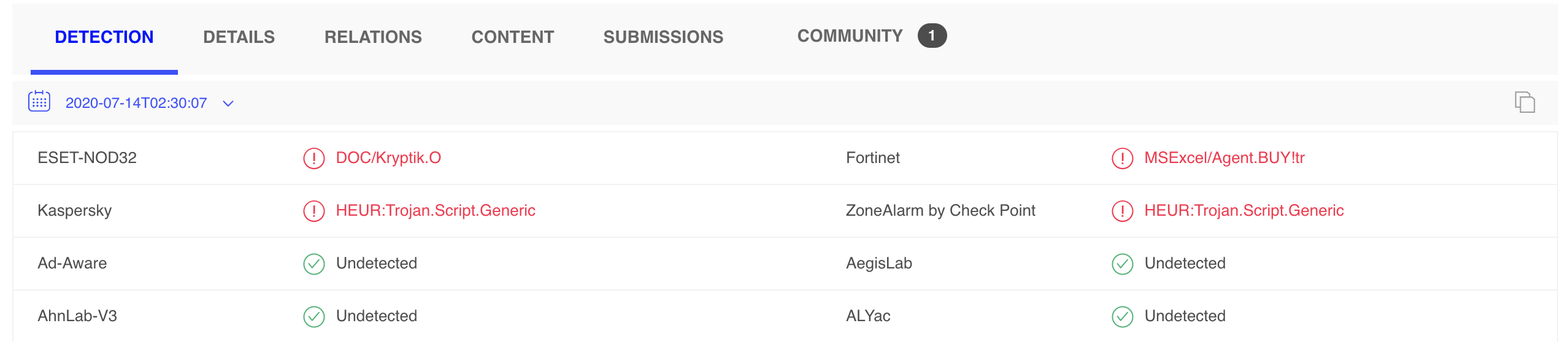
Low Detection:
This sample is once again leveraging Macrosheets… still a good tactic for actors, despite having extensive coverage for 18 months now. Some previous InQuest writing on Macrosheets:
- ZLoader 4.0 Macrosheets Evolution
- Getting Sneakier: Hidden Sheets, Data Connections, and XLM Macros
- Extracting “Sneaky” Excel XLM Macros
This macrosheet provides an extra level of intricacy in it’s obfuscation technique. Eventual payload is Remcos RAT, which, has decent AV detection (14/72):
That payload is downloaded from: hxxp://47.106.112.106:8032/app/logo[.]gif
And has relations to the following Domains:
The purpose of the office domain is self evident. For those who aren’t familiar, Huobi is a legitimate crypto currency exchange: https://www.huobi.com
Indicators
Note: There is a lot of interesting pivots that can be done from the Indicators
| Date Observed | Indicator Type | Indicator |
|---|---|---|
| 7/14/2020 | XLS Document | fe809aa7410d9df4db47ea209891c441028836edadd44beb0997d9d25be354d3 |
| 7/14/2020 | Binary | 0892656183c07a099887cd0ad837f05d17cd77a8d253f3e8b637bc099c3bcb0b |
| 7/14/2020 | Hostname | update.office365excel.org |
| 7/14/2020 | Hostname | update.huobibtc.net |
| 7/14/2020 | IP Address | 47.106.112.106 Aliyun Computing Co. Ltd 37963 |