The year-long anticipation for the big day is almost here! Christmas (and other Holidays) are here to enjoy! All of the shopping, wrapping gifts, baking cookies, and family members arriving is an exciting time. All that is left to do for the big day is put up the stockings and find out if you have been naughty or nice this year. No one wants to get coal in their stocking, but it does happen. In this case, unfortunately, your stocking is your computer, and bad guys are delivering the coal in the form of ransomware. Your computer is where you hope not to find a lump of coal, but trinkets from Santa and not where you find out whether you have been naughty or nice. So, what can be done about this mess in our Christmas stocking?
In case people are not aware of what ransomware is, in short, it disrupts the use of computers via unauthorized modifications to data rendering it unusable. The user’s data (files) are standard extensions like “.doc” for example and they are changed from .doc to whatever the Ransomware variant is programmed to change it to while encrypting the files, i.e. (.DOC can be changed to .OHNOES). These files are no longer accessible except to the Ransomware creators. The screen will populate, showing a ransom demand or note asking for payment in the form of cryptocurrency (typically Bitcoin/Monero) or initiate a process using throwaway email accounts (one-time use email addresses) to carry out additional instructions to the infected individuals. The next step is to deliver the desired ransom payment to the threat actor. After delivery, the threat actor will either offer decryption or restore the data (files) to an accessible/usable state via a key for decryption of their choosing or any other method they can dream up.
The reason for bringing this up is that an unaware user or “target” of a spearphishing campaign can take down a whole city’s emergency communication system (sorry NOLA sounds rough, but good work on seemingly being able to stop it from spreading). My guesses at the time were Megacortex or Ryuk. It ends up that the answer is Ryuk which is easily pronounced if you have played Street Fighter II.

After the New Orleans’ news regarding a devastating ransomware attack was released, a coworker sent over a link to a pretty neat historical ransomware attack map that identifies state and federal utilities that have been targeted with ransomware variants and links to any articles on the attacks. Here is the latest view of this attack map and the link. Ransomware Attacks Map | StateScoop
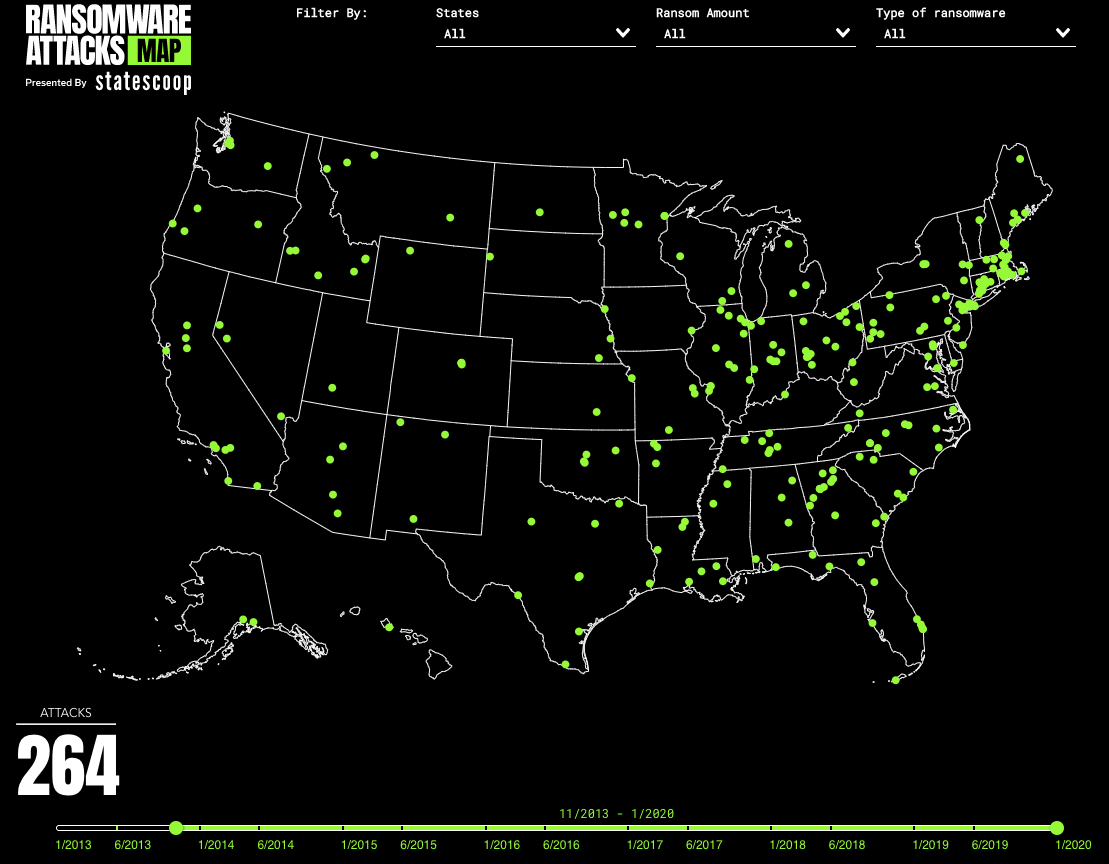
After reviewing these historical events, it is apparent that the number of ransomware attacks is going to continue to rise going into 2020. The continued targeting of critical infrastructure and individuals in both the public and private sectors is going to get worse before it gets better.
One critical component to help thwart off this hot garbage is getting consumers to care, even just a little bit about what I am calling a prelude to the next major world battle. The worst attitude that I can identify is the lack of caring and a woeful sense of urgency by both professionals and individuals. Many clients believe that the security industry should be able to stop this nastiness. The truth is with the amount of variants found from a simple Google search was well over 1500 and the amount of White Hat defenders versus Black Hat nefarious individuals is an astonishing revelation. There is approximately 1 “good guy” versus over 13,000 “bad guys” on a daily basis. That is just a crazy amount of pressure that the good guys have to face and so every little bit of shared knowledge to the less informed helps.
The non-stop reporting and observations people are sharing on social media make it apparent that we have run into a problem that we can not easily fix. The varying sophistication level of these delivery methods that attackers are coming up will continue to evolve and at the same time it does not fair well for the security. This is because the only thing that the attackers/threats actors do is change the email address for delivery of the ransom, give next stage instructions, or change the Cryptocurrency wallet which prolongs the delivery of the coal on your computer.
In Conclusion:
Ransomware is being monetized with little to no effort by individuals that are trying to make a quick buck. This is due to open-source code (easy obtainable copies) of ransomware and it’s out of control. There have been cases in the past where meddling novices have been trying to get some quick cash for concert tickets and such and stumbled into some ransomware to try out. This did not end well for them however, no concert for them as they were caught. This goes to show the ease of access to ransomware components and variants can cause serious damage when meddled with by novices. We hope that everyone has a fun and safe holiday season!
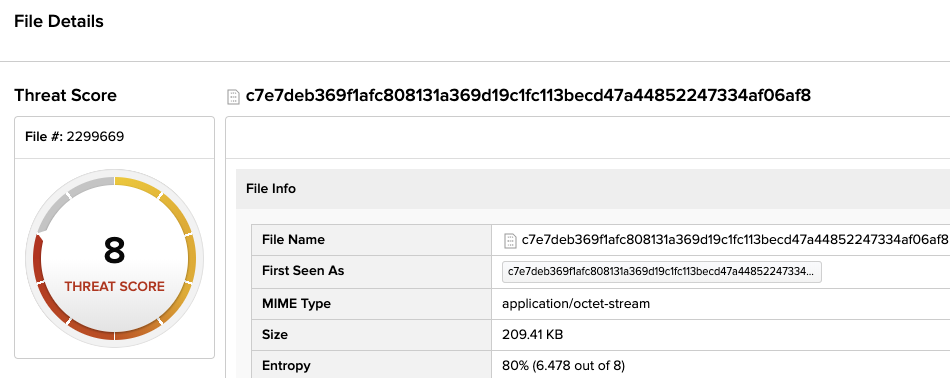
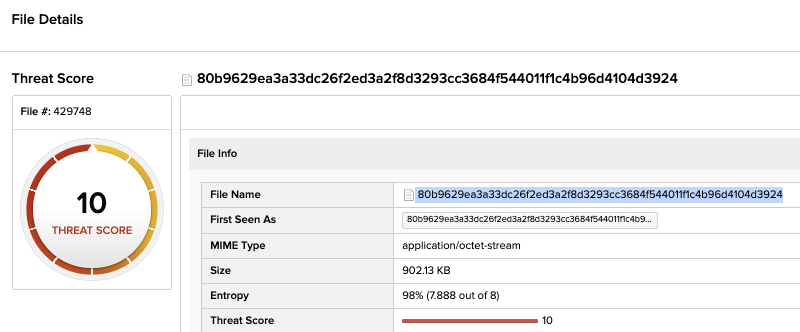
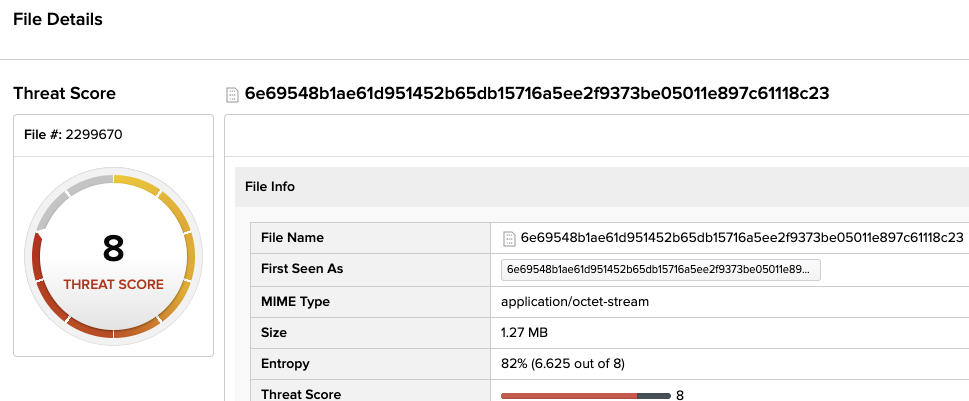
Here is a list of interesting samples with Threat scores from our (DFI) Deep File Inspection
RYUK – c7e7deb369f1afc808131a369d19c1fc113becd47a44852247334af06af8c987
MegaCortex – 80b9629ea3a33dc26f2ed3a2f8d3293cc3684f544011f1c4b96d4104d3924
LockerGoGa – 6e69548b1ae61d951452b65db15716a5ee2f9373be05011e897c61118c239a77